No-IP Updating DDNS Address from VPN
-
But the 73.x.x.x IP there is the correct one?
You have a different dyndns client that's running on mullvad_vpn_denver?
Are you sure there is not another client running somewhere else that might be updating the ddns.net entry?
Steve
-
@stephenw10 Correct but the most recent events (should have mentioned, I have my log view flipped so newer events are at the top) shows that Dynamic DNS is pulling from my vpn to Mullvad for some reason even though I have it set to only WAN. I will triple check that I don't have any other clients with DDNS enabled but I am 99.99% I don't.
-
And here for a more normal view, now most recent logs are at the bottom but you can still see dyndns is updating from all of my vpns for some reason...
2022-09-28 09:54:32.591314-06:00 php-fpm 22139 /rc.dyndns.update: phpDynDNS (site.ddns.net): No change in my IP address and/or 25 days has not passed. Not updating dynamic DNS entry. 2022-09-28 09:54:36.269588-06:00 check_reload_status 398 updating dyndns mullvad_vpn_denver 2022-09-28 09:54:40.893574-06:00 check_reload_status 398 updating dyndns site_to_site_site 2022-09-28 09:55:44.500746-06:00 check_reload_status 398 updating dyndns site_to_site_site 2022-09-28 09:55:48.069564-06:00 check_reload_status 398 updating dyndns mullvad_vpn_denver 2022-09-28 09:55:53.212823-06:00 check_reload_status 398 updating dyndns WAN_DHCP 2022-09-28 09:55:54.268282-06:00 php-fpm 19444 /rc.dyndns.update: Dynamic DNS: updatedns() starting 2022-09-28 09:55:54.351864-06:00 php-fpm 19444 /rc.dyndns.update: Dynamic DNS noip-free (site.ddns.net): 73.x.x.x extracted from local system. 2022-09-28 09:55:54.351890-06:00 php-fpm 19444 /rc.dyndns.update: Dynamic DNS (site.ddns.net): running get_failover_interface for wan. found em0 2022-09-28 09:55:54.432583-06:00 php-fpm 19444 /rc.dyndns.update: Dynamic DNS noip-free (site.ddns.net): 73.229.x.x extracted from local system. 2022-09-28 09:55:54.432650-06:00 php-fpm 19444 /rc.dyndns.update: Dynamic Dns (site.ddns.net): Current WAN IP: 73.229.x.x Cached IP: 73.229.x.x 2022-09-28 09:55:54.432669-06:00 php-fpm 19444 /rc.dyndns.update: phpDynDNS (site.ddns.net): No change in my IP address and/or 25 days has not passed. Not updating dynamic DNS entry. 2022-09-28 10:00:55.875749-06:00 php-fpm 360 /services_dyndns.php: Successful login for user 'user' from: 172.20.x.x (Local Database) -
Those logs indicate it's checking each WAN, that's what the dyndns updater does. But then is shows it find the expected IP against em0 directly and that's the same as the cached IP.
Those logs do not appear to show it updating the record with the VPN IP address.Try disabling it entirely and see if it still gets updated by something.
Have you ever configured anything else to update that dyndns entry?Steve
-
@stephenw10 So for whatever reason, if when it's cached correctly in the logs with the 73.x.x.x address (my public WAN IP) it still gets updated with the Mullvad VPN public IP and NO-IP DDNS only seems to get updated with VPN IP when I add the firewall rule for LAN to force traffic from my main LAN out of that interface (VPN). Should I be setting up to force traffic out the VPN a different way?
-
@deathgrin Maybe show all rules on Floating and all NAT Outbound rules.
Maybe you have another DDNS Client you forgot about on one of your hosts?
-
@bob-dig I am 99% positive I don't have anything else updating Dynamic DNS besides my pfsense box. Here are snippets of the rules you asked for. I also have manual rules in outbound NAT where I was trying to force all traffic destined for anything NOIP for DDNS updates out my main WAN and not vpn.
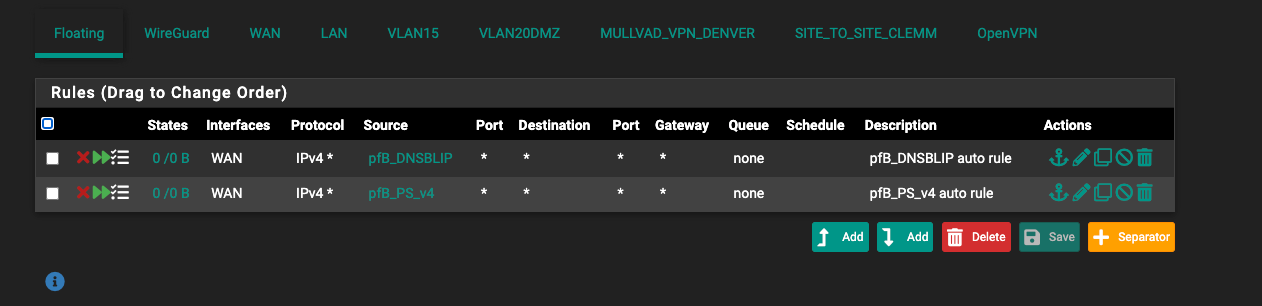
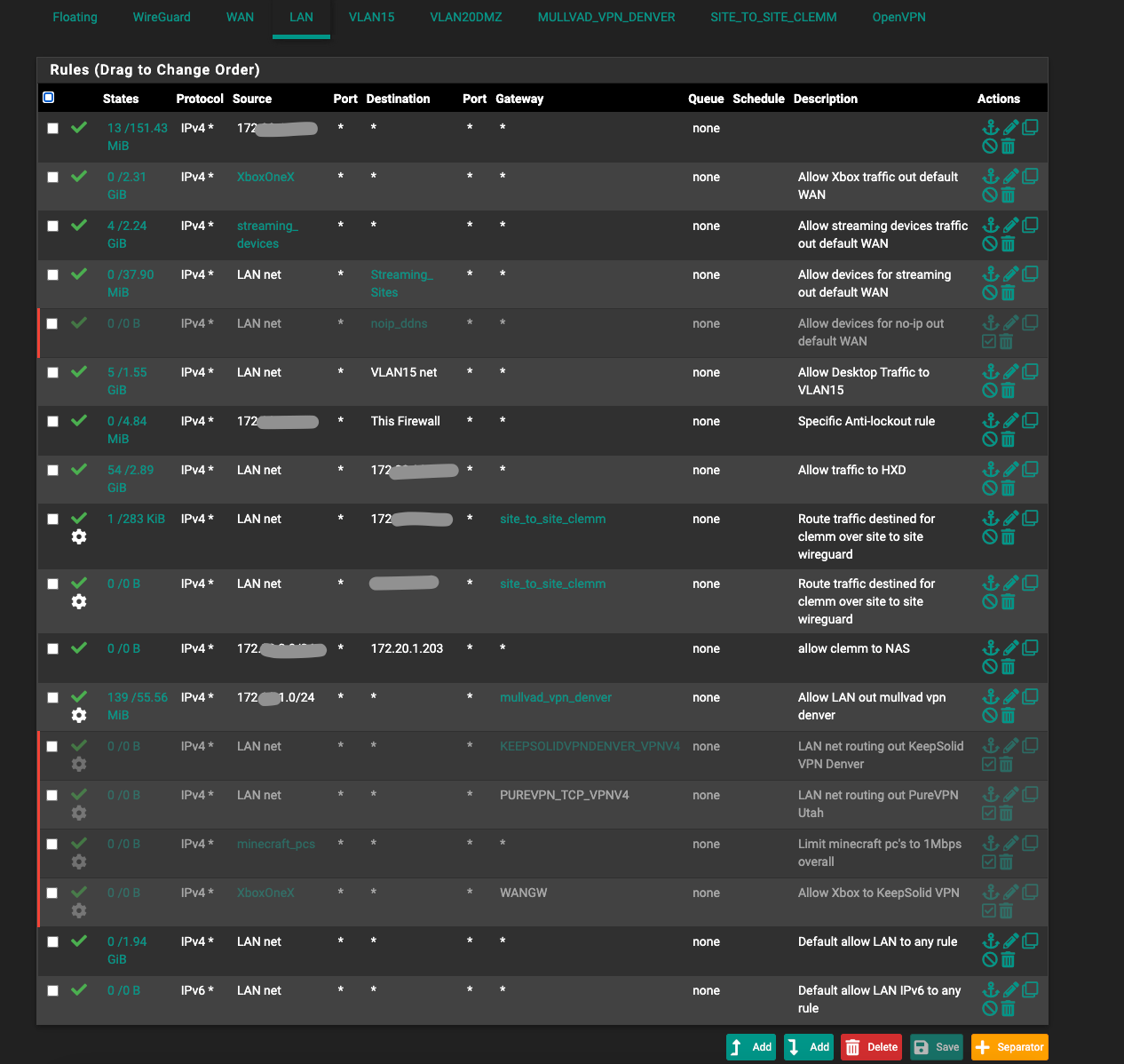

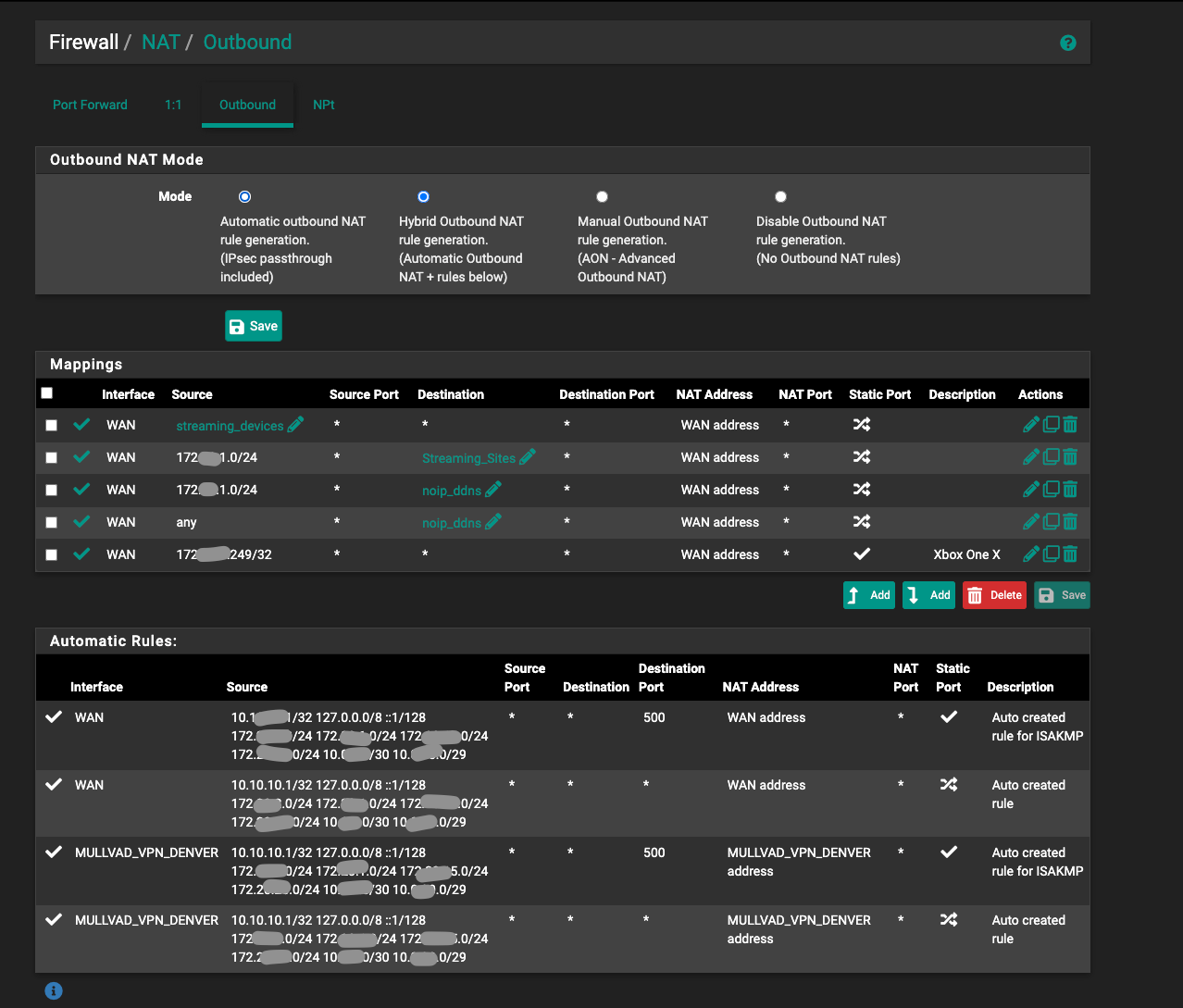
-
@deathgrin I don't think you need any of the manual outbound rules (other then xbox) but I am no expert.
But the rules seem to be ok. -
@deathgrin Default Gateway (SystemRoutingGateways) should be WAN, if you haven't checked that.
-
@bob-dig yeah I have my default WAN manually set to the specific ISP Interface and not set to Automatic.
-
@deathgrin Maybe it is a hiding ddclient on some linux server or in your Access-point or something, I don't think it is pfSense.
-
Technically we haven't seen the port forwards and 1:1 NAT yet, maybe there...
-
It sure behaves exactly like something updating it from the LAN.
The policy based routing rules on the LAN interfaces are never hit by traffic generated on the firewall itself. Even if it's sourced from the LAN interface address. So if changing them affects the ddns client it's almost impossible for it to be the firewall.
Yes, those outbound NAT rules are not required except the static ports rule for Xbox.
The one with source 'any' will be NATing traffic soured from it's own WAN IP back to it own IP which can break things. It should definitely be removed. Using source 'any' in an OBN rule is almost always a mistake.
Steve
-
@Bob-Dig I don't have any 1:1 rules setup but here are my port forward rules. @stephenw10 I have deleted all of my NAT rules besides for Xbox. I have started a tcpdump to monitor for any traffic going to noip update address for my LAN, so we shall see if anything reaches out.
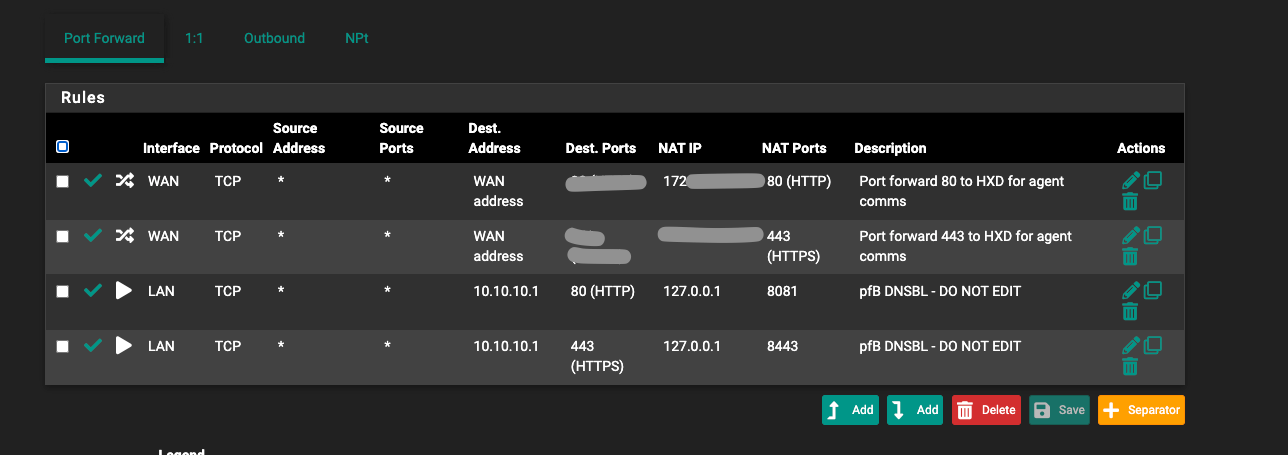
-
You could also re-enable the ddns rule on LAN and enable logging on it.
-
Or maybe change the credentials for No-IP and only update the pfSense DDNS Client with that, if they use those.
-
@bob-dig @stephenw10 You guys were 100% right... lol. I ended up having it configured through my wireless router (which I had setup as ap mode only). In AP only mode, it hides the ddns configuration... (smh). So when I checked it as a possibility it didn't show up. But after monitoring tcpdump I saw it reach out and try to update, so changed it back to router mode and was able to disable it. Thank you all for your help!