how to get IP Attacker into the blocklist
-
@ezvink :
Go read the official pfSense documentation here for instructions on configuring a port forward: https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html. As @Cool_Corona mentioned, you are doing it incorrectly.And as @johnpoz stated, be sure that you are not blocking RFC1918 addresses on the WAN interface for this test. You configure that on the bottom of the page from the pfSense menu INTERFACES > WAN.
-
@johnpoz
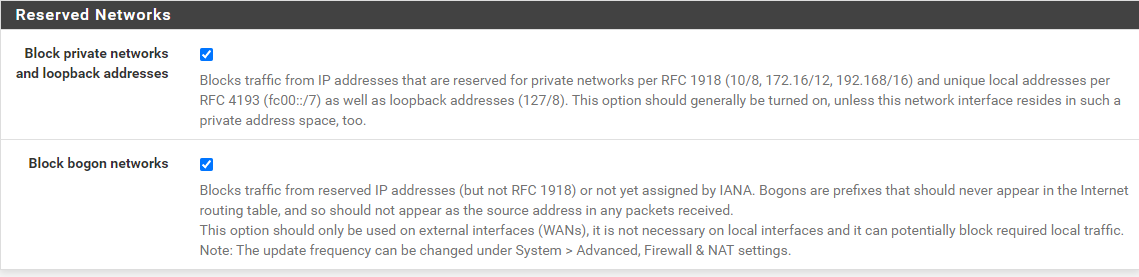
I left this setting by default sir, so which one should I uncheck? both of them?
-
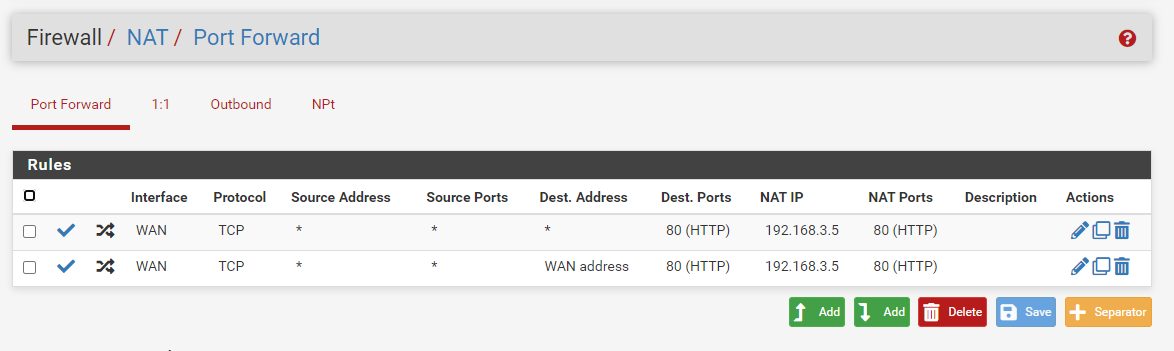
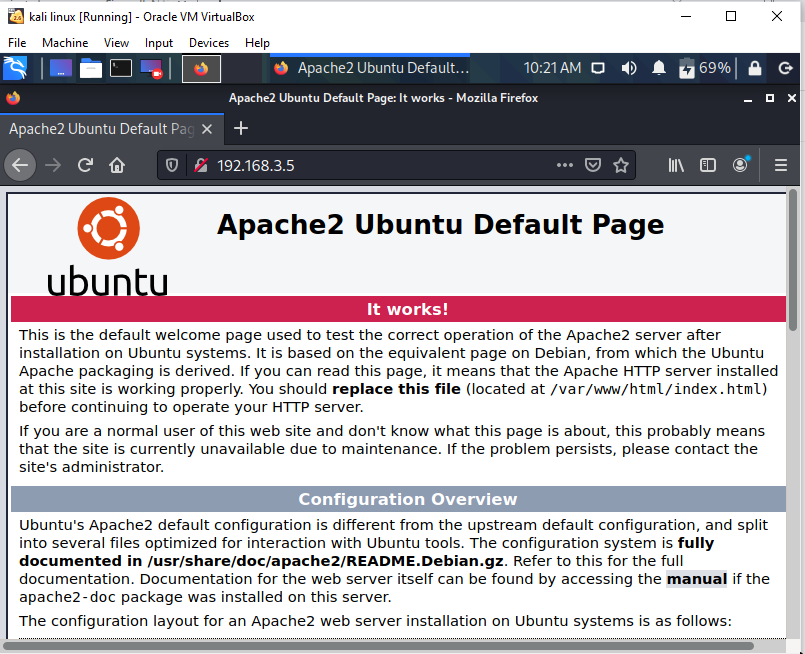
I use port forward like this, and the attacker can access the web server using the same network "bridge adapter" as the pfsense WAN adapter.
but when i try to ping the webserver ip it can't, because my portforward setting is TCP not ICMP. it's like that right sir?Well, but when I tried to attack the webserver's ip address, there was no warning that appeared on Suricata, what do you think is the problem, sir?
-
@ezvink dude just take the F, there is no way you pass this "exam" ;)
-
@johnpoz
Isn't this forum to help those in trouble, right, sir? -
@ezvink we have been trying for what weeks.
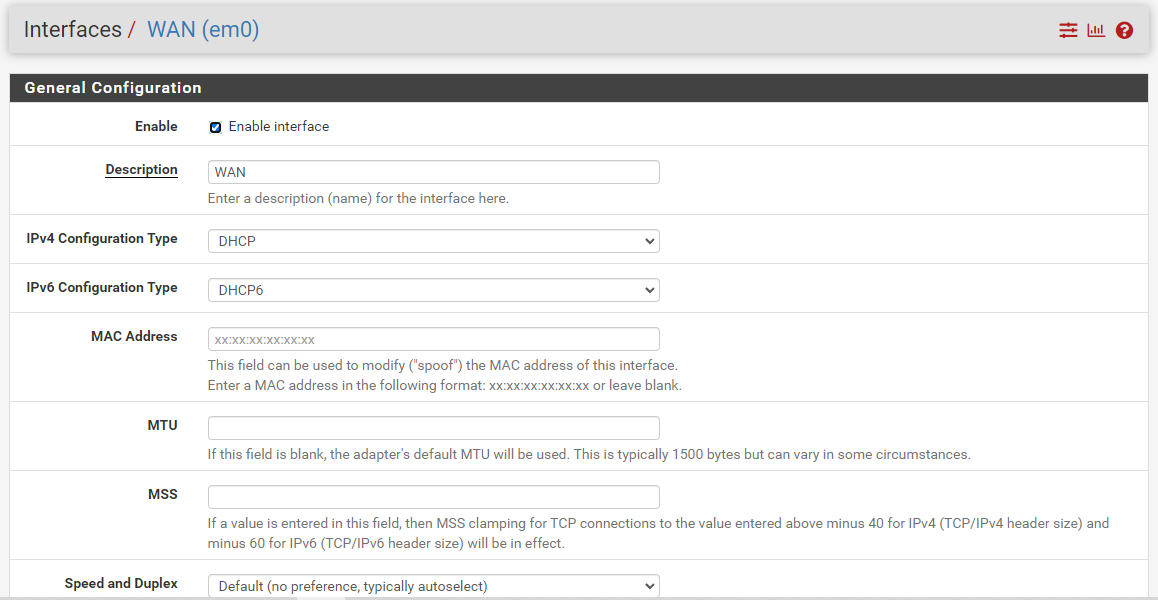
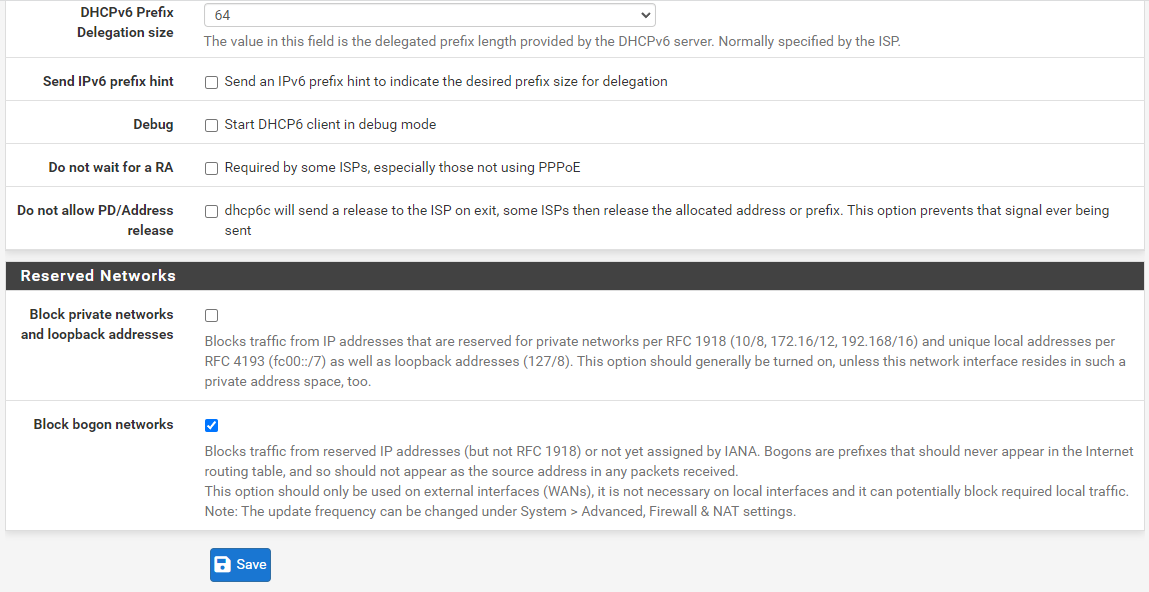
You are asked if you are blocking rfc1918, and where to turn it off - but then you ask which one to check. Which one of those do you think blocks rfc1918? Do you think you have any need to block bogon? How would bogon be source into your wan on a specific network?
Your rule you posted clearly states TCP, but then you ask if your sending icmp? How would we know your the one using hping.. How did your rule trigger before if you were sending icmp?
Asked to see your wan rules - no posting..
Did you modify ips to listen on the wan port now?
Your passlist shows 192.168.18/24 - did you remove that?
-
@johnpoz
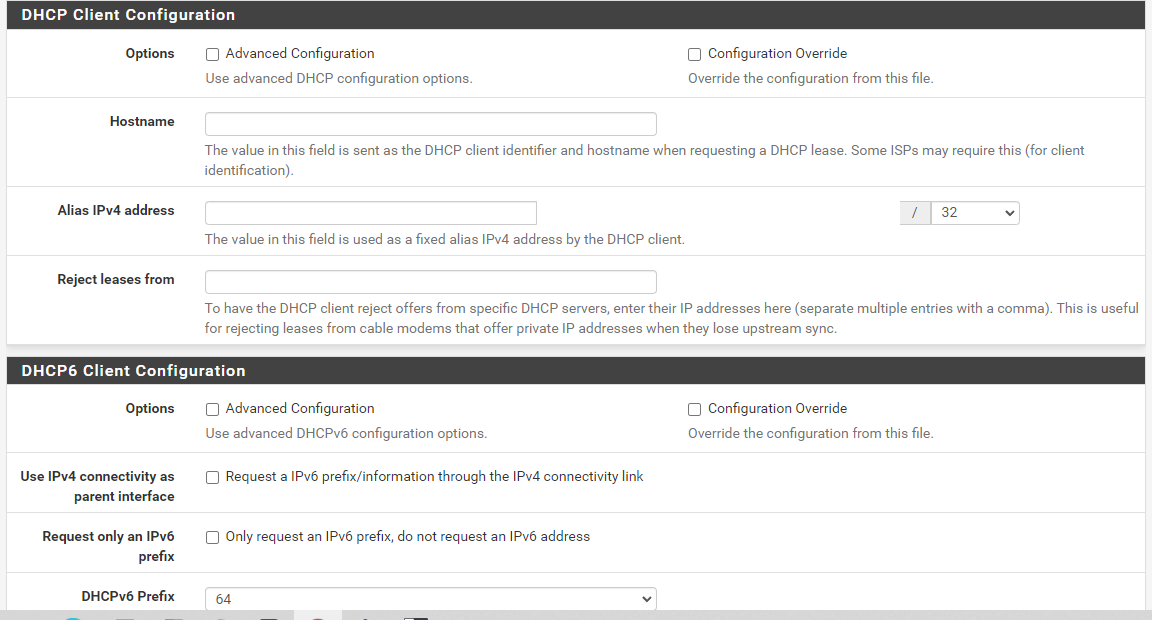
like this sir my wan settings
-
@ezvink
on ips I only add opt1(webserver) interface only
I also didn't delete it, I left it the default sir -
@ezvink If you want some one to do your assignment for you then just pay some one to do it.
If you want to learn to be an IT professional then learn how to do research and test systems your self.@johnpoz said in how to get IP Attacker into the blocklist:
dude just take the F, there is no way you pass this "exam" ;)
agree
@ezvink said in how to get IP Attacker into the blocklist:
Isn't this forum to help those in trouble, right, sir?
The forum is not here to do your assignment for you.
You may not like the honest assistance you have received however if you want technical ability rather then just a grade for an assignment you are not doing, then it is actually more valuable than the many technical pointers you have been given.
-
@bmeeks
Thank you sir, because of your suggestion the project I am working on can run well. thanks again sorry if i confused you -
Before attacking, finish first the basic setup.
I mean, this :
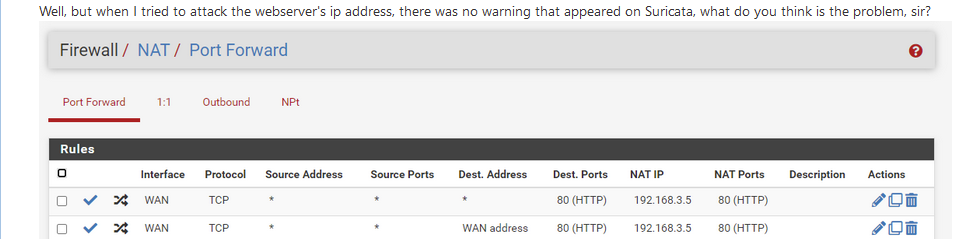
is not done any more.
http over port 80 is something of the past, as all traffic passes very visible over the internet. That the opposite of 'security'.
Google, for example, won't index http sites any more. Browsers start to show warnings when http is used.
The solution has been found a decade ago : use https over port 443.
So, add a new NAT rules, same settings as the "port 80 rule", but now you use port 443.
And do not forget to tell apache2 that it should listen port 443 also.
And consider disabling port 80 (http) functionality all together - and if you do, ditch the port 80 pfSense NAT rule.When done, you can start thinking about 'security'.
One of the best starting points would be : leave the /var/www/html/ folder empty, just keep the index.html file and don't edit it.
Do not install "PHP" (Java, whatever) as this would open up a whole new set of angle of attacks.