WAN firewall log entries
-
Apologies for the probably basic question but I couldn't find an answer.
When I look at the firewall logs for my WAN interface I see block entries with a source and destination IP that is not mine. Why is this?
Thank you.
-
@parkerim like what for the destination - its quite possible your seeing broadcast traffic on your wan connection?
Could you post an example of this traffic where the destination is not your wan IP.
As to source traffic on your wan - yeah that is going to come from all over the planet - the internet is a noisy place.
-
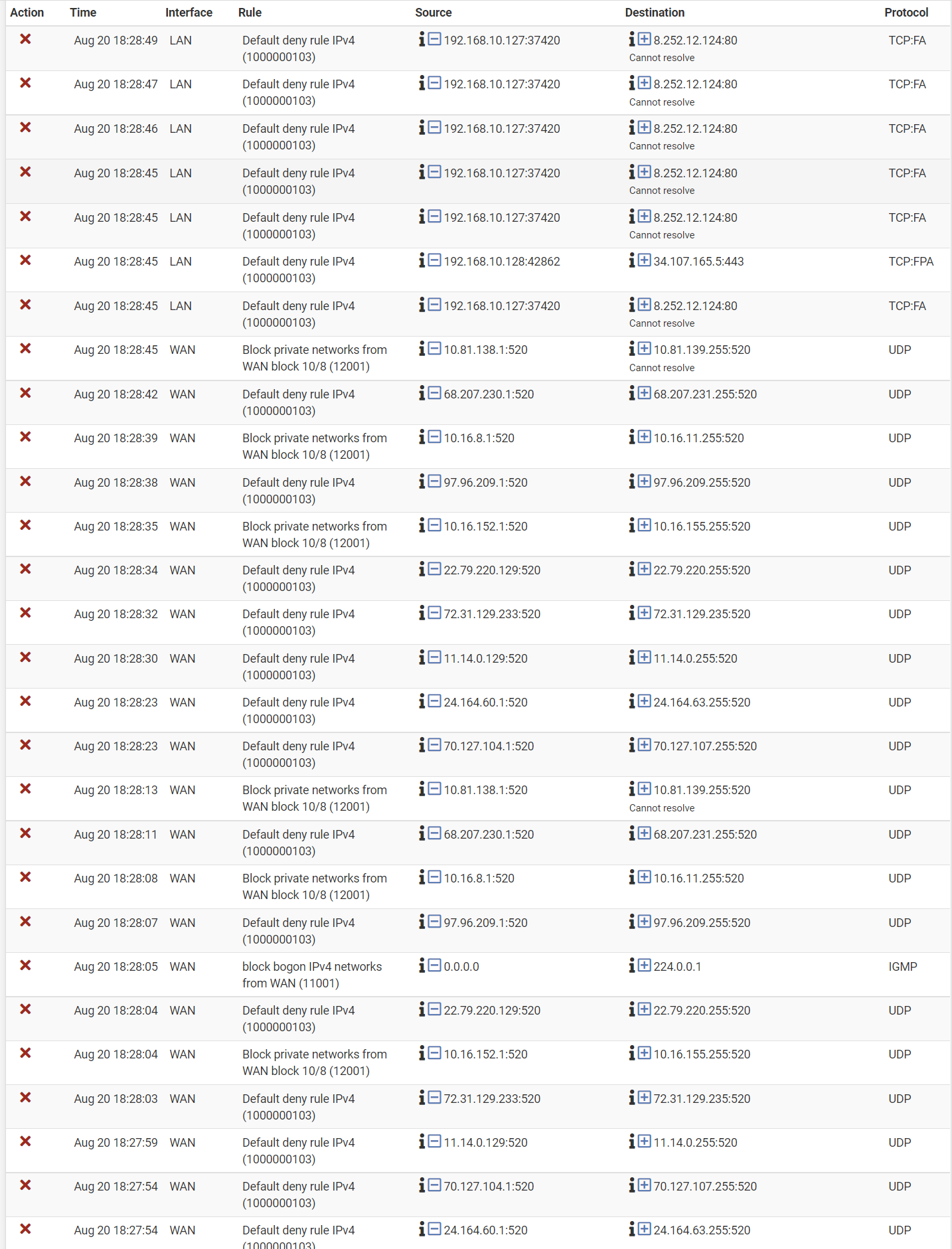
Thank you for the quick response, I do understand I am going to get my fair share of bots and folks scanning. But this wasn't expected.
-
@parkerim this all look like broadcast
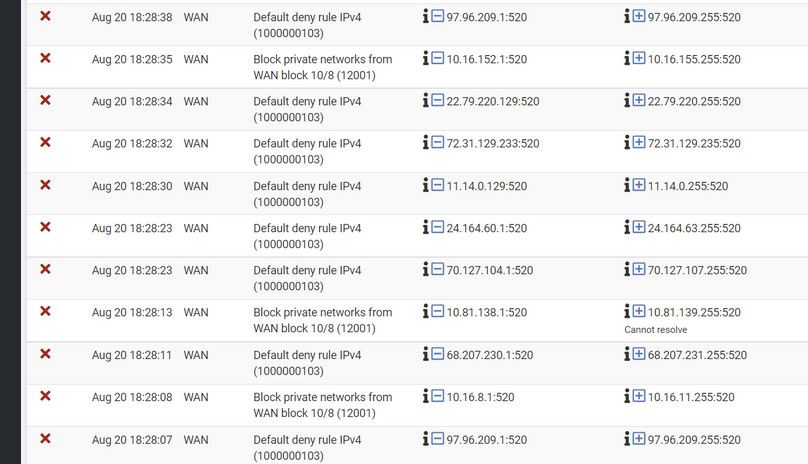
While x.x.x.255 doesn't have to be a broadcast network.. it could be a host address depending on the mask of the network.. It screams in what your showing since that is not your public IP to be broadcast traffic.
Its not uncommon for a ISP to run multiple L3 networks on the same L2..
If I look up all those destination IPs they all seem to belong to Charter (I take it this is your isp) - the ones I checked do.. The one that is really really odd is the 11.14.0.x addresses - those are owned by the DoD ;)
But then again its not completely uncommon for those networks to be used where they are not supposed to be used ;)
Company I worked for use to use DoD space inside there DC.. Because it was just being local, and never going anywhere outside the DC, etc. its bad practice but it is done way more often then you would think.
Port 520 is rip protocol - odd that would still be used anywhere to be honest..
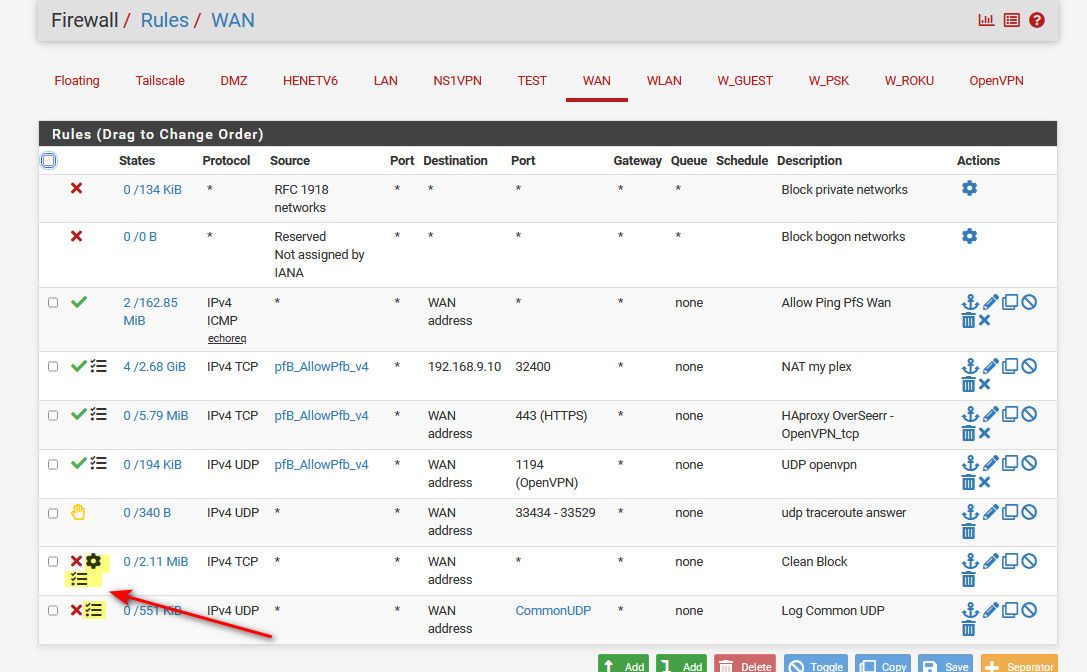
In my opinion that is all just noise - your best bet if filling up your logs would be to just not log it.. You could create a specific block rule on your wan to block that traffic and not log it. Or you could turn off logging of the default deny rule, and then just create a block rule to log what you want to see. This is what I do, I don't log default and just log SYN only traffic to my IP and common UDP ports..
There is some other odd IPs in there as destination though the 8.x.x.x address not a common broadcast address, and the .235 address
Oh those 8.x.x.x are on your LAN, and out of state.. Those are being not seen on your wan, that is just something a client tried to go to and the traffic is out of state.
I can see what some of that could be odd and confusing to see.. Where exactly is this pfsense - is this your home internet connection via charter ISP? Or is it in a colo or dc somewhere?
The one to the .235 address could also be broadcast that would be broadcast for a x.x.x.232/30 network.. And you see that source is .233 which yeah points to broadcast as well just a different network mask.
a x.232/30 network would be hosts .233 and .234 with .235 being the broadcast for that /30