OpenVPN in 2.6.0 problem with "remote-cert-tls" after restart.
-
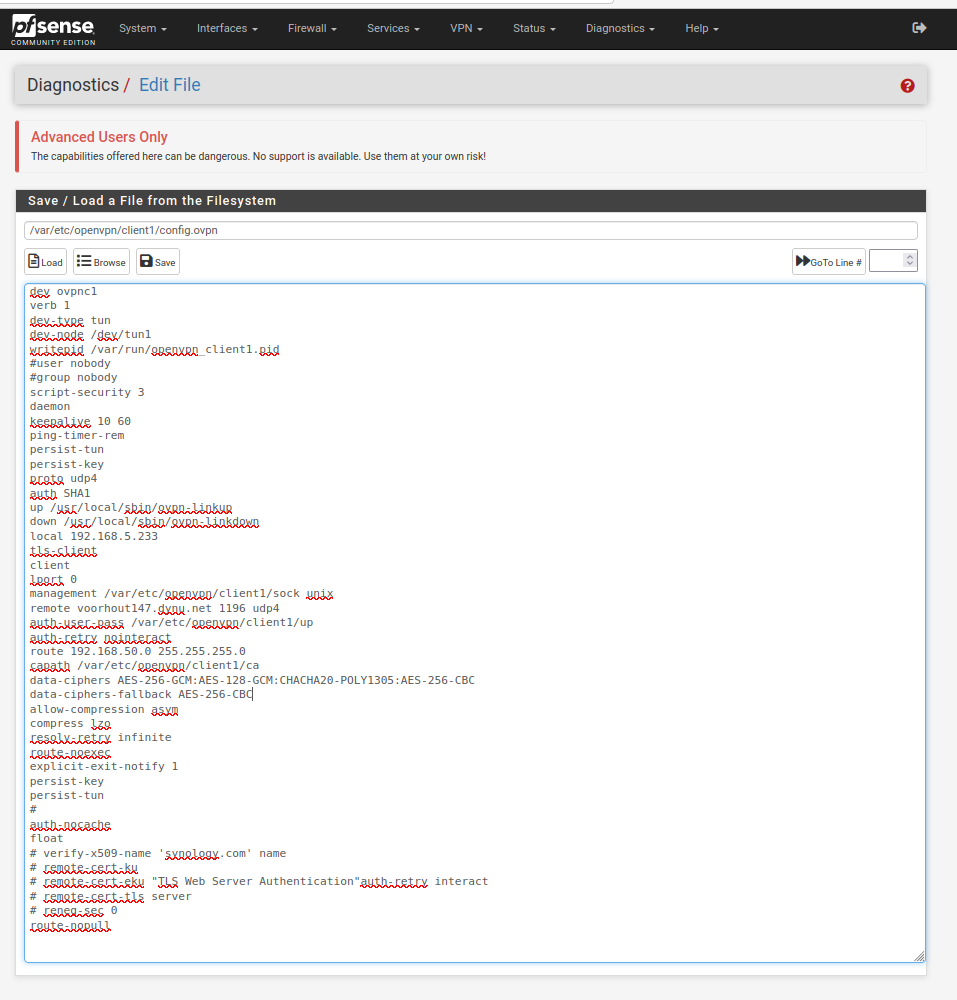
The openvpn client in the new 2.6.0. fails after restart the service. It was no problem in the 2.5.2. The happened when connecting to a Synology OVPN server on a disc station. The error I received was " Certificate does not have key usage extension" The imported CA apparently does not contain the proper user key. But when you don't include "remote-cert-tls server" in your config.ovpn configuration than it works when you safe the profile. However if you restart the service it includes this "remote-cert-tls server" again in the config.ovpn. This cause that the connection doesn't startup again although the service is running.
See attached screendumps of the config.ovpn files after "save" and after "restart or reboot" .

-
Afaik 2.6.0 began to check the certificate type.
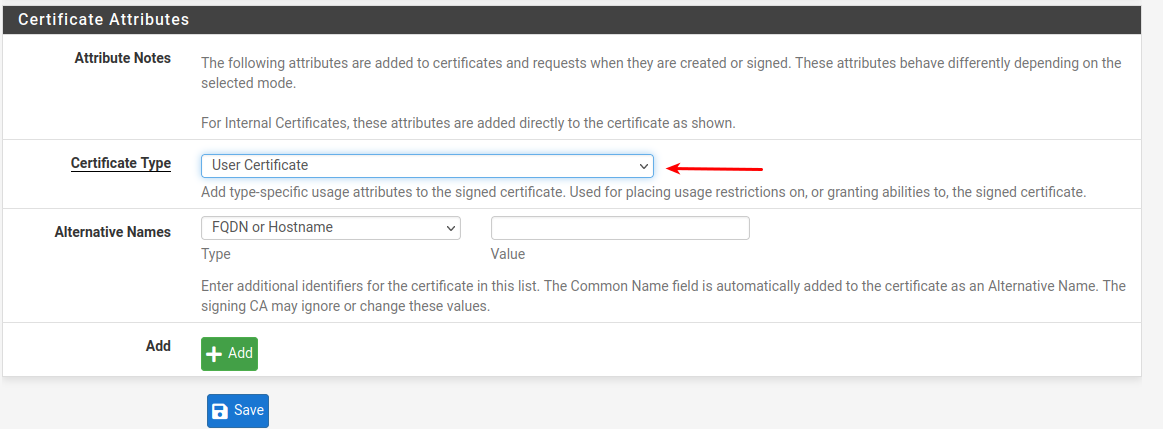
You would (should) generate the OpenVPN Server certificate with Certificate Type Server , and the Client with type "User certificate"
-
Dear Afaik
There are two issues. The connection is a client in pf-sense with a server in dsm7.1 of Synology. So the certificate was imported from Synology and this doesn't support the extended key option. Therefore the directive "remote-cert-tls server" is not supported. This was no isssue in Pfsense 2.5.2 were this "remote-cert-tls server" was used, unless you added it in the extra options. So you ended up with a less secure connection. I waiting for Synology whether they can provide a undated cert.
The bug in Pfsense is that if you safe the vpn settings the service starts up without this "remote-cert-tls server" and the connection starts up oke. However if you restart (or reboot) the openvpn service automaticly includes the "remote-cert-tls server" option and the connection fails and keep starting up if a watchdog is activated.I tested your suggestion by generation of server and user certificates and put the server cert,key,ca in DSM but that endedup as a " TLS Error: cannot locate HMAC in incoming packet from [AF_INET]192.168.5.115:1195".
Regards,
Rini -
@rini
My giess is:
You would have to put a copy of the pfsense Root CA "public part" on the DSM too.
It has to know the full chain.