Strange messages in the firewall log. Why? How to suppress?
-
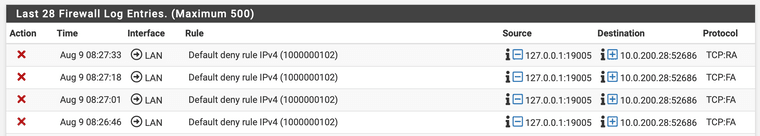
In my firewall log I am repeatedly seeing these messages, once every 15 seconds or so...
The process that has port 19005 open on the pfSense system (NetGate 3100 running 22.05) is xinetd.
I have several questions:
-
Why is xinetd on the firewall system sending messages to this one (macOS) system on my home network (out of the many 10s of systems present)?
-
According to the message this traffic originates from the firewall's 'localhost address, so how can it even be sent to a non-localhost address?
-
Why does a firewall rule specifying 127.0.0.1 as the source (or destination - I have tried both) address match this traffic?
I know that I can suppress this traffic by disabling logging for the default rules but I do not want to do that. I would prefer to (a) eliminate this specific traffic (it seems erroneous) or failing that (b) suppresses just this type of log message.
Any help is appreciated.
-
-
@chrisjenk
hey there,
maybe this link delivers an explanation?
https://tcpip.wtf/en/pfsense-xinetd-readjusting-service.htmSounds similar....?
-
@chrisjenk That is an outbound log - why are you blocking traffic outbound on your lan?
Who is 10.0.200.28, is that pfsense lan IP?
-
@johnpoz said in Strange messages in the firewall log. Why? How to suppress?:
@chrisjenk That is an outbound log - why are you blocking traffic outbound on your lan?
Who is 10.0.200.28, is that pfsense lan IP?
It is just the regular Firewall log. Yes the traffic is marked as 'outbound' because it originates on the NetGate pfSense host (127.0.0.1 - localhost) and is directed at a MacBook pro laptop (10.0.200.28). This makes little sense to me (how can traffic from 'localhost' (127.0.0.1 be sent to a non localhost IP???). Why is pfSense generating this traffic and why only to this one specific system (I have 6 Macs on my home network plus many other systems and devices)? This traffic certainly seems suspect/erroneous to me.
It is not me that is blocking this traffic; as you can see from the log entries the traffic is being blocked by the default deny rule in pfSense. The issue here is (a) why is this traffic occurring at all (pfSense bug maybe?) and (b) how can I stop these messages cluttering up they log without disabling all logging for the default deny rule.
-
@chrisjenk there is no outbound blocking out of the box - for pfsense to block something outbound you would of had to create the rule in floating.
Why did you do this. RA and FA are closure of communication in TCP (RST,ACK and FIN,ACK), so that would be out of state traffic..
-
@johnpoz said in Strange messages in the firewall log. Why? How to suppress?:
@chrisjenk there is no outbound blocking out of the box - for pfsense to block something outbound you would of had to create the rule in floating.
Why did you do this. RA and FA are closure of communication in TCP (RST,ACK and FIN,ACK), so that would be out of state traffic..
Nope, I have no floating rules. This traffic has been in my log since day 1 (around 18 months ago)... Recently I started a process of trying to reduce spurious log traffic and I am currently stuck on these specific messages. As I said the more fundamental question is why/how pfSense is trying to send from a localhost address to a LAN address. This makes no sense and should not even make it to the filter layer...
-
@chrisjenk agreed that makes no sense - but pfsense has no block outbound rules unless you created them in floating tab.
And there is specific rules to allow pfsense to go anywhere it wants anyway. And from loopback
# loopback pass in on $loopback inet all ridentifier 1000012011 label "pass IPv4 loopback" pass out on $loopback inet all ridentifier 1000012012 label "pass IPv4 loopback" pass in on $loopback inet6 all ridentifier 1000012013 label "pass IPv6 loopback" pass out on $loopback inet6 all ridentifier 1000012014 label "pass IPv6 loopback" # let out anything from the firewall host itself and decrypted IPsec traffic pass out inet all keep state allow-opts ridentifier 1000012015 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts ridentifier 1000012016 label "let out anything IPv6 from firewall host itself" -
@johnpoz said in Strange messages in the firewall log. Why? How to suppress?:
@chrisjenk agreed that makes no sense - but pfsense has no block outbound rules unless you created them in floating tab.
And there is specific rules to allow pfsense to go anywhere it wants anyway. And from loopback
# loopback pass in on $loopback inet all ridentifier 1000012011 label "pass IPv4 loopback" pass out on $loopback inet all ridentifier 1000012012 label "pass IPv4 loopback" pass in on $loopback inet6 all ridentifier 1000012013 label "pass IPv6 loopback" pass out on $loopback inet6 all ridentifier 1000012014 label "pass IPv6 loopback" # let out anything from the firewall host itself and decrypted IPsec traffic pass out inet all keep state allow-opts ridentifier 1000012015 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts ridentifier 1000012016 label "let out anything IPv6 from firewall host itself"Yes, my system has those rules. From /tmp/rules.debug:
loopback
pass in on $loopback inet all ridentifier 1000007811 label "pass IPv4 loopback"
pass out on $loopback inet all ridentifier 1000007812 label "pass IPv4 loopback"
pass in on $loopback inet6 all ridentifier 1000007813 label "pass IPv6 loopback"
pass out on $loopback inet6 all ridentifier 1000007814 label "pass IPv6 loopback"let out anything from the firewall host itself and decrypted IPsec traffic
pass out inet all keep state allow-opts ridentifier 1000007815 label "let out anything IPv4 from firewall host itself"
pass out inet6 all keep state allow-opts ridentifier 1000007816 label "let out anything IPv6 from firewall host itself"At the risk of repeating myself , there are no floating rules (of any kind) defined and no interface rules explicitly set to block this traffic. Also, the log message clearly indicates that the block is due to the Default deny rule IPv4 which is not one of my rules (i.e. it is a system rule).
So maybe this is a bug?
-
@chrisjenk said in Strange messages in the firewall log. Why? How to suppress?:
So maybe this is a bug?
And if that was the case why are not lots and lots of people reporting - I don't see any such logged entries.
While there could be some bug involved - its something unique in your setup/config that is presenting these symptoms.
Do you have any packages installed, have you modified outbound nat? Do you have multiple networks, vlans? What is your version of pfsense?
Here is the thing for a close FA or RA to be sent, then there had to be a SYN and SA sent before for the connection to be created -- this is out of state FA and RA block - which yes makes sense for the default deny rule that is inbound and outbound - But showing FA and RA means communications was happening and then it was stopped an your state lost? Are you seeing other logs like SA? Where pfsense tried to open the session but failed so finally sent FA, and then at last RA..
-
@johnpoz said in Strange messages in the firewall log. Why? How to suppress?:
@chrisjenk said in Strange messages in the firewall log. Why? How to suppress?:
So maybe this is a bug?
And if that was the case why are not lots and lots of people reporting - I don't see any such logged entries.
While there could be some bug involved - its something unique in your setup/config that is presenting these symptoms.
Do you have any packages installed, have you modified outbound nat? Do you have multiple networks, vlans? What is your version of pfsense?
Here is the thing for a close FA or RA to be sent, then there had to be a SYN and SA sent before for the connection to be created -- this is out of state FA and RA block - which yes makes sense for the default deny rule that is inbound and outbound - But showing FA and RA means communications was happening and then it was stopped an your state lost? Are you seeing other logs like SA? Where pfsense tried to open the session but failed so finally sent FA, and then at last RA..
I don't think my setup is that 'special'. On the 'local' side I have a main home network (IPv4 and IPv6), a guest network (VLAN 1003, IPv4 and IPv6), a 'special purposes' network (IPv4 and IPv6). I also have a single WireGuard tunnel. The only packages I have installed are WireGuard, aws-wizard (not actually used) and ipsec-profile-wizard (also not used). As I mentioned earlier, this is pfSense 22.05 on a NetGate 3100. I have not modified OutboundNAT but there are two auto generated rules there.
This traffic (from xinetd on ports 19xxx) seems to be related to NAT+Proxy. I was using that but I just switched to a split DNS setup to eliminate the need for that and those messages no longer appear in the log.
To my mind there is at least one bug here, most likely two:
-
A bug that sometimes causes unexpected traffic from xinetd in the firewall to a host in the local LAN, as a result of something related to NAT+Proxy.
-
A mis-logging/mis-reporting issue where such traffic is identified as originating from 127.0.0.1 (impossible) rather than the correct firewall interface address (which in this case would be 10.0.200.1).
Anyway, from my perspective the problem is now solves. Hopefully any such bugs will be fixed in some future release of pfSense.
-
-
@chrisjenk
That's interesting for it seems to be quite related to the "solution" mentioned in my link above...
there a change from NAT+Proxy to pure NAT solved the issue -
@the-other said in Strange messages in the firewall log. Why? How to suppress?:
@chrisjenk
That's interesting for it seems to be quite related to the "solution" mentioned in my link above...
there a change from NAT+Proxy to pure NAT solved the issueYes indeed. Thanks for that pointer since it helped me figure out what was causing the issue (but not why it is causing it). It seems like NAT+Proxy is best avoided unless you simply have to use it.