3.1.0_6 UPDATE
-
@bbcan177 This is the best news in a long time given the slightly shaky rumours that have been circulating.
Thank you for your excellent work - your package is what makes pfSense the best solution around :-)
-
@jdeloach said in 3.1.0_6 UPDATE:
I don't see any issues listed in any of the messages, that
I have ever had.This is also not a must be for everybody I would be glad about to see the same here, but I am also using very old
hardware and perhaps to "small foot print" for this load.
PC Engines APU4D4Granted I don't use Netgate hardware and only run
CE 2.6.0.It is an software problem so it should be nothing to do
with the hardware it selfs, but with much packages installed and much of list feeds, snort rules and av signatures it is perhaps here and there able to point on.Swap space is always 0% and CPU usage is never
spikes above about 3%.Only my AV signatures are taking 1 GB - 1,7 GB of ram and I only own 4 GB hard soldered on the board! So 4 GB swap is not such a great thing if you have to deal with a bunch of rules and lists.
By the way I'm running Snort as well as pfBlockerNG.
Me too, but it comes squid & squidguard plus clamav on top of it and with some lists I haven´t seen such numbers
before like you. And WiFi and FreeRadius are not activated
at this time. I really think it should be in the near future another box more strong or powerful. -
@jdeloach said in 3.1.0_6 UPDATE:
I don't see any issues listed in any of the messages, that I have ever had. Granted I don't use Netgate hardware and only run CE 2.6.0. Swap space is always 0% and CPU usage is never spikes above about 3%.
By the way I'm running Snort as well as pfBlockerNG.
As I understand the issue, it’s related to a change in the logging format pfsense uses in pfSense+ 22.05
That release is as far as I remember a pfsense+ release only - there where no CE 2.6.1 or whatever that could have been called.
I might remember wrong, but CE2.6 came with pfsense+ 22.01 -
@keyser said in 3.1.0_6 UPDATE:
I might remember wrong, but CE2.6 came with pfsense+ 22.01
CE branch (CE tree)
pfSense CE 2.5 > 2.6 > 2.7.....
Plus branch (Plus tree)
pfSense+ (Plus) 22.01 > 22.05 > 22.09 > 22.11....
Developer branch (devel tree)
pfSense x.y devel is even a developer version for testing out
using at home and/or in some rarely cases, only. -
@bbcan177 Yay! Just upped my Patreon contribution.
-
@lohphat said in 3.1.0_6 UPDATE:
@bbcan177 Yay! Just upped my Patreon contribution.
For those that need to donate to the cause (myself included):
-
I upgraded from _4 to _6, had to manually restart unbound (as usual), and had to reapply the pre-existing patch in /net/usr/local/pkg/pfblockerng/pfblockerng.inc
... - $r = explode(')', $result, 2); + $r = explode(' ', $result, 2); ...Watching the git commits, there was activity in the pfblockerng.inc file but not the above change.
Is there a Redmine bug tracking that?
-
@lohphat said in 3.1.0_6 UPDATE:
Is there a Redmine bug tracking that?
yes
@steveits said in 3.1.0_6 UPDATE:
https://redmine.pfsense.org/issues/13154
The code changes didn't find their way into _5 or _6.
-
FYI, 3.1.0_7 is out now with the included fix... Just installed it on my 6100 and everything is working fine.
-
@cloudified Same here. As usual, had to manually restart unbound
-
@lohphat said in 3.1.0_6 UPDATE:
@cloudified Same here. As usual, had to manually restart unbound
Same here. This is only my 2nd time upgrading pfBlocker and I guess that's expected behavior.
-
@bbcan177 Is 3.1.0_7 out for +22.05?
-
@jmv43-0 It is, which is why I just posted that. I noticed it as an available upgrade in Package Manager on my 6100 running 22.05+. Plus he already said it would be coming out this week.
-
pfBlocker-NG 3.1.0_7 and acme 0.7.3 as today they are available for 22.05 I updated in time and all is fine since
the update. Look at the numbers now;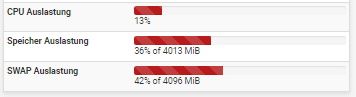
-
@cloudified said in 3.1.0_6 UPDATE:
I guess that's expected behavior
More or less...I seem to recall a post from BBCan177 a while back, saying it was a bug in pfSense's package system, so he can't fix it.
-
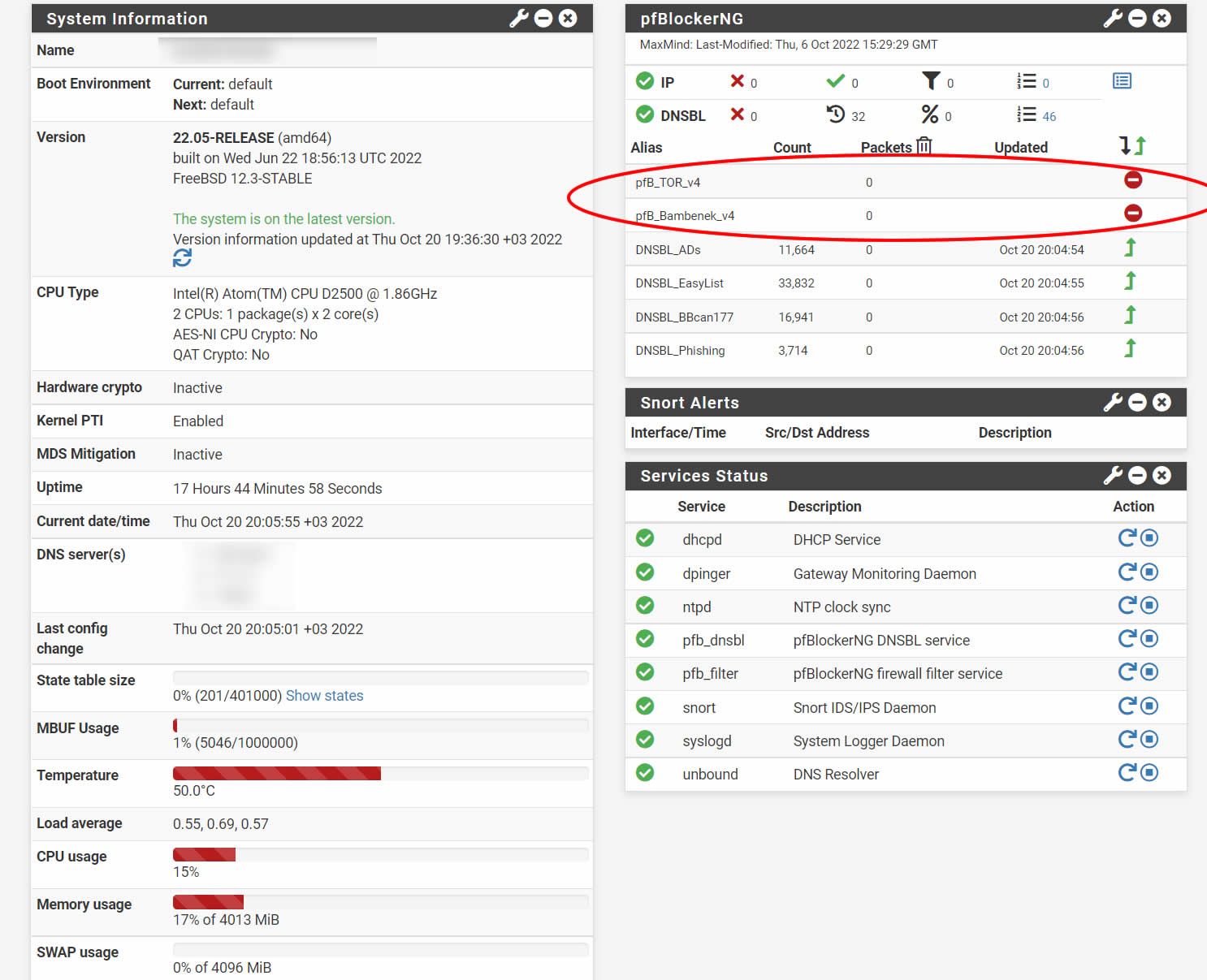
3.1.0_7. everything is fine, but Old rules are not deleted on widget
-
@turker said in 3.1.0_6 UPDATE:
3.1.0_7. everything is fine, but Old rules are not deleted on widget

@turker Do a force reload and restart the pfBlocker services.
-
@cloudified
i do Force reload pfBlocker services and restarted, pfsense restarted. Nothing changed. -
@turker are you getting any table memory errors? That might indicate that you need to increase your Firewall Maximum Table Entries in the System / Advanced / Firewall & NAT section. I had to increase mine from 400,000 to 1,000,000 to account for all of the pfBlocker lists I have configured.
-
@cloudified
@turkerDid you manually create firewall rules for those aliases or did it create them automatically? Check your firewall rules and see if those aliases still appear in your firewall rules, if they do, delete those firewall rules.
I've seen cases where I created rules with aliases in pfBlocker but didn't delete them and they would still show up in that table, like you are showing.