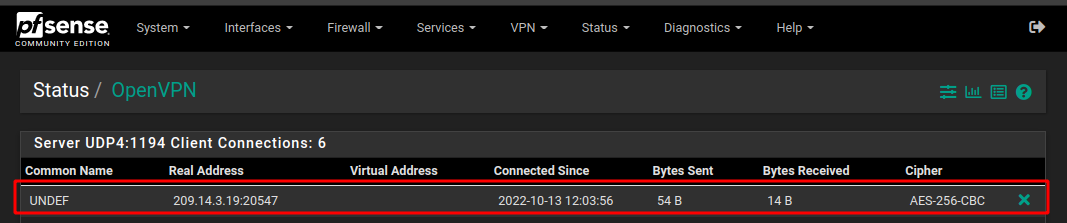
OpenVPN - Common name UNDEF
-
Please!
I'm in trouble, looks like someone wants to hack my OpenVPN. IPs from different countries. In Status/OpenVPN they are displayed as UNDEF. I've tried blocking through firewall rules, but when refreshing the page, they return.
-
Looks more like a config error.
My OpenVPN server setting description :
Under Status :
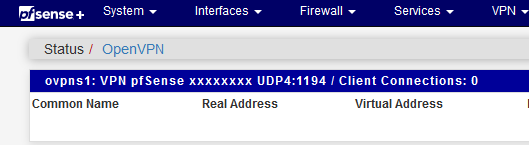
Note the internal OpenVPN server instance ID : ovpns1 - and this one is missing. Are you using CE 2.6.0 ?
and the description "VPN pfSense xxxxxxxx", yours is probably just "Server".You're seeing a UNDEF client connection : this might be 'something' playing with your WAN 1194 UDP port. That's ok, as he would not have the access credentials.
-
@gertjan
The configuration is correct. Access is performed through certificates (SSL/TLS) but my concern is the attempt to access through port 1194. I tried to block it with firewall rules, but they keep trying to enter.
Version 2.5.2 -
@luisthiago said in OpenVPN - Common name UNDEF:
I tried to block it with firewall rules,
By default, there are no WAN firewall rules .... so everything is blocked.
As soon as you use on WAN a rule like this :
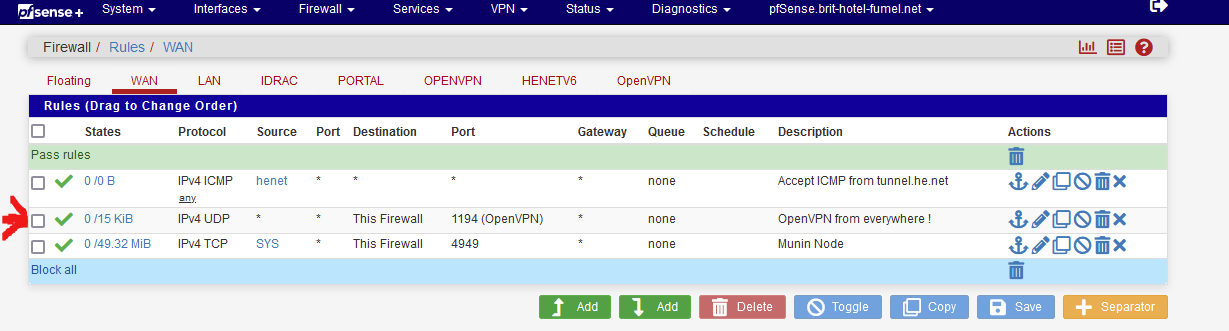
then the entire world can knock on your "WAN IP UDP port".
That doesn't mean they have the 'key' ;)You can, of course, change this firewall rule a bit, so it accept only YOUR IP (when you're remote), and no other IP ;)
@luisthiago said in OpenVPN - Common name UNDEF:
Version 2.5.2
That's what I would call a security issue.
That ancient pfSense used an ancient OpenVPN from back then (check the openvpn log to know the your OpenVPN server version).
You really should think twice : should you maintain old software and decide to use OpenVPN ?
My advice : please, don't. -
@gertjan Thank you my friend! I will upgrading the version of the pfSense.
-
Did you check the logs to make sure those weren't valid users?
I've seen clients connect as UNDEF before under certain configurations. If they are valid users, you can add
username-as-common-name
to the custom options on the server to get the correct names to display. -
@dotdash thank you for your reply. Weren't valid users, are IPs of the several countries of the world. I'm thinking to install pfBlockerNG. I will upgrading the version of the pfSense too, in the moment is 2.5.2.
-
@luisthiago Those are probably researchers knocking on your door. pfBlockerNG contains filters for well-known port scanners. Legitimate researchers will knock on your door more often than the Chinese will try to get in through telnet, and that happens dozens of times each day.
-
FYI- There are a couple different ways that they can show up UNDEF:
- If something probes the server port without actually speaking the OpenVPN protocol or otherwise doesn't complete authentication
- If you use User Auth only (no SSL/TLS) and do not have "Username as common name" enabled
The latter is normal/expected and OK. You probably want to enable that option in that case anyhow, it really only has benefit when using SSL/TLS+User Auth and each auth user can have multiple different certificates.
The former is a bit trickier since you kind of have to have OpenVPN open to the world to accept remote access VPN connections, but the good news is as long as you have a TLS key on the tunnel (Either TLS auth or TLS encryption+auth) it's a non-issue. It won't matter if anything probes the VPN port because without the TLS key the packets will be rejected without even performing a full TLS exchange.
Everyone should have a TLS key on their OpenVPN servers anyhow not only for the authentication protection, but also because it is an extra authentication factor ("something you have", similar to a cert) and it has also been proven effective at protecting the server against OpenSSL exploits like Heartbleed in the past.