How to block access to the firewall
-
Hello,
I need to block the access to the firewall, I have the following setup:
8 interfaces and ~20 VLANs.
Each one of them has a main IP address assigned, unfortunately, all of them allow the access to the firewall, so I was wondering if there is any FW rule that can stop it.Let me explain better:
- VLAN1 - IP 10.50.50.1
- VLAN2 - IP 10.50.51.1
- PHYSICAL INTERFACE 1 - IP 10.70.50.1
All of them are seen as gateways from the devices that belong to those networks, but I think you know that.
Basically, if I hit each of these IPs above I end up in the login page of Pfsense, this is what I want to block.
I would leave myself just 2 accesses to the firewall, the main one and a backup one from the router interfaces, plus probably one VLAN. -
@jt40
Add a block rule and select "This firewall" at destination and enter the concerned port.
You can do this with a floating rule. This can be applied to multiple interfaces. So you can hit all desired interfaces with only one strike. -
@jt40 as already stated the "this firewall" is the built in alias you would use to block all access to the firewall IPs, both lan side and wan IP, etc.
But keep in mind you prob want to allow access to stuff like ping or dns to pfsense IP on these interfaces?
Creating the rules you want for a multi-segmented network can get complicated, and some effort will be involved.
Again I would stress to stay away from shortcuts and trying to put stuff in floating that uses multiple interfaces, or grouping. You will thank me latter when looking to why something is allowed or blocked that shouldn't be.. When your rules are explicit and clearly written on each interface..
Take the extra time now and spend time writing the rules how you want them on each specific interface vs trying to take shortcuts.. You will be thankful later for sure when something is not working how you think it should be working.
edit:
I have been working with firewalls since there were just packet filters, and not actual stateful firewalls. It is best to be explicit and clear in your rules. So that later when your looking to why something doesn't work you don't have to piece together which rules are applied first, is that a member of this group or that group?My floating rules are very very limited. Just being a good netizen - I have rule to make sure no rfc1918 traffic sneeks out my wan via a outbound block to rfc1918. With an allow rule above that does allow access to my modems 192.168.100.1 address.
Floating tab is for advanced stuff - you should make sure you very familiar with how just normal rules work placing them on the specific interfaces in question before you attempt putting stuff in floating..
I would highly suggest you learn and get experience with just setting up rules on your interfaces, even if it takes a bit of extra time before you look to taking shortcuts with floating rules or grouping interfaces..
-
@johnpoz said in How to block access to the firewall:
@jt40 as already stated the "this firewall" is the built in alias you would use to block all access to the firewall IPs, both lan side and wan IP, etc.
But keep in mind you prob want to allow access to stuff like ping or dns to pfsense IP on these interfaces?
Creating the rules you want for a multi-segmented network can get complicated, and some effort will be involved.
Again I would stress to stay away from shortcuts and trying to put stuff in floating that uses multiple interfaces, or grouping. You will thank me latter when looking to why something is allowed or blocked that shouldn't be.. When your rules are explicit and clearly written on each interface..
Take the extra time now and spend time writing the rules how you want them on each specific interface vs trying to take shortcuts.. You will be thankful later for sure when something is not working how you think it should be working.
edit:
I have been working with firewalls since there were just packet filters, and not actual stateful firewalls. It is best to be explicit and clear in your rules. So that later when your looking to why something doesn't work you don't have to piece together which rules are applied first, is that a member of this group or that group?My floating rules are very very limited. Just being a good netizen - I have rule to make sure no rfc1918 traffic sneeks out my wan via a outbound block to rfc1918. With an allow rule above that does allow access to my modems 192.168.100.1 address.
Floating tab is for advanced stuff - you should make sure you very familiar with how just normal rules work placing them on the specific interfaces in question before you attempt putting stuff in floating..
I would highly suggest you learn and get experience with just setting up rules on your interfaces, even if it takes a bit of extra time before you look to taking shortcuts with floating rules or grouping interfaces..
You just spotted my problem, I just verified that this method doesn't work for me, unless I enable DNS and ping, the traffic is allowed otherwise, that's why in the other thread I was able to ping 8.8.8.8, and that's why my web pages load up if the domain has been resolved already in the current window, which anyway persists somewhere in the system because I can ping the same address from the command line, but not for new addresses.
Based on this, what did you mean with multi-segmented networks?
Is the case of having another gateway instead of the main gateway IP from the VLAN?
For example, VLAN 1 10.70.70.1 with a rule to allow the traffic to the gateway 10.70.80.1?Or what could be another method?
Shall I really create each rule manually? :DWhat about the DNS service? Shall I set up one in Pfsense?
What about the DHCP service? I think that this can't be changed, it must be the main VLAN IP and in any case, it doesn't have anything to do with the traffic, so I don't see it as a problem.
-
@viragomann said in How to block access to the firewall:
@jt40
Add a block rule and select "This firewall" at destination and enter the concerned port.
You can do this with a floating rule. This can be applied to multiple interfaces. So you can hit all desired interfaces with only one strike.I've just read your message again and again, so, if I block the IP and port ONLY, that should work, damn I didn't think to that before.
I was blocking access to the FW entirely with that rule, which blocks access to the gateway entirely...I can't use "This Firewall" because it doesn't allow to specify the IP or port, but I can create a custom rule.
-
@johnpoz said in How to block access to the firewall:
My floating rules are very very limited. Just being a good netizen - I have rule to make sure no rfc1918 traffic sneeks out my wan via a outbound block to rfc1918. With an allow rule above that does allow access to my modems 192.168.100.1 address.
The problem with creating a rule that allows access from my VLAN to the modem IP just doesn't work, what can I do...
How did you disable the traffic for packets belonging to RFC 1918? Did you mean all the internal traffic doesn't go outside without a specific rule?
-
@jt40 said in How to block access to the firewall:
I can't use "This Firewall" because it doesn't allow to specify the IP or port, but I can create a custom rule.
Sure you can, that is just an alias of the destination IP, you can set ports on that.. So it can be used as example to block access the web gui ports and ssh.
Also you put what you want to allow before it, then just allow the block to anything else to this firewall.
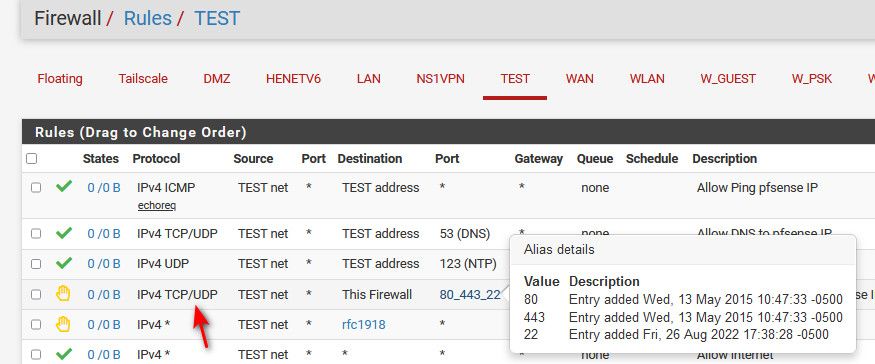
example this allows ping, dns and ntp to the pfense IP on that interface, and then the this firewall blocks any and all other stuff to any pfsense IP

Here its edited to block only access to gui ports via a simple ports alias.
If you want to block just ports, you would have to change from any on the rule to something with ports tcp or udp or both tcp/udp