Authenticate/Decrypt packet error: packet HMAC authentication failed
-
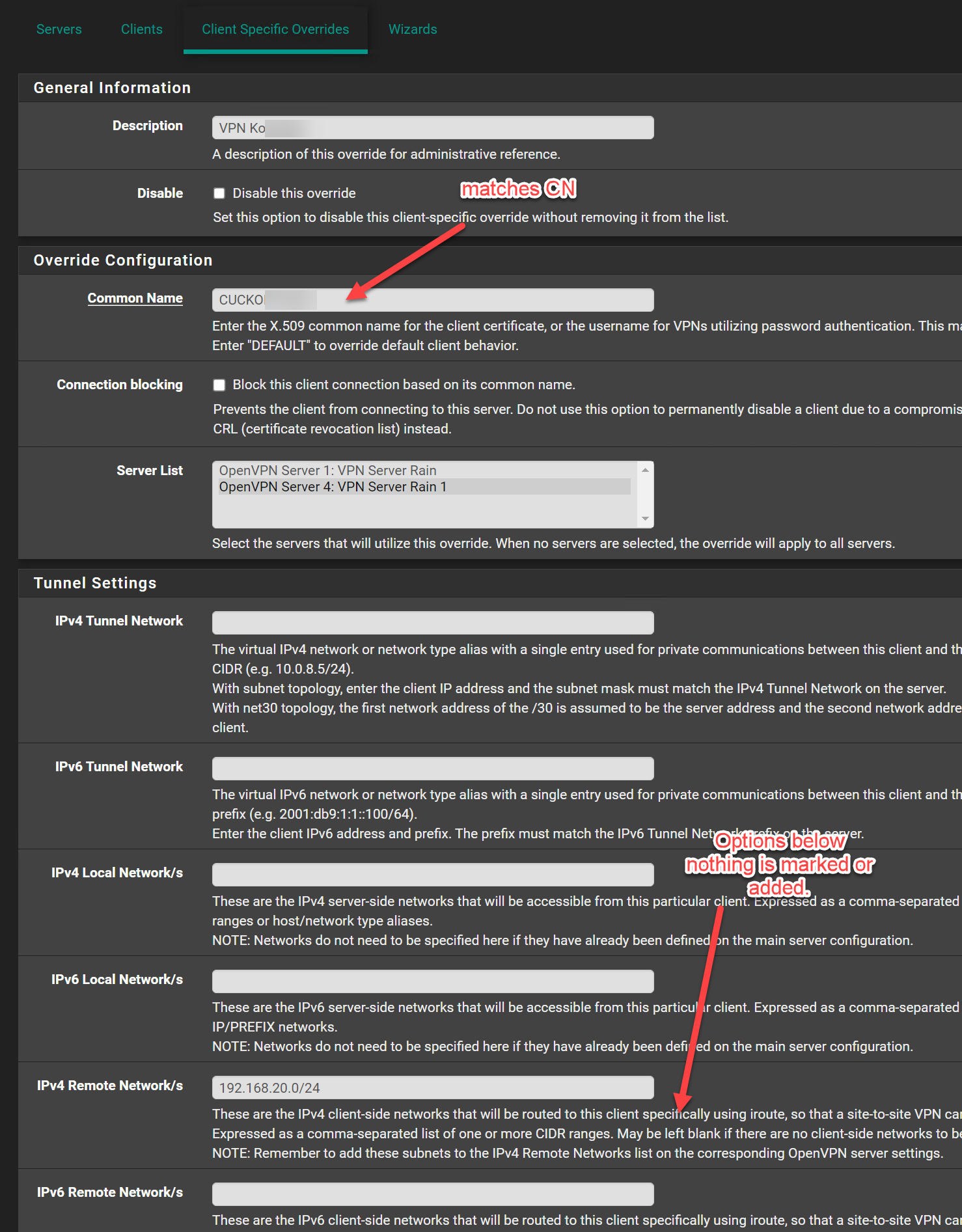
@hispeed Hey - as I learned recently, you have to take the Tunnel Network Address (10.0.5.0/24) out of the client config - When using an override.
I'm assuming your TLS keys match and your certs are in order. Try the tunnel network and report back.
-
@swixo
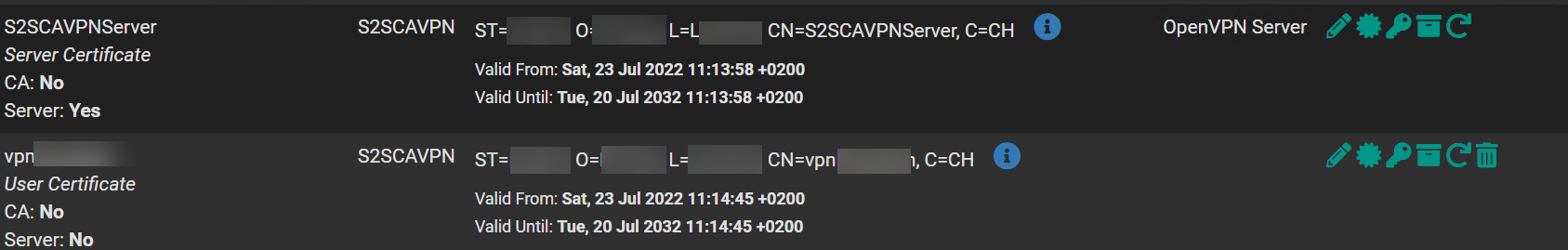
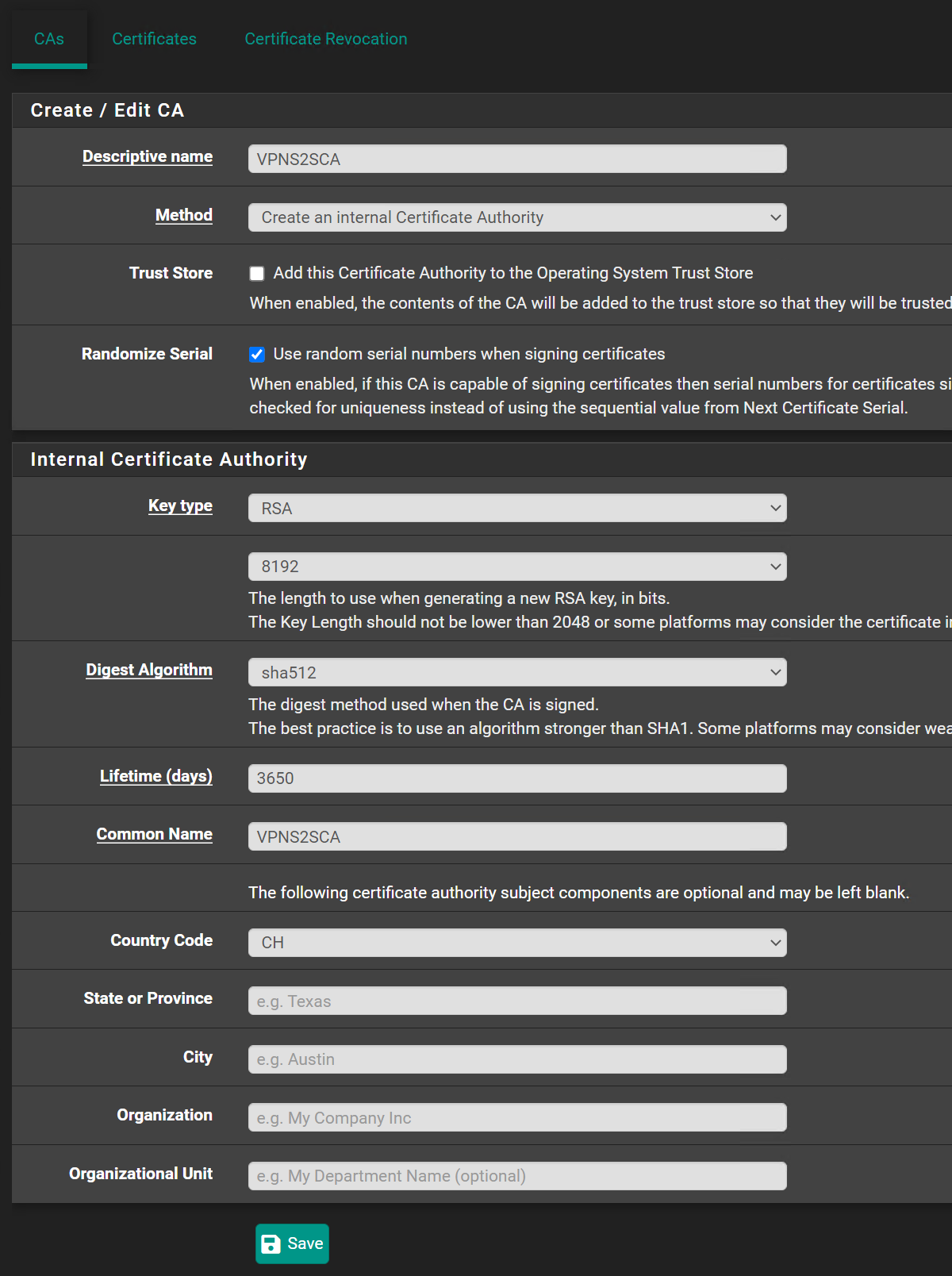
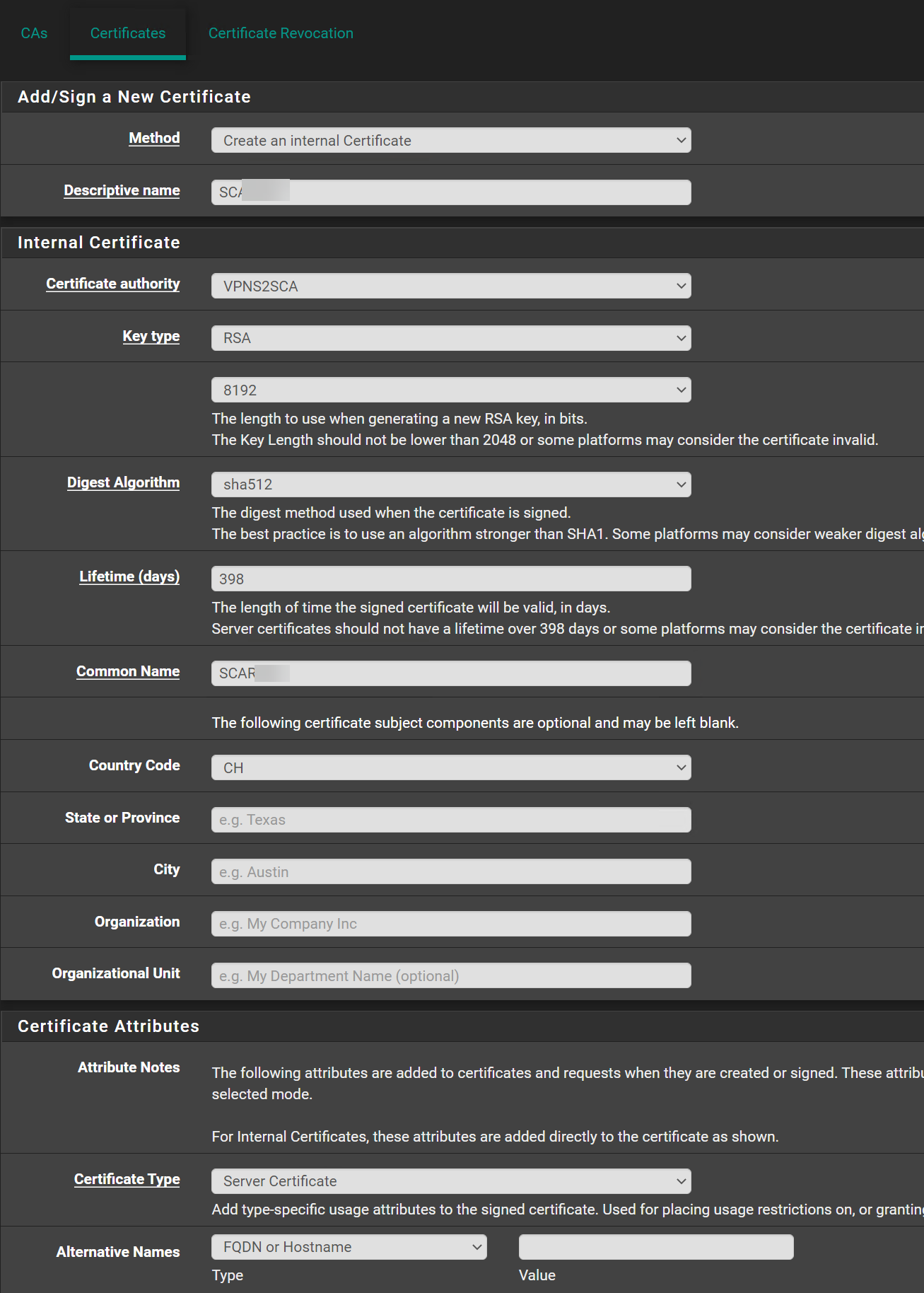
No luck still the same error.CA:
Server Certificate:
Client Certificate:
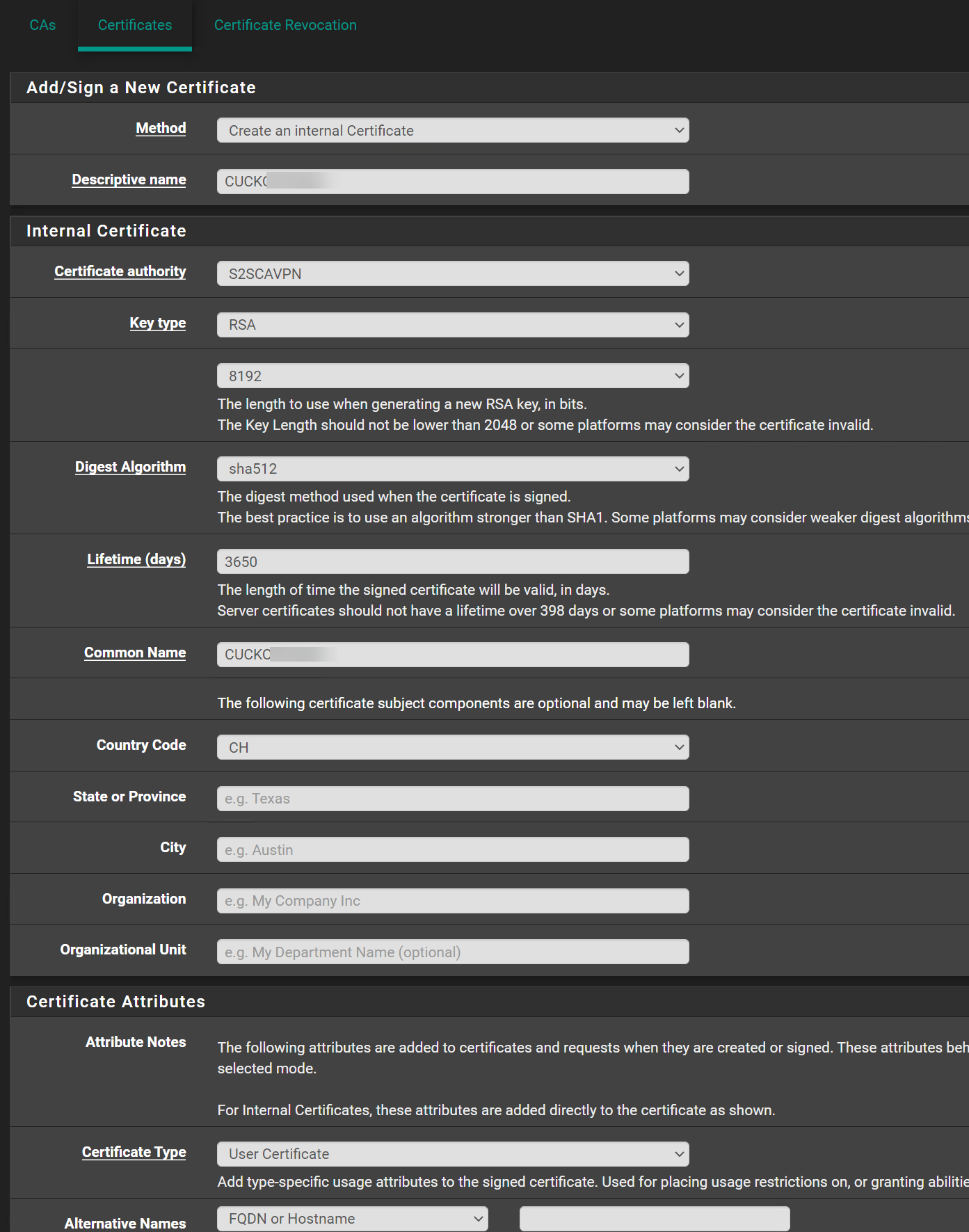
Is this fine like that?
-
@hispeed also - have the process widget on your dashboard - restart the openvpn server and client services manually after making changes like this. For some reason - mine requires that.
-
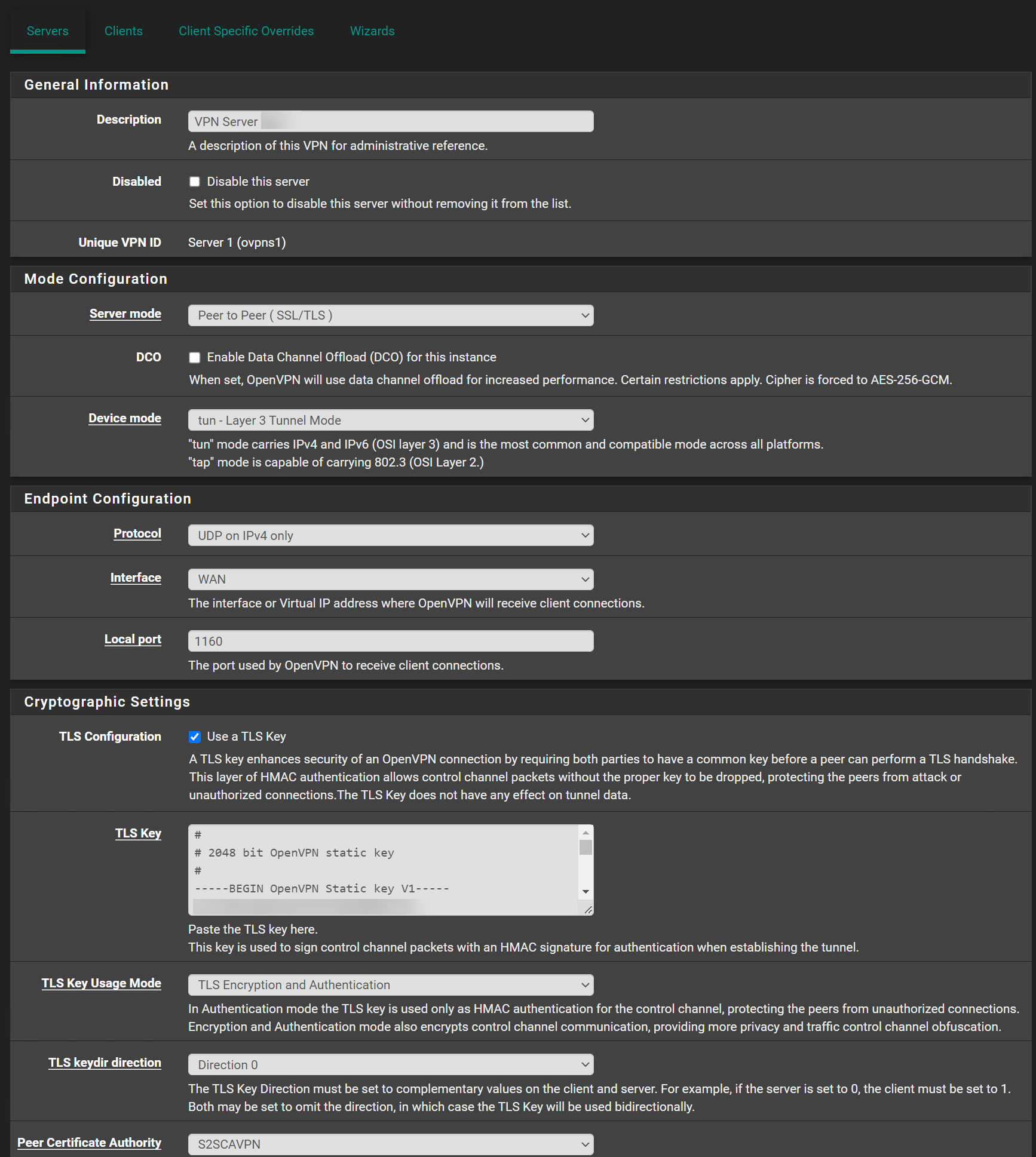
@swixo Oh here is a problem - you have TLS Auth+Encryption on the Server and TLS Auth only on client.
Those need to match.
-
I restarted the client and server, doesn't help. I also changed the TLS Auth on both side to TLS Auth only.
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 SIGUSR1[soft,tls-error] received, client-instance restarting
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS Error: TLS handshake failed
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS Error: TLS object -> incoming plaintext read error
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS_ERROR: BIO read tls_read_plaintext error
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 VERIFY ERROR: depth=0, error=unable to get local issuer certificate: CN=CUCKOXXXXXX, C=CH, serial=4 -
@hispeed Can you show your client override?
-
@hispeed
The client and server certificates are issued by different CAs.Both have to be from the CA you've selected in the server settings and copied to the client.
-
-
@hispeed
Is the CN from the Client? And these are both coming from the same CA / Copied from the Server to the client? -
@swixo Since its tough to see the certs because of redaction,
the general process I would follow:On Server:
Create CA. From the CA->Generate the Server Cert and the Client Cert. Make sure server bit set (on the server cert).Export the CA Cert (no key) to a file - and Import that to the client.
Export the Client .P12 file on the server, and import it to the Client.
Assign the certs in the server and client config. Pay attention to the CN in the override.
-
@swixo and @viragomann
It works finally. Thank you for this hint viragomann and also swixo. Boah i was so close to give up. My fault I took the wrong CA for the client certificate.
Stupid error i have spent several hours and recreated several times the certificates.....
Thank you and have a good weekend.
-
@hispeed Great! Another triumph!