Can't access remote network through OpenVPN with allow all firewall rules everywhere.
-
I'm connected to a remote PFSense firewall using OpenVPN. OpenVPN firewall rule on remote PFSense is ...
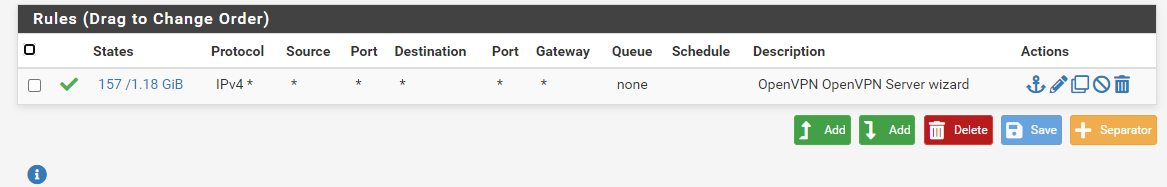
Im trying to get to the security cameras on the SECURITYCAMERANETWORK that has the following firewall rules on the remote PFSense (the top rule to allow all was created for troubleshooting)...
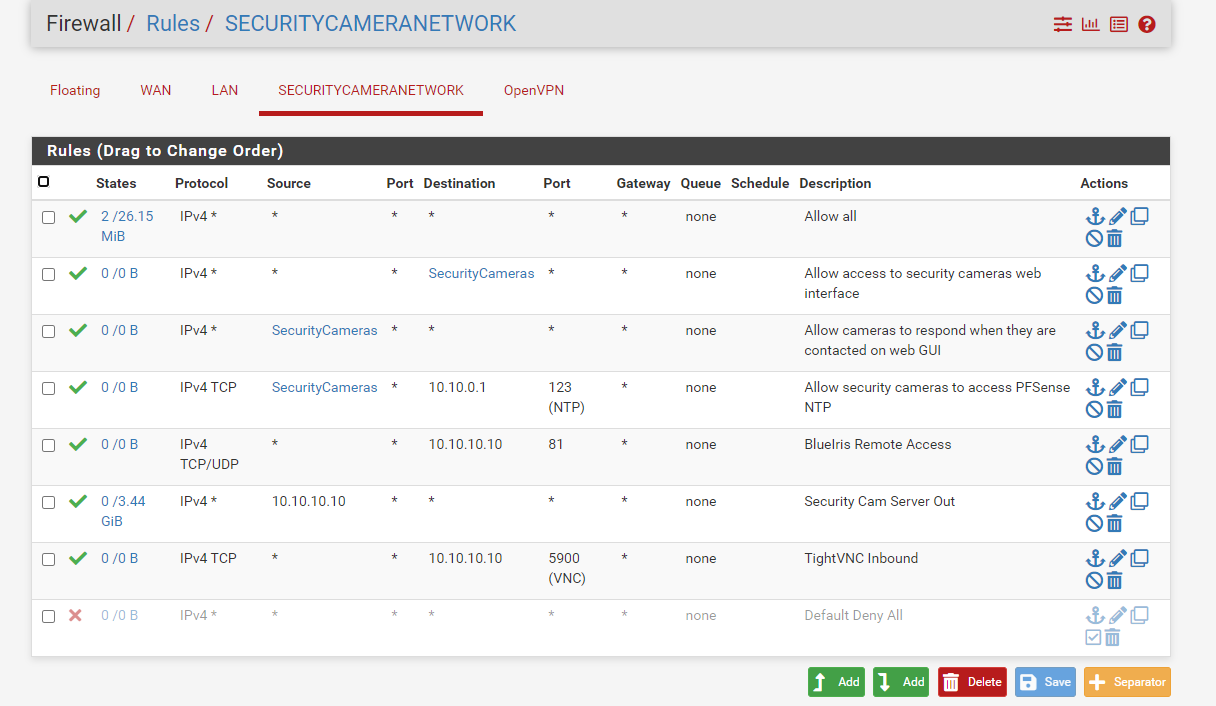
I can't access any cameras on the SECURITYCAMERANETWORK.
I can access the security camera pc at 10.10.10.10 however via tightVNC.
I can't ping anything on the SECURITYCAMERANETWORK through the OpenVPN connection however. I can only TightVNC into 10.10.10.10. From TightVNC running on 10.10.10.10 I can get to everything on SECURITYCAMERANETWORK.
What is stopping me from getting to every thing on SECURITYCAMERANETWORK when I'm connected through OpenVPN?
I don't know what else to do. OpenVPN firewall has a rule to allow all, and I put a test allow all rule onto the security camera network. What is blocking the communication?
-
Remote PFSense is a Protectli vault. OPT1 goes to a GS316EP swich. I just updated the firmware. OPT1 ethernet cable goes to port 14. Port 13 is security camera PC, port 1-12 are cameras...
-
Here are the WAN firewall rules in case they have something to do with it, which I wouldn't think they would...
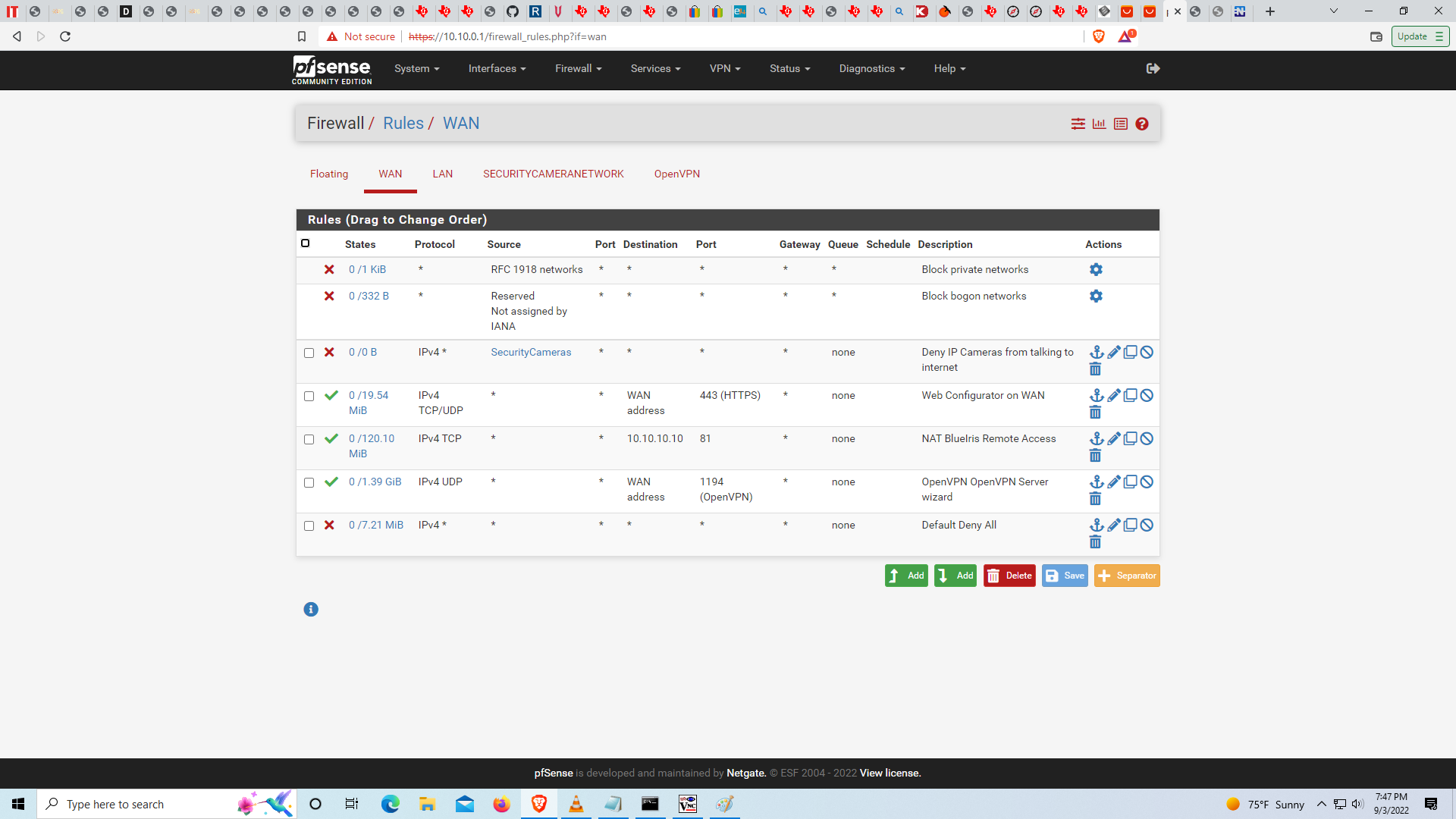
-
It should also be noted that the network I am currently on is a 192.168.10.0 subnet. All networks on the remote PFSense system are within the 10.10.0.0 class B subnets.
-
@skysurf76 said in Can't access remote network through OpenVPN with allow all firewall rules everywhere.:
What is stopping me from getting to every thing on SECURITYCAMERANETWORK when I'm connected through OpenVPN?
Common issues with such devices is they don't have a gateway. So they don't know how to get back..
If you can get to the device on the 10.10.10 network through the vpn, but just not the cameras would mean your routing correctly through your vpn, and that is working.
Can you get to the camera's from your lan for example?
If you can not either then yes that points to a no gateway sort of issue, or a firewall on the cameras (unlikely) but either way doing an outbound nat on the camera network interface so it looks like traffic going to the cameras is coming from your pfsense cameranetwork interface IP that should allow you remote access.
-
@johnpoz I double checked all the network settings in the cameras and everything is working fine inside the the security camera network. I have an identical setup at another location, same cameras even, and am using PFSense there and this works fine. I've tried comparing PFSense settings and they look identical.
From the VPN I can connect to Security Camera PC (10.10.10.10) TightVNC no problem. That appears to be the only connectivity I have to the securitycamera network through the VPN. I cannot ping anything on the security camera network from the VPN.
When I use PING inside of PFSense (Diagnostics>PING) I can ping everything on the security camera network from PFSense.
Something is preventing what appears to be all communication from the VPN to security camera network (other than 10.10.10.10:5900 TightVNC).
Interestingly I can ping 10.10.50.1 (OpenVPN Gateway) and get responses from the security camera PC. If I try the same thing to 10.10.50.2 (current OpenVPN IP on the remote computer) I get nothing. When I try to ping the remote computer 10.10.50.2 from inside PFSense (Diagnostics>PING) I also get no response. Its almost like something somewhere is blocking traffic through the VPN.
In continuing to dig, I started logging the OpenVPN pass rule and got the following...
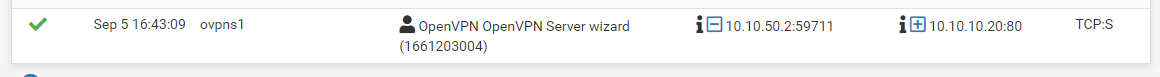
10.10.10.20 is one of the cameras, so the packet is getting passed. Now to see if its getting passed in the security camera network allow all rule...
And I didn't see it in the pass rule on the security camera network. So after it passes the OpenVPN rule, its not making it to the security camera network :/
-
@skysurf76 said in Can't access remote network through OpenVPN with allow all firewall rules everywhere.:
Now to see if its getting passed in the security camera network allow all rule...
The rule there would have nothing to do with it.. You could have zero rules on that interface..
Sniff (packet capture under diagnostices) do you see that traffic to 10.10.10.20:80 when you try and talk to that camera from your vpn - since your seeing it in the vpn rules.
Another problem could be your mask is wrong on the cameras? And they think 10.10.50 and 10.10.10 are the same network, so they never send the return traffic back to pfsense, ie say the mask on the cameras were 255.255.0.0 vs 255.255.255.0
Sniff on the camera interface will tell you for sure if traffic is being sent to the camera and they are just not answering.
-
@johnpoz ANNNNND I solved it. I changed the intermediate OpenVPN network from 10.10.50.0/24 to 192.168.50.0/24. 10.10.50.0/24 didn't overlap with any other networks on either end of the tunnel. No idea why it didn't work? Bug?
-
@skysurf76 they don't overlap but the mask on the camera could be wrong? Did you manually set the mask on the camera or is via dhcp?
-
@johnpoz Yep. I just checked. You got me. Damnit! LOL Rookie mistake.
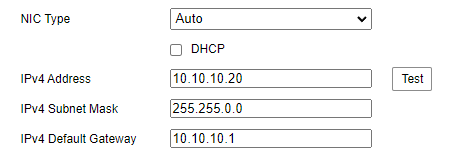
Oh well, all's well that ends well. I appreciate the help!
-
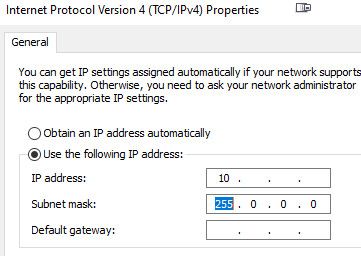
@skysurf76 glad you got it sorted.. Everyone makes typo's - problem also is some of these devices auto fill in the mask for you, I think windows defaults to a freaking /8 when you start the IP with a 10 ;)
-
@johnpoz Yeah I'm going through all the cameras now, and it looks like they have all 255.255.0.0. I can't believe I missed that when I was putting IPs on them. Also I can't believe they would default to a /16 mask.
-
@skysurf76 yeah look at windows - just validated it uses a freaking /8
-
@johnpoz The ironic part is I'm normally a 192 guy, but I didn't want any collisions when I VPNed into the location this thread is about, so I made that location all 10's. Technically I believe that even though 10 is a private range, its still a class A(/8). And 192 is class C(/24).
Doesn't matter how much you know though, the gremlins always come. :)
-
@skysurf76 classes haven't been a thing for like 30 years, ever since cidr came out - believe 1993, classes are no longer really even a thing ;)
But yeah they come up still..
-
@johnpoz Your last post made me feel so old.
Also that the fact somehow in the bowels of mind I know that CIDR means classless inter-domain routing....I think lol.
-
@skysurf76 dude we get old, not feeling it is the secret... The sad part is 30 years ago really doesn't seem like that long ago.. Doesn't seem like that long ago I was running around adding co processors to the pc at the job, and installing tcp/ip via a floppy into windows hehehe