Managed switch not distributing other VLAN addresses
-
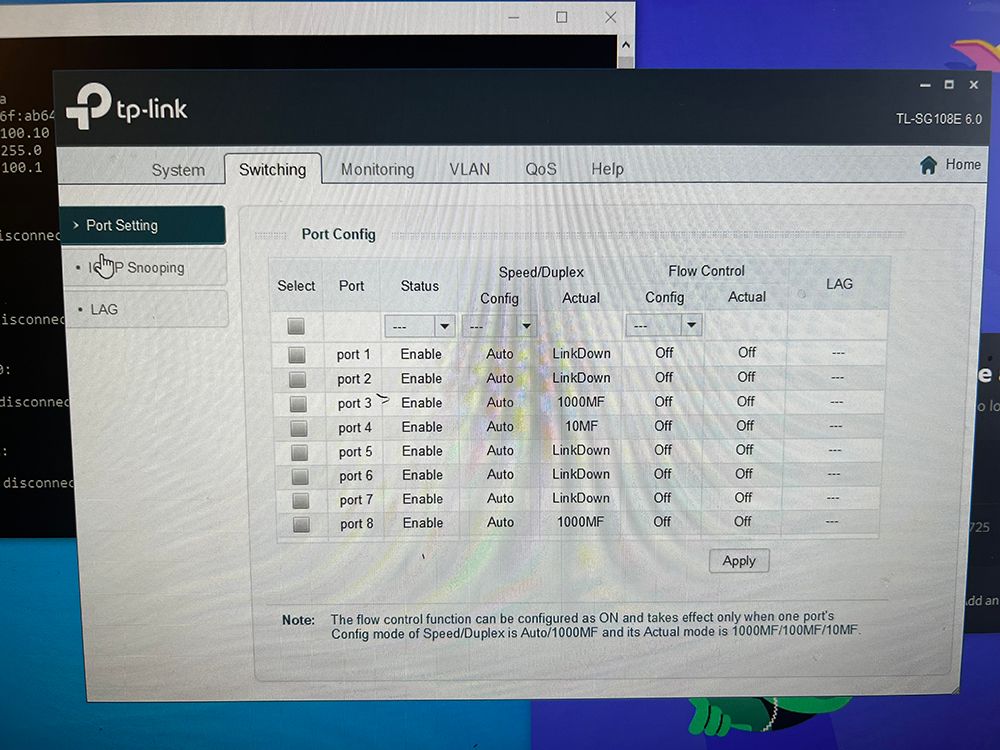
@jarhead I guess you mean these settings?
-
@mannenor nope.
Go back to your other picture. See where it says "802.1q vlans"?
That. -
@jarhead said in Managed switch not distributing other VLAN addresses:
picture. See w
Ah my bad.. I see I send the same pic twice instead of a different one this is the other one
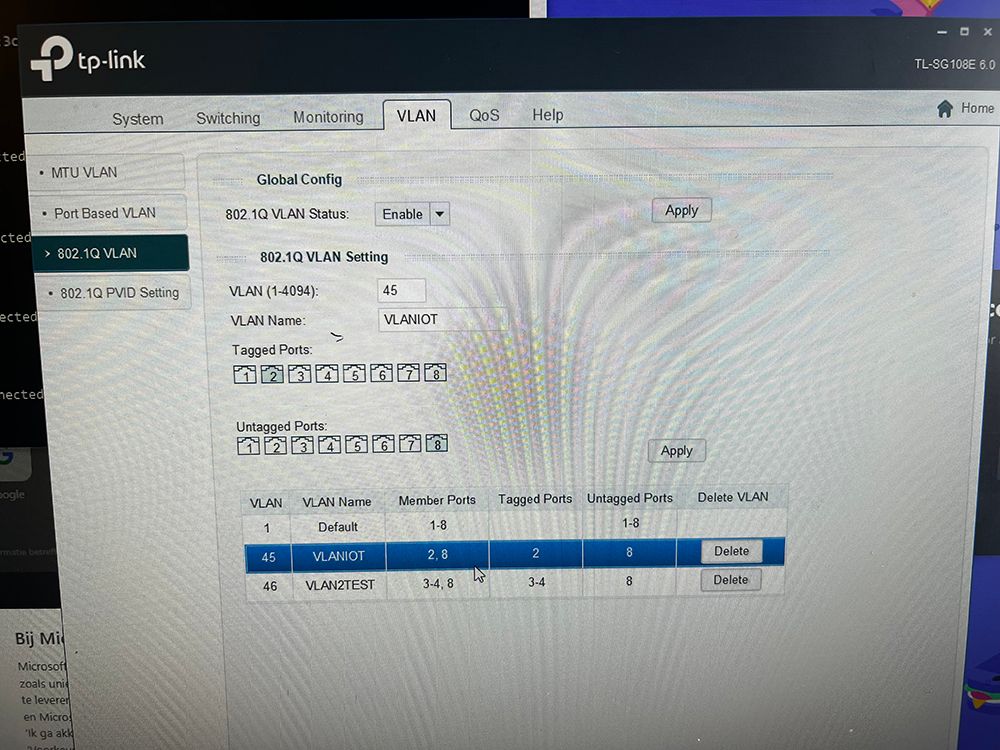
-
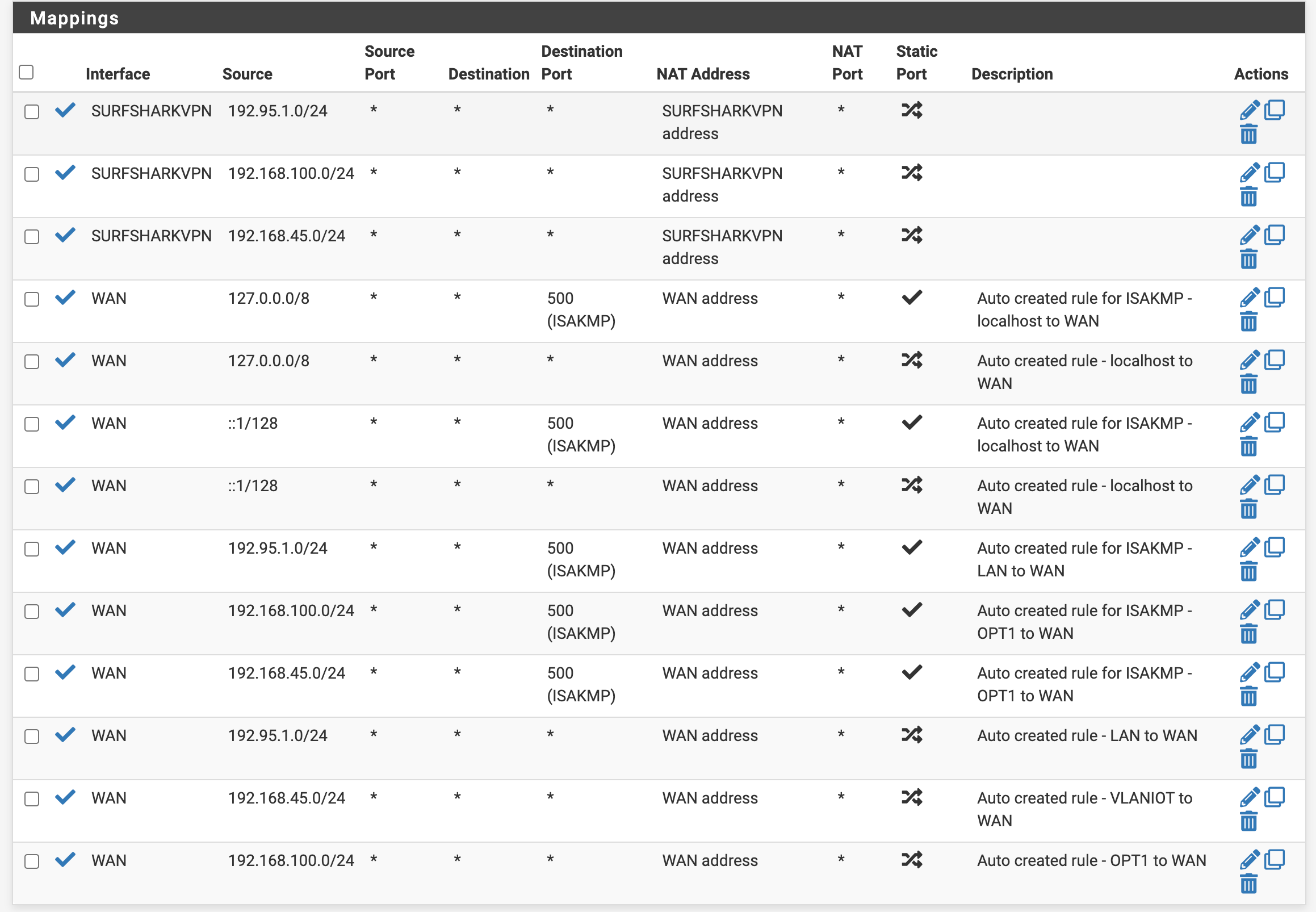
@mannenor You can not have more than 1 vlan untagged on any port.
You have vlan 1 on all 8 ports - now you also have 45 and 46 untagged on port 8.. You can only have 1 untagged on any port..
Your port 8 has 1, 45 and 46 all untagged... This is borked!!
-
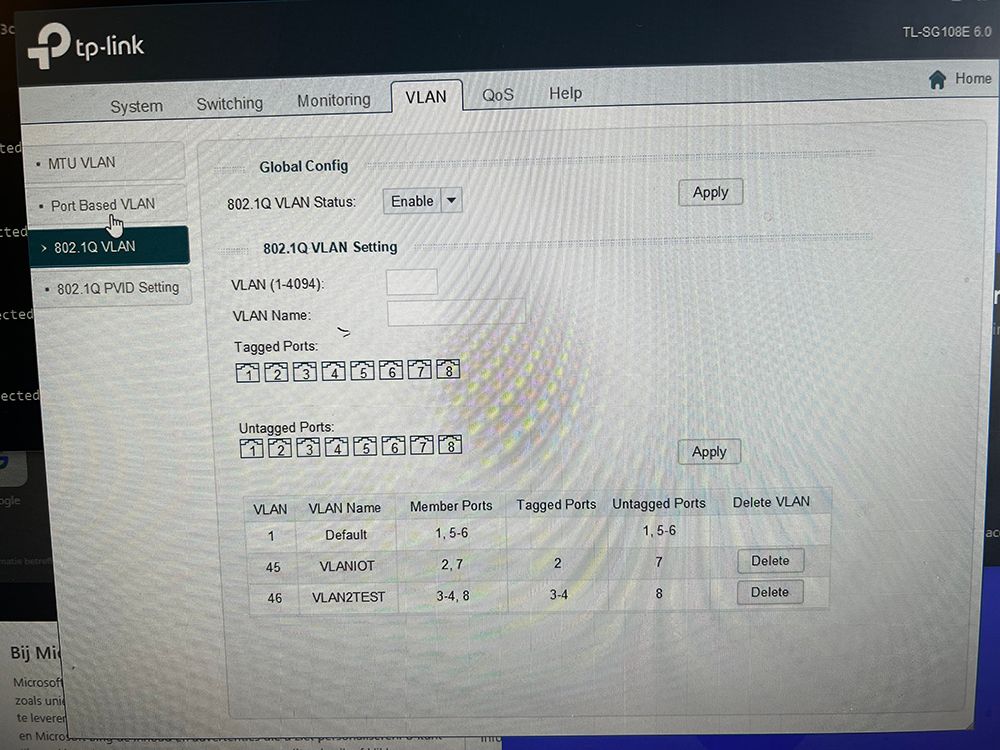
@johnpoz Ah, so like this it should be fine I guess? But I'm getting the wrong lease and not the correct subnet when I change it like this. it Places me on a 169.254.. network and not the 192.100.. that I want.
What issue could it be the reason why it's not doing what I want in this case? I have copied the lan rules from my other VLAN's which do work.
Thanks in advance!
-
What is not giving you the IP you want?
169.254 is indication that a dhcp client could not talk to a dhcp server.
So you removed vlan 1 from port 8, but your previous post showed the pvid on port 8 as 1, etc..
And you have port 7 in vlan 46 as the pvid, even though its set for vlan 5 as untagged..
-
@mannenor You have all kinds of issues here.
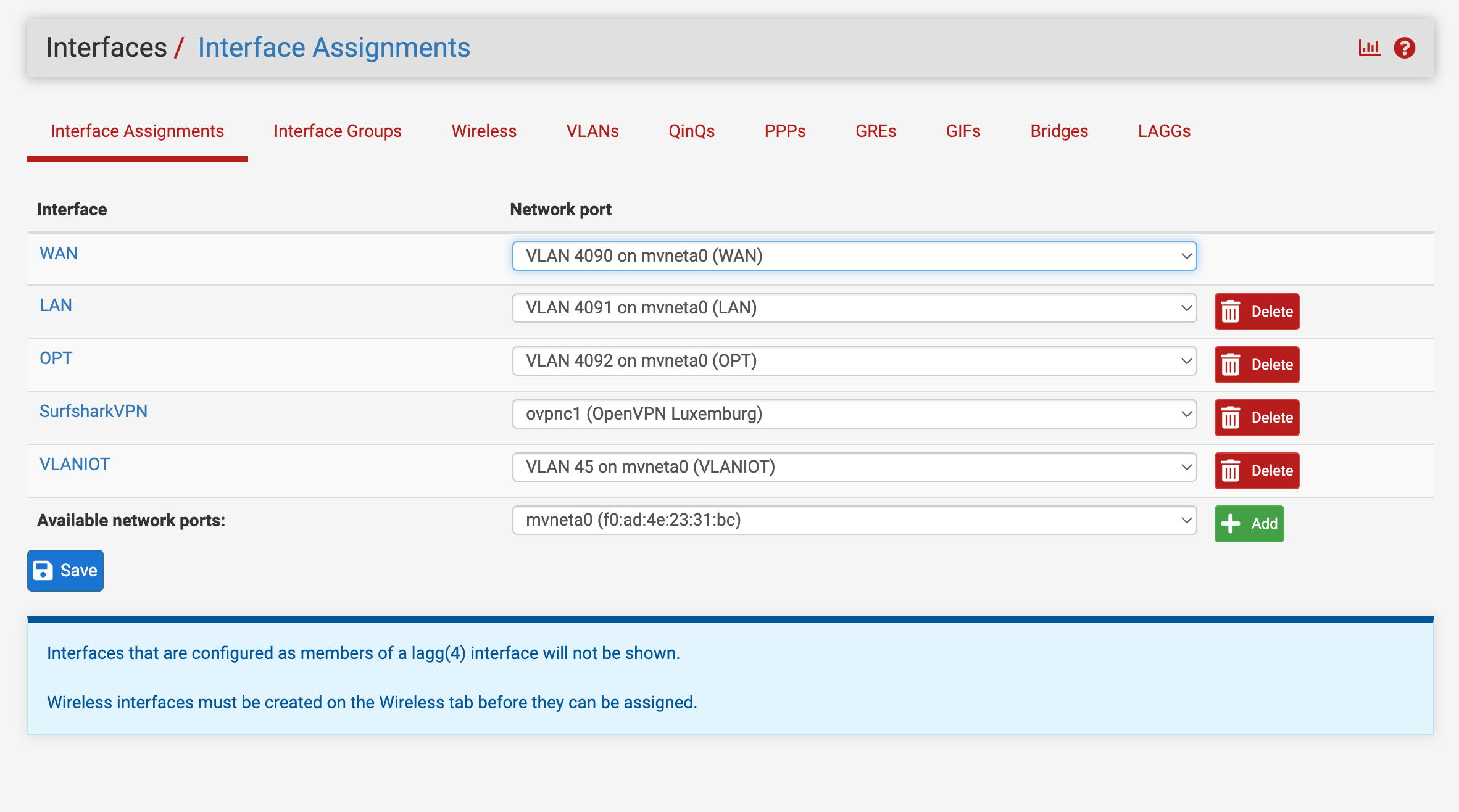
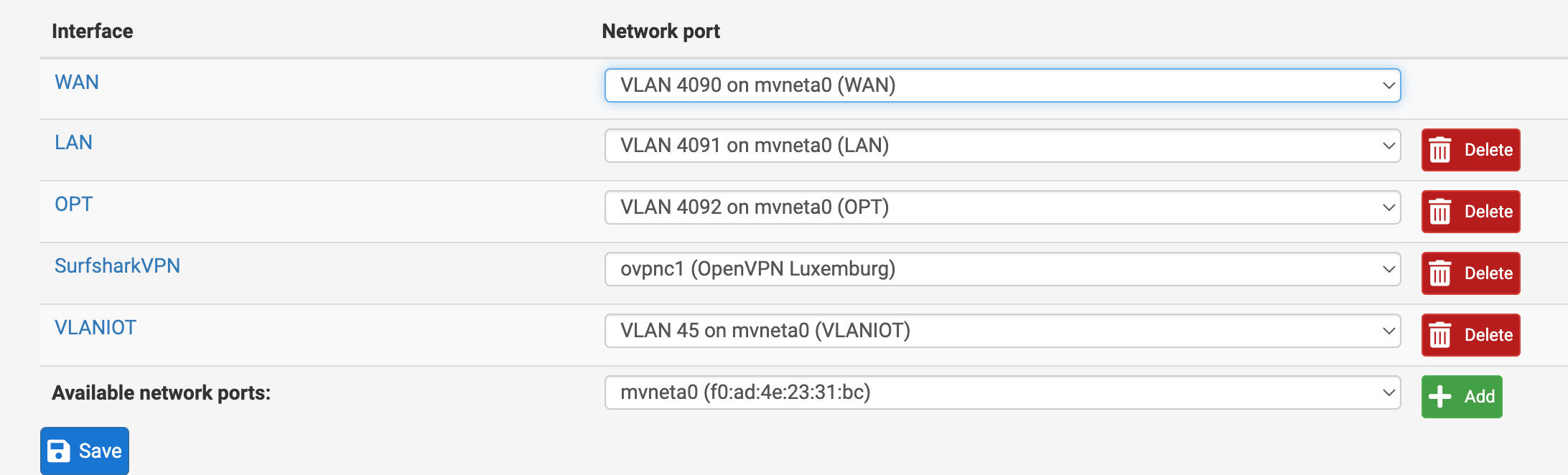
What port is going to your pfSense?
You said 8 I thought? But that port isn't tagged anywhere. You need to tag all vlans going to pfSense on that port.
Then you have ports tagged that should be untagged.
Don't tag a port connected to an end device (ie PC's etc.)Next, port 7 is untagged in vlan 45, but you have the pvid set to 46. Change it to 45.
Judging by what you said you want, you should have port 8 as the only tagged port, carrying all 3 vlans.
Fix that stuff and test.
-
@jarhead said in Managed switch not distributing other VLAN addresses:
Don't tag a port connected to an end device (ie PC's etc.)
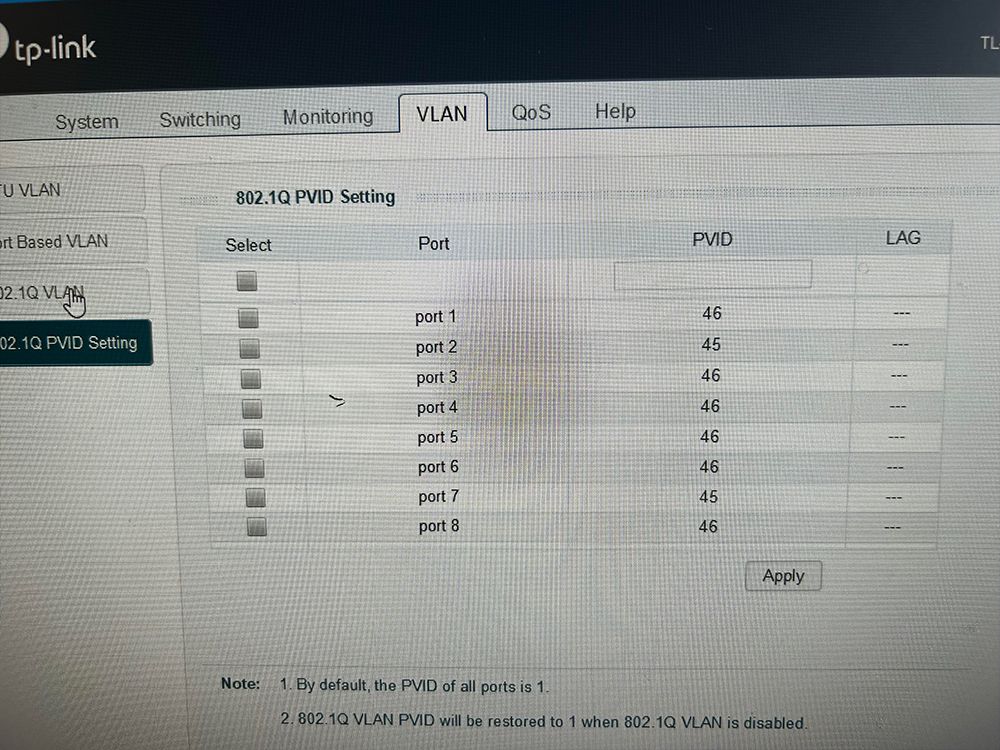
This is what I have now and I was actually testing the ports on my windows pc where I am also setting up the routing on my VLAN's with the TP Interface.
So I need to have a switch between the VLAN or it won't work? I guess that might be the problem than. I do have internet now again but it's still going through the OPT exit.
The OTP port from my firewall netgate goes to port 8 on my TPLink Switch. And now currently I am testing on port 3 to reach the .46 interface aka VLAN 46.
-
That depends on how old the switch is. Some with the problem can be updated. Some, such as my AP, are too old. So, first thing is check for an update and see if the problem continues.
-
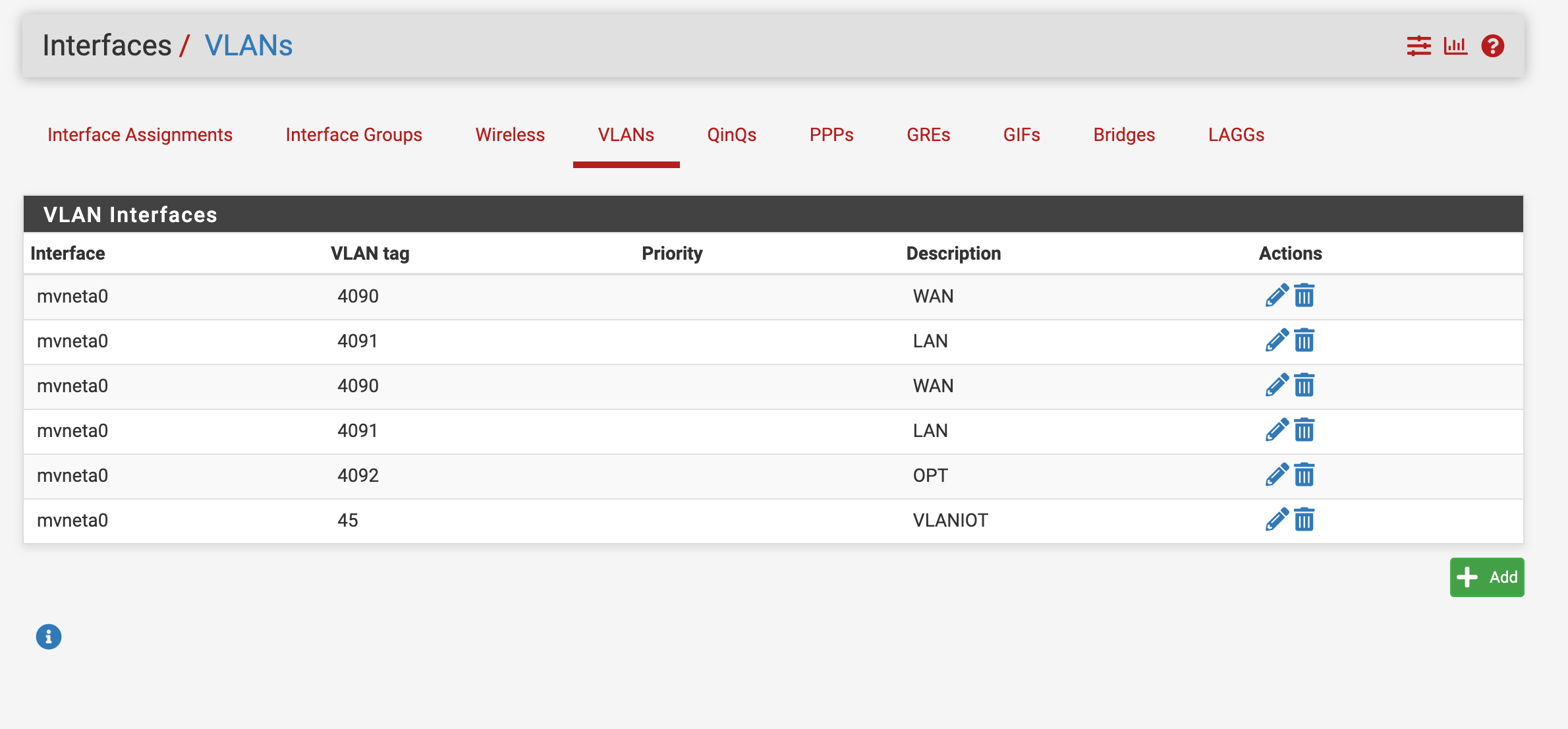
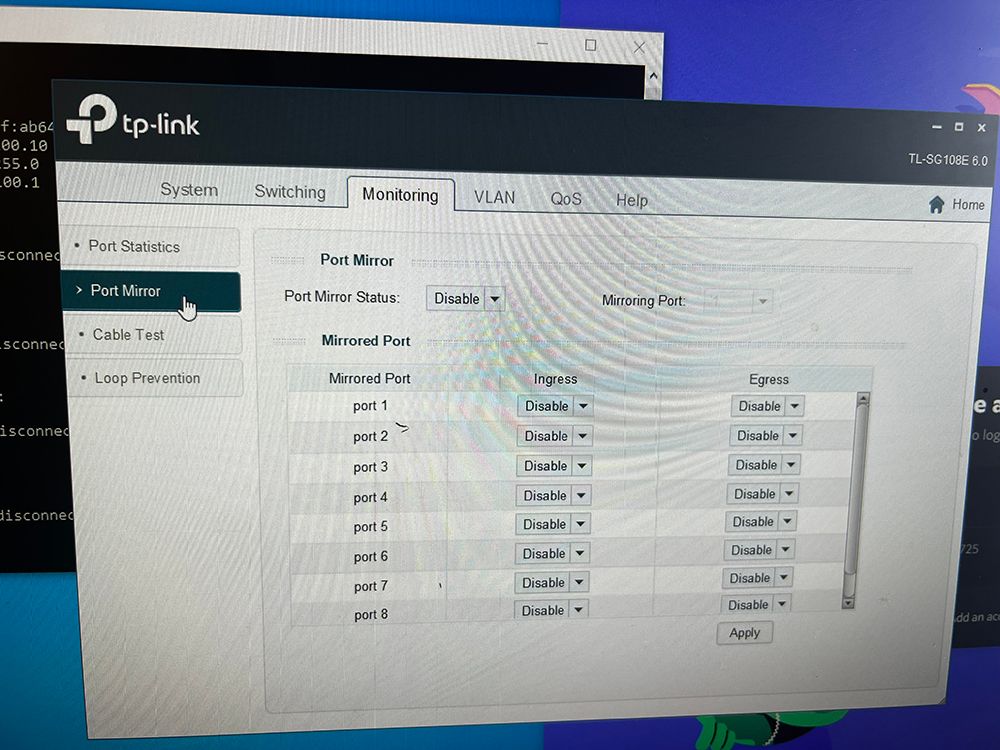
@jknott TL-SG108E is a new switch I recently bought last week..
-
@mannenor what a cluster you have..
You have all your ports pvid set to 45 and 46, yet the only ports you have in 45 and 46 untagged is ports 7 and 8.
Clearly you do not understand what a PVID is..
This is the vlan the switch will put traffic coming into that port that has no tag.. So from what you posted untagged traffic coming into port 1, 5-6 are going to be in vlan 46
From your last posting 1,5 and 6 would have a pvid of 1. 7 would have 45 and 8 46.
Not exactly sure what your doing with port 4, you have 46 tagged it..
What exactly do you have plugged into what on this switch?
-
What exactly do you have plugged into what on this switch?
Agreed.
@MannenOR
Post a drawing of what you actually want, topology"wise", and we can help you.
As is, you're making a mess as we go.You need a trunk port going to pfSense. Tagged with all vlans.
All other ports will be untagged with the vlan that you want the device plugged into that port on.See if you can do that.
-
@jarhead So What I am trying to setup I have drawn over here. The NetGate Firewall goes to the managed switch, from there it goes from PORT 8. And I want my VLAN to work on outgoing Port 3 so that for the unmanaged switch, all devices will be on the VLAN45.
Thanks for your time anyway guys I appreciate the help!
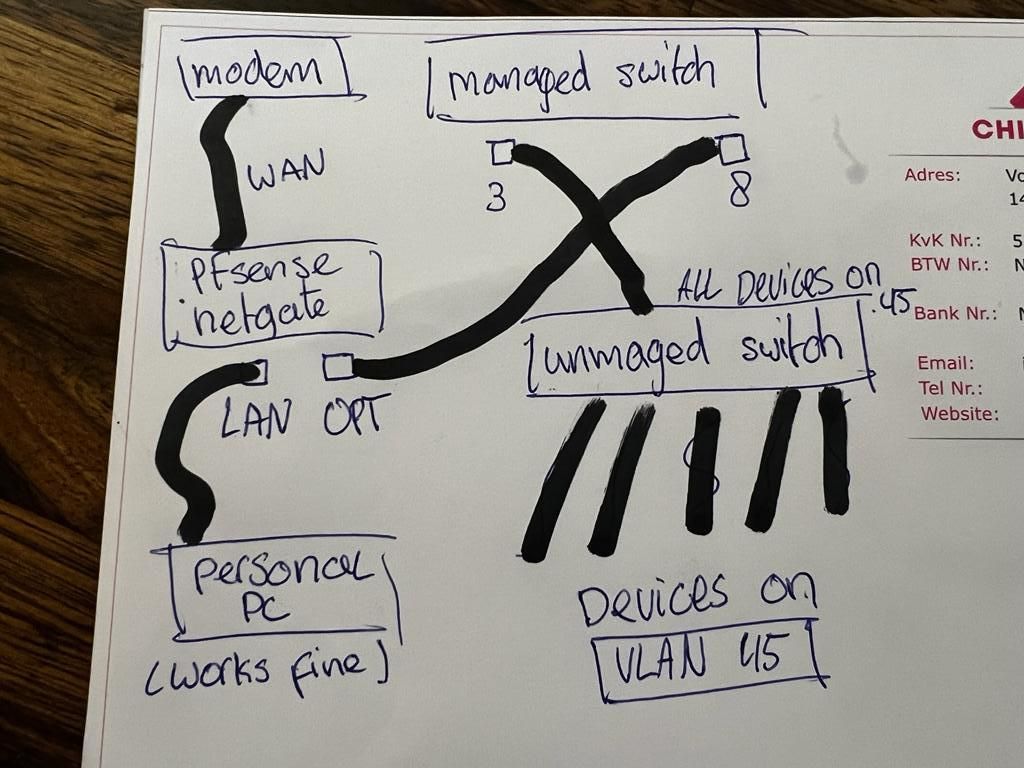
-
@mannenor So all you want is one network going to the OPT interface??
Why use vlans at all? Just assign the address on the interface itself. -
@jarhead For now yes for testing purposes. After that I want to set up multiple VLAN's for my guests, Smart Home IOT network, Cameras and personal.
-
@mannenor what network is 192.95.1/24
Why are you using this? That is a public range, use rfc1918 on your networks..
Your example as already mentioned is just 1 network.. no tagging needed..
Are you going to run an untagged (native network) on this interface.. Is that going to be your vlan 45 on your switch? 192.168.45/24?
And then what you want another vlan 192.168.46/24 that will ride this same physical connection from opt interface on pfsense to port 8 on your switch.
-
@mannenor said in Managed switch not distributing other VLAN addresses:
@jarhead For now yes for testing purposes. After that I want to set up multiple VLAN's for my guests, Smart Home IOT network, Cameras and personal.
Yeah, there's no need to test, it'll work.
Plan what you want and do it.
"Piece mealing" it will just cause frustration down the road.
Best advice, use OPT interface as a trunk port. Meaning don't assign an IP to it.
Then add the vlan 45 and 46 to it. Assign them as interfaces. Give them IP's.
After that, pfSSense will have both vlans on the OPT port. Connect that to port 8 of the switch.
Tag that port with both of those vlans. Untag port 3 with vlan 45. done. -
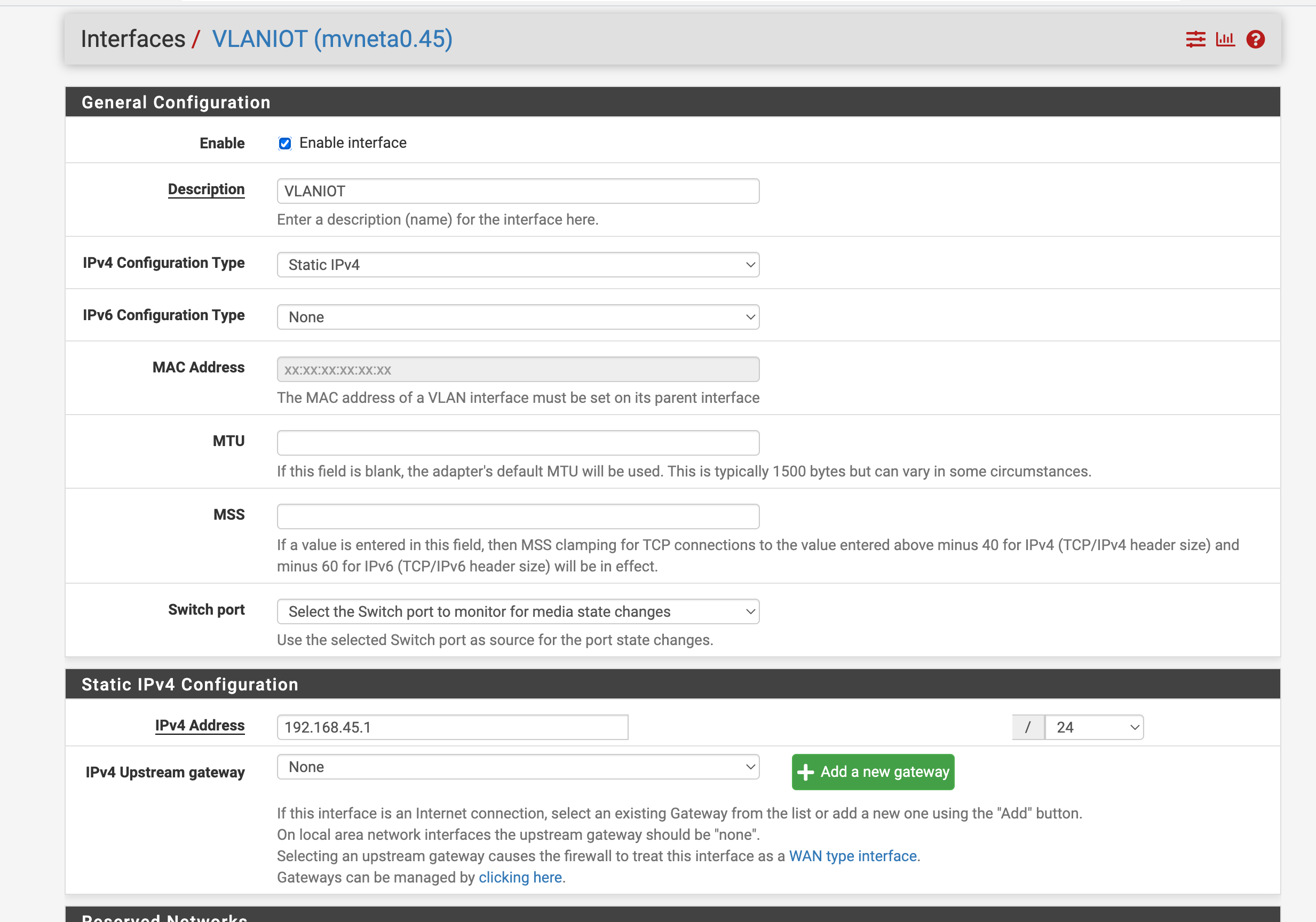
@johnpoz 192.95.1/24 is the main setup for my PFSense Firewall and also the LAN. The OPT1 has a VLAN attached to it. I want indeed VLAN45 on 192.168.45/24 for the unmanaged switch.
And later I want to add the .46/24 network to a different switch which I still have to buy but I want to have .45/24 working first so that I know what I am actually doing is working..
-
@mannenor said in Managed switch not distributing other VLAN addresses:
192.95.1/24 is the main setup for my PFSense Firewall and also the LAN
And that is a horrible choice - where did you get the idea that you should use that address space? Are you "University of Salford" in the UK?
Well I would just put your 192.168.45/24 native on the port on pfsense..
This is untagged.. And will be the pvid on port 8.. And port 3, and port 3 and 8 will be in vlan 45 untagged.
Now put 192.168.46/24 as vlan on pfsense same physical port and it will be tagged 46.. Now added port 8 46 tagged.
Now put some other port on your managed switch say port 7 in 46 untagged, pvid 46... plug in a laptop - there you go on vlan 46.
-