FTP accesable on LAN, but not to port forwarded WAN on public IP address.
-
@stephenw10, this is the first time I have setup a port forward like this, so I may have done something incorrect. Let me ask this, it is easier for me to change the data channel port range rather than update all of the devices to look a new FTP port. So if I start the range from 50023- to 60000 and keep the FTP port at 50022. What should the settings look like on the forward rule? I had to have a Redirect target port, so I presumed that was the port I was sending to on 50022.
Thanks,
-
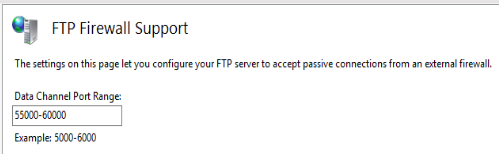
Yes, you can do that, probably don't need anywhere near that number of ports either. So 55000-60000 would be fine.
The destination and target ports should 50022, yes.
It was being caught by the other rule because the port range overlapped and presumably you put that rule above the single port rule. And because you had entered the start port as 50022 it ended up on a different port.With those changes the initial TCP connection should succeed. It may still fail when it switches to the passive data range though. We shall see...
Steve
-
@stephenw10 so I changed my server data channel port to 55000-60000.
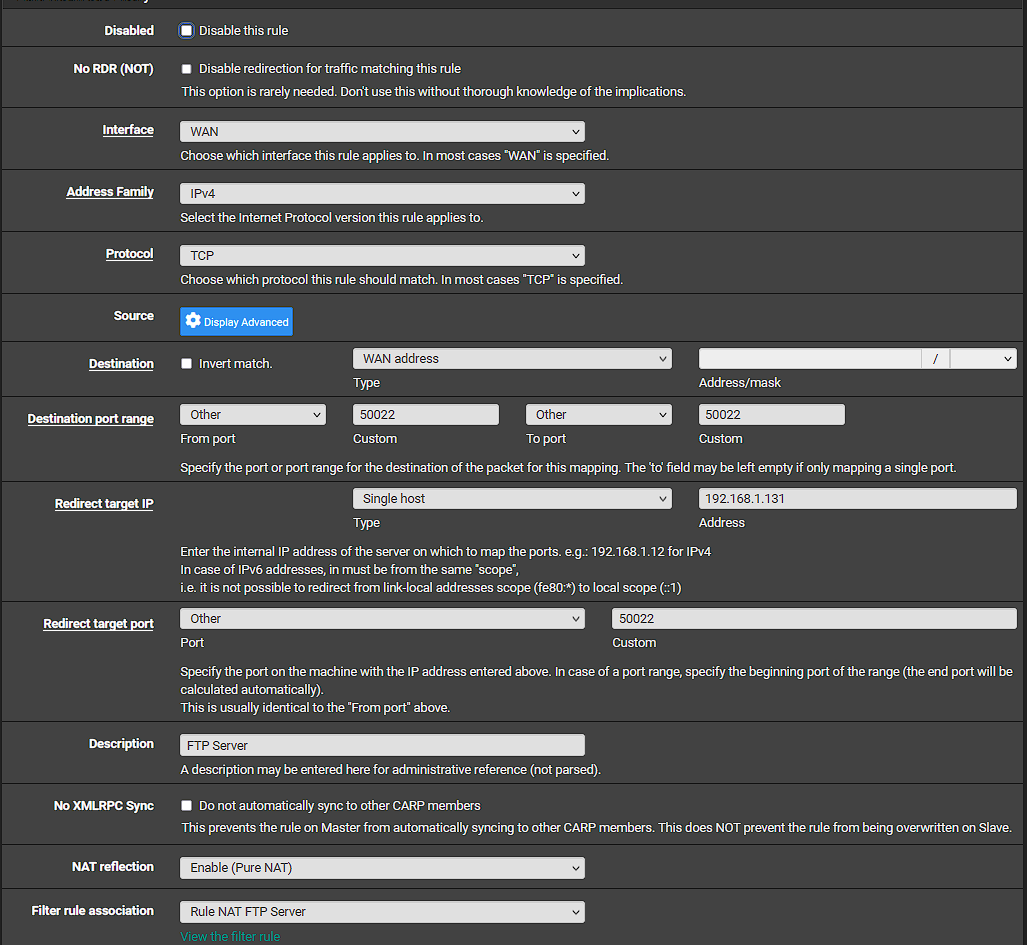
Here is what I modified the NAT rule to be:
I ran another capture on pfsense after these changes:
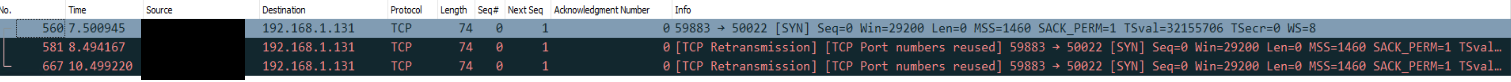
Here was the wireshark:
-
So to be clear you should have two port forward rules. That one for the FTP port, which looks correct. And another one for the passive mode data port range.
That pcap was on the pfSense WAN I assume?
If you pcap on the internal interface or the mirror port do you see traffic there?
Do the states in pfSense look correct?
Steve
-
@stephenw10 I did not have 2 rules. I made a NAT rule for the data ports. Does this look correct?
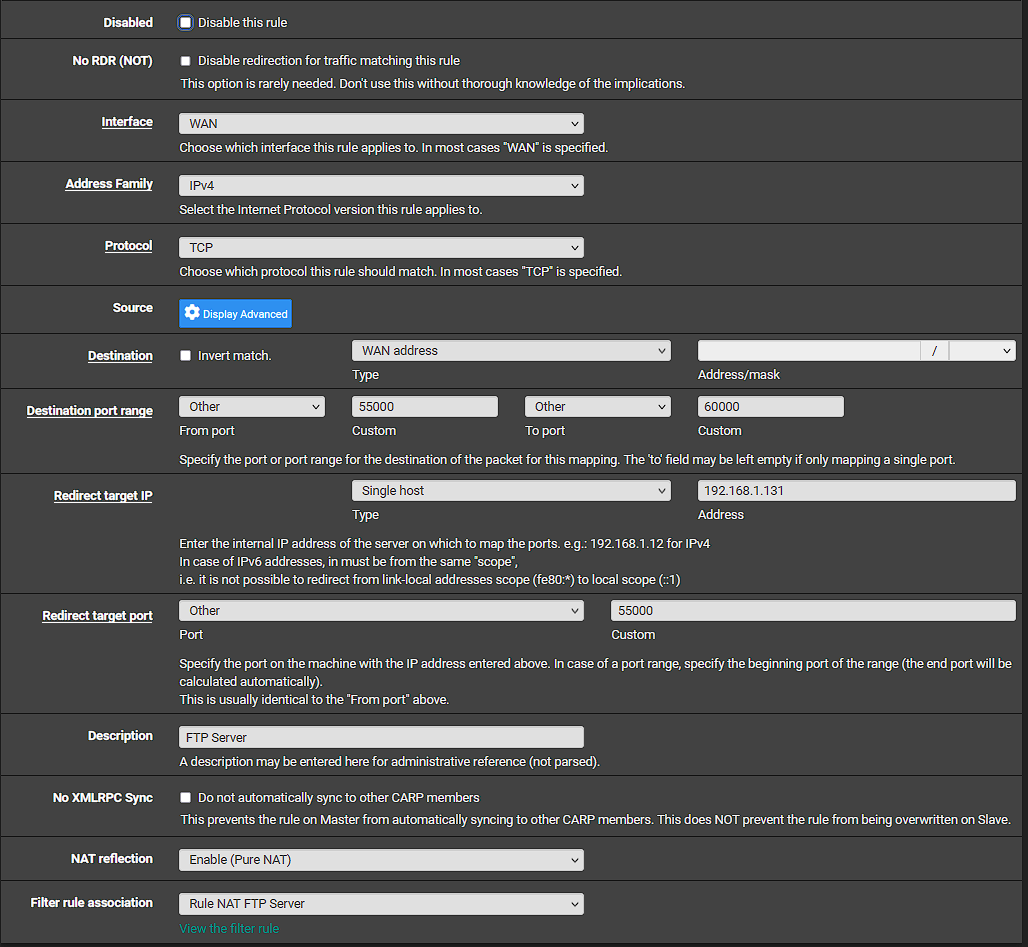
In regard to the pfsense capture, yes that was on the WAN.
On wireshark mirror port I am still only seeing the 3 SYN requests.
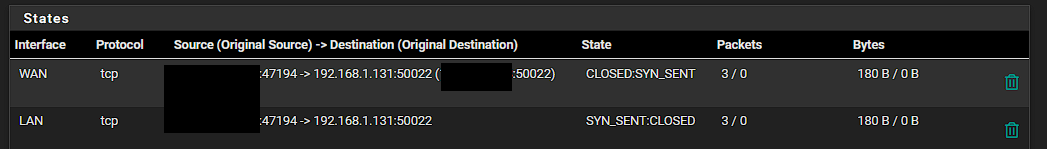
Here are the states:
-
Ok, that all looks correct. The states are being created as expected also.
With that result it's almost certainly the server blocking the connection or unable to respond.
So that would a local software firewall rule on the server only allowing traffic from within its own subnet (the Windows default).
Or a lack of a route to be able to respond. Can the server ping out to external IPs in general?Steve
-
@stephenw10, good morning. So I worked on this some more last night, and have still not completed it, but I believe I am farther. I tried to ping the source IP from site2, and it failed. I then tried to do a packetrt that resulted in 30 timeouts.
From here I tried to log into the router at site2 and when the captive portal would display it would not take my credentials. I then observed blocked traffic that I was not seeing before from Snort to that IP. I found this was also the case of why I could not ping. However after suppressing ICMP, and the alert for the captive portal I can now login to the site2 router, but I still can not ping. I do see allowed traffic hitting an any source, any port open to that IP address. I even stopped the Snort service thinking that if it is not running, it can not filter against the block lists, but that did not seem to help.
So, I still can not get the FTP from the site2 to work at this point. Just wanted to give an update. Thanks again for your help.
-
It doesn't look like a problem at site 2 to me because you are seeing the FTP traffic arrive at site 1 and be forwarded to the server. The server just never replies.
Either the server is blocking it or it's trying to reply via the wrong route or has no route.
Can we assume the server itself is able to ping something external? Can it ping site 2 dircetly?
Steve
-
@stephenw10 said in FTP accesable on LAN, but not to port forwarded WAN on public IP address.:
Either the server is blocking it
This would be my bet, while if you enable ftp on the server it might prompt you to open the port in the firewall. I find it unlikely its smart enough to open the new 50022 port you changed the ftp to listen on.
As stated already, if your seeing a state created that traffic was sent to your ftp server, and you see no reply, this screams an issue with the server your sending too. Or your sending to the wrong IP?
If you sniff and see the traffic hit your ftp server pfsense wan. Next step to prove to yourself pfsense is sending on the the traffic, sniff on the lan interface - do you see traffic being sent to 50022.. The states should prove that too you already, but seems you need more proof its something with your server, so do a simple sniff.. Pfsense has no control making something reply.. It can only send the traffic on.
Common issues
Firewall on host your sending too.
You have the wrong IP your sending too
The device your sending too isn't even listening on the port your think it is.
The device your sending too doesn't use pfsense as its gateway. -
@johnpoz hello and good morning,
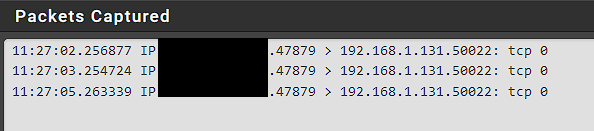
I ran a pfsense capture on the Lan, and can see the inbound traffic.
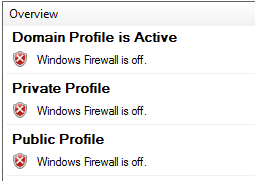
I had disabled the firewall on the server for testing to ensure there were no issues with it, and have left it off.
Here is the configuration for the IIS FTP.
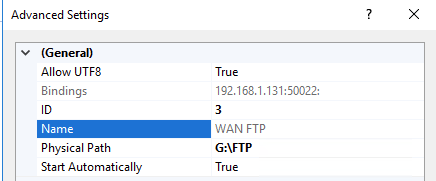
I spun up one of my Kali VM's and ran an NMAP against the port just to show. I know it works as the local pointed to the WAN IP works with no issues. Just the remote that does not work.
Here are the gateway settings on the server.
Here is the pfsense gateway address.

Let me ask this. You mentioned prior that IIS was not very good for FTP. I just set it up because it was already on the server. Is there another option opensource that I can install and use that may work better?
Thank you,
-
Almost anything is better than IIS IMO.

Reolink seem to suggest a server in their docs.I can see no reason why it wouldn't be responding from what you've posted but clearly it isn't. Choosing a high level port like that can often hit some unexpected issues.
You could change the port in IIS back to the default 21 and then just set the port forward in pfSense to forward incoming traffic on 50022 to 21 internally.
Steve
-
@regilayt filezilla ftp server is free.
Clearly your packets being sent to the box, most likely a firewall issue. Since you can see traffic being sent to this .131 IP
You running any other security software on the box. Firewalls quite often will allow local network, and block remote networks, etc.
So your using pure nat, so guess what the source is when you come from local network and hit your wan IP..
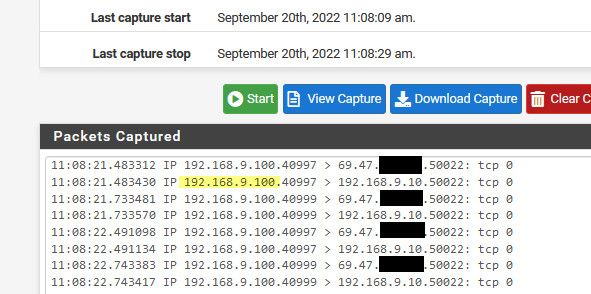
Firewall most likely would allow that since the source is local.. I hit my wan IP from my 192.168.9.100 box, with a port forward set to send that to my 192.168.9.10 box.. See the sniff on my lan interface sees the traffic to my wan IP, and then look how it sends it on to the 192.168.9.10, the source is my .100 address.
I have nothing listening on my 9.10 on port 50022, just wanted to show you what happens with a pure nat, to why that would be working, but might not work from a remote IP since quite possible a firewall is blocking it. Here is the thing your seeing the traffic sent to the .131, its not a pfsense problem if you do not get a response..