Suspicious Traffic?
-
@deanfourie I don't see any states to that 8. address.
So pfsense didn't create, nor did a client create a connection to there.. Do a simple filter on your state table for the IPs in question.
If you do not see any states then pfsense did not create the connection, nor did a client behind pfsense.
And what you could be seeing could be SA scan, that is being interpreted wrong???
But if your concerned that pfsense, or something behind pfsense is creating connections to somewhere it shouldn't be - look in the state table.. If a connection attempt was made from or through pfsense then a state would exist. Even if the connection was not established.
Here - trying to ping one of those IPs.. Even though not getting an answer, you can see the state in the state table from pfsense
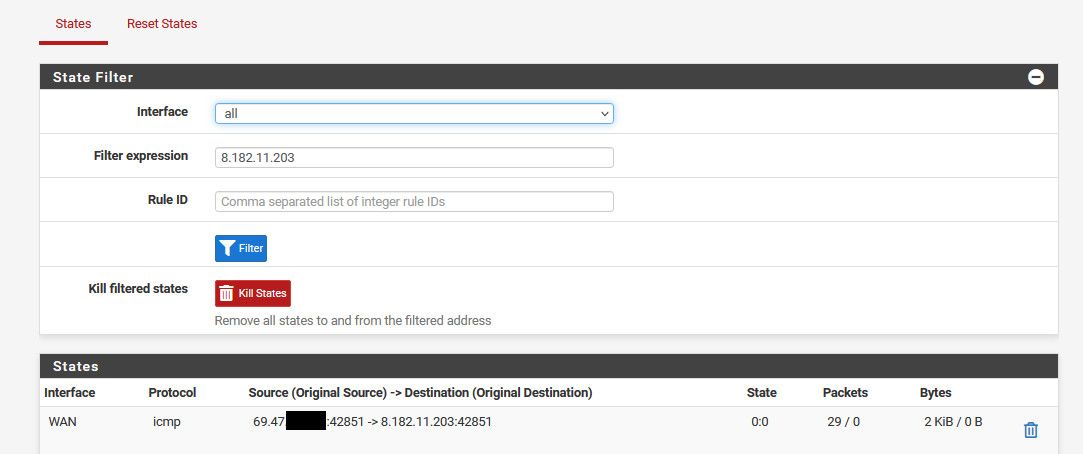
-
@johnpoz Ok great ill do this.
I hate working with upstream gateways and double natting, would much rather put the router in bridged mode and get WAN IP from DHCP and boom! Last time I did this I was on the naughty list with the ISP. They warned me
I will do more careful watching of the state table. My concern is actually with the 4G router still though,
If its doing some sort of dodgy proxying at the 4G router, I'm not going to be able to see that from pfSense WAN side as its before the WAN interface.
I mean at the end of the day, it is a Huawei router...
I cant even disable TR-069 on it, nor can I change the LAN subnet mask.
-
If you're concerned about it the only thing you can really do is tunnel all your traffic through it so the router never sees inside it. There is obviously overhead to doing that though.
Steve
-
@stephenw10 I originally was routing all traffic through a VPN, however I got so many more weird connections as a result.
One question I do have is, would doubling NATting effect the results of the flows in ntopng.
Like matching ports and applications etc?
Thanks
-
No I wouldn't expect it to. The source/destination ports/IPs that ntop can see are still the same.
-
@stephenw10 said in Suspicious Traffic?:
No I wouldn't expect it to. The source/destination ports/IPs that ntop can see are still the same.
Thank you
-
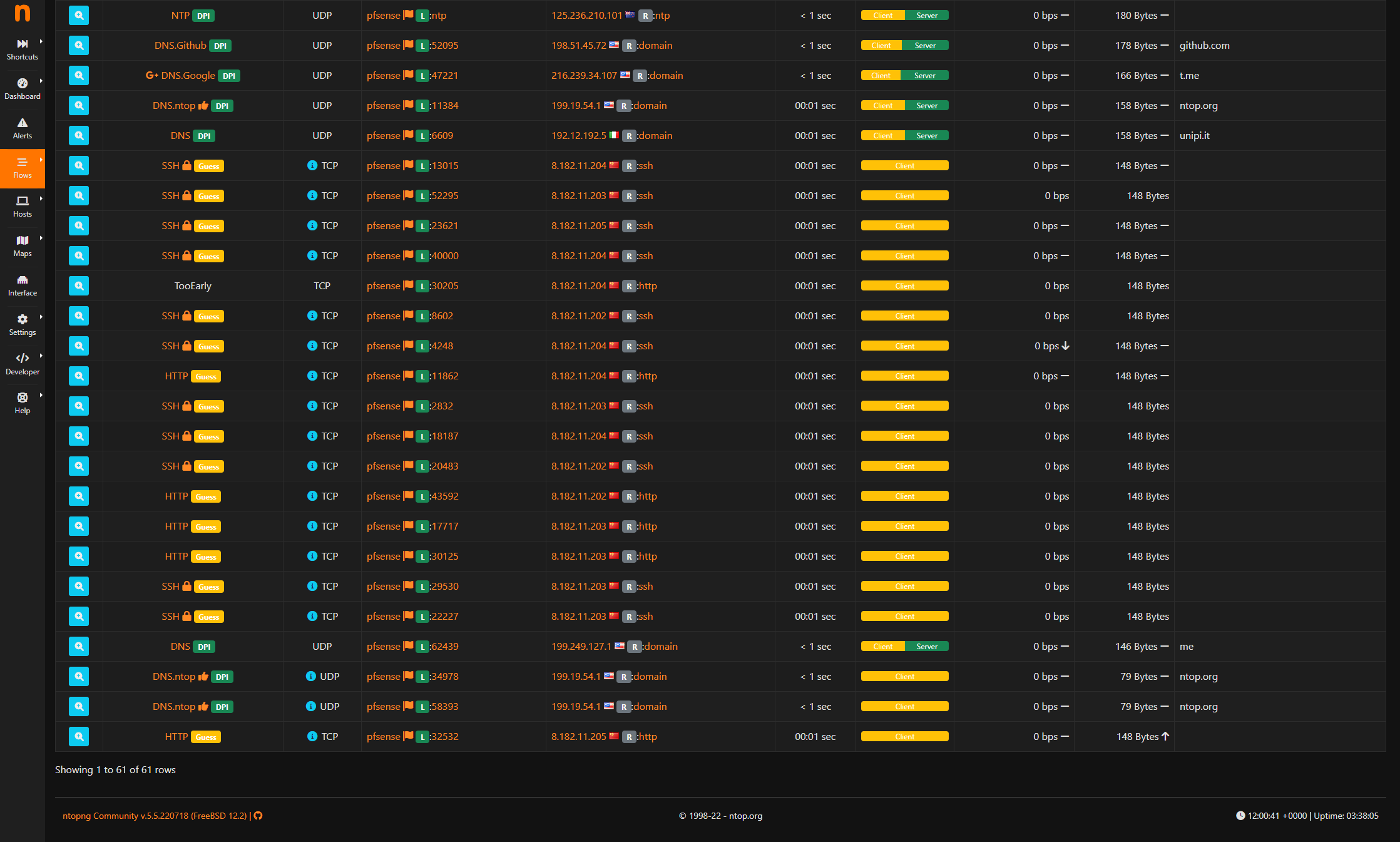
Maybe someone could take a look at this capture. Lots of SSH from 192.168.8.2 which is my pfSense firewall.
Also a lot of TCP retransmissions. I'm not sure how my pfSense could be sending out SSH traffic?
-
@deanfourie pfsense out of the box would not be doing any ssh outbound..
You would see retrans when you send a syn and you don't get an answer..
Did you look in your state table for those IPs to what behind pfsense might be trying to talk to those IPs.. Looks like Ips on your ISP network.
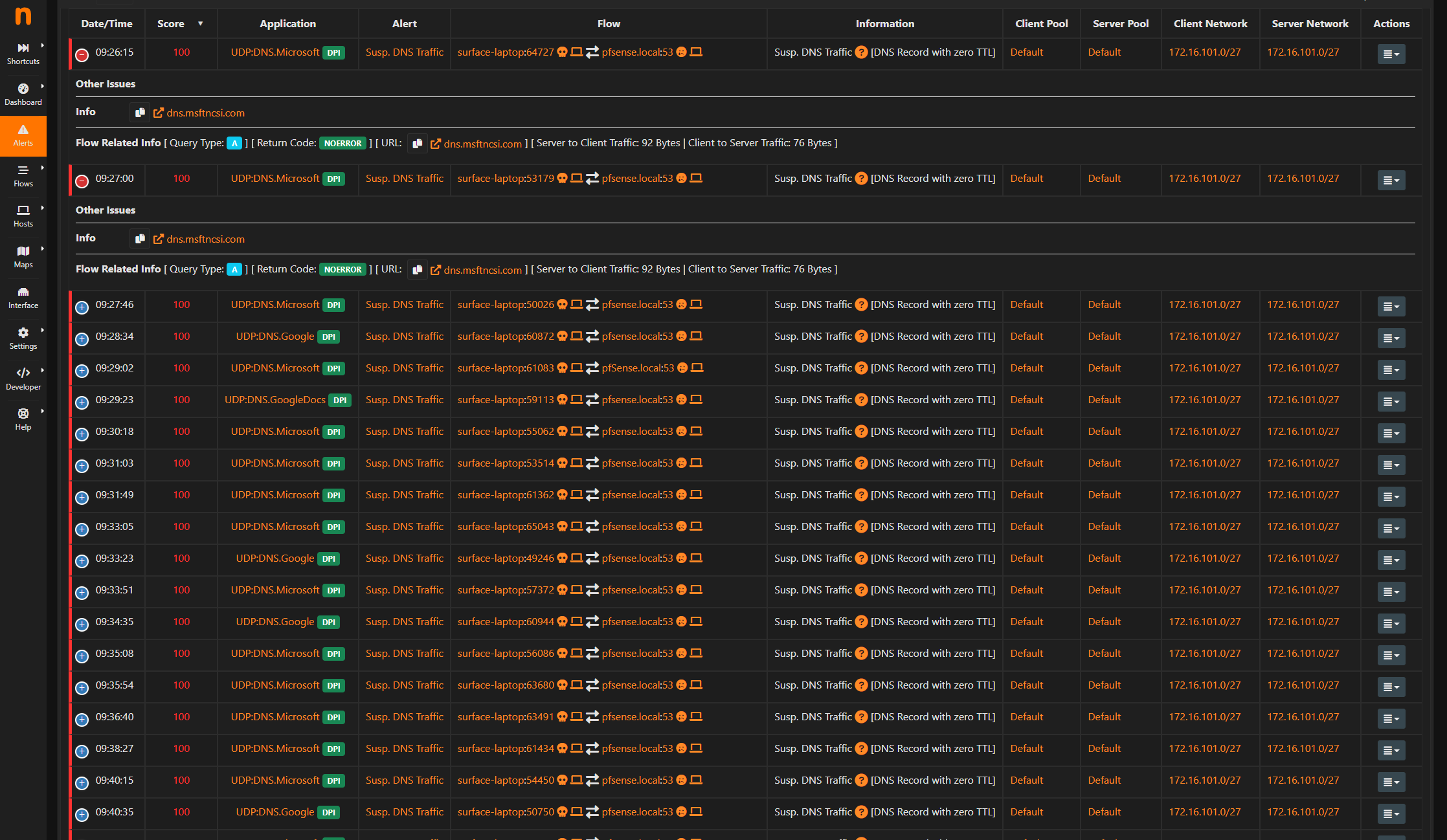
;; ANSWER SECTION: 22.239.24.86.in-addr.arpa. 86400 IN PTR cpc152131-stkp13-2-0-cust21.10-2.cable.virginm.net.Dude do you have Ntopng running in discovery mode on your wan?? That would for sure freaking do it..
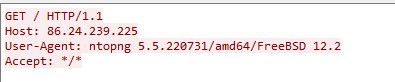
-
@johnpoz Heres what I found in the states table.
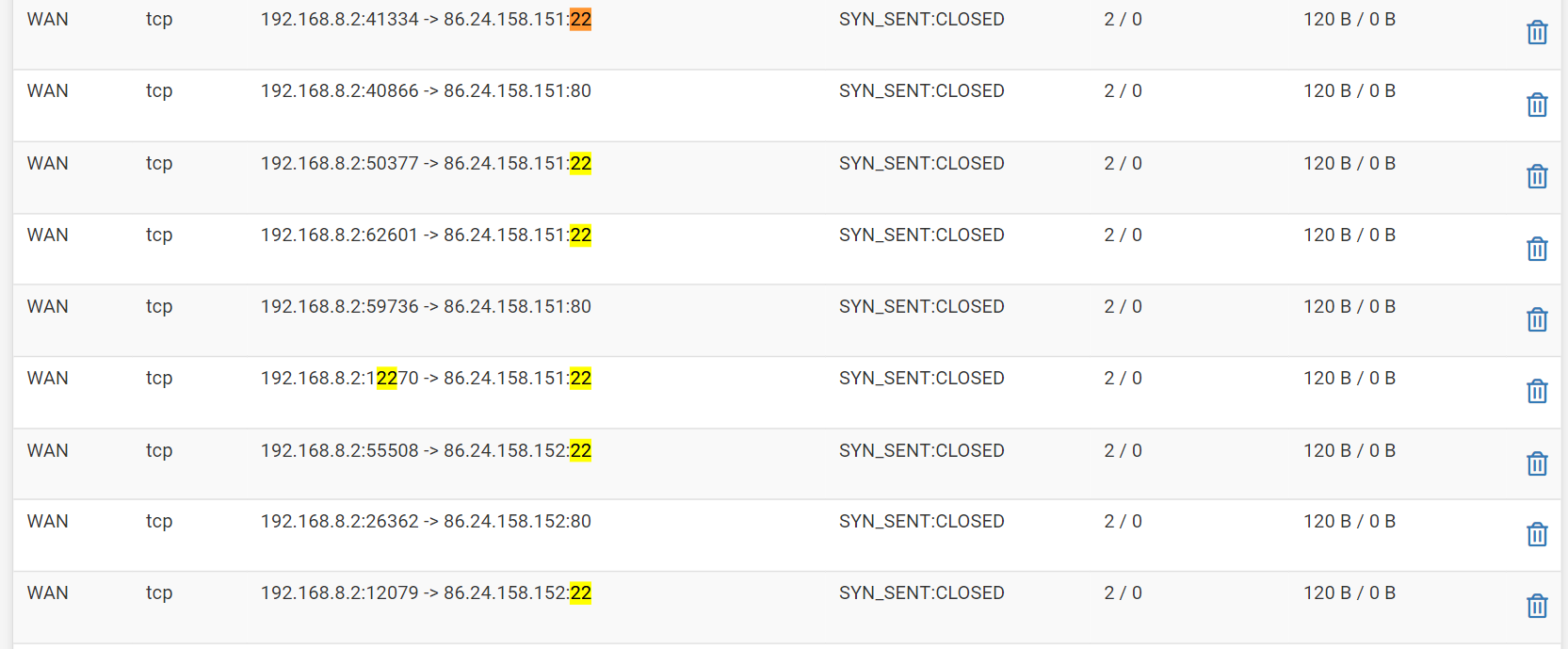
-
@deanfourie Dude stop having ntop try to discovery your wan.
-
@johnpoz oh that's not ntop that's the states table.
-
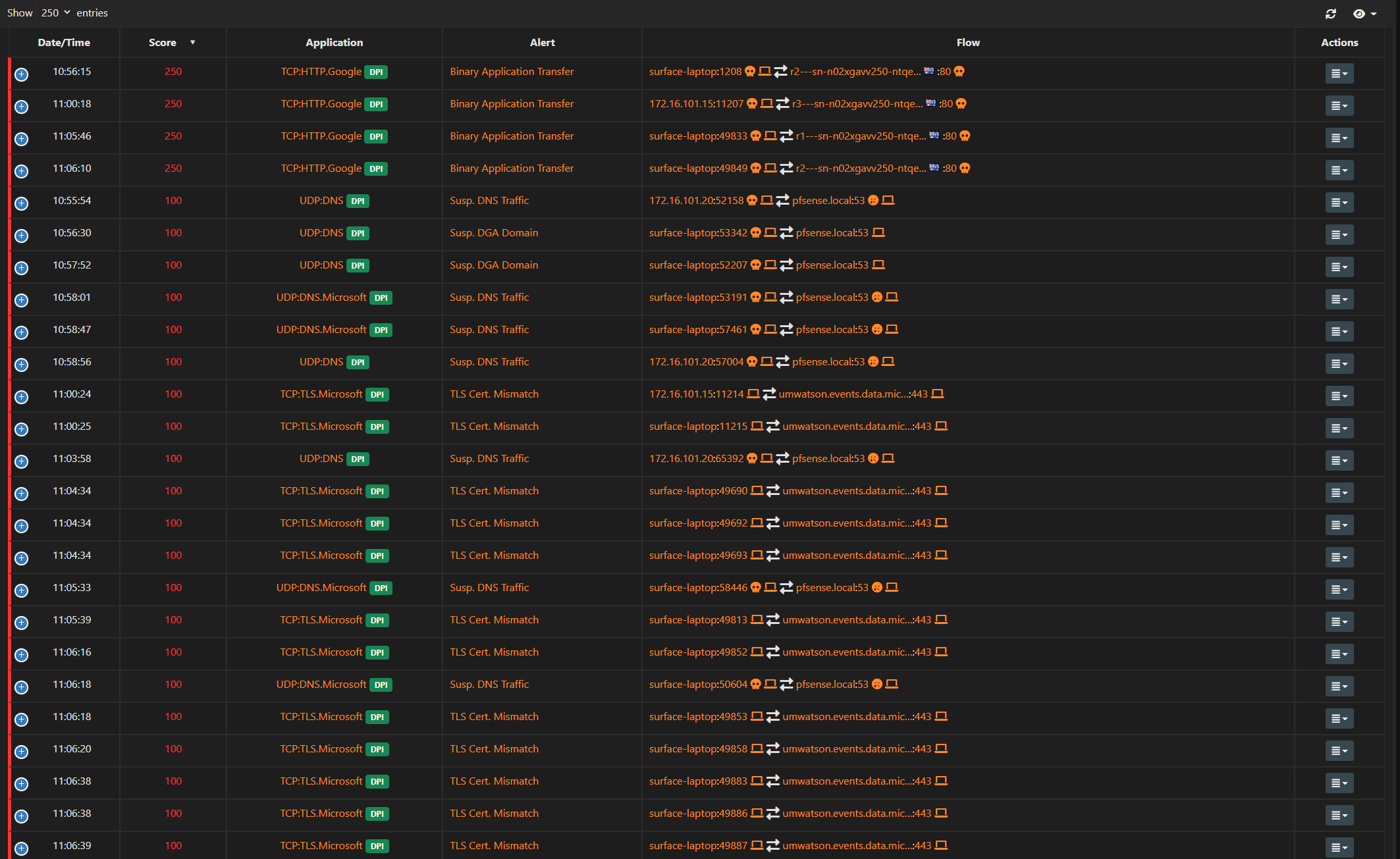
@deanfourie Again the only thing that would do what your seeing is ntop in discovery mode.. Turn it off and that traffic will stop..
Its not suspicious traffic - its ntop in discovery mode..
Why you would have it trying to discover your wan what is causing that traffic.
-
@johnpoz so you're telling me that ntop is creating these outbound ssh connections?
-
@deanfourie Yes - its discovery mode.. Is looking for stuff.. ssh (port 22) being one of the things it looks for.
Here is a recent thread - same sort of thing
https://forum.netgate.com/topic/172680/ntopng-sshguard
Here is the code from the ntop
https://github.com/ntop/ntopng/blob/dev/scripts/lua/modules/discover_utils.lua#L495
-
@johnpoz but would it not see this traffic only if this traffic existed? Hence why it's seeing it
I don't know what am I missing?
-
@deanfourie its creating it!! Turn off discovery!
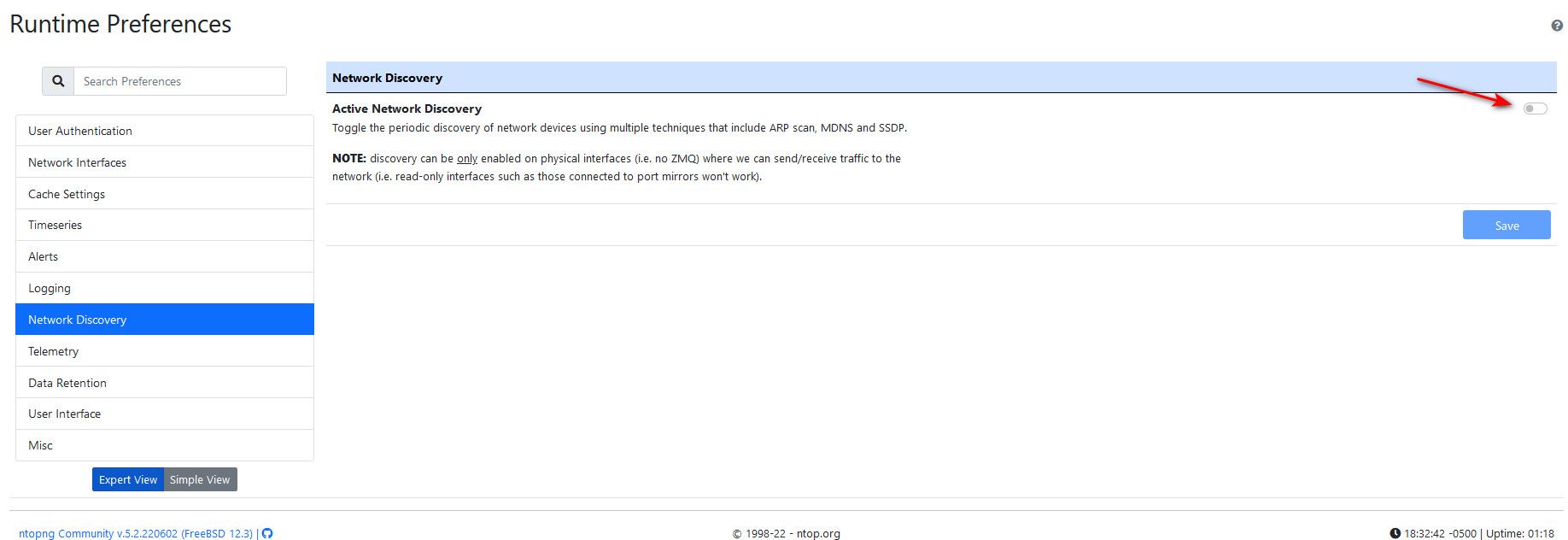
Ntop is creating the traffic - so yes you see it
Or uncheck ntop from using your wan.. There is little reason for ntop on your wan. You wan to see where your clients are going - not all the noise hitting your wan.
-
@deanfourie dude, my WAN is a upstream gateway, is is simply another private network as far as ntop is concerned.
The fact is I'm seeing SSH traffic from my pfSense WAN interface, and seeing the connections in the pfSense states table.
How's that normal?
-
Because ntop is sending them to try to detect hosts on that subnet. That's what the active discovery does.
-
@deanfourie I have no idea what else to tell you - ntop is creating that traffic, its not suspicious.
If you don't want it doing it, then turn it off from doing it, if you want your ntop discovery your isp network - have at it, they might not be happy about that, or your isp other users, etc..
Why don't you turn off the auto discovery I showed you - do you continue to see this traffic?
-
@stephenw10 but the connection is to a external IP?