Authenticate/Decrypt packet error: packet HMAC authentication failed
-
I tried to get my Peer to Peer ( SSL/TLS ) OpenVPN working today. I recreated the certificates and rebooted the Firewall but with no luck.
I always get this error: Authenticate/Decrypt packet error: packet HMAC authentication failed
Online i read it's probably a certificate problem but I seriously checked them triple.
Jul 23 17:52:16 openvpn 87717 Authenticate/Decrypt packet error: packet HMAC authentication failed Jul 23 17:52:15 openvpn 37415 Authenticate/Decrypt packet error: packet HMAC authentication failed Jul 23 17:52:15 openvpn 37415 Authenticate/Decrypt packet error: packet HMAC authentication failed Jul 23 17:52:07 openvpn 87717 Initialization Sequence Completed Jul 23 17:52:07 openvpn 87717 Incoming Data Channel: Using 512 bit message hash 'SHA3-512' for HMAC authentication Jul 23 17:52:07 openvpn 87717 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Jul 23 17:52:07 openvpn 87717 Outgoing Data Channel: Using 512 bit message hash 'SHA3-512' for HMAC authentication Jul 23 17:52:07 openvpn 87717 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Jul 23 17:52:06 openvpn 87717 [S2SCAVPNServer] Peer Connection Initiated with [AF_INET]188.62.167.223:1160 Jul 23 17:52:06 openvpn 87717 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 8192 bit RSA, signature: RSA-SHA512 Jul 23 17:52:06 openvpn 87717 P2P mode NCP negotiation result: TLS_export=0, DATA_v2=0, peer-id 0, cipher=(not negotiated, fallback-cipher: AES-256-CBC) Jul 23 17:52:06 openvpn 87717 WARNING: 'ifconfig' is present in local config but missing in remote config, local='ifconfig 10.0.5.0 10.0.5.1'Additional Information:
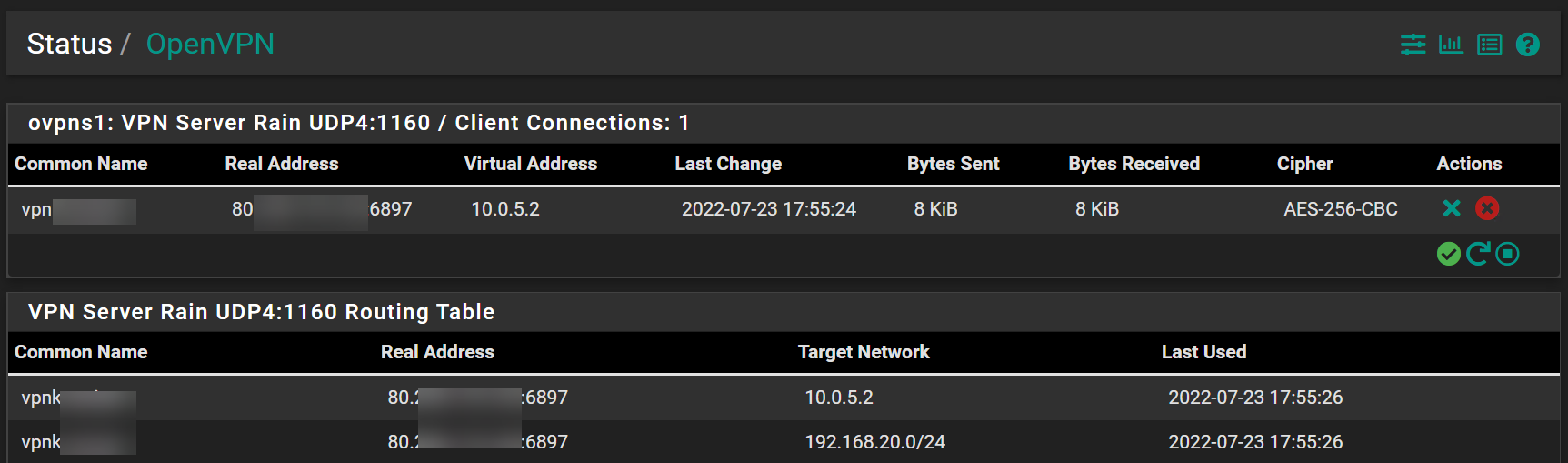
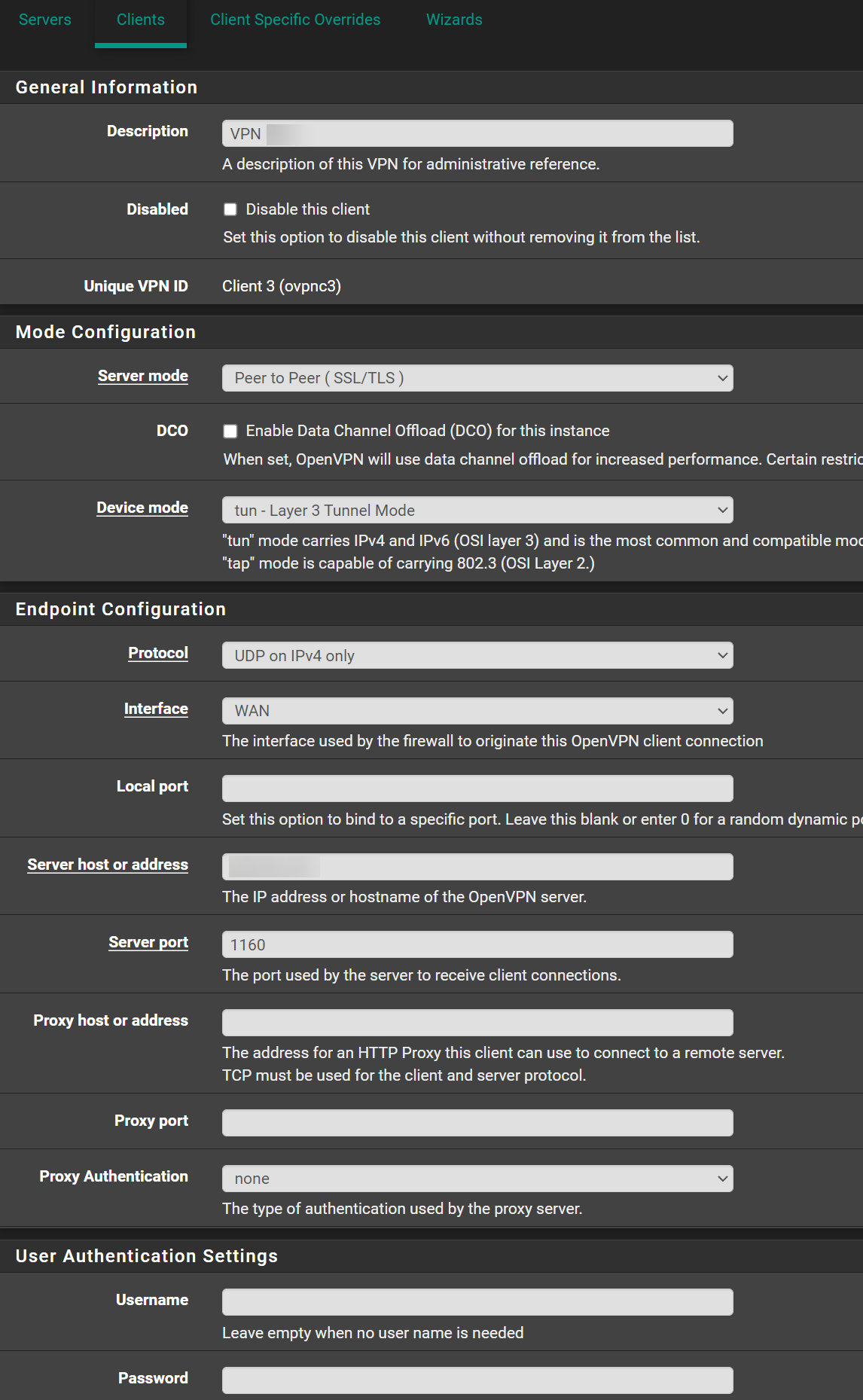
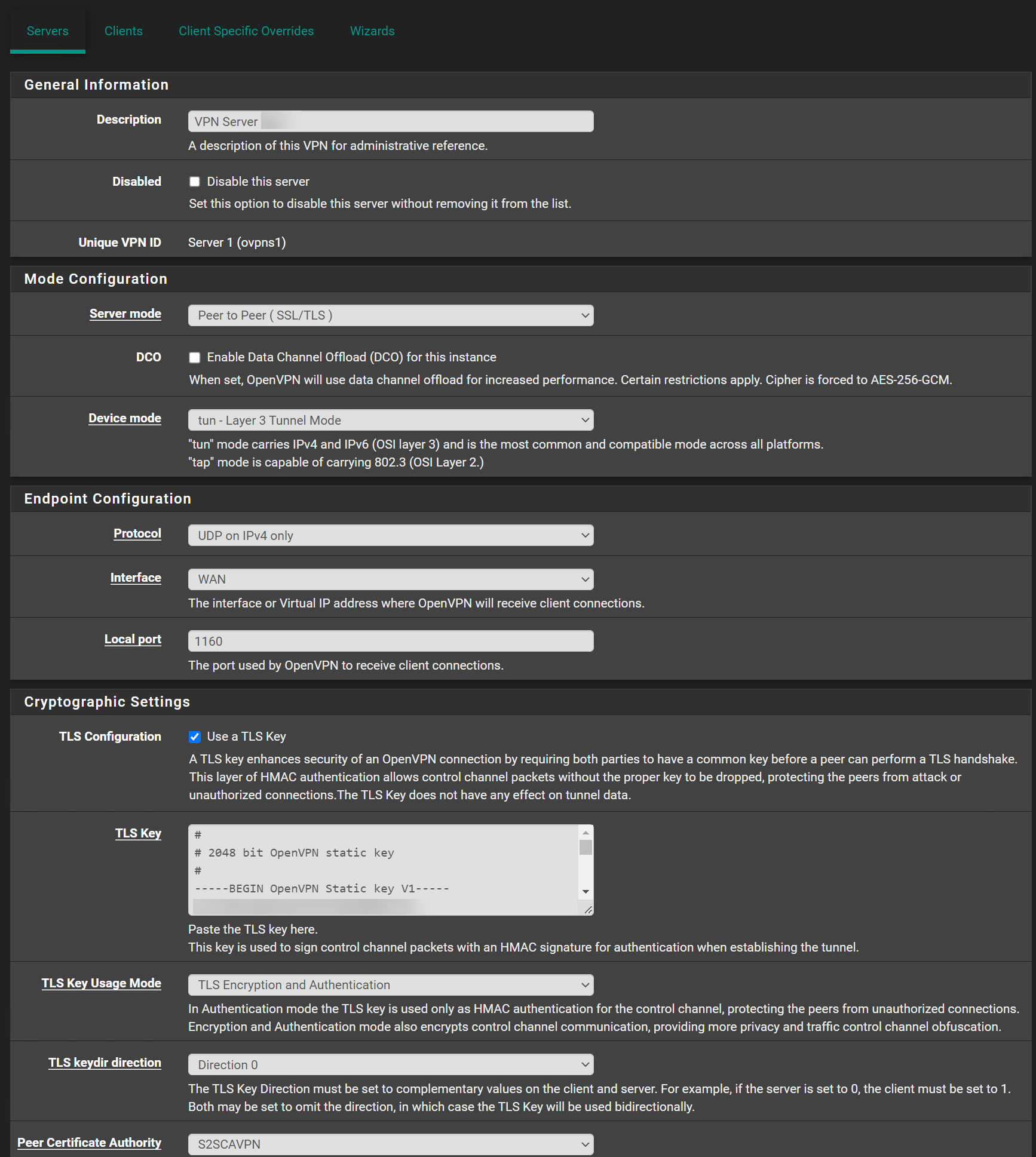
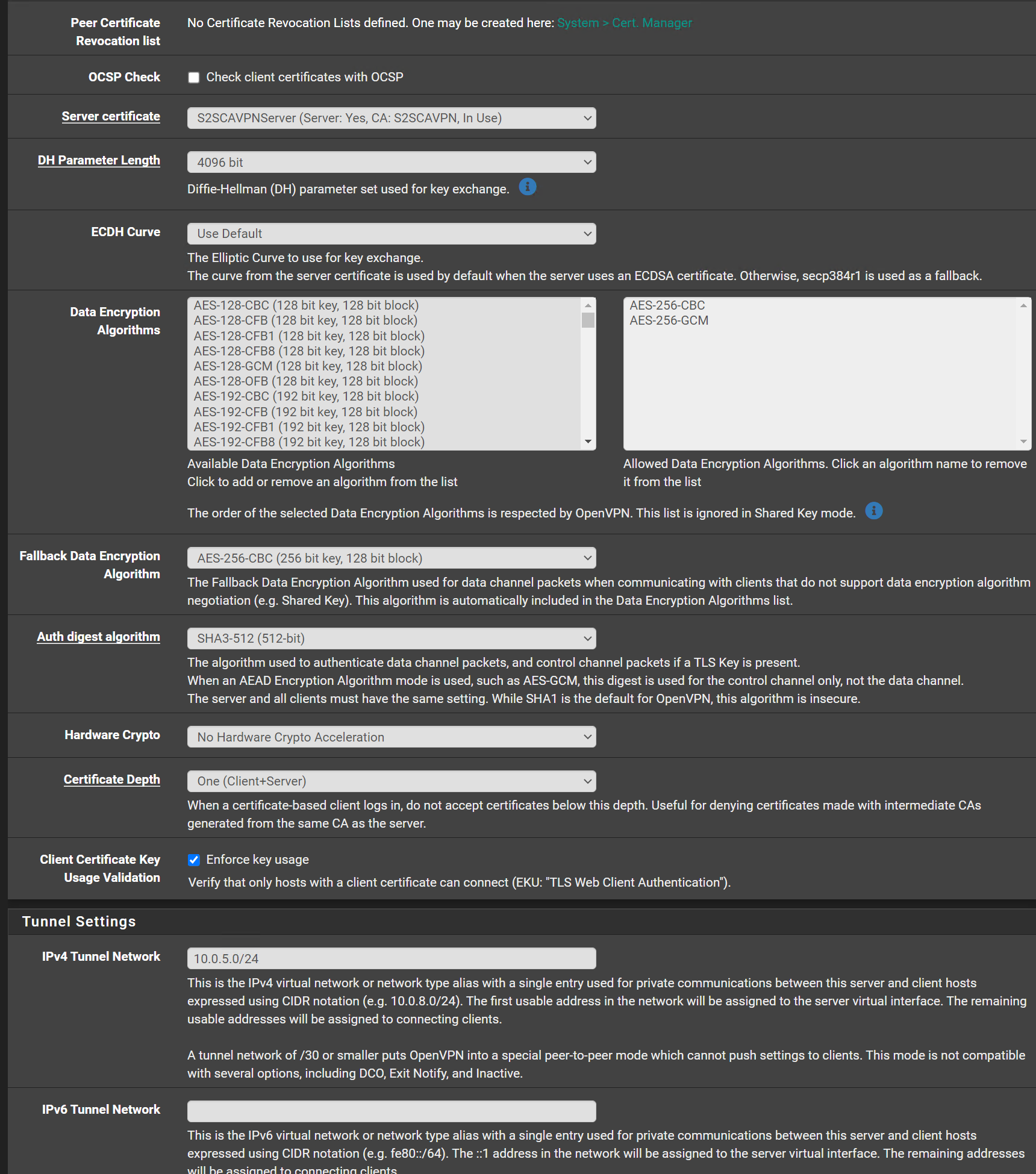
OpenVPN Server Configuration:
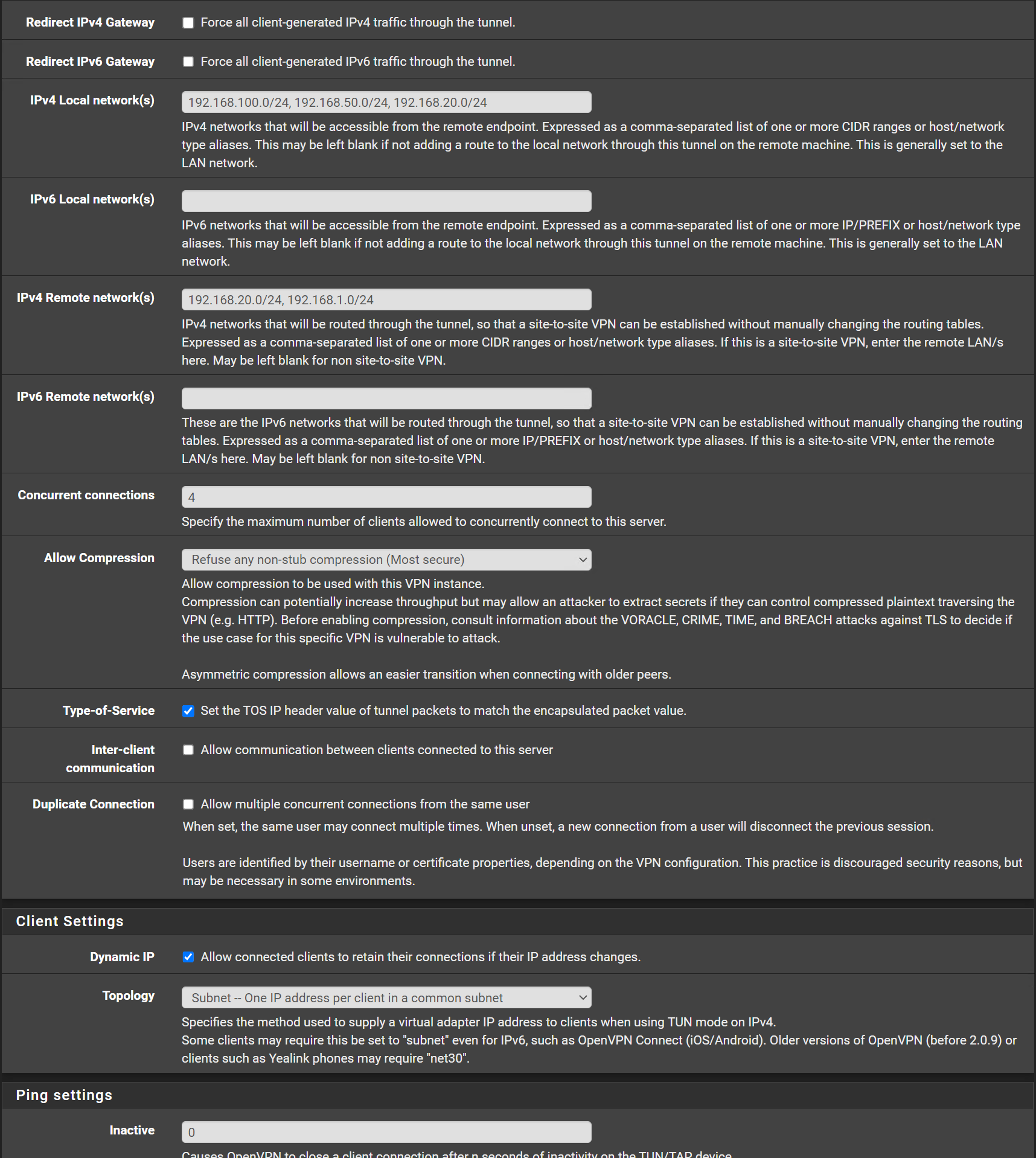
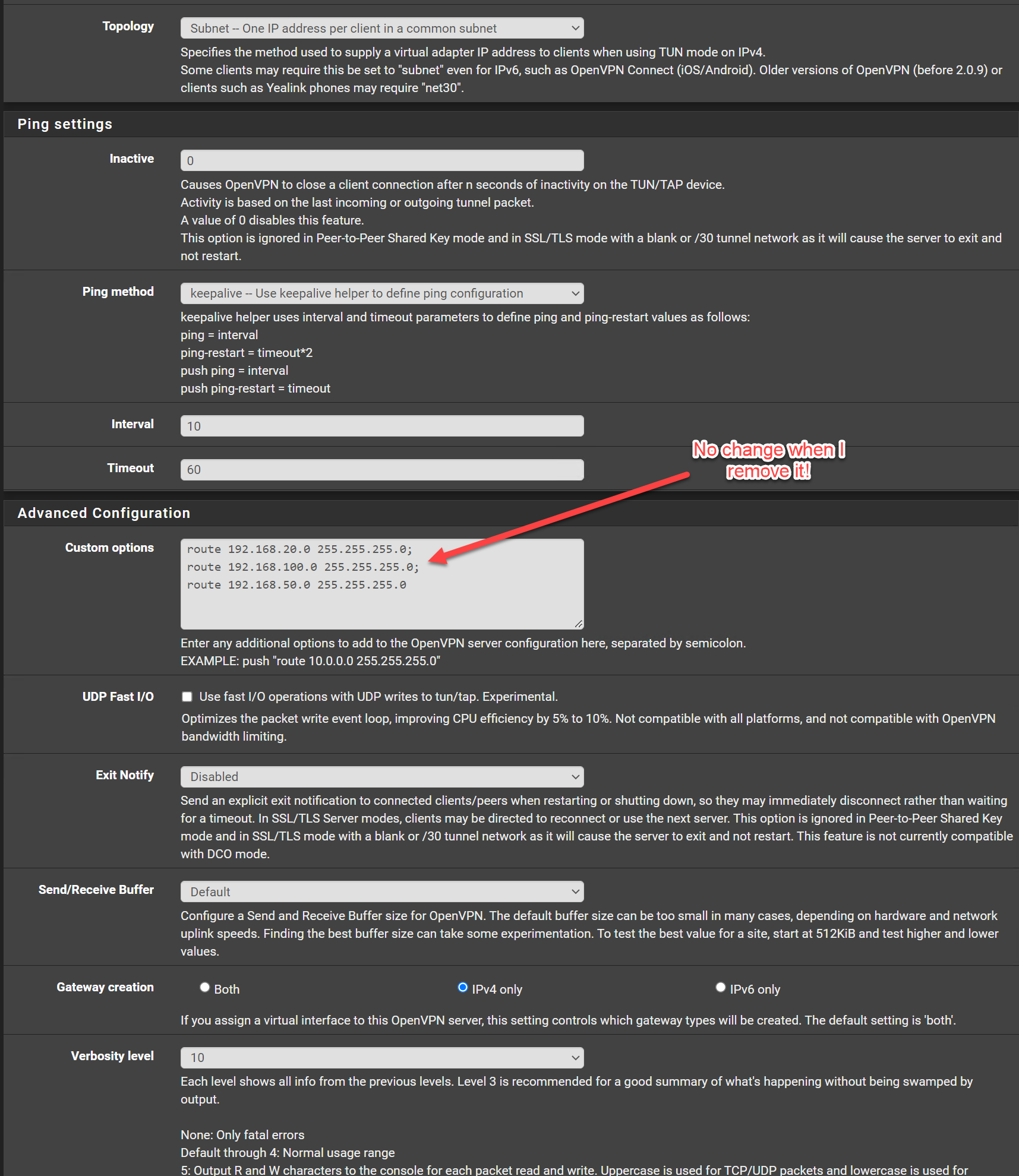
Certificate
Server and User
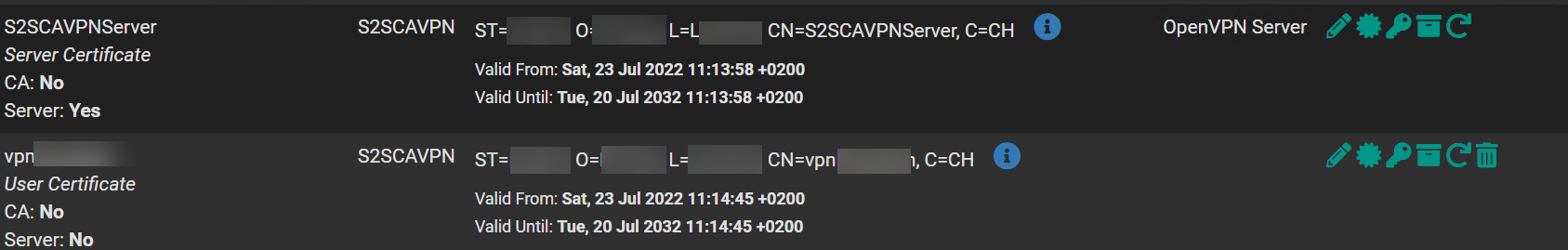
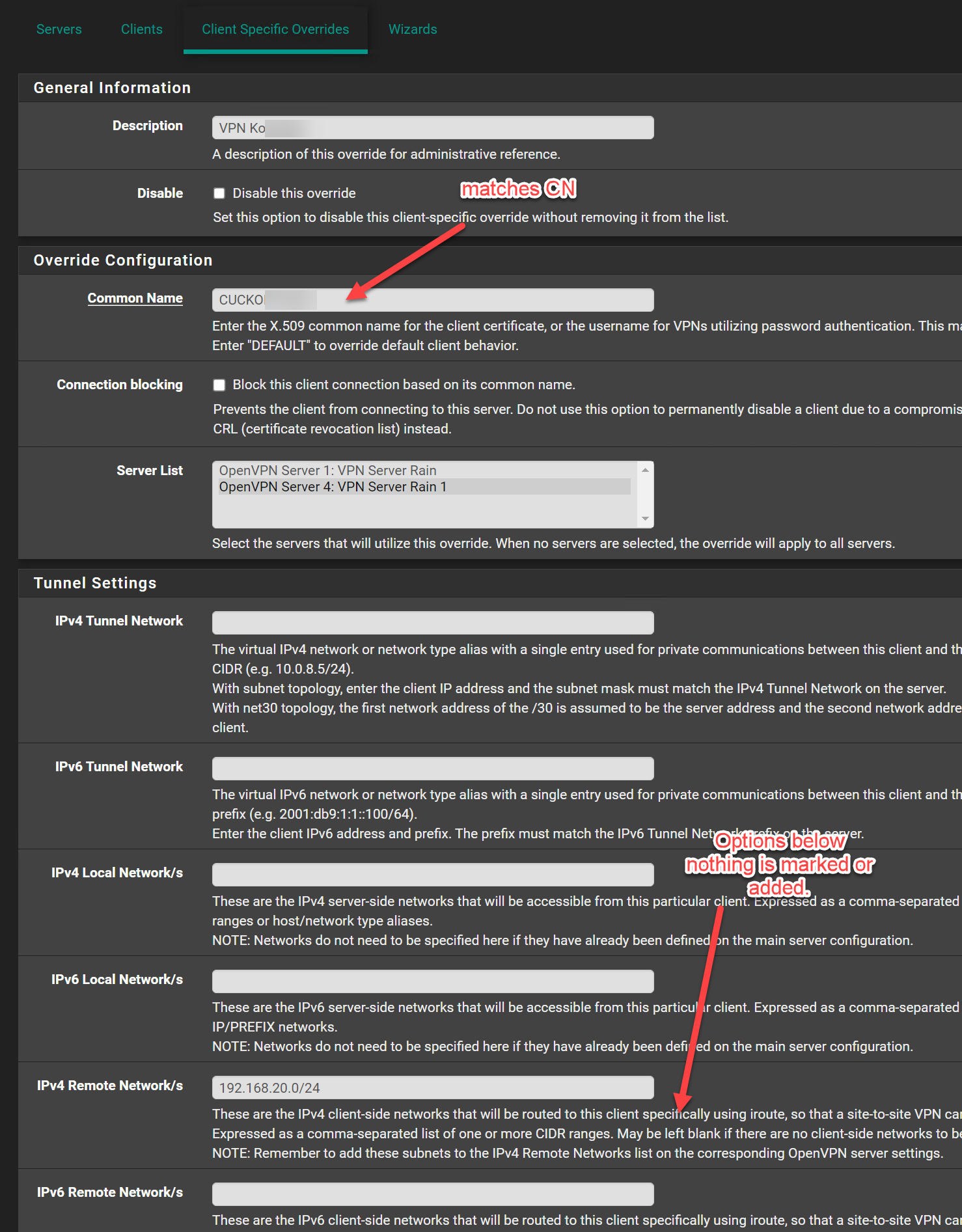
I also made the Client Specific Override this should be fine I followed the official netgate Tutorial for all this.
Any help is welcome.
-
@jimp
How much does the support cost to get a side to side from 2 pfsenses to work with TLS certificate on the latest pfsense version? -
Can you show us a client config?
I have key direction to "Both Directions". Harder to make a mistake that way. -
@swixo Show us the client override too.
-
-
@hispeed Hey - as I learned recently, you have to take the Tunnel Network Address (10.0.5.0/24) out of the client config - When using an override.
I'm assuming your TLS keys match and your certs are in order. Try the tunnel network and report back.
-
@swixo
No luck still the same error.CA:
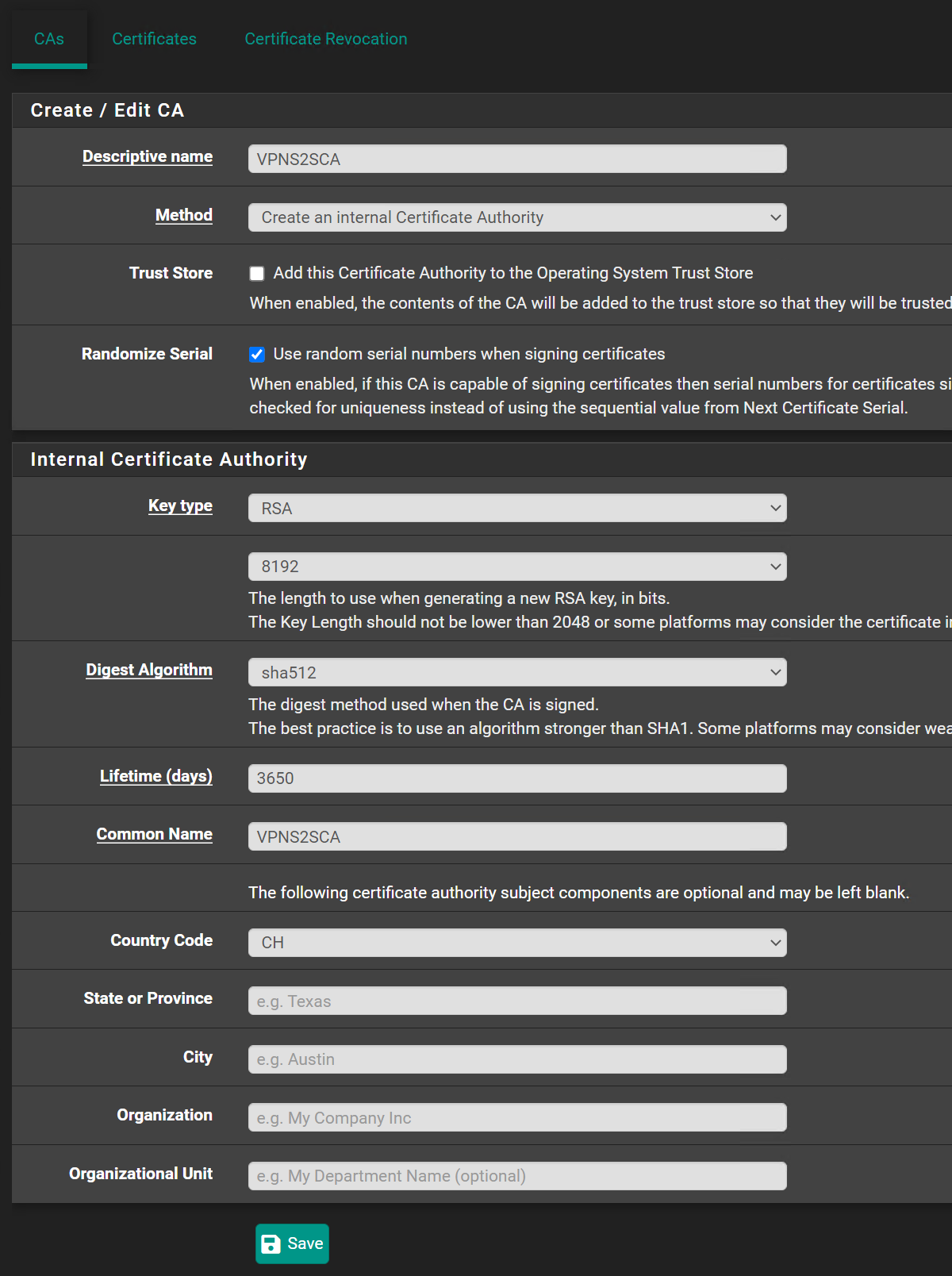
Server Certificate:
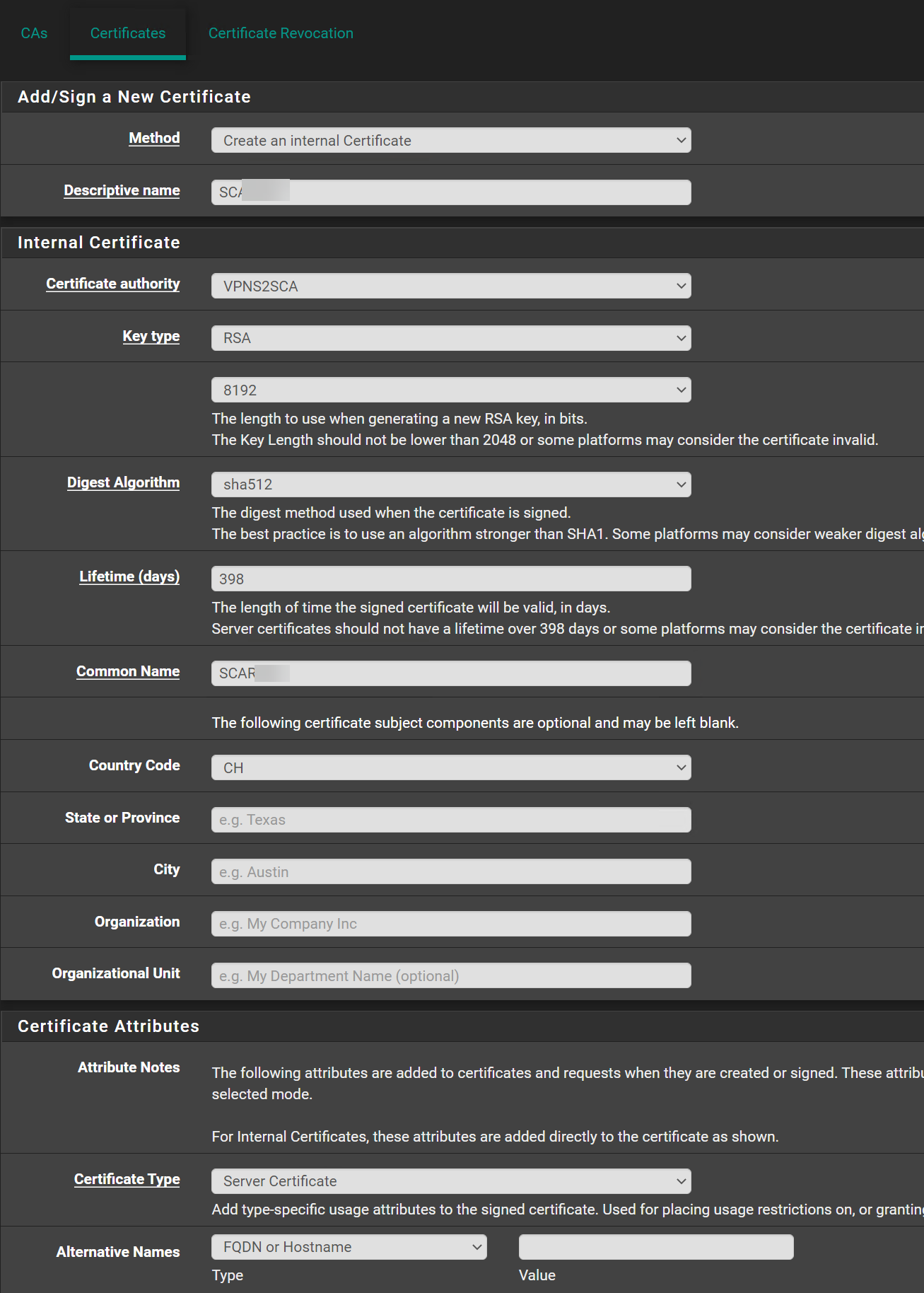
Client Certificate:
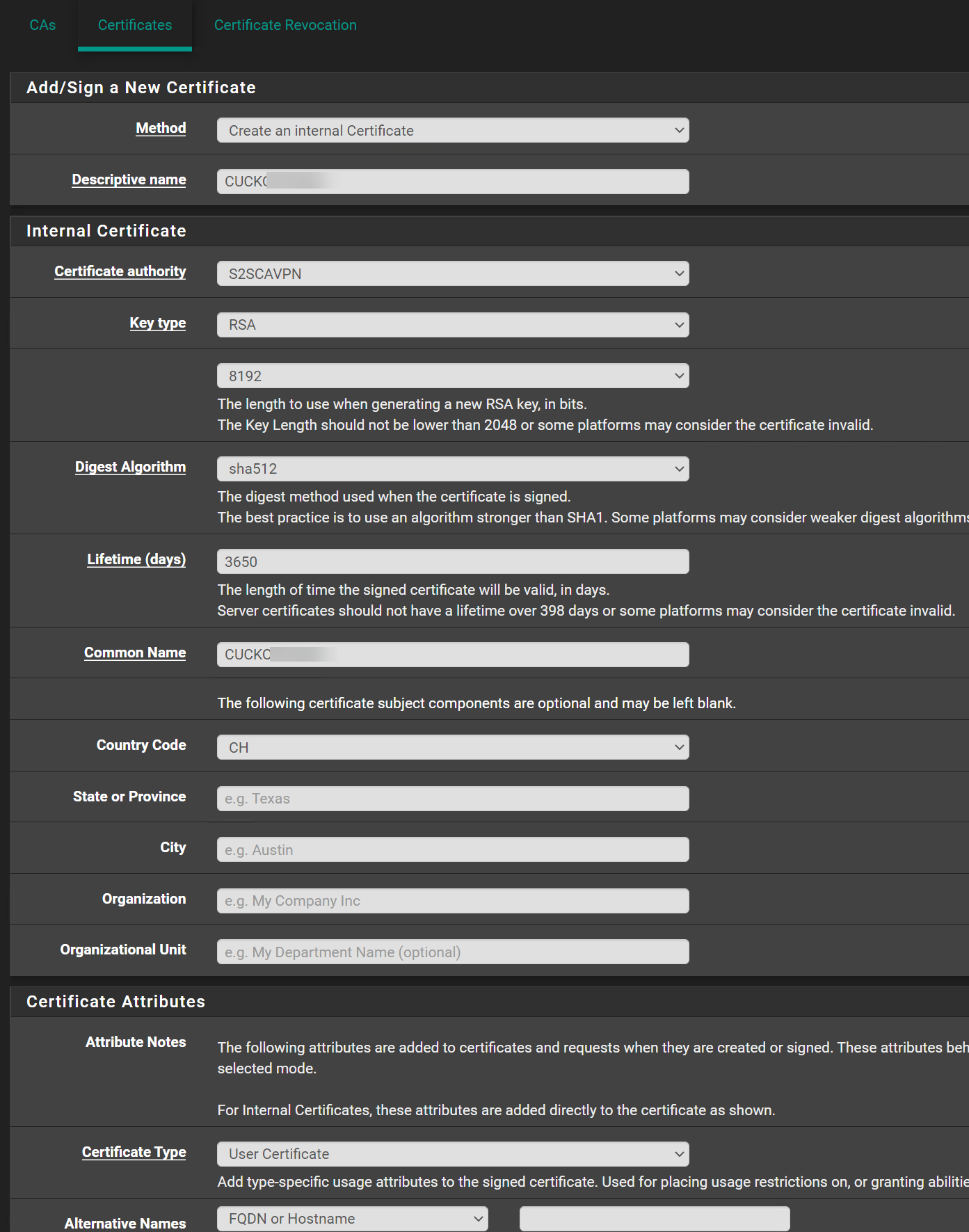
Is this fine like that?
-
@hispeed also - have the process widget on your dashboard - restart the openvpn server and client services manually after making changes like this. For some reason - mine requires that.
-
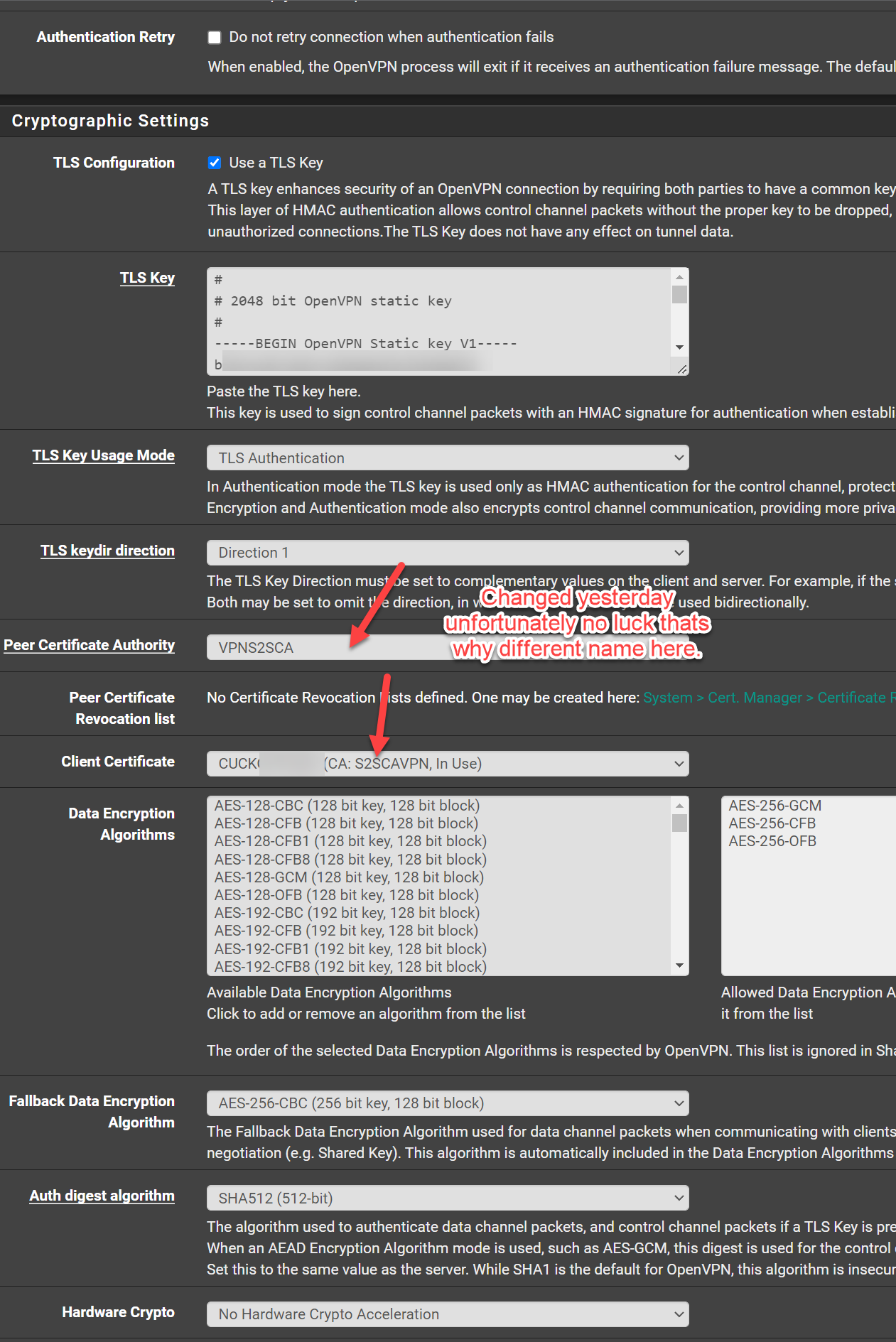
@swixo Oh here is a problem - you have TLS Auth+Encryption on the Server and TLS Auth only on client.
Those need to match.
-
I restarted the client and server, doesn't help. I also changed the TLS Auth on both side to TLS Auth only.
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 SIGUSR1[soft,tls-error] received, client-instance restarting
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS Error: TLS handshake failed
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS Error: TLS object -> incoming plaintext read error
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 TLS_ERROR: BIO read tls_read_plaintext error
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Aug 6 16:48:03 openvpn 71708 XX.XXX.179.XXX:19708 VERIFY ERROR: depth=0, error=unable to get local issuer certificate: CN=CUCKOXXXXXX, C=CH, serial=4 -
@hispeed Can you show your client override?
-
@hispeed
The client and server certificates are issued by different CAs.Both have to be from the CA you've selected in the server settings and copied to the client.
-
-
@hispeed
Is the CN from the Client? And these are both coming from the same CA / Copied from the Server to the client? -
@swixo Since its tough to see the certs because of redaction,
the general process I would follow:On Server:
Create CA. From the CA->Generate the Server Cert and the Client Cert. Make sure server bit set (on the server cert).Export the CA Cert (no key) to a file - and Import that to the client.
Export the Client .P12 file on the server, and import it to the Client.
Assign the certs in the server and client config. Pay attention to the CN in the override.
-
@swixo and @viragomann
It works finally. Thank you for this hint viragomann and also swixo. Boah i was so close to give up. My fault I took the wrong CA for the client certificate.
Stupid error i have spent several hours and recreated several times the certificates.....
Thank you and have a good weekend.
-
@hispeed Great! Another triumph!