Cannot pre-load keyfile
-
@johnpoz That was it! Perfect I have been looking for this answer for a week now. Rock Star!!!
-
@technolust did you get rid of your other errors.. There really no reason not to use ncp, and use of a AES-XXX-GCM cipher via ncp, you can always set for now fallback to CBC
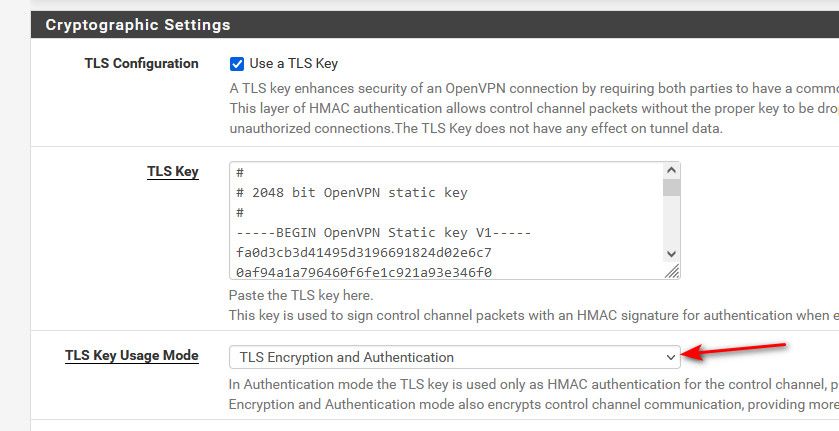
I would also look to changing from tls-auth to tls-crypt, which does both auth and encryption.
-
@johnpoz Yeah, I manually deleted the old records and then created the new one (copy pasta) then imported from the new path. I believe the ncp was depricated in 2.6 I haven't installed it yet.
I'm not sure how to change the tls-auth to tls-crypt. Something I will have to look at over the weekend. Seems a lot less convoluted. Will it matter if I have 1G up and 1G down on the link?
Here is the new config
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote xxx.xxx.xxx.xxx 1194 udp4
nobind
verify-x509-name "pffw-myvpn-cer" name
auth-user-pass
pkcs12 fw-myvpn-UDP4-1194-username.p12
tls-auth fw-myvpn-UDP4-1194-username-tls.key 1
remote-cert-tls server
explicit-exit-notify -
-
@johnpoz Will try when I get back.
-
I made the change but not sure what the difference is/does.
-
@technolust the tls key is encrypted if you use TLS-Crypt.. this has a few benefits, one being somewhat hiding openvpn connections from being detected by a signature. Also can prevent an dos attack against tls auth.
I do not believe pfsense has enabled support for tls crypt v2 as of yet, this is where all clients would use a different tls key, etc.
Is it the end of the world if you were only using auth vs crypt, no - but if your going to go through your settings anyway to fix something, prob a good idea to use the strongest settings your clients and server support. Use of tls-crypt vs just auth would be considered a stronger setup from a security standpoint.
-
@johnpoz Ahh ok, that makes sense now. I couldn't grasp the concept that tls-crypt was encrypting the tls key not the certificate. For some reason I had it in my head and thought... Why would we encrypt an encrypted certificate.... Duh....
You mentioned tls v2 would this require a certificate for each client as well or just keys?
Thanks so much for your education, clarification, and help! I have learned a bunch from your help!
-
@technolust tls-crypt v2, not just tls 2 ;)
This is somewhat new thing from openvpn, but I think there are some speed bumps in trying to implement that in pfsense (how to keep track of all the different users tls keys, etc)
There is a thread around here about it..
ah here it is
https://forum.netgate.com/topic/165231/pfsense-ui-doesn-t-support-inline-keys-tls-crypt-v2 -
@johnpoz That is exactly what I was thinking... How to keep track of all the tls keys... Now to figure out how to utilize some of the addins like nort...
I can't thank you enough for all your help!!