Firewall auto blocking IPv4 link local traffic on LAN?
-
I am seeing messages like this fairly frequently in the log:
Aug 7 14:57:56 LAN Block IPv4 link-local (1000000101) 169.254.184.229 224.0.1.60 IGMP
I don't have any rules set up to block this traffic and indeed I have a rule near the top of the LAN ruleset that should, as it happens, allow this traffic.
Any idea why the firewall seems to be automatically blocking it? Any way to stop it logging the fact?
Thoughts appreciated.
-
@chrisjenk that is a specific rule
cat /tmp/rules.debug | grep 1000000101
block in quick from 169.254.0.0/16 to any ridentifier 1000000101 label "Block IPv4 link-local"You have something wrong to be honest if your seeing that, why do you have something on your network using link local address space sending IGMP?
You can turn off that specific link-local rule by allowing for it.
But yeah that rule is above any rule you put in.. you have to allow for that and then that rule goes away.
But best option would be to figure out why your having that traffic in the first place - devices on your network shouldn't be sending that unless they had a problem getting an IP address from dhcp, etc.. I would do a sniff via packet capture to figure out via mac address what exactly on your network is sending that traffic and fix it there vs just not logging it.
-
@johnpoz said in Firewall auto blocking IPv4 link local traffic on LAN?:
@chrisjenk that is a specific rule
cat /tmp/rules.debug | grep 1000000101
block in quick from 169.254.0.0/16 to any ridentifier 1000000101 label "Block IPv4 link-local"You have something wrong to be honest if your seeing that, why do you have something on your network using link local address space sending IGMP?
You can turn off that specific link-local rule by allowing for it.

But yeah that rule is above any rule you put in.. you have to allow for that and then that rule goes away.
But best option would be to figure out why your having that traffic in the first place - devices on your network shouldn't be sending that unless they had a problem getting an IP address from dhcp, etc.. I would do a sniff via packet capture to figure out via mac address what exactly on your network is sending that traffic and fix it there vs just not logging it.
These are Apple Airport Extreme WiFI access points - well they can be routers but these are configured in bridge mode so are acting just as APs - and are on the latest firmware (such as it is). They have fixed IP addresses and are working just fine. I have absolutely no idea why they are sending this traffic (maybe it is because they have IGMP snooping enabled?) nor any idea how to turn it off (not sure that I want to disable IGMP snooping since these units are also switches and do have a few smart home devices connected to their Ethernet ports). I guess the question is, does this IGMP traffic have to leave the LAN? Does it have to reach the SG3100? If I block it will it cause any problems? My guess is not since it is already blocked :-) In any event, I'd like to stop these messages cluttering up the log.
Any advice?
-
@chrisjenk said in Firewall auto blocking IPv4 link local traffic on LAN?:
does this IGMP traffic have to leave the LAN?
No - you don't want to disable something that you have no idea what it even is ;) Do you run a bunch of multicast things where devices would join different multicast groups? If not you have zero use for IGMP snooping ;)
Do you have IPTV via multicast running on your network for example?
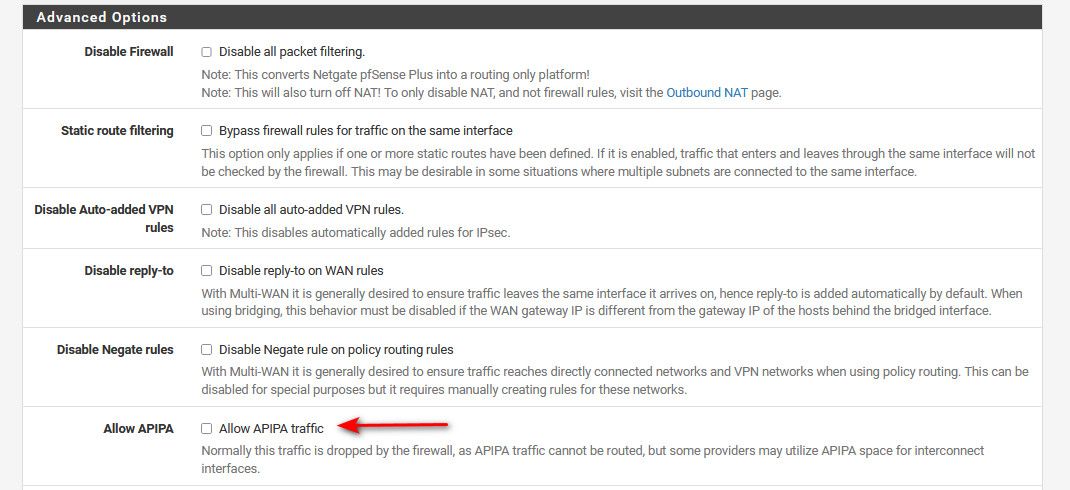
If you don't know how are don't want to disable it at the device sending it - then don't log it, if you allow APIPA then that block rule will go away.
No it has zero reason to reach pfsense - you could filter it at your smart switch if you want.
-
@johnpoz said in Firewall auto blocking IPv4 link local traffic on LAN?:
@chrisjenk said in Firewall auto blocking IPv4 link local traffic on LAN?:
does this IGMP traffic have to leave the LAN?
No - you don't want to disable something that you have no idea what it even is ;) Do you run a bunch of multicast things where devices would join different multicast groups? If not you have zero use for IGMP snooping ;)
Do you have IPTV via multicast running on your network for example?
If you don't know how are don't want to disable it at the device sending it - then don't log it, if you allow APIPA then that block rule will go away.
No it has zero reason to reach pfsense - you could filter it at your smart switch if you want.
I'm not consciously running anything that I know for sure uses multicast but we have a house full of Apple stuff and many other smart devices so it isn't inconceivable that something somewhere uses it. Since this traffic has effectively been blocked since I installed the SG3100 over a year ago I decided to allow APIPA and then added a custom rule to block this but not log it.
One step closer to decluttering the firewall log so I can focus on anything interesting/problematic.
-
-
@chrisjenk said in Firewall auto blocking IPv4 link local traffic on LAN?:
so it isn't inconceivable that something somewhere uses it
Multicast - sure possible, but that is not what igmp snooping is ;) IGMP snooping is not sending multicast to everyone, only the devices that have jointed that multicast group.
This is normally needed in high bandwidth multicast stuff - say you had a multicast TV stream going - would you want that stream going to every single port, every device on your network - this is what multicast is.. Or would you like your switch to say hey only send that to the TV device that joined that multicast stream.
Multicast discovery of other devices, IGMP is not something needed in that sort of setup.