OpenVPN server certificate verify failed on pfSense 2.6.0
-
Re: User Auth Failed
After upgrading to pfSense 2.6.0, my OpenVPN Server has stopped establishing connections. This is the same issue that user @blasterspike and @bpmartin have described experiencing. The connection worked perfectly before I upgraded to 2.6.
System info
Version 2.6.0-RELEASE (amd64)
built on Mon Jan 31 19:57:53 UTC 2022
FreeBSD 12.3-STABLEThe system is on the latest version.
Version information updated at Thu Sep 8 13:08:17 EDT 2022
CPU Type Intel(R) Core(TM) i5-6500 CPU @ 3.20GHz
Current: 2500 MHz, Max: 3201 MHz
4 CPUs: 1 package(s) x 4 core(s)
AES-NI CPU Crypto: Yes (active)
QAT Crypto: NoopenVpn config
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA512
tls-client
client
resolv-retry infinite
remote mydomain.com 1194 udp4
setenv opt block-outside-dns
nobind
verify-x509-name "internal-ca" name
pkcs12 pfsense-UDP4-1194-Laptop.p12
tls-crypt pfsense-UDP4-1194-Laptop-tls.key
remote-cert-tls server
explicit-exit-notifyOpenVpn Log
022-09-07 00:03:40 OpenVPN 2.5.2 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021
2022-09-07 00:03:40 Windows version 10.0 (Windows 10 or greater) 64bit
2022-09-07 00:03:40 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10
Enter Management Password:
2022-09-07 00:03:41 TCP/UDP: Preserving recently used remote address: [AF_INET]xx.xx.xx.xxx:1194
2022-09-07 00:03:41 UDPv4 link local: (not bound)
2022-09-07 00:03:41 UDPv4 link remote: [AF_INET]xx.xx.xx.xxx:1194
2022-09-07 00:04:41 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
2022-09-07 00:04:41 TLS Error: TLS handshake failed
2022-09-07 00:04:41 SIGUSR1[soft,tls-error] received, process restarting
2022-09-07 00:04:46 TCP/UDP: Preserving recently used remote address: [AF_INET]xx.xx.xx.xxx:1194
2022-09-07 00:04:46 UDPv4 link local: (not bound)
2022-09-07 00:04:46 UDPv4 link remote: [AF_INET]xx.xx.xx.xxx:1194
2022-09-07 00:04:52 SIGTERM received, sending exit notification to peer
2022-09-07 00:04:53 SIGTERM[soft,exit-with-notification] received, process exiting -
@jcpingu said in OpenVPN server certificate verify failed on pfSense 2.6.0:
xx.xx.xx.xxx:1194
is your
remote mydomain.com 1194 udp4
right ?
When you did this :
(check your network connectivity)
by looking at the server side == pfSense OpenVPN server, the OpenVPN server log, what did it you see ?
-
Had the same issue. Solution was:
https://redmine.pfsense.org/issues/13424
https://blog.nuvotex.de/pfsense-crl-has-expired/ -
@gertjan said in OpenVPN server certificate verify failed on pfSense 2.6.0:
xx.xx.xx.xxx:1194
Yes, xx.xx.xx.xxx:1194 is my domain ip.
On the server side, i get this:
Sep 9 15:39:59 openvpn 1547 VERIFY WARNING: depth=0, unable to get certificate CRL: C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=Fang, emailAddress=info@airvpn.org
Sep 9 15:39:59 openvpn 1547 VERIFY WARNING: depth=1, unable to get certificate CRL: C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org
Sep 9 15:39:59 openvpn 1547 VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org
Sep 9 15:39:59 openvpn 1547 VERIFY KU OK
Sep 9 15:39:59 openvpn 1547 Validating certificate extended key usage
Sep 9 15:39:59 openvpn 1547 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sep 9 15:39:59 openvpn 1547 VERIFY EKU OK
Sep 9 15:39:59 openvpn 1547 VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=Fang, emailAddress=info@airvpn.org
Sep 9 15:39:59 openvpn 1547 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1601', remote='link-mtu 1602'
Sep 9 15:39:59 openvpn 1547 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo'
Sep 9 15:39:59 openvpn 1547 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sep 9 15:39:59 openvpn 1547 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sep 9 15:39:59 openvpn 1547 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_CHACHA20_POLY1305_SHA256, peer certificate: 4096 bit RSA, signature: RSA-SHA512 -
@jcpingu said in OpenVPN server certificate verify failed on pfSense 2.6.0:
Sep 9 15:39:59 openvpn 1547 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='
Adapt your server - and so client - settings 'compression'
You saw the :
Deprecated.
on the server settings page ? Since OpenVPN 2.5.x 'compression' support is limited and considered "Deprecated".
No cert error on the server side.
Btw : you use a cert from airvpn, a VPN ISP. Thats strange.
On the server side, pfSense, you should use your own main CA certificate like :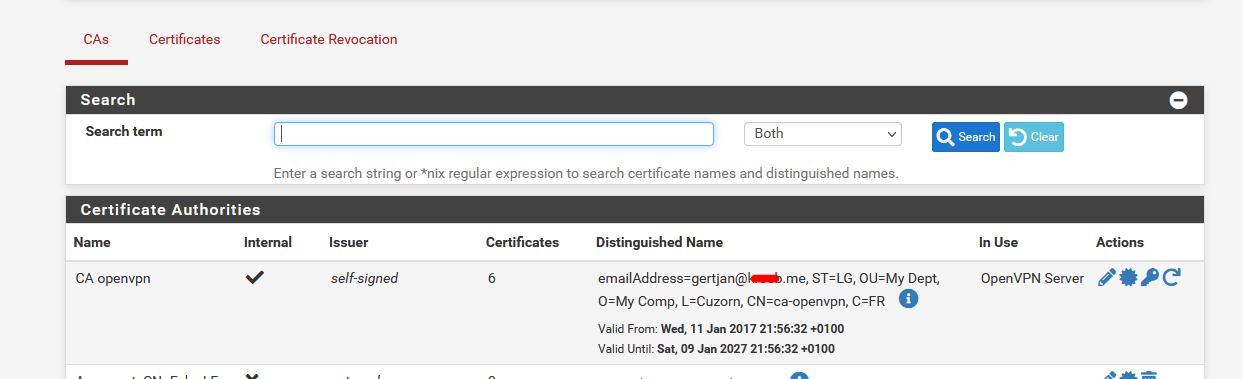
(you have to make one) and a certificate for the OpenVPN server based on this CA :
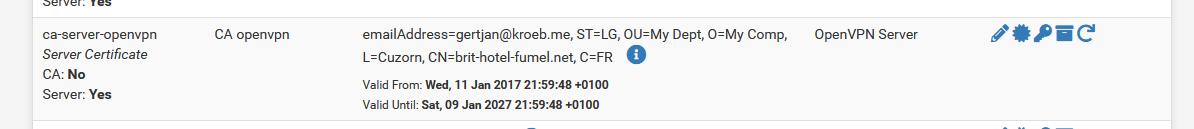
This certificate is used in the server instance :
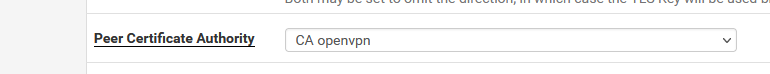
For every openvpn client user you also make a cert :
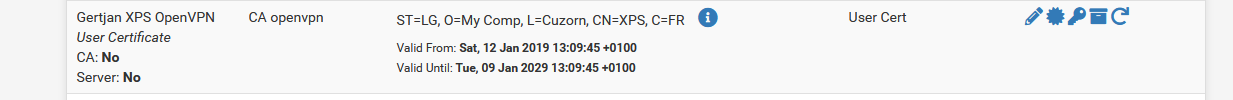
and that one gets exported for 'client' use.
See the Netgate => OpenVPN (Youtube) videos.
-
Which OpenVPN video are you referring to? I had this roadwarrior vpn access working in 2.5.2 fine with no issues. It is only after I upgraded to 2.6.0 that it would not connect.