HAProxy Nextcloud WebDAV URL Discovery
-
I am wanting to configure HAProxy on pfsense to reverse proxy / SSL offload my Nextcloud website. I have configured a http_to_https and Nextcloud frontend and a Nextcloud backend. I have also configured the ACME package to provide Let's Encrypt certificates to HAProxy.
This is all working fine and I am happy with the configuration so far. Nextcloud is complaining about the WebDAV discovery URLs :
- "/.well-known/webfinger"
- "/.well-known/nodeinfo"
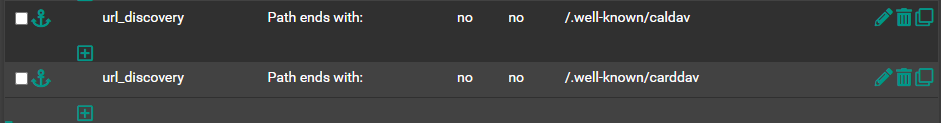
- "/.well-known/caldav"
- "/.well-known/carddav"
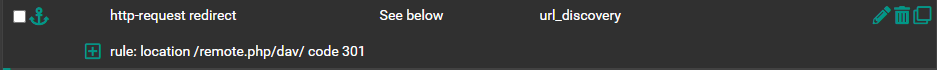
so I have configured what I think I should in the HAProxy backend to resolve the paths to "http-request redirect location /remote.php/dav/ code 301" as per the Nextcloud documentation.
But this does not remove the warning from Nextcloud. Can anyone who has this setup please comment on what I might be doing wrong?
# Automaticaly generated, dont edit manually. global maxconn 500 log 192.168.1.1 local3 debug stats socket /tmp/haproxy.socket level admin expose-fd listeners uid 80 gid 80 nbproc 1 nbthread 1 hard-stop-after 15m chroot /tmp/haproxy_chroot daemon tune.ssl.default-dh-param 2048 server-state-file /tmp/haproxy_server_state listen HAProxyLocalStats bind 127.0.0.1:2200 name localstats mode http stats enable stats admin if TRUE stats show-legends stats uri /haproxy/haproxy_stats.php?haproxystats=1 timeout client 5000 timeout connect 5000 timeout server 5000 frontend HTTP-to-HTTPS bind 192.168.1.1:80 name 192.168.1.1:80 mode http log global option http-keep-alive timeout client 30000 http-request redirect scheme https frontend Public-Web bind 192.168.1.1:443 name 192.168.1.1:443 ssl crt-list /var/etc/haproxy/Public-Web.crt_list mode http log global option http-keep-alive option forwardfor acl https ssl_fc http-request set-header X-Forwarded-Proto http if !https http-request set-header X-Forwarded-Proto https if https timeout client 30000 acl Cloud var(txn.txnhost) -m str -i website.com acl Cloud var(txn.txnpath) -m str -i /nextcloud acl aclcrt_Public-Web var(txn.txnhost) -m reg -i ^website\.com(:([0-9]){1,5})?$ http-request set-var(txn.txnhost) hdr(host) http-request set-var(txn.txnpath) path use_backend Nextcloud_ipvANY if Cloud aclcrt_Public-Web use_backend Nextcloud_ipvANY if aclcrt_Public-Web backend Nextcloud_ipvANY mode http id 100 log global http-response set-header Strict-Transport-Security max-age=15552000; timeout connect 30000 timeout server 30000 retries 3 acl Cloud var(txn.txnpath) -m sub -i /nextcloud acl Cloud_dav var(txn.txnpath) -m sub -i /.well-known/carddav /.well-known/caldav /.well-known/nodeinfo /.well-known/webfinger acl Cloud_caldav var(txn.txnpath) -m sub -i /.well-known/caldav http-request set-var(txn.txnpath) path http-request allow if Cloud http-request redirect location /remote.php/dav/ code 301 if Cloud_dav http-request redirect location /remote.php/dav/ code 301 if Cloud_caldav server cloud 192.168.1.2:80 id 101 -
So nobody from pfSense or the community knows or wants to share. Doesn't Netgate run Nextcloud... assuming its behind pfsense and HAProxy.
-
@bradi
I'm not running Nextcloud behind HAproxy though, however as far as I know HAproxy, the http-request redirects must be set in the frontend, not in the backend. -
Thanks for the reply viragomann, I have removed the ACLs from the backend and added to the frontend. No change in error from Nextcloud. I have tried having them configured in both the frontend and backend and received an error "Your web server is not yet properly set up to allow file synchronisation, because the WebDAV interface seems to be broken."
As this seems a trivial use of HAProxy I am surprised it seems so hard to resolve (searching for this problem does not seem to provide a solution other than "thanks that fixed it"), I suspect this may also have something to do with using HA Proxy on pfSense as using nginx Proxy Manager I have no problems.
I would prefer not to have to spin up another container just to be a reverse proxy as this is baked into pfSense and it appears to me that it should work with the correct ACLs.... I just don't understand why it is not. Hence this post of the pfSense forum.
If anyone has this working (nudge nudge Netgate) a helping hand would be appreciated for this plus user.
-
I stumbled on this old thread looking for similar information, so I'll provide my simple solution for future searchers.
I have similar setup to OP and configured my frontends in the PFSense GUI by referencing the code in the Nextcloud Docs.
Frontend ACL:
Frontend Actions:
-
@milehigh I have tried but it ends up with that the second part is not able to be saved due to that I have a http redirect already http to https. Any suggestions what to do?
-
@swemattias said in HAProxy Nextcloud WebDAV URL Discovery:
the second part is not able to be saved due to that I have a http redirect already http to https.
Possibly you did that wrong? Did you limit the respective ACL to non-HTTPS Traffic?