Gre tunnel to protect IP.
-
Hello, I created a gre tunnel as shown below. I wanted the machine with the ip 192.168.1.10 to have the public ip not mine but the ip of the protected wan. The Gre tunnel is already created and the pfsenses communicate but the public ip that is protected is not in the vm. I've tried putting static routes but it didn't work, I think I may not have created the static routes correctly.
I appreciate help
Compliments
Tiago Serra
-
You need a policy based routing rule for 192.168.1.10 to force all it's traffic across the tunnel:
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.htmlSteve
-
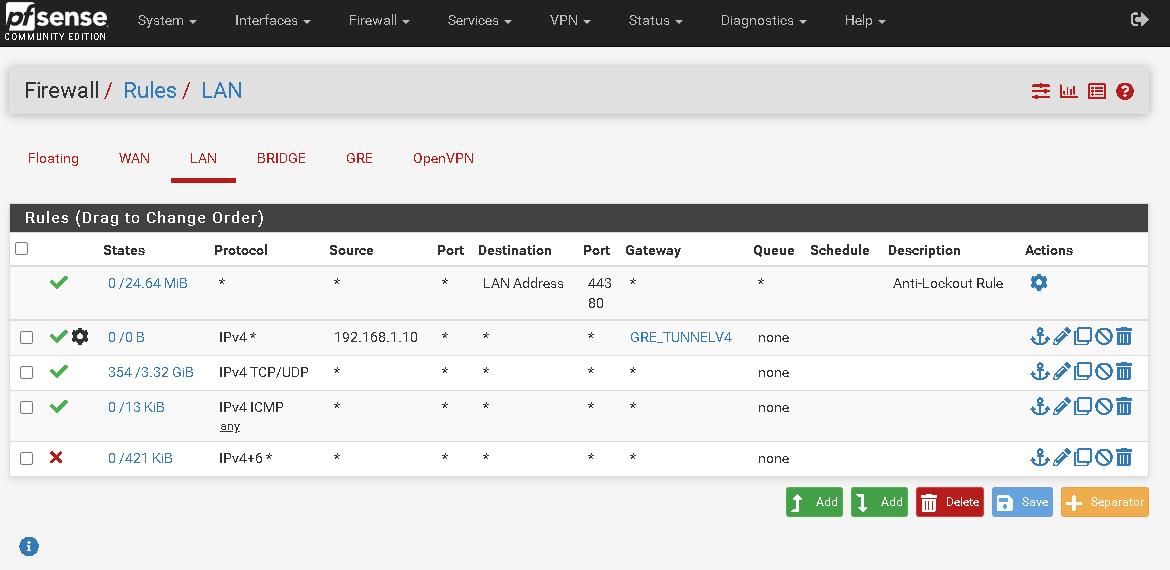
I added this rule but the traffic continues to go out through my gateway.
-
You will have to clear any existing states. You can see that rule has not matched anything yet.
-
This post is deleted! -
It is, but the machine has no internet connection.
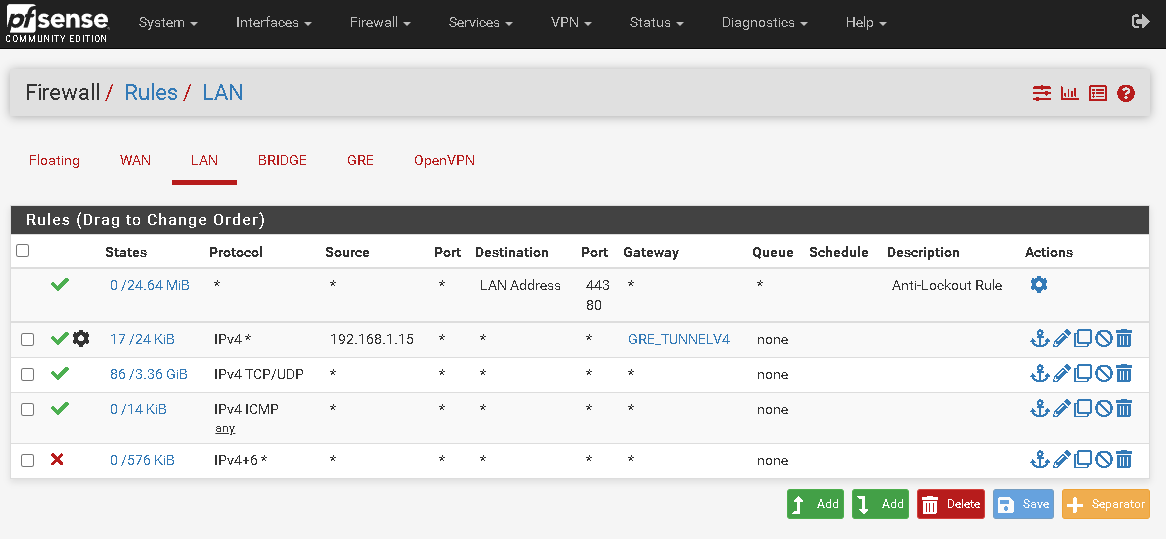
-
Is the traffic going over the tunnel though? Do you see states on the GRE interface?
You probably need to add a manual Outbounf NAT rule at the other end if you don't have a static route back to 192.168.1.0/24 there. Check the states at that end to see what's happening.
Steve
-
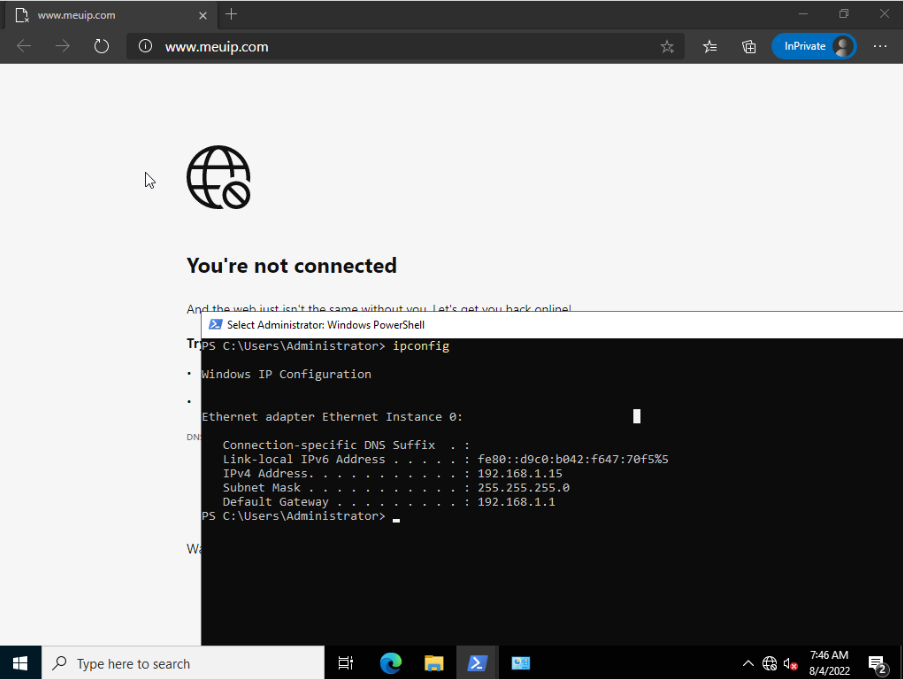
The machine ping the other side
just don't have internet
Do I check the states in my host pfsense?
-
Yes, because it's probably not Outbound NATing the traffic. Add a rule for that.
-
In my host's pfsense? What rule do I set?
-
Yes. Check the states at the remote side and see if traffic is leaving the WAN without NAT. If it is switch Outbound NAT to hybrid mode and add a rule to cover it.
-
These are the remote host states
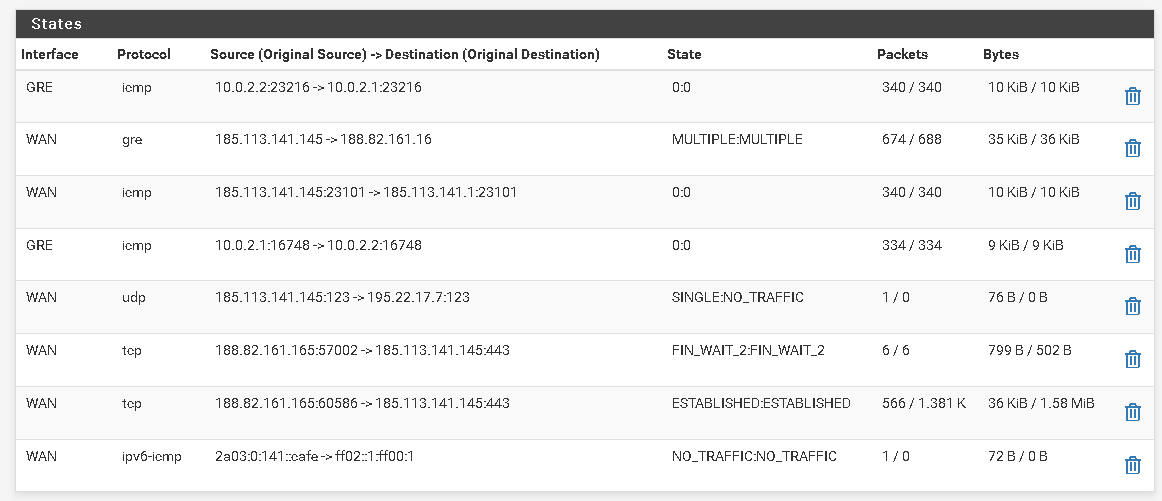 @stephenw10
@stephenw10 -
You need to start a continuous ping from 192.168.1.15 so you can see where it's opening states.
-
I ping the local machine to the remote tunnel
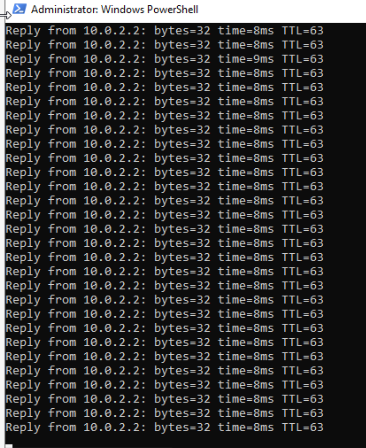
These are the states on remote pfsense with continuous ping on the local machine

-
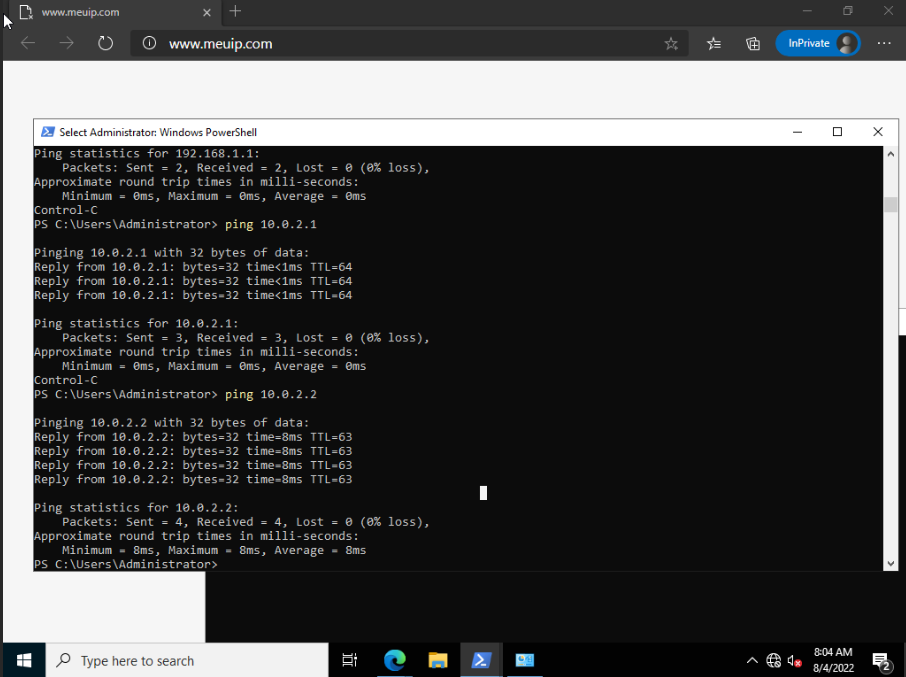
You need to ping from 192.168.1.15 to something external like 8.8.8.8. Then look at the states it's generating at both ends.
-
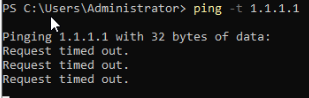
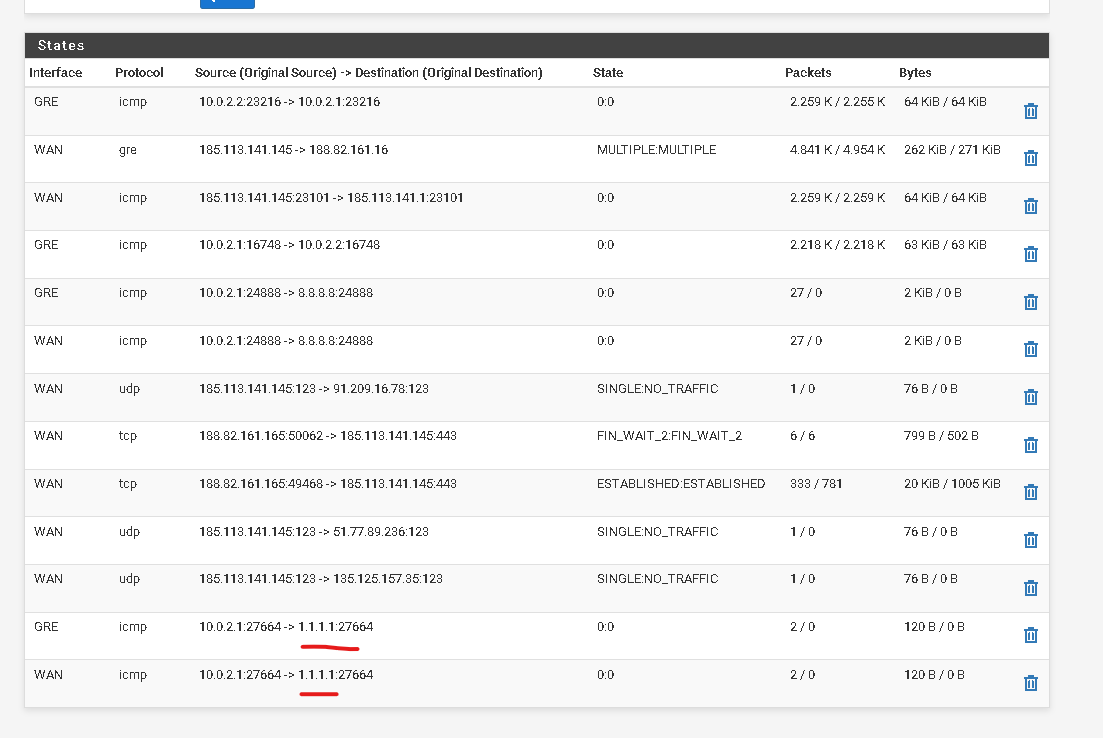
This is how the states are with the continuous ping for 1.1.1.1. I put 1.1.1.1 because I have google dns to be used like this for a better view
-
Ok, so it's actually outbound NATing at the other end of the tunnel. You can see it appears as 10.0.2.1 rather than 192.168.1.15. So you may want to disable the NAT for the GRE interface at the client end.
You can also see it's not NATing the traffic out of the WAN at that end so you need a rule to add that there. That rule will depend on whether you disable the NAT at the client end. -
@stephenw10
Can you tell me where I can disable NAT?
For GRE tunnel only. I have the ip 192.168.1.2 with NAT for port 8006 going out through my WAN since it doesn't need protection that ip.
Thanks -
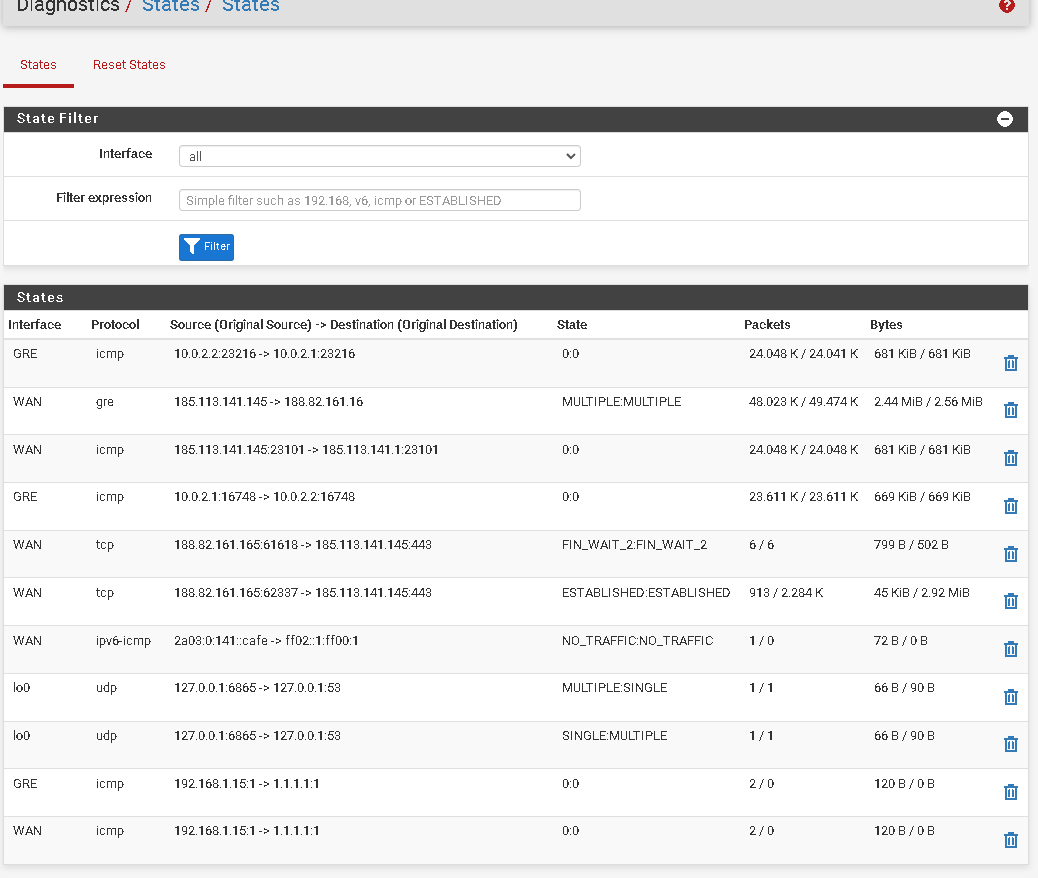
I've already disabled NAT only in the tunnel on the pfsense client and it's already here without NAT. Now it will just be creating a static route right?
-
Ok, so you need to add an Outbound NAT rule on that side for 192.168.1.0/24 on WAN.
If you have added a static route back to the main side I would expect the auto outbound rules to cover that so I assume there is not.
Steve