Renewed CA and Cert; now I can't log in from Safari 14.1.2
-
I migrated from 2.4.4 on an APU to 22.05 on an SG-1100 by exporting and then importing the config (with Netgate's help).
I noticed that my CA and webGUI cert were expired, so I clicked the Reissue/Renew buttons on both and accepted all the defaults.
Now I can no longer log in from Safari 14.1.2/macOS 10.14.6. If I click Show Details and then visit this website:
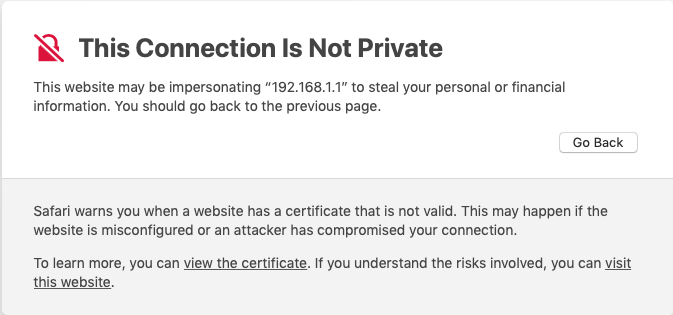
I get a prompt to make changes to my Certificate Trust Settings:
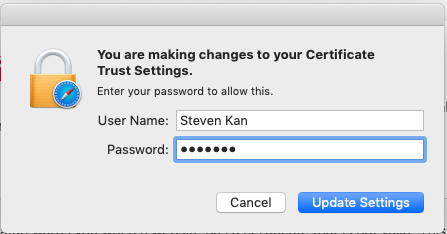
which I accept, but then it puts me in an endless loop of the same error.
I can bypass this warning in Chrome (by typing thisisunsafe) and in Firefox by clicking through several warnings, but I can't get through this on my Mac.
I even exported the webGUI certificate and imported it on my Mac, and it shows as "trusted for 192.168.1.1":
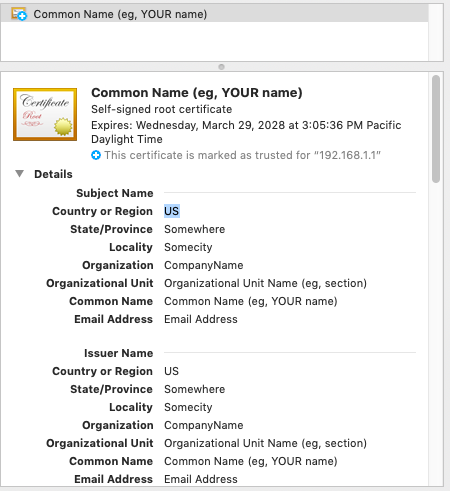
but I still can't log in from Safari.
I can click through the warnings on my iPhone (iOS 16.0.2) and get to the admin page.
Is my Safari too old?
p.s. updating Safari requires updating macOS, which I don't want to do right now because I have some expensive software that will not run on macOS > 14.
-
@thewaterbug Did you export and install the CA?
Most times people install the server cert, you need the CA -
Yes, I downloaded and installed the CA, and I still have the same problem.
-
@thewaterbug said in Renewed CA and Cert; now I can't log in from Safari 14.1.2:
I downloaded and installed the CA
And what CA did you install - the self signed cert that pfsense generates as no CA to download and trust.
Also that common name is not what would be generated by pfsense selfsigned cert, yours just says "common name" ??
Here is example of self signed cert for the webgui that pfsense generates.
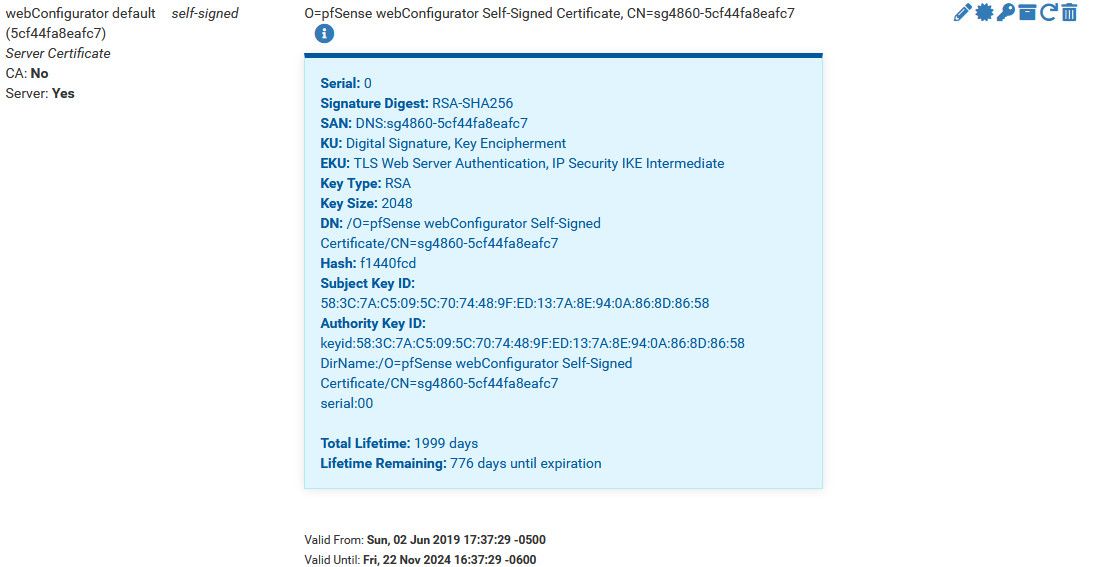
If you want a cert that you can install the CA from so your browser trusts it, then create a CA in the cert manager, then create a cert using that CA, putting in the appropriate CN and SANs that you access your webgui with.. You can even add rfc1918 addresses, etc. Use that cert for your web gui.
Now have your browser trust that CA.. And it will not warn you about the cert on the pfsense web gui.
edit: example here is my CA, and the cert the web gui uses that was issued by that CA.
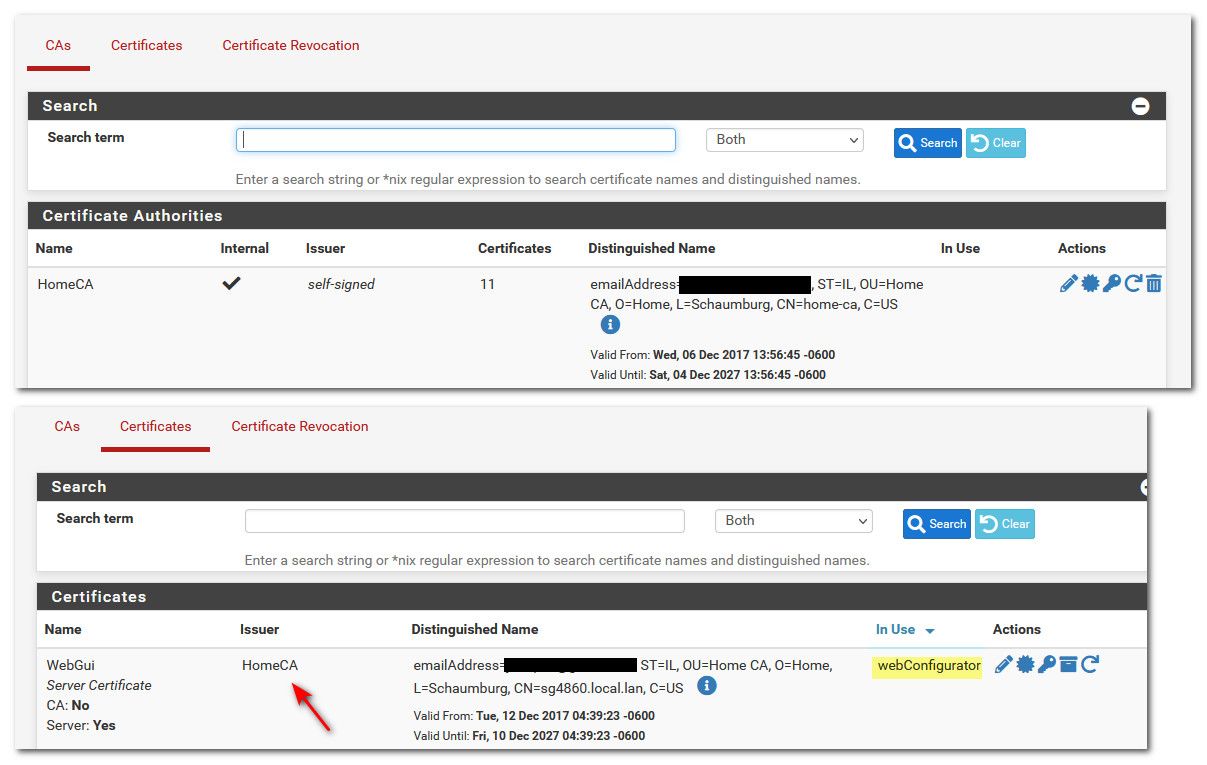
You wont be able to use a 10 year cert, because browsers no longer accept those, unless they were created before they put in those limits of like 398 or something days.
edit2: I don't have a mac to play with for safari - but I do have it on my phones. Phones are a bit different, but you install the ca cert as a profile, then you go to your trust cert settings under general settings, and you can enable to trust that CA.. Then if you load load up safari it will trust the webgui cert signed by the CA you trust

-
Thanks! I had done most of the steps, but didn't know I had to change the cert that the webGUI was using in System: Advanced: Admin Access: SSL/TLS Certificate:
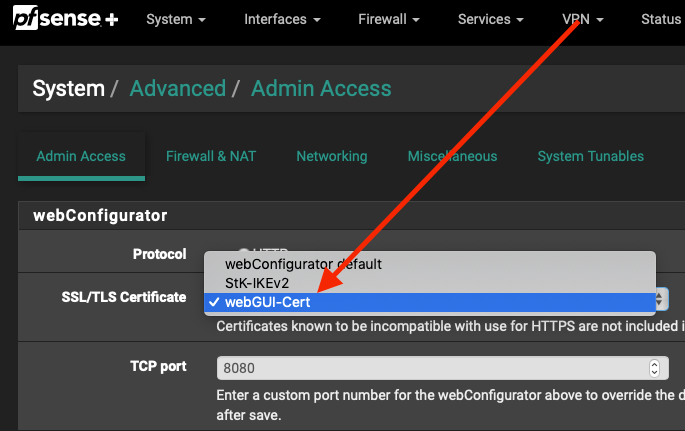
I selected the new cert, and now I can log in from Safari after accepting the warning once.
Thanks again!
-
@thewaterbug said in Renewed CA and Cert; now I can't log in from Safari 14.1.2:
Safari after accepting the warning once.
there shouldn't be a warning at all if you trust the ca, using the correct cert and the fqdn san your using to access it matches
-
This post is deleted! -
@johnpoz said in Renewed CA and Cert; now I can't log in from Safari 14.1.2:
there shouldn't be a warning at all if you trust the ca, using the correct cert and the fqdn san your using to access it matches
I'm afraid I don't grok what the Alternative Names entry/ies mean.
Do I enter the names/attributes of the pfsense box here? Or the attributes of the machines that will be browsing to the pfsense box?
If the latter, what should I enter if it's a mobile device that might be on any network, with any IP address, connecting through the VPN?
On a Mac laptop, the hostname changes all the time, as it gets an incrementing number appended to it randomly, e.g. Steven-Kans-MBP-2093.local.
-
@thewaterbug said in Renewed CA and Cert; now I can't log in from Safari 14.1.2:
I'm afraid I don't grok what the Alternative Names entry/ies mean.
The SAN would be "Alternative names"/IP's the certificate should be valid for.
Since the certificate here "validates" the pfSense, it would be alternate names/ip's for accessing the pfSense.In general (server use) you could make a cert , that would be valid for multiple fqdn names, and ie. install the same cert on several servers.
These are examples of SAN's
Company Web server
www.acme.comCompany Mail server
mail.acme.comCompany FTP server
ftp.acme.comAnd the "full monty" ... Often discouraged by "Public ROOT CA's"
Everyting company related
*.acme.com -
@thewaterbug as mentioned @bingo600 your SAN would the names or IPs you want to access the service using the cert on..
For example here is mine for my webgui cert.
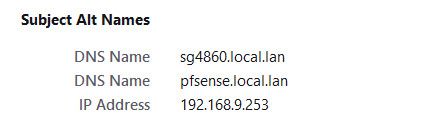
Your CN should be what you commonly use, CN = Common Name, but you really should have at least SAN that matches your CN.. So for example my CN is the sg4860.local.lan, and also you see I have a SAN with the same fqdn.
edit: btw here is one of my older walk thru creating a CA and cert.
https://forum.netgate.com/topic/141033/tls-certificate-can-i-make-a-fake-ca/19?_=1665333214113
-