More efficient way to block other VLANs?
-
I have about 5 VLANs that I am trying to configure, half, I only want the VLANs to see itself.
CAMLAN has no access to to others, Guest is the same, Segmented, etc.
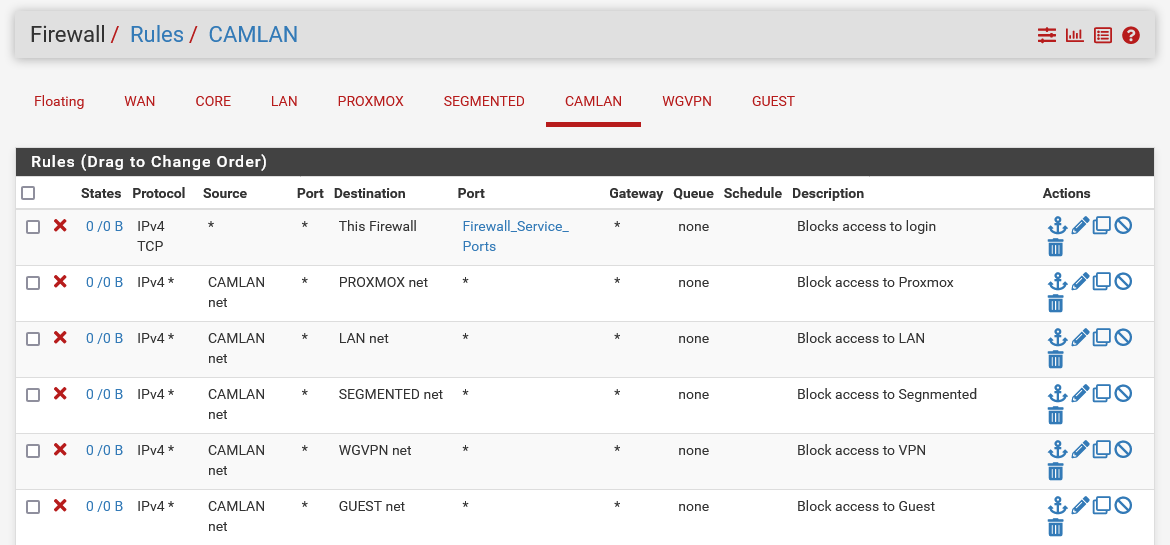
As you can see here, I have to block CAMLAN source to the listed destinations. Is there another way to do this without adding the destinations, one by one?
-
@creationguy You can create an alias with all your internal networks, or RFC1918 networks.
Then, create:1st rule:
Allow LAN_NET to LAN_IP_ADDRESS udp/tcp 53 to allow DNS
Here you can create more rules for other services you want LAN_NET to be able to use from the gateway.2nd rule:
Block LAN_NET to "alias mentioned above" ipv4*3rd rule:
Block LAN_NET to this firewall
If you don't block to this firewall, you will be able to reach the GUI using WAN IP
But if you have NAT reflection enabled, don't create this rule.4th rule:
Allow to the internet. -
What I'm trying to do is reduce the amount of times I need to duplicate these rules to the other VLANs, if I can't, it's fine, it's just a bit of work.
-
@creationguy said in More efficient way to block other VLANs?:
What I'm trying to do is reduce the amount of times I need to duplicate these rules to the other VLANs
In the example above, you will accomplish your goal with less rules.
Also, firewall rules are not something you will change everyday, most of the times is set and forget. -
@mcury Thank you, I will digest this in a bit.
-
@creationguy You don't need to add block rules.
Everything is blocked with zero rules added.
So just add rules that you want to pass and all else is blocked. -
@jarhead That is true when you don't want Internet access.
Once you add the allow all at the bottom for internet access, you will need block rules above. -
@mcury No, you don't.
Just add rules for what you want to pass.
So no allow all. -
@jarhead said in More efficient way to block other VLANs?:
@mcury No, you don't.
Just add rules for what you want to pass.
So no all all.You know all the IPs in the Internet?
You need all for internet access. -
@mcury You don't need to know the IP's. Just the ports.
-
@jarhead said in More efficient way to block other VLANs?:
@mcury You don't need to know the IP's. Just the ports.
Isn't that an allow all ?
SRC LAN_NET to * ?We are not speaking about ports here
-
@creationguy the simple way to block all your other vlans is to just create an alias with all the rfc1918 space in it, then use that to block all access to rfc1918 space - this assumes all your other vlans are rfc1918 space.. So unless you have routed public IP space that your using on your vlans this would take your example rules down to 2.
1 blocking access to "this firewall" ports you want to block, and then a block rfc1918 rule. Then your allow all "internet" rule.
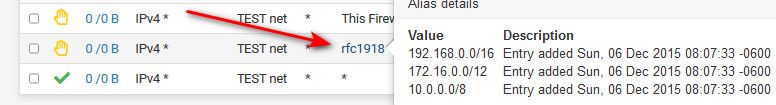
Advantage of such a alias is you auto block access to any future vlans you might add as well without having to adjust your rules.
-
@mcury said in More efficient way to block other VLANs?:
SRC LAN_NET to * ?
Technically you could invert the rfc1918 for an allow rule. But I am with you.
-
@mcury said in More efficient way to block other VLANs?:
@jarhead said in More efficient way to block other VLANs?:
@mcury You don't need to know the IP's. Just the ports.
Isn't that an allow all ?
SRC LAN_NET to * ?We are not speaking about ports here
How is that an Allow All?
Take my Guest Wifi.
I only allow internet on it.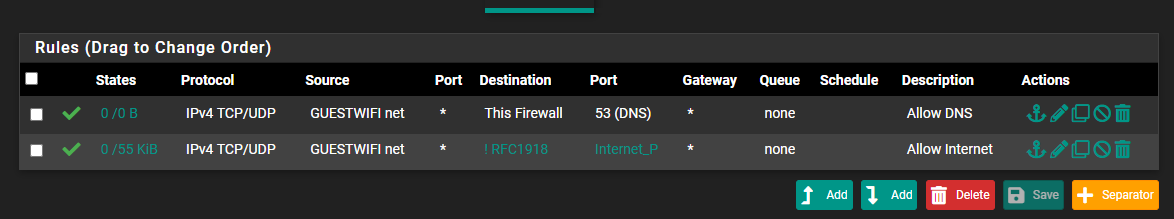
They have access to DNS, then the alias Internet_P is internet ports, 53, 80, 443, 853 and I added 123 because I use that alias in other networks and it was just easier to add it. I have to add the DNS rule even though 53 is allowed in the second rule because I block rfc1918 which would be the gateway. Everything else is blocked.
Then there's my Camera network.
Doesn't need internet at all so no allow all. I do have rules I toggle to allow two servers to the internet for updates but other than that, I allow NTP, whole network to an off site recorder, and access to a NAS.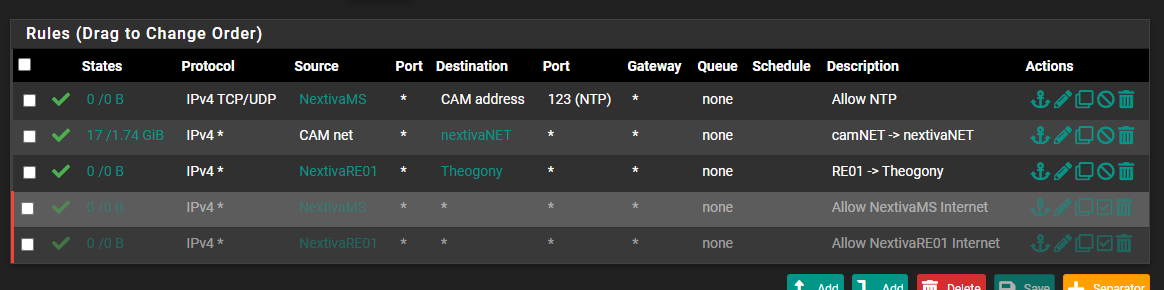
But either way, I think you're missing my point. When creating rules always start with everything is blocked, what do I want to allow. Then fine tune as needed.
As I said, don't need to know all the IP's, just the ports.
-
@jarhead said in More efficient way to block other VLANs?:
then the alias Internet_P is internet ports, 53, 80, 443, 853
There is no internet ports. A browser can use any port and sometimes they do.
I noticed it when I did a speed test and I was wondering, how could I archive such high numbers. The reason was that the speedtest website ran over vpn and showed my vpn IP but the speedtest itself was run on another port which was not part of my "webports". Took me some time to figure that out.So your inverted rfc1918 alias is doing the real "work" here, not the ports.
Your public WAN-port is still accessible from the guest-wifi though.
-
@bob-dig said in More efficient way to block other VLANs?:
There is no internet ports.
Gonna have to disagree there. If I take 80 and 443 out of that alias, no more internet.
Your public WAN-port is still accessible from the guest-wifi though.

And that's fine. There's nothing there.
-
@bob-dig there has been a bunch of threads about ! rules, not a fan.. While agree they can work - just makes it harder to read and there have in the past been issues with vips and bang rules.
I would suggest always be explicit in your blocking or allowing..
While I agree a !rfc1918 could be used - its just easy to read when your explicit in in your rules.
-
@jarhead said in More efficient way to block other VLANs?:
Gonna have to disagree there. If I take 80 and 443 out of that alias, no more internet.
But even now your guest probably can't run a speedtest like Ookla.
I think this is unacceptable.
@johnpoz Still never used a vip.
But in the end, if you make your rules tighter (e.g. with ports) it should be more secure.
So I am with @Jarhead too. -
@bob-dig said in More efficient way to block other VLANs?:
But even now your guest probably can't run a speedtest like Ookla.
I think this is unacceptable.
Honestly, not really sure I would want a guest that would need to run a speedtest on my internet... get your own damn internet for that!!
