Dynamic IP and update Certificate
-
I have a dynamic IP from my ISP which I have named in Dynamic DNS.
I use DynDNS (account.dyn.com).
Everytime I get a new IP from my ISP I have discovered I can't connect to pfSense/OpenVPN server with OpenVPN client without downloading certificate and install it in the OpenVPN client ... over and over.
This is very annoying ...
How can that be avoided since I have defined a hostname for my WAN IP in Dynamic DNS. -
@zkab Your using acme cert for your openvpn?
-
@johnpoz No ... I have my own CA.
What I tested was to replace the IP with an Dynamic DNS FQDN on the remote line in the certificate ... and it seems to work.
Can that be done inpfSEnse instead? -
@zkab that is normally how you would do it. You would create a CA in pfsense, and create a cert with this CA for use in openvpn.
The CN on this cert doesn't have to be anything valid or even a fqdn.. Client would validate that the CN is correct, for example on the cert I use the CN = pfsenseopenvpn
How you access the server from your client via IP or some FQDN you point to the IP via some dynamic dns wouldn't come into play here.
When I export the ovpn file for a client, it has this in it
verify-x509-name "pfsenseopenvpn" name
-
@johnpoz CN ???
When ISP changed IP and I could not connect ... checking the certificate I saw that the old IP was still in the certificate:remote xx.xx.xx.xx 1194 udp4 nobind verify-x509-name "my-dyndns-name" namewhere xx.xx.xx.xx = old IP
It seems the verify-x509-name "my-dyndns-name" name had no effect.
Now I haveremote my-dyndns-name nobind verify-x509-name "my-dyndns-name" nameand it seems to work OK.
But I had to edit certificate for all vpn client ... so my question is if this could be done in one place in pfSense? -
@zkab no once the client has the the client config, there is no way to update that without sending new config to client, or having them update it.
-
@zkab said in Dynamic IP and update Certificate:
I saw that the old IP was still ...
... hard coded into the OpenVPN client config.
Instead of using
remote xx.xx.xx.xx 1194 udp4you should create an OpenVPN client config with
remote my-dyndns-name 1194 udp4and now, when your WAN IP changes, the dyndns magic will change your "my-dyndns-name" so it points to your new WAN IP.
That's what dyndns is all about.edit :
Pick your (dyndns) host name from here :
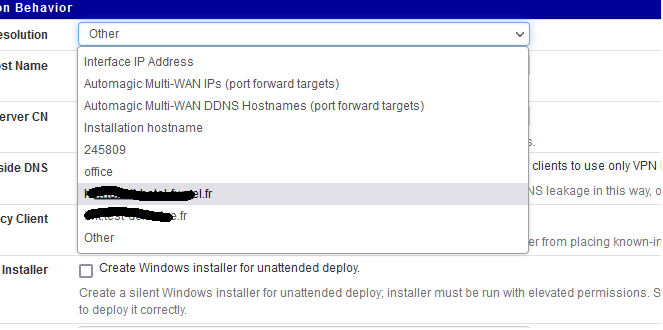
when exporting the openvpn client config.
-
@gertjan I think that is what he did, but the problem is the client has the old setting. He was asking if there is a way to just change that in pfsense and have all the clients configs update automagically.
Which there is no way.. Its like if I told you the password was 123, and then I changed it to 456. Unless I tell you to use this new 456 password, your not going to get in.
-
@johnpoz said in Dynamic IP and update Certificate:
update automagically.
'clients' that can't login any more over VPN are more often then not magically motivated to (example) look in their mails **, and find the new openvpn config to be put in place, so they regain access. Right ?
True, the pfSense admin that changes the openvpn config has to contact very openvpn client user. We all love OpenVPN for that, especially if there are many users.** I know, openvpn config over mail is bad ...
-
@gertjan Thank you guys for your support