Best Use of HAProxy, ACME, Let's Encrypt
-
I've taken my time reading posts on many forums, including here, the Let's Encrypt forum, and Proxmox forum.
My journey started trying to find a solution to unencrypted websites on my local network i.e. when accessing my Proxmox and NodeRed websites on my local network, the websites complain they are unsecure.
So, I went down a rabbit hole attempting to work out a self-signed certificate and key combo which failed. Then someone on the Proxmox forum suggested I needed an external certificate authority, such as Let's Encrypt. So over to the Let's Encrypt forum I went, and most of the people there told me I needed to install HAProxy and ACME on my pfsense firewall, as that combination would allow me to somehow solve the unencrypted issue with internal websites.
Most of the info I read and videos I watched relates to using HAProxy and ACME to enable people on the internet to access a web server on my internal network. That is not what I want to do... as I explained, I want to 'secure' the access to my various 'internal' only websites.
So, here I am... having read a number of documents, and still no closer to finding a solution using HAProxy and ACME. If you are reading this, and are kind enough to share info, that would be very much appreciated. Even if all you share is a link to some info... it will still be very much appreciated.
Thanks, Mark
-
@gregoinc said in Best Use of HAProxy, ACME, Let's Encrypt:
I want to 'secure' the access to my various 'internal' only websites.
To who - your own internal users where you control the browser or machine? If so why not just create your own CA, issue your own certs and have clients trust the CA.
Example. I access my nas, switches, unifi controller, pfsense gui, printer gui all with certs I issued and my clients trust the ca.
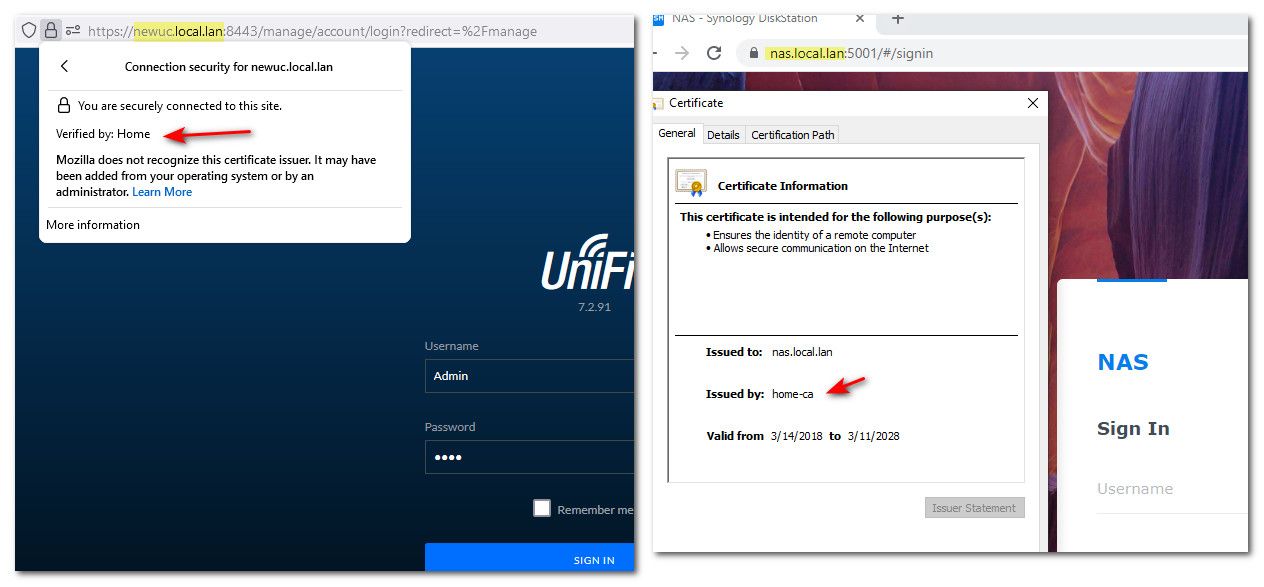
Different browsers on the same machine trusting certs issues by my CA.
If this is all internal you don't need a public trusted CA to create the certs.. That is only really required when some unknown user/machine is going to access the site and you can not easily have them trust your certs. Ie if the was some public site then yeah using acme would work.
-
@gregoinc The direction you want to take depends solely on effort
- Have your firewall be its own CA and issue the cert. You will need to go to every client within your LAN and have them trust the cert
- (Preferred): Register a domain. example.com. In my case, my domain is registered within Cloudflare. CF also manages my external DNS. Then within ACME, issue yourself a wildcard certificate *.example.com (or individual cert for each application if you want but wildcard is easier). Once you get your cert which should take a few seconds or a minute then you can use the cert within HA proxy to do the SSL termination.
Because the certificate is signed by a valid CA, your clients will implicitly trust the cert and your certificate errors will go away.
Once you have that wildcard cert you can use it for anything within the LAN. I use it, for example, when i log into my pfsense i no longer get the ssl error message.
There are quite a few resources on Youtube that will show you how to do option 2
-
@michmoor said in Best Use of HAProxy, ACME, Let's Encrypt:
have them trust the cert
Trust the CA - now going forward any cert for any domain or san with a rfc1918 address would be trusted. It is a 1 time thing.
But yes comes down to how many clients you have that would be accessing these resources. If they are admin gui's to your devices I would think the number of clients that you would have to set your CA is limited.
-
@johnpoz said in Best Use of HAProxy, ACME, Let's Encrypt:
Trust the CA - now going forward any cert for any domain or san with a rfc1918 address would be trusted. It is a 1 time thing.
Loading certs on multiple clients could be a pain. For my home network at least, Using apps like Jitsi or NextCloud, there are no admin access requirements but being able to log in without a cert issue is nice.
Multiple ways to solve a somewhat benign problem for sure but I like the idea of a valid CA just issuing my certs. One and done.
Now if you do want to make services available over the WAN you already have a domain and a cert to use. -
@michmoor sure - there are always multiple ways to skin the cat.
I use an acme cert for service I provide to the public over haproxy. Because this was the simple solution, and the renew of that cert can be automated. And to be honest getting the service to even use a cert not provided for int he software, so the backend is not encrypted, only the frontend to haproxy is doing the ssl offload, when the proxy talks to the service its only http.
But I see no reason to bounce off my haproxy to access my switch gui for example. Having to install the acme cert on that switch every 90 days would be PITA.
For me it was 1 and done thing because it was done before browsers set limits to length of the lifetime, so set certs life for 10 years.
Which solution is easier comes down to the details. Maybe he has like his phone/tablet and his pc that access his internal services that all can locally handle the ssl. If so then trusted CA is easier to implement... Now if he has lots of clients, and lots of different services that may or may not support ssl even - then sure the haproxy is a better solution.
To know the best way to skin a specific cat, you need to know its breed, its size, its color, etc.. ;) hehehe
-
@johnpoz said in Best Use of HAProxy, ACME, Let's Encrypt:
To know the best way to skin a specific cat, you need to know its breed, its size, its color, etc.. ;) hehehe
Wonderfully put :)
-
@johnpoz said in Best Use of HAProxy, ACME, Let's Encrypt:
@gregoinc said in Best Use of HAProxy, ACME, Let's Encrypt:
I want to 'secure' the access to my various 'internal' only websites.
To who - your own internal users where you control the browser or machine? If so why not just create your own CA, issue your own certs and have clients trust the CA.
Hi John, I agree... only issue, I am an idiot... and cannot work out how to issue my own certs to each of the applications I use i.e. Unifi, Node Red, Home Assistant, etc.
I created my own root CA...
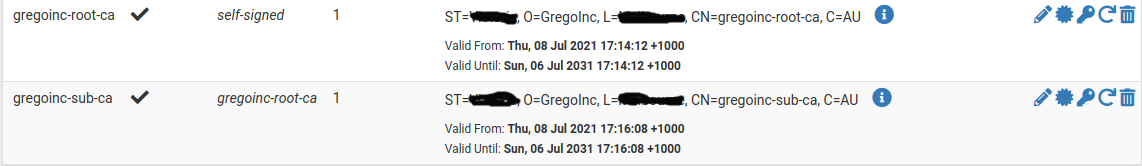
Example. I access my nas, switches, unifi controller, pfsense gui, printer gui all with certs I issued and my clients trust the ca.

Different browsers on the same machine trusting certs issues by my CA.
This is the holy grail for me... however I have been told on various forums it is 'easier' to use ACME and HAProxy, than individually assigning certificates to each application. But I am no expert, which is why I am here.
If this is all internal you don't need a public trusted CA to create the certs.. That is only really required when some unknown user/machine is going to access the site and you can not easily have them trust your certs. Ie if the was some public site then yeah using acme would work.
Agreed. When watching the multitude of YouTube videos it became clear to me that most people use HAProxy and ACME to allow people on the internet to access a website on thier internal network i.e. sharing a plex server. I am not seeking to do this.
I have my own domain - gregoinc.com so theoretically I could do the ACME / HAProxy approach, but I am not convinced, other than it could be easier than individual certs. But like I said I am no expert.
Thanks, Mark
-
===group
===@michmoor said in Best Use of HAProxy, ACME, Let's Encrypt:
@gregoinc The direction you want to take depends solely on effort
- Have your firewall be its own CA and issue the cert. You will need to go to every client within your LAN and have them trust the cert
As I wrote above in my reply to John, I'd heard this approach requires greater effort than the one you've outlined below. But like I said to John, I am not expert?
- (Preferred): Register a domain. example.com. In my case, my domain is registered within Cloudflare. CF also manages my external DNS. Then within ACME, issue yourself a wildcard certificate *.example.com (or individual cert for each application if you want but wildcard is easier). Once you get your cert which should take a few seconds or a minute then you can use the cert within HA proxy to do the SSL termination.
Because the certificate is signed by a valid CA, your clients will implicitly trust the cert and your certificate errors will go away.
Once you have that wildcard cert you can use it for anything within the LAN. I use it, for example, when i log into my pfsense i no longer get the ssl error message.
There are quite a few resources on Youtube that will show you how to do option 2
I have read a number of forums and watched countless videos on YouTube. As I wrote to John, most of the content is geared towards people wanting to open up a website on thier LAN to people on the internet.
I installed ACME and created all necessary items i.e. certificate, keys...
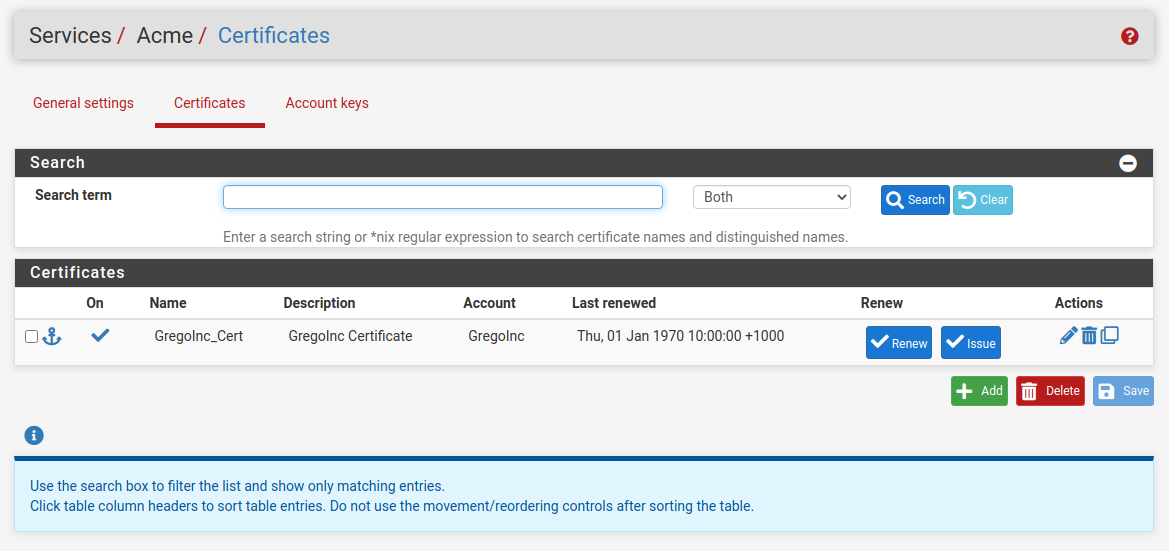
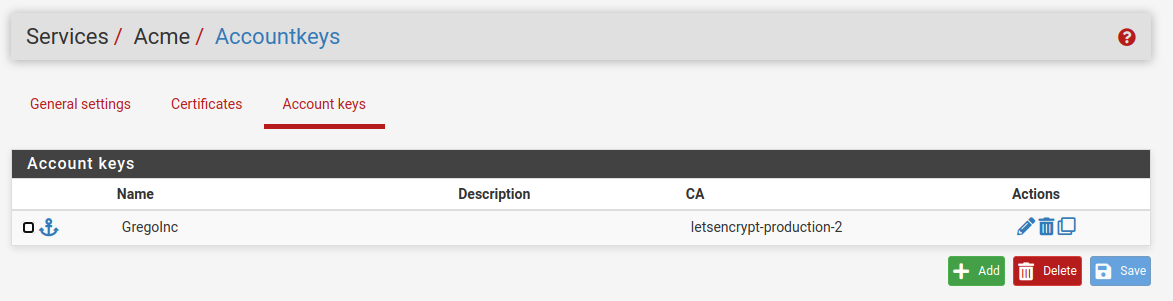
I figure I might be heading in the right direction... created a wild card entry...
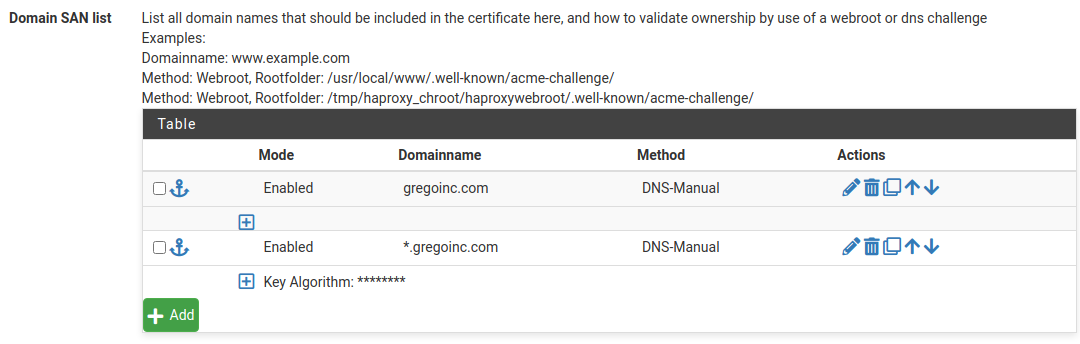
Got to this point... and now I am unsure how to hook it all to HAProxy which I also have installed. Like I said, most of the content I've read is not for internal use, but external connections coming in.
Thanks, Mark
-
@johnpoz said in Best Use of HAProxy, ACME, Let's Encrypt:
@michmoor said in Best Use of HAProxy, ACME, Let's Encrypt:
have them trust the cert
Trust the CA - now going forward any cert for any domain or san with a rfc1918 address would be trusted. It is a 1 time thing.
I guess it depends on whether or not I use my own CA or Let's Encrypt... I assume this is what you are saying here?
But yes comes down to how many clients you have that would be accessing these resources. If they are admin gui's to your devices I would think the number of clients that you would have to set your CA is limited.
I am a pretty crazy super nerd.... so I have a few sites

Ideally, I'd like something that is low admin, and I could be wrong but a large degree of folks are saying the HAProxy path is the best? But that assumes I can get it working in the first place

-
@michmoor said in Best Use of HAProxy, ACME, Let's Encrypt:
Loading certs on multiple clients could be a pain.
This is what I have been coming up against, multiple ways to load certs on various clients... which is why I started looking at ACME and HAProxy.
Multiple ways to solve a somewhat benign problem for sure but I like the idea of a valid CA just issuing my certs. One and done.
This is what I have been reading... and sounds like a lower admin overhead. But it is extremely unlikely I will ever open my network to the outside world. But I guess it would be nice to have the option?
-
@johnpoz said in Best Use of HAProxy, ACME, Let's Encrypt:
@michmoor sure - there are always multiple ways to skin the cat.
I use an acme cert for service I provide to the public over haproxy. Because this was the simple solution, and the renew of that cert can be automated. And to be honest getting the service to even use a cert not provided for int he software, so the backend is not encrypted, only the frontend to haproxy is doing the ssl offload, when the proxy talks to the service its only http.
I have struggled to understand the logic of using what is essentially an external facing access solution for internal use? But I am willing to stick with it if it will make my life easier... and is less admin overhead.
My greatest challenge is individually modifying each application to use a certificate. Most of my apps are on linux hosts, so it can be challenging for me to get individual certs to worm... but like I said, I am an idiot when it comes to this stuff.
But I see no reason to bounce off my haproxy to access my switch gui for example. Having to install the acme cert on that switch every 90 days would be PITA.
This is what I am seeking to avoid as well. I have a number of switches.
For me it was 1 and done thing because it was done before browsers set limits to length of the lifetime, so set certs life for 10 years.
Which solution is easier comes down to the details. Maybe he has like his phone/tablet and his pc that access his internal services that all can locally handle the ssl. If so then trusted CA is easier to implement... Now if he has lots of clients, and lots of different services that may or may not support ssl even - then sure the haproxy is a better solution.
Like I said, don't underestimate how much of a super nerd you have here

-
Any feedback on the best way to configure HAProxy would be very much appreciated.
I think all I need is a little guidance relating to the Front and Back end configuration, so even a link to some info would be helpful.
Thanks, Mark
-
@gregoinc I just went through this myself. I originally had made all my own certs and added them to clients root cert authority but the self hosted web interface for my home security system doesn't allow for adding of ssl certs. Since I already have a paid for domain name for 10 years and this was so easy I just set it up for all my home private severs on LAN. I know I'm about a month late, but for anyone else maybe it will help. YouTube: How To Create pfsense Let's Encrypt Wildcard Certificates using HAProxy