Creating My Own IP4 Deny List Within PFB
-
I am trying to create my own IP4 deny list so I can control access to specific sites without having to use too many feeds that might go beyond what I require.
Before I begin, I appreciate that everyone has their way of approaching a task, however if what I am proposing will work (which I believe it should) I would prefer to remain on this course as I have an idea and want to run with it. Only way to learn.
So this is how I see this working out:
- Create an myipblocklist.txt file in folder ../var/db/pfblockerng/deny
- Edit myipblocklist.txt file with the ip addresses I have selected
- Go to PFS>Firewall>pfBlockerNG>IP>IP4
- Click "Add" and within the IP4SourceDefinitions panel add the location of the ip text file /var/db/pfblockerng/deny/myipblocklist.txt
- Fill in unique header/label
- Set the desired values within the Settings panel
- Leave remaining values/panels as is and save
- Do a Force Update
- Test to see if some ip's within the txt file are now blocked
Problem 1:
This seems to be a show stopper. I cant create the text file. Using the command "touch myipdenylist.txt" I get the error "touch: myipdenylist.txt: Permission denied". I think this is related to a security key but am not sure.Once I get this resolved I can continue with my plan as outlined and keep fingers crossed.
Thank you in advance for your input.
PS...If it is relevant, I am doing this via SSH using Putty.
-
@lpd7 if all you want is list of stuff that you want to block. There are many ways to solve this issue just with unbound, or with just an native alias.
Unbound in the custom options box can load a file that has your stuff in it. Native aliases can contain IPs or fqdn that resolve to be blocked, or even whole networks.
Where How are you trying to do the touch command? Are you using some other user account other than the root/admin account. I notice you said your doing this via ssh and putty.
See here ssh'd to pfsense cd to where you said you wanted to created it, the dir is empty, did touch command and then there is the file.
[22.05-RELEASE][admin@sg4860.local.lan]/var/db/pfblockerng/deny: ls [22.05-RELEASE][admin@sg4860.local.lan]/var/db/pfblockerng/deny: touch myipblocklist.txt [22.05-RELEASE][admin@sg4860.local.lan]/var/db/pfblockerng/deny: ls -la total 10 drwxr-xr-x 2 root wheel 3 Aug 25 15:16 . drwxr-xr-x 11 root wheel 15 Aug 25 12:13 .. -rw-r--r-- 1 root wheel 0 Aug 25 15:16 myipblocklist.txt [22.05-RELEASE][admin@sg4860.local.lan]/var/db/pfblockerng/deny: -
Mmm, how large a list are you intending here?
-
@lpd7 How are you logging in via ssh, using "admin"?
-
@johnpoz
Hi John
I did what you did to create the txt file (touch) and I get the permission denied message. Could it be a certificate/key issue? The account I log in with is an admin account, I can control everything, I tried root but no password worked. This would be handy to solve as I am sure it will come up again.[2.6.0-RELEASE] [xx@fw1.home.arpa]/var/db/pfblockerng/deny: touch myipblocklist.txt
touch: myipblocklist.txt: Permission deniedI think I have to be logged in as root...?
I like the idea of having a txt file or other as the source for the filtering because it seems it would be easier to manage, so either in the pfb deny folder or using the unbound mode. I looked for Unbound but not sure where that is located, I may have missed it as I thought I looked everywhere.
Thanks.
PS..I will need to deny individual ip's as well as whole networks, does that throw a wrench into my plans?
-
@stephenw10
Hey Stephen
Right now there are about 40 networks I want to block and I am just getting started. I could see this getting pretty big, if gets really big maybe have to split it up? -
@steveits
Hi Steve
I disabled the admin account when I set this up and am using my account which also belongs to the admin group. I just did some reading and if I understand what I read, it seems that I may have to log in with the admin account as root is somehow associated with admin specifically. May have to read it again, my eyes are tired. -
@SteveITS @stephenw10 @johnpoz
Ok I solved that one. I activated the admin account and logged in as admin and was presented with the PFS console screen and selected 8 and then went and created the txt file.....woo hooo I love it when persistence pays off.
Ok so now that I got the txt file created I want to start adding ip's, question is can I use the same txt file for individual ip's and whole networks or should there be one for each? And what would be the format? I am in a playful mood.
Would the following examples be the correct syntax for network and individual ip?
192.64.14.0/24
192.100.10.225The other lists/feeds I have setup seem to follow this with the exception of using # to make comments.
-
@lpd7 Ah, good. There was some other place I can't recall where the actual admin account is necessary. I know one is in the HA config sync...it has a field for the username but doesn't use it. (or, did, it's been a while)
If you are just blocking IPs, as noted above there are a couple of what I would say are simpler options, for instance creating a network alias and entering the networks into the GUI fields. If the list changes and you will be generating it, pfSense can pull an alias file from any web URL.
You can check your results via Diagnostics/Tables.
-
@lpd7yeah if your using some non root account. Like I created a testuser and put them in the admin group, and this does not work. Permission denied, but that is because the permissions are locked to only root being able to access that.
[22.05-RELEASE][testuser@sg4860.local.lan]/var/db/pfblockerng: ls -la total 124 drwxr-xr-x 11 root wheel 15 Aug 25 20:14 . drwxr-xr-x 21 root wheel 45 Aug 25 18:53 .. drwxr-xr-x 2 root wheel 2 Jul 25 08:03 ET drwxr-xr-x 2 root wheel 3 Aug 25 15:16 deny drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsbl drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsblalias drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsblorig -rw-r--r-- 1 root wheel 10001 Aug 4 22:00 geoip.txt -rw-r--r-- 1 root wheel 143360 Aug 25 20:14 ip_cache.sqlite -rw-r--r-- 1 root wheel 0 Jul 25 08:03 mastercat -rw-r--r-- 1 root wheel 0 Jul 25 08:03 masterfile drwxr-xr-x 2 root wheel 2 Feb 14 2022 match drwxr-xr-x 2 root wheel 10 Aug 25 15:00 native drwxr-xr-x 2 root wheel 10 Aug 25 15:00 original drwxr-xr-x 2 root wheel 2 Feb 14 2022 permit [22.05-RELEASE][testuser@sg4860.local.lan]/var/db/pfblockerng:If you had installed the sudo package you should be able to allow your other user to su up to root.. And then you could do it.
[22.05-RELEASE][testuser@sg4860.local.lan]/var/db/pfblockerng: sudo su We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. Password: # ls -la total 247 drwxr-xr-x 11 root wheel 15 Aug 25 20:14 . drwxr-xr-x 21 root wheel 45 Aug 25 18:53 .. drwxr-xr-x 2 root wheel 2 Jul 25 08:03 ET drwxr-xr-x 2 root wheel 3 Aug 25 15:16 deny drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsbl drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsblalias drwxr-xr-x 2 root wheel 2 Feb 14 2022 dnsblorig -rw-r--r-- 1 root wheel 10001 Aug 4 22:00 geoip.txt -rw-r--r-- 1 root wheel 143360 Aug 25 20:14 ip_cache.sqlite -rw-r--r-- 1 root wheel 0 Jul 25 08:03 mastercat -rw-r--r-- 1 root wheel 0 Jul 25 08:03 masterfile drwxr-xr-x 2 root wheel 2 Feb 14 2022 match drwxr-xr-x 2 root wheel 10 Aug 25 15:00 native drwxr-xr-x 2 root wheel 10 Aug 25 15:00 original drwxr-xr-x 2 root wheel 2 Feb 14 2022 permit # cd deny # whoami root # touch newfile.txt # ls -la total 20 drwxr-xr-x 2 root wheel 4 Aug 25 21:12 . drwxr-xr-x 11 root wheel 15 Aug 25 20:14 .. -rw-r--r-- 1 root wheel 0 Aug 25 15:16 myipblocklist.txt -rw-r--r-- 1 root wheel 0 Aug 25 21:12 newfile.txt #.I will need to deny individual ip's as well as whole networks, does that throw a wrench into my plans?
It would for the way to block domains with unbound options, either directly or loaded by file in the custom options box in unbound. This would only work for actual domains to be prevented from being looked up.
-
@johnpoz
You just id'd my next issue...Sudo is not available and I cant do apt-get or any update. I was trying to use nano to edit the txt file which is how I stumble upon this. Not sure why. I know I did this on my Ubuntu VM instances from the terminal but dont recall installing any packages on the FW outside of what PFS installed when I built it.How do i crack this nut?
Thinking cap is on tonight.
-
@lpd7 you’re making it hard. :)
Diagnostics/Edit file.
System/Packages , install sudo package.
pfSense is not Linux, and it isn’t designed to have lots of things installed on it.
-
@lpd7 @SteveITS is right I think your making this harder than it needs to be, and just install the sudo package via the gui
Also to the linux comment by Steve - while sure there is cmd line, and stuff you can do from that - generally speaking pfsense is meant to be fully managed by the gui. You should really never have to do anything directly from the cmd line.
While you might be used to editing files directly on linux, conf files, and etc - with pfsense your meant to do it via the gui.
Also nano can just be installed with pkg install nano
I have it installed on mine, it is in the pfsense repo
[22.05-RELEASE][admin@sg4860.local.lan]/root: pkg info nano nano-6.0 Name : nano Version : 6.0 Installed on : Sat Jul 2 09:25:52 2022 CDT Origin : editors/nano Architecture : FreeBSD:12:amd64 Prefix : /usr/local Categories : editors Licenses : GPLv3 Maintainer : danilo@FreeBSD.org WWW : http://www.nano-editor.org/ Comment : Nano's ANOther editor, an enhanced free Pico clone Options : DOCS : off EXAMPLES : off NLS : on Shared Libs required: libintl.so.8 Annotations : FreeBSD_version: 1203506 build_timestamp: 2022-06-01T19:10:49+0000 built_by : poudriere-git-3.3.99.20211130 port_checkout_unclean: no port_git_hash : 44b5542e32b4 ports_top_checkout_unclean: yes ports_top_git_hash: eac3af4a7698 repo_type : binary repository : pfSense Flat size : 2.38MiB Description : nano is a small, free and friendly editor which aims to replace Pico, the default editor included in the non-free Pine package. Rather than just copying Pico's look and feel, nano also implements some missing (or disabled by default) features in Pico, such as "search and replace" and "goto line number". WWW: http://www.nano-editor.org/ [22.05-RELEASE][admin@sg4860.local.lan]/root:If what your looking to do is block IPs and CIDRs - that is just much easier to do with the built in aliases to be honest via gui, you can load in a bunch if you have them already in some other file.
You can then just edit that added to it remove from it via the gui.
-
Yes, 'big' here would be a list of >10,000 subnets for example.
If you are dealing with, say, <1000 subnets then just use an alias in pfSense directly.
Side note; whilst not as powerful as Nano the Easy Editor
eeis included in pfSense by default and is more than enough to edit a few txt files. Also it has almost zero learning curve!Steve
-
@stephenw10 @johnpoz @SteveITS
All good info, I know that I may be going about this the hard way but thats how I learn that is until my brain overloads and I need to take a twizzler and pepsi break or maybe something stronger like a skittles and red bull. Let me digest this and take some notes and summarize and see if I cant settle on a solution you think would work best. Thank you. -
@lpd7 said in Creating My Own IP4 Deny List Within PFB:
Hello all my apologies for the delay but I can only devote time in chunks, my family wont give me space to play unless its something they want to play. I have to remind myself where I left off but I did enter a bunch of TikTok ip addresses via the bulk import option but yet I can still access the web site, I am going to do a bit more digging to see if I cant locate more addresses to see if there are others that were missed. Since the kids are back to school my oldest is once again "playing silly buggers" so I have to find a way to clamp down or at the very least log with specific detail (url, duration, frequency, etc) what they are up to so we can decide on how best to address or ban the devices all together (now wouldnt that make me popular). I will regroup and see where I had left off (need to take notes) and go from there. Thanks for all of your help.
-
Something like Tiktok exists over many, many IP addresses. If I was attempting that I would first try using their AS number in an alias via pfBlocker. That usually blocks enough things to make it unusable even if not blocked entirely. Works quite well for Facebook and Netflix. I've never tried it for Tikok.
Steve
-
@stephenw10
Hey Stephen thanks for the recommend, I may give this a whirl. Now the question, how do I find the AS numbers? I did a search for TikTok AS routing and nothing came up, gonna have to do a bit more research. Would they be listed in an internet registry somewhere? Thanks. -
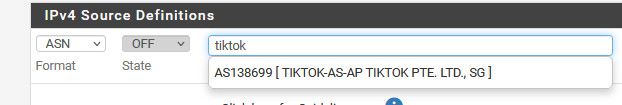
its right there built into pfblocker
But there prob way more than that - because I believe lots of it is hosted on other CDNs
-
Yup. Many, many IPs!
But that's usually enough to break it sufficiently.