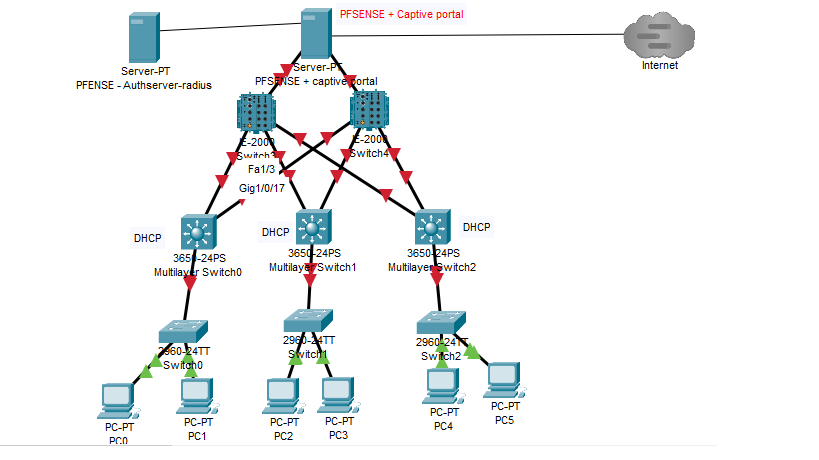
Net topology
-
This post is deleted! -
@emad4
Should be possible if:
-You don't do nat on the switches
-Clients use pfsense for DNSWhy did ya start a seperate topic?
-
@heper
There is no NAT on Cisco switches but the NAT is only enabled on PFsense server -
@emad4
Can someone answer me please -
@emad4 answer what?
You asked if it was possible originally.
I replied.What more of an answer do you want?
-
Thank you but I uploaded a diagram so to know how to do that , how to enable a captive portal for clients based on the diagram I sent.
I enabled captive portal on the server and it does not work. How can I direct other pcs to captive portal while there are Ips between pfsense server and other clients. In other words , how to make each lan reach pfsense server (captive portal) while each lan has a specific range ?
-
@emad4 said in Net topology:
Thank you but I uploaded a diagram so to know how to do that , how to enable a captive portal for clients based on the diagram I sent.
First: The graphic you uploaded appears to have been deleted.
Second:
https://docs.netgate.com/pfsense/en/latest/captiveportal/common-scenarios.html#common-captive-portal-scenarios
and
https://docs.netgate.com/pfsense/en/latest/captiveportal/index.html -
@rcoleman-netgate
Thank you for your replay and the links you sent.
Technically , I know how to enable and configure captive portal on pfsense server and I did that before in a scenario when my pfsesnse server worked as dhcp and it was much easier for me to configure captive portal on it. But I mean now how to make clients recognize the captive portal of pfsense when pfsense server is not working as dhcp , in other words there are some ips (routers) between the clients and pfsense ..I will try to upload a diagram to make the scenario more clear. -
Please find the topology below concerning my question
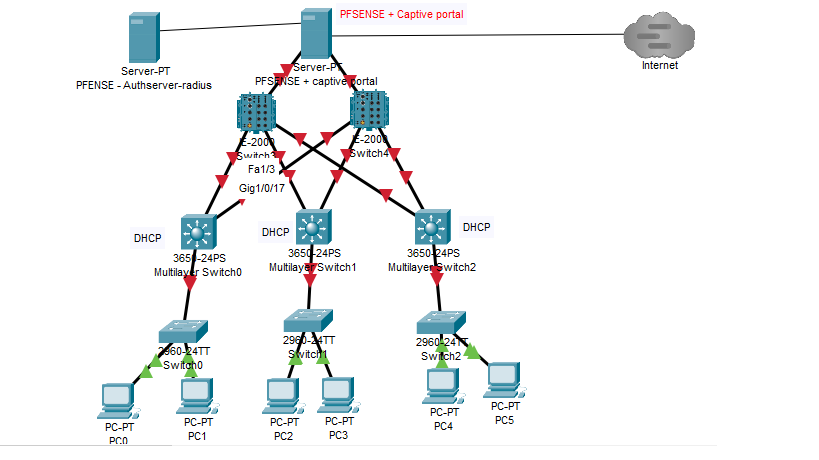
-
@emad4
A router between the captive portal client and pfSense : the portal can't obtain neither the MAC neither the IP of the portal client. -
@gertjan as you know, a "router" is not an issue as long as there is no NAT
@emad4 it doesn't/shouldn't matter what device is handling dhcp.
@heper said in Net topology:
@emad4
Should be possible if:
-You don't do nat on the switches
-Clients use pfsense for DNS -
@heper
There is no NAT on cisco switches but nat is activated on pfsense serverI added the IP of pfsense as a dns for clients but the login page is not appeared and instead a website is opening , for example if I want to open Google.com or MSN.com , there is no login page and those websites open normally even I activated the captive portal on pfsense and Dns is added for clients to direct to pfsense server.
Just I want to mention that when I enabled the captive portal , ping to 8.8.8.8 is lost and when I disabled it , ping continues normally
-
Between
@emad4 said in Net topology:when I enabled the captive portal ,
and
@emad4 said in Net topology:
.... ping to 8.8.8.8
you should identify against the portal.
By default, a captive portal blocks (nearly) everything.
edit : if possible : build things up from "easy and it works" to "complex" :
Between the access points and pfSense : use ordinary switches. Now your portal works.
You'll notice that :
A captive portal users connects to your portal SSID.
It requests a DHCP lease, typically, pfSense will handle this. The pfSense portal network IP should be the gateway and DNS.
Now, the device will emit a hidden http (not https !) request.
If the page returned contains an expected word like "Success", the OS of the device knows there is no portal (Portal support is build in the OS of the devices used, not pfSense), and that a clear direct Internet connection can be presumed.
If something else gets returned, the device (the OS) presumes that their might be a captive portal in place. It launches a user app web browser with the same http request, again.
The http (port 80) request to the test URL gets redirected on pfSense to "127.0.0.1 port 80" (again), this is where the captive portal web server listens : it will send the captive portal's login page. The device's browser shows the login page, the user (a human) can interact with this page. After posting this page back to the server with the user credentials, the device's IP and MAC are added to the pf firewall table with all the other authenticated portal users : the captive portal becomes transparent for the device/user.I advise you to see all this work for your : you'll be needing :
pfSense + a captive portal setup.
An access point - or a switch.
A test device.Afterwards, you can add other hardware.
As soon as things break, you will know what to remove (or reconfigure). -
@gertjan
Yes exactly , I mentioned that to show that captive portal is working but login page is not appeared
What shall I do ? -
@gertjan Thank you for time you spent to answer my question
-
@emad4 said in Net topology:
What shall I do ?
Some more tests :
On the portal client device, lauche a "ipconfig /all"
The IPv4 show is in the correct network ?
DNS IP == Gateway IP == the pfSense portal network IP ?When connected, wired or by Wifi, to the portal network, but before eautification, so before any login page shows up, DNS requests should work ! This is important.
Again : DNS TCP and UDP to port 53, the pfSense portal network should not be blocked.
So,nslookup google.comshould work.
Follow :theses tips : Troubleshooting Captive Portal
For in depth portal info : see here.
The captive portal video's, the classic and advanced, are still valid today.