LAG or use two physical switch ports?
-
I have the 4100 Max and a Netgear swithc that supports LAG. I have 5 VLANs, all VLANs are on IGC0. Port 24 uplinks to IGC0 and that port is tagged with those VLANs.
Is there any performance gain if I were to:
- LAG to ports together on the Switch and Netgate
or - Use Port 24 for Primary VLAN and the least used VLANs and uplink to IGC0. Then use Port 23 to uplink to IGC1 and configure that for the 2nd most used VLAN
- LAG to ports together on the Switch and Netgate
-
@creationguy putting the interfaces that will have the most intervlan traffic between them on their own physical interface is a way to control the flow of data where most used.
While throwing all your vlans on a lagg might be a simpler way of doing it, if you don't have any clue to what vlans talk to each other the most, or the amount of your data flow isn't enough to worry about, etc.
Breaking out your most traffic vlans to their own physical interface gives you control. I have most of my networks on their own physical interface. But share vlans on 1 physical port for my wifi networks - they have less traffic, no client could ever use full gig anyway. And they never talk to each other anyway. Its always a wireless client talking to a wired device on its own physical network. Or they are just talking to the internet.
Your the only one that knows what talks to what, so you would be the one to decide if you should break out some networks to their own physical. You also need the ports to be able to do this - the more ports on your router and the more ports on your switch give the flexibility to do what makes the most sense for your network.
The problem when you lag and just throw all your vlans on the lagg is you have no control of what will haripin and what might not hairpin.
-
@johnpoz
I think that I will start with moving my CAMLAN VLAN to IGC1 and port 23 on switch. LAN and Proxmox VLAN talk to each other a lot, maybe I'll put Proxmox on IGC2 as well. -
@johnpoz I'm a little lost now. I enabled VLAN 90 (CAMLAN) on IGC1. DHCP and firewall rules were copied over from the old CAMLAN configs. I deleted the old CAMLAN config from IGC0. It seems that all of that is correct.
On the switch, I configured Port 23 which is connected to IGC1 to:
VLAN member: 1,90, VLAN Tag: 90Port 24 which is connected to IGC0 to:
VLAN Member: 1,10,20,200. VLAN Tag: 10,20,200I took 90 from 24 and placed it on 23. Devices can no longer communicate with devices on 90 VLAN.
-
Hmmm, I think what the problem was that under interfaces, I disabled IGC1 so it wouldn't show in the Firewall as a configurable option. I had VLAN 90 attached to IGC1 and that is enabled and configured for DHCP.
IGC0, by itself, needs to be on? Can I just leave it with no IPv4 config and no DHCP? Do I need FW rules on it since it's not being used?
I do have FW rules on VLAN 90 connected to IGC1. I don't think that I'm doing a good job explaining. Here's some screen shots:
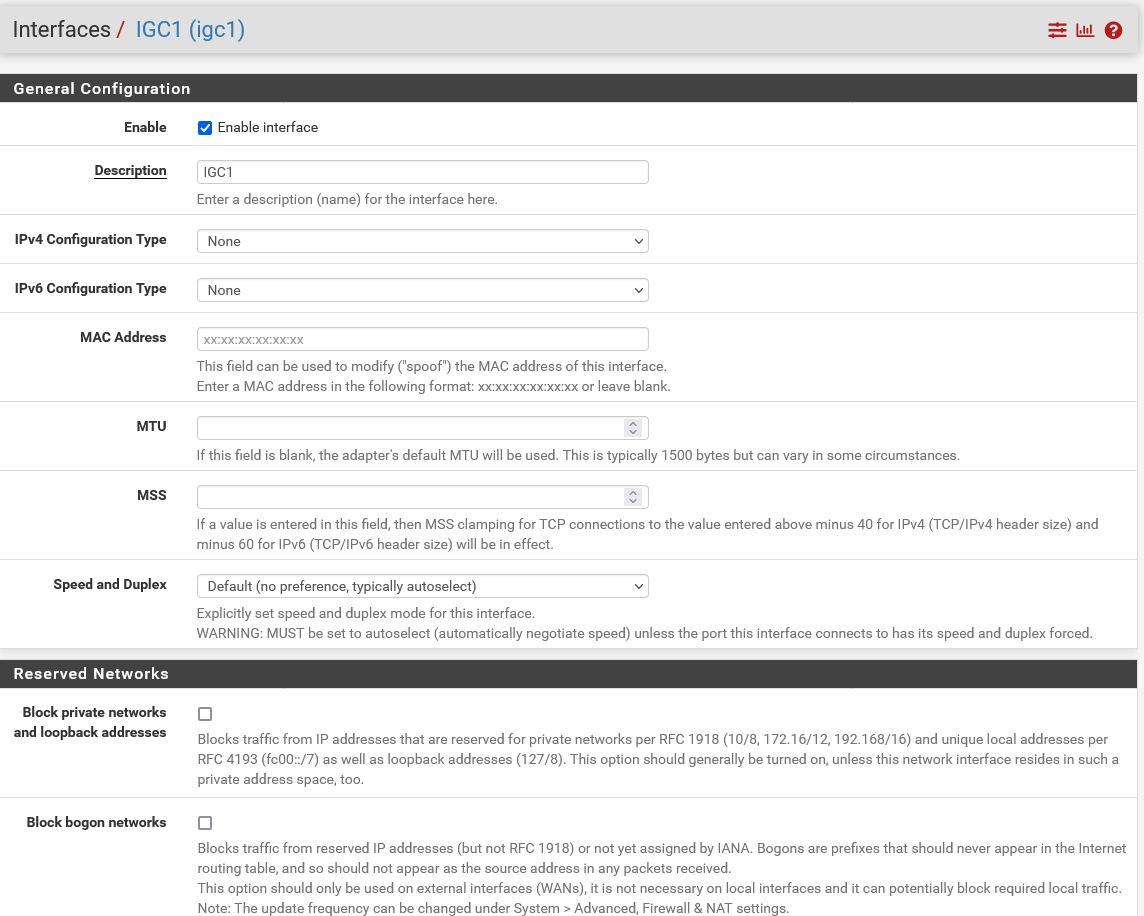
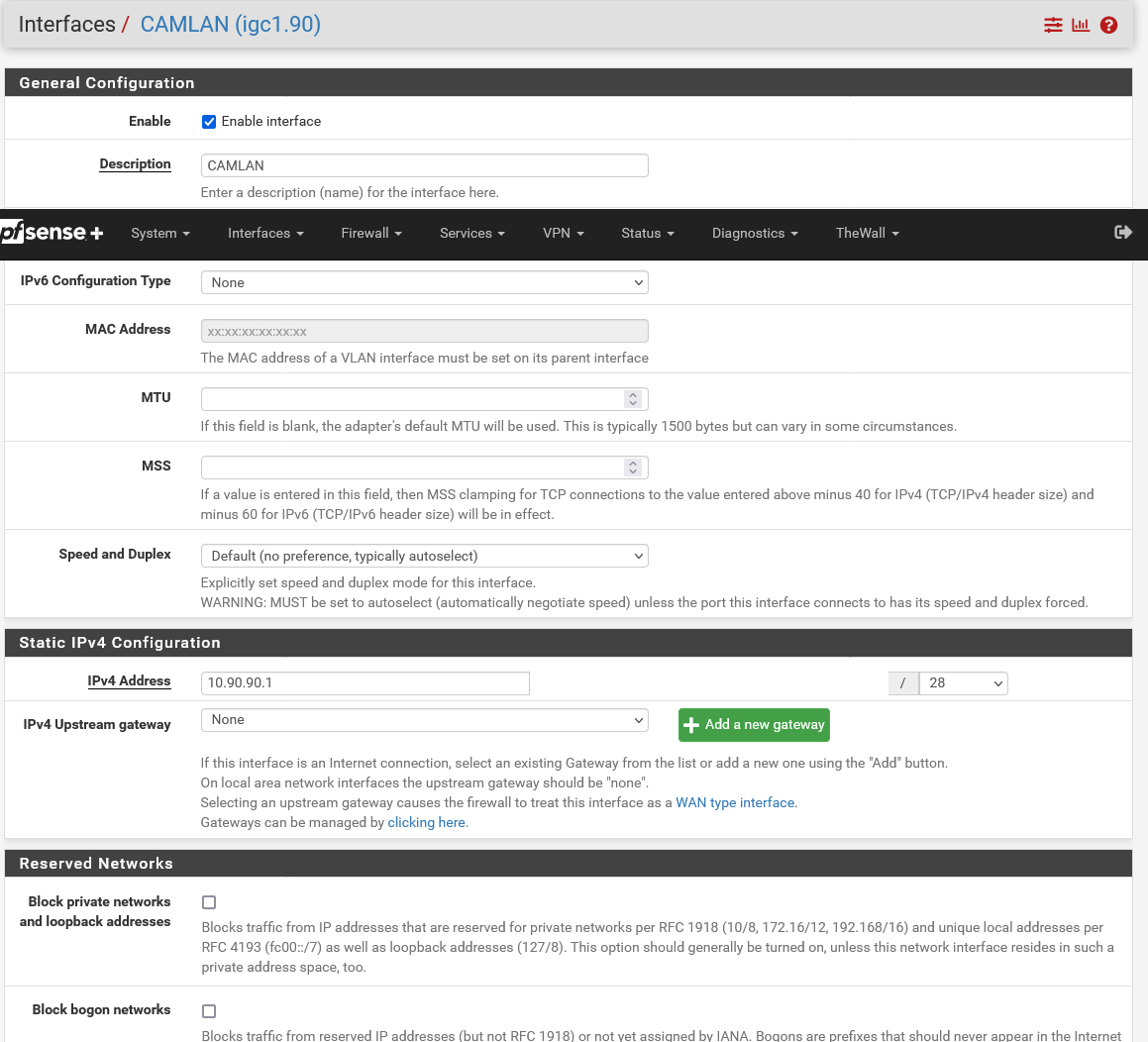
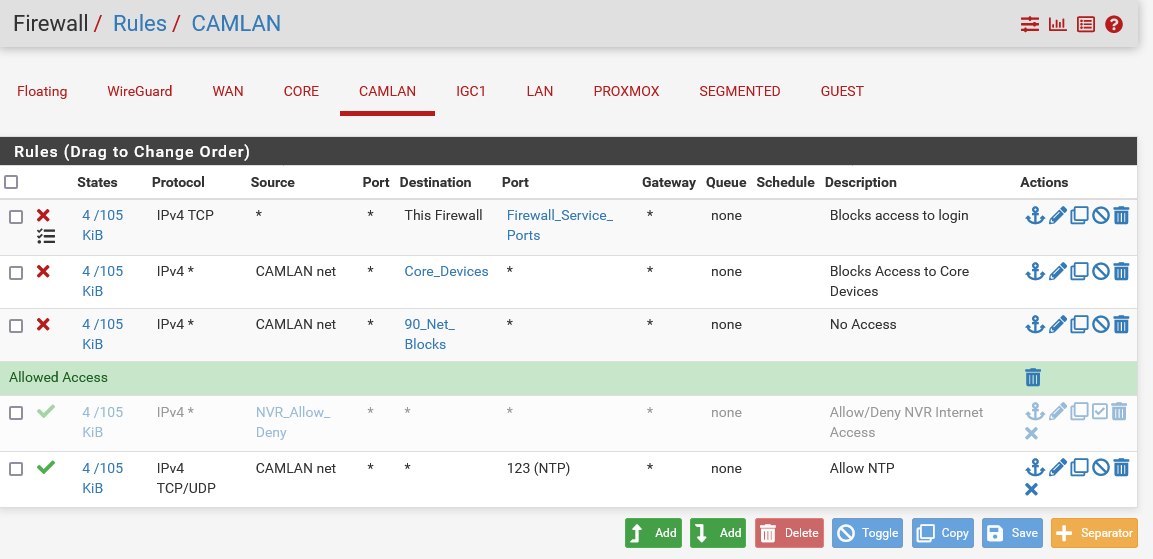
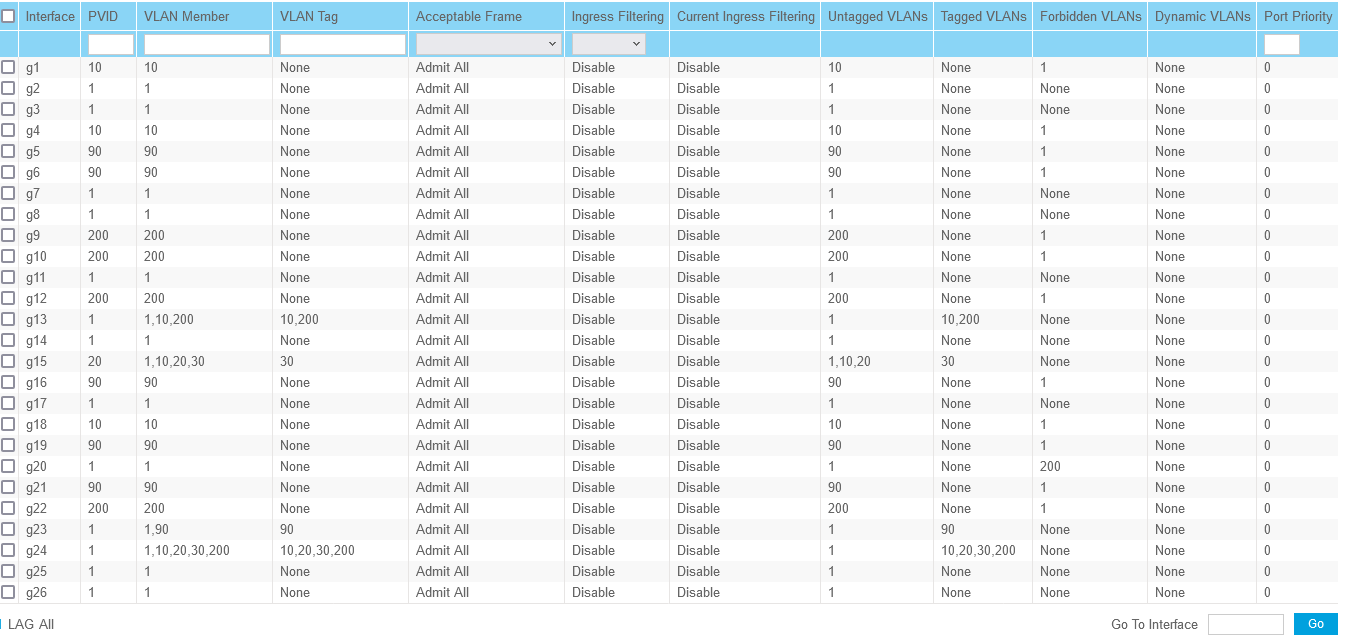
-
Just wanted to bump this
-
@creationguy this makes no sense
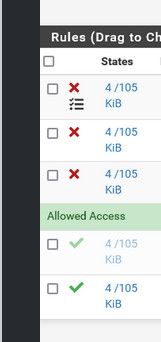
How would all of these rules show exactly the same amount of traffic? And how would block rules have active states?
Did you copy these rules.. I am thinking they all have the same RID?
Nor do I understand why you have g23 and g24 both in vlan 1? Makes no sense to do that.. You didn't bridge igc0 and igc1 did you? How would they have vlan 1 traffic on them? That would be native untagged traffic..
-
@johnpoz said in LAG or use two physical switch ports?:
Did you copy these rules.. I am thinking they all have the same RID?
Smells a bit of
https://forum.netgate.com/post/1063789 -
@bingo600 said in LAG or use two physical switch ports?:
https://forum.netgate.com/post/1063789
sure does - what version of pfsense are you running, are you on a 2.7 snapshot? There was another thread around here where that happened as well. Took a bit to find that one, have to see if I can find it.
But just don't see how all 4 of those rules could have the exact same amount of traffic, and the same amount of active states. How does a block rule ever have a active state? I have never seen that, shouldn't be able to happen because the firewall rule blocks traffic before a state is ever created.
Or wait - maybe the thread I am thinking of is when he had changed the interface names in the xml, and his aliases were not working.. So many threads - heheheh.. But yeah what your seeing there with the states and traffic - something is not right that is for sure.
-
@johnpoz I'm on 22.05-RELEASE (amd64).
I did use the Copy button, should I not have done that? I used it to copy from the old camlan vlan, thought it would be easier.
With this switch, I need to have vlan 1 on there or I can manage the switch. No bridging.
edit: Rebuilding the rules now.
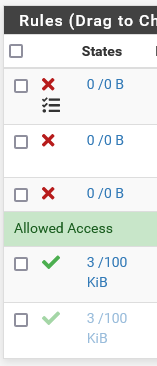
I think I know the answer, but do I need to have IGC0 enabled in order for IGC0.90 to work? It appears that way. If so, I guess I'm all set?
Is there really that big of an issue with the vlan 1 on 23 and 24? I could remove it from 23 and see what it does but in the past its caused problems.
-
@creationguy you should not have vlans enabled on ports that they are not viable on. putting those ports in vlan 1 means any untagged traffic seen will be in vlan 1 per your pvid, and any broadcast traffic that is in vlan 1 will go out those ports, etc.
There is zero reason for those to have vlan 1 on them, unless you want untagged traffic in and out and in your default vlan. And how would that be on both of them.. It makes no sense..
And your bottom 2 rules still seems like same RID..
-
@johnpoz I'll rebuild those, did not notice that. Thank you.
I am learning this VLAN stuff trial by error... mostly by error. I'm trying to scratch together how to do this with this particular switch so I do thank you for the help.
I changed port 23 as show and I can still reach the cameras and nvr.
Port 24 is connected to IGC0 on the 4100, I have VLANs set up on that interface, the ones you see in the screen shot. How should I have the PVID set on that?
Port 13 is my Access point that, 10 and 200 are the VLANs for LAN and Guest.
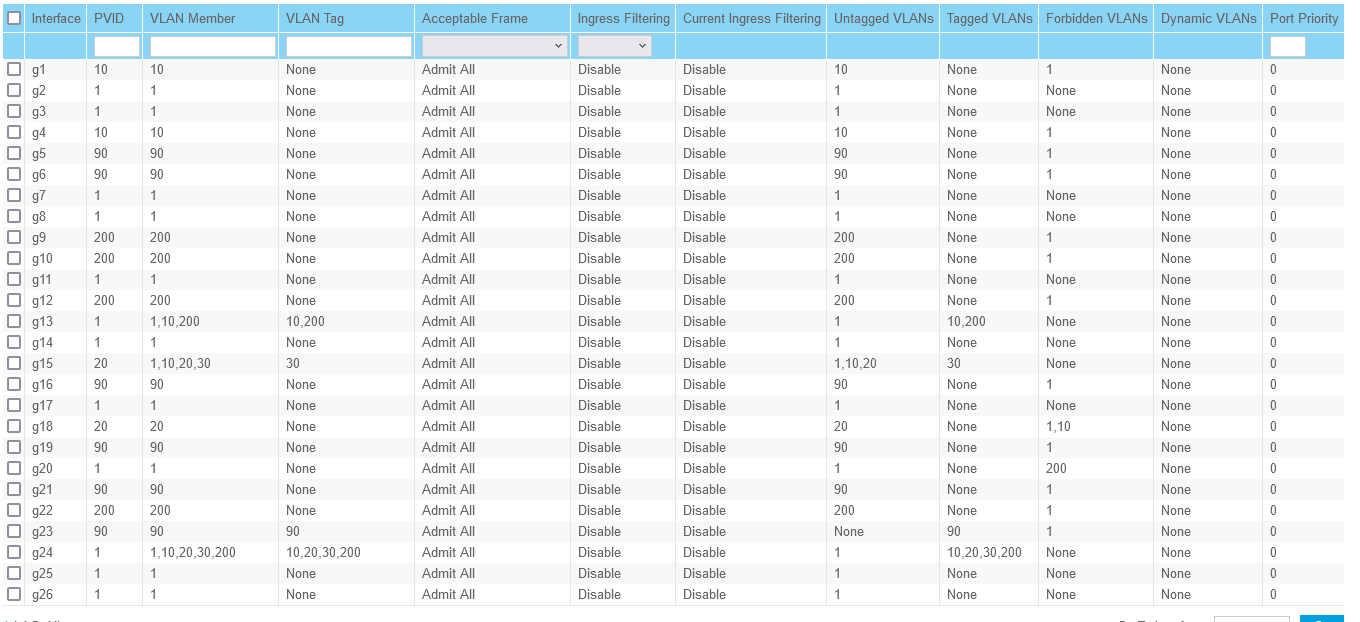
-
@creationguy pvid should be what vlan you want the traffic in if for whatever reason there is untagged traffic seen into that interface.
Do you have a IP set directly on the interface? That would be untagged, and the pvid should be set to what vlan you want that on your switch.
-
@johnpoz said in LAG or use two physical switch ports?:
@creationguy pvid should be what vlan you want the traffic in if for whatever reason there is untagged traffic seen into that interface.
Do you have a IP set directly on the interface? That would be untagged, and the pvid should be set to what vlan you want that on your switch.
I'm not sure if you're referring to port 24 and PVID or the WAP. I need to have port 24 have those VLANs list, I can only enter 1 PVID for that port so I don't know what what it should be without breaking anything.
If you're asking about IP on the interface, for IGC1, no, no IP is configured.
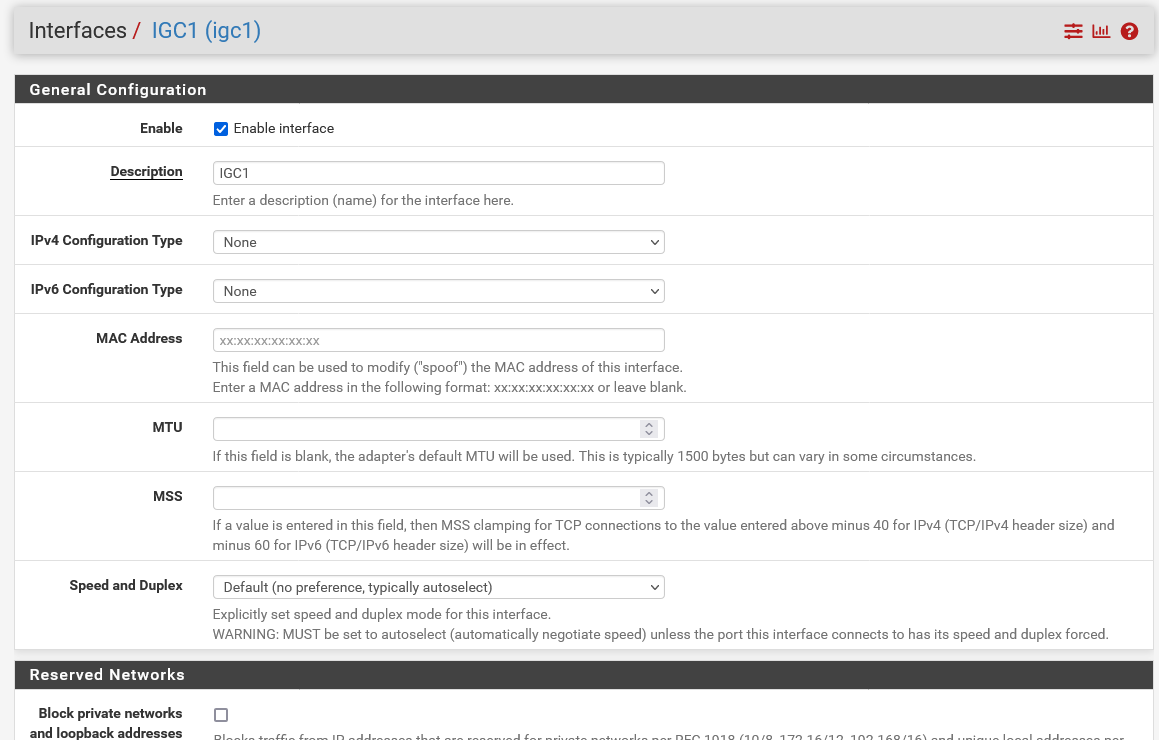
-
@creationguy if there is no IP on the interface - how could you have traffic untagged and if you did why would you want it on vlan 1?
What interface on pfsense is in vlan 1? Any of them?
-
@johnpoz I may have configured the interfaces incorrectly. IGC0 is named "core", I have LAN, on IGC0.10. Core does have an IP of 10.0.0.1, that interface is untagged. When I first set this up about a month ago, I thought that I had to use the untagged interface.
-
@creationguy said in LAG or use two physical switch ports?:
I thought that I had to use the untagged interface.
You don't have too.. If your not going to run multiple vlans on the interface there is little reason not too. I run a untagged vlan even on the interface I run other vlans on. Its just not 1 in my case on the switch.
But vlan 1 which is the default vlan of the switch, doesn't have to be used, and for sure should be removed from any ports where your not using it.. This could be the switch vlan for your untagged interface in pfsense network, but it should be removed from all other ports on the switch that you do not want in that network, etc.
-
@johnpoz On IGC0, I have the 4100, WAP and the Switch "utagged", would I just change the PVID on those ports, 24, 13 to say VLAN 2 or whatever I am not using?
-
@creationguy If your running tagged only on the port.. Then yeah it would be best to set the pvid to the vlan you want any for whatever reason untagged traffic that might hit that interface to be in.
Might be best to use some black hole vlan ID there, other than the default vlan 1. For example you create a vlan 666 for example. Add ports that are disabled, or ports that should never see untagged traffic set the pvid to that.. This goes nowhere only to other disabled ports, etc.
if your not using vlan 1 actually for anything, that could be your "blackhole" or disabled vlan ID sure..
If you are actually using vlan 1 for other untagged traffic, ie an interface on pfsense has an IP directly on its interface, then your other interfaces that only have tagged traffic should not be in that same vlan for any untagged traffic, whatever the ID is your using on the switch.
-
This post is deleted!