PfBlockerNG Not Blocking Categories
-
Hey everyone, I have setup PfblockerNG to block a bunch of categories, ie Adult, sites, gambling, etc...but nothing is blocked. I can search for any one of the categories I chose to block and nothing happens. There are myriad of video showing basically the same setup to block but as I say nothing blocked. Bit confused, this is my first Pfsense setup. Thanks
-
This post is deleted! -
@stormgate said in PfBlockerNG Not Blocking Categories:
I have setup PfblockerNG to block a bunch of categories, ie Adult, sites, gambling, etc...but nothing is blocked.
You are using :
right ?
If so, I'll give an example.
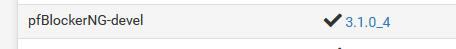
Lets say I don't like sport related sites : I check :
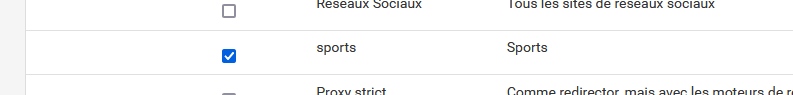
do a force reload for pfBlockerng-devel.
For testing purposes, I have a look at the DNSBL file that got downloaded :
/var/db/pfblockerng/dnsbl/UT1_sports.txt( I saw the file name in the force reload logs that scrolled over the screen while reloading )
The first entry is :
,1-2pitch.com,,1,UT1_sports,DNSBL_UT1Lets test "1-2pitch.com" on my PC :
C:\Users\Gauche>nslookup Serveur par dÚfaut : pfSense.mylocalnet.net Address: 192.168.1.1 > 1-2pitch.com Serveur : pfSense.mylocalnet.net Address: 192.168.1.1 Nom : 1-2pitch.com Address: 10.10.10.1 >This shows two important details :
My PC is using 192.168.1.1 == pfSense as the local DNS resolver. This is important.
If my PC was using, for example, 8.8.8.8 then your case is solved : it bypasses pfSense == pfBlockerng-devel complexly. DNSBL blocking won't work.You saw the answer : 10.10.10.1 : that is a local IP, a virtual IP created by pfBlockerng-devel.
If the answer was : 185.87.187.187 then you know that your PC isn't using pfSense as its resolver. Ask yourself the question : what was the reason for you to change your default PC IP settings ? ;) and advise : undo that.When I use "1-2pitch.com" in a web browser on my PC, I got the famous :
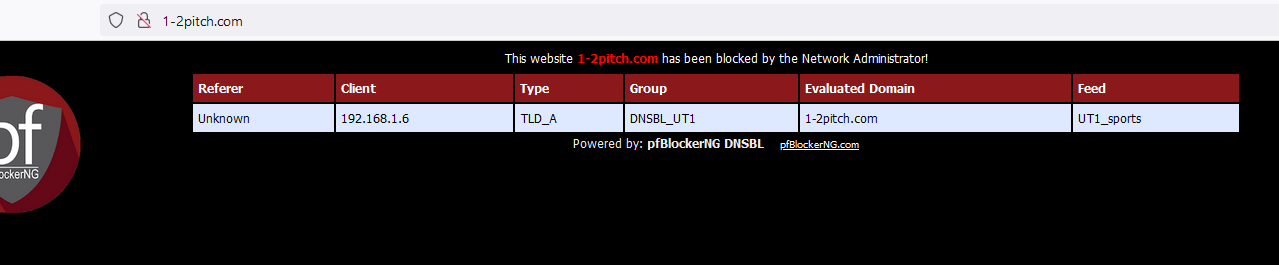
although this is very rare.
Most sites are https these days, so that page can't show. You just see a browser error.Btw : I'm using the resolver mostly using default settings.
In the Alerts log of pfBlokcerng-devel I saw :
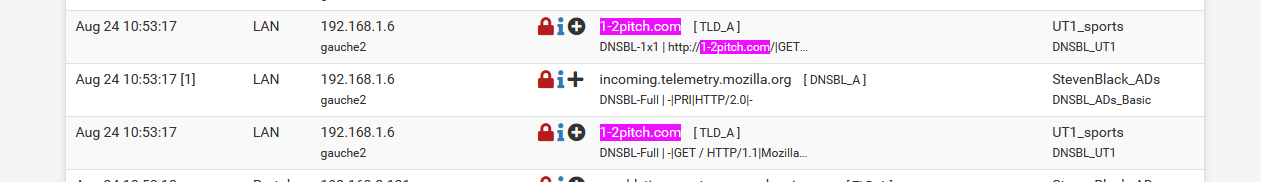
and Is have now :
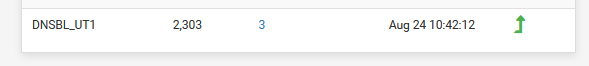
as there were 3 hits.
-
@gertjan Correct I am using the Development version. So what I did was I added rules to my testing network, 4 rules in total. I first blocked DNS(53) and DNS over TLS (853), then added to Pass rules for those same DNS blocked rules that allowed the request to pass to pfsense. I did notice anything I blocked was not resolving but I am not getting any blocking page (https pages) but I did start some entries that indicated the Ut1 list was being used now but its not consistent. One my main network I added all these rules but noticed this morning the DNS rules have now blocked the Aruba switches from accessing the cloud so I have to do a bunch more testing. I am using DNS over TLS btw with cloudflare.
-
@stormgate said in PfBlockerNG Not Blocking Categories:
I am not getting any blocking page (https pages)
These do not exist !!
Remember, I already said :@gertjan said in PfBlockerNG Not Blocking Categories:
although this is very rare.
Most sites are https these days, so that page can't show. You just see a browser error.so, you won't see the image I've shown above when you visit a https site.
The pfblokcerng-devel wb page that shows that page only works if the browser wanted to visit a http site. Pire http, not https site are very rare these days.
"1-2pitch.com" was one of them, so its probably a site that isn't maintained any more for years now. edit : correction : the domain is for sale now.1-2pitch.com will still get blocked : the web sit doesn't show up. That's what counts. For the end user it looks like the site doesn't "work". That's enough. They will abandon after hitting Refresh xx times.
@stormgate said in PfBlockerNG Not Blocking Categories:
then added to Pass rules for those same DNS blocked rules
-
@gertjan Yes thank you for that explanation, that does help alot and makes sense. I am going to check my rules when I get home, I have this setup offsite to setup so unfortunately I haven't gotten to setting up remote access to check things while at work. I have to check my DNS rules I have a feeling I made a mistake looking at your rules.
-
@gertjan Also wanted to say I really appreciate you taking the time to respond to my issue, many thanks.
-
@gertjan Are you using a custom NAT rule is that what your second is referring too.
-
@gertjan I think its working now, I fixed my rules to match yours plus I had had the same rules but with 853 to get it all working. My Aruba switches no longer connect to the cloud management system but one thing at a time. Now I can see what else may have broke. Thanks for your help.

-
@stormgate said in PfBlockerNG Not Blocking Categories:
@gertjan Are you using a custom NAT rule is that what your second is referring too.
Spot on.
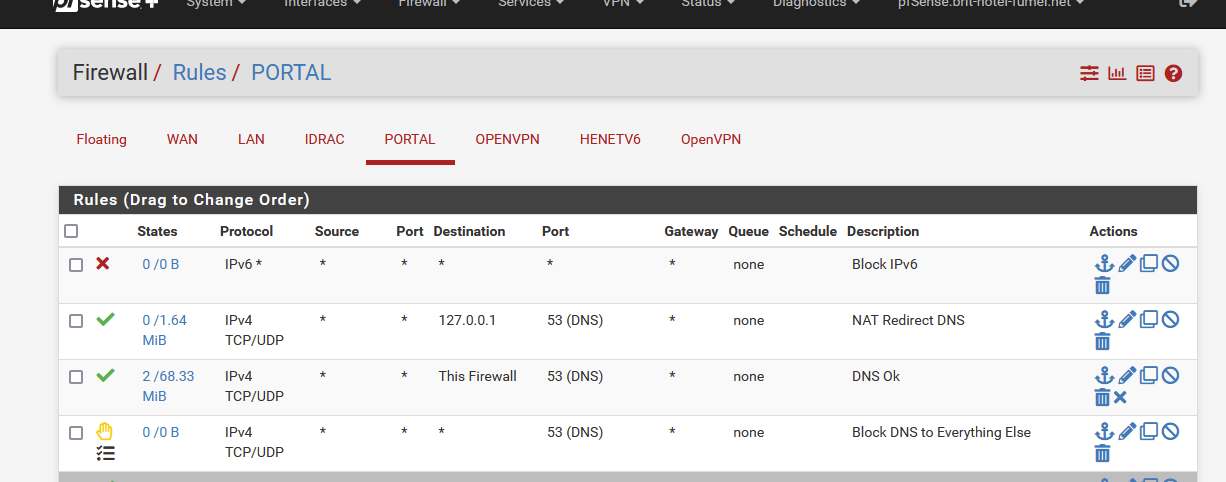
Read Redirecting Client DNS Requests.The rules I showed are (some of) the rules of my captive portal.
I don't need to block any port 853 attempts as that port will be blocked, as everything is bocked except TCP/UDP to port 53. Any non local, non-portal network traffic to port 53 will get redirected to the DNS resolver on pfSense by this rule.There are a whole bunch of people out their that had the bright idea to override their DHCP settings, and add 8.8.8.8 as their DNS. This will break the portal .... they will never get to the captive portal login page.
This step is very important for a captive portal that the DNS works.
The third rule grants access to my local pfSEnse DNS. This rule is there for the clients using normal DHCP settings ( == they obtained my portal's address as the DNS).
The counters in front of rule 2 and 3 show their usage.
@stormgate said in PfBlockerNG Not Blocking Categories:
My Aruba switches no longer connect to the cloud management system but one thing at a time
They have an IP ? ( these are smart switches ? )
All depends on the rules you have on your interface.And if they use a host name that has to get resolved fist, AND this hos t name is on one of the lists you use, then, yeah, they will get blocked.
But all this is easy to find out .... -
@gertjan Yes thanks very much, the solution to the Aruba equipment issue was simply set them back to DHCP, they don't need static since they can be managed through Aruba onboarding system. Remove the earlier rules to allow visibility but once set to DHCP, they communicated on their own through the rule set. I obviously have quite a bit more work to see how everything works but this is a good step forward, without DNS and filtering working correctly didn't make sense to work on anything else. As I mentioned I am using DNS over TLS hence the reason I needed the 853 rules.