Unabl to renew cert / Unable to add the DNS record (NameSilo)
-
Hi.
I have tried to renew my domain today and yesterday, but it is not working (has worked before).
Sat, 30 Jul 2022 03:36:06 +0200 Issued Certificate Dates: Valid From: Sat, 30 Jul 2022 02:36:05 +0200 Valid Until: Fri, 28 Oct 2022 02:36:04 +0200Tried update the package pfSense-pkg-acme from 0.6.10_1 to 0.7.3 but the issue is the same.
Getting this:
LE_Root_Cert Renewing certificate account: LE_Cert server: letsencrypt-production-2 /usr/local/pkg/acme/acme.sh --issue --domain '*.flemmingss.top' --dns 'dns_namesilo' --home '/tmp/acme/LE_Root_Cert/' --accountconf '/tmp/acme/LE_Root_Cert/accountconf.conf' --force --reloadCmd '/tmp/acme/LE_Root_Cert/reloadcmd.sh' --log-level 3 --log '/tmp/acme/LE_Root_Cert/acme_issuecert.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [Namesilo_Key] => 74XXXXXXXXXXXXXXXXXX30 ) [Thu Oct 20 14:28:25 CEST 2022] Using CA: https://acme-v02.api.letsencrypt.org/directory [Thu Oct 20 14:28:25 CEST 2022] Single domain='*.flemmingss.top' [Thu Oct 20 14:28:25 CEST 2022] Getting domain auth token for each domain [Thu Oct 20 14:28:27 CEST 2022] Getting webroot for domain='*.flemmingss.top' [Thu Oct 20 14:28:27 CEST 2022] Adding txt value: xuhXXXXXXXXXXXXXRb--Up7OAiitBLSCFhdyrBc8i-I for domain: _acme-challenge.flemmingss.top [Thu Oct 20 14:28:29 CEST 2022] Unable to add the DNS record. [Thu Oct 20 14:28:29 CEST 2022] Error add txt for domain:_acme-challenge.flemmingss.top [Thu Oct 20 14:28:29 CEST 2022] Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.log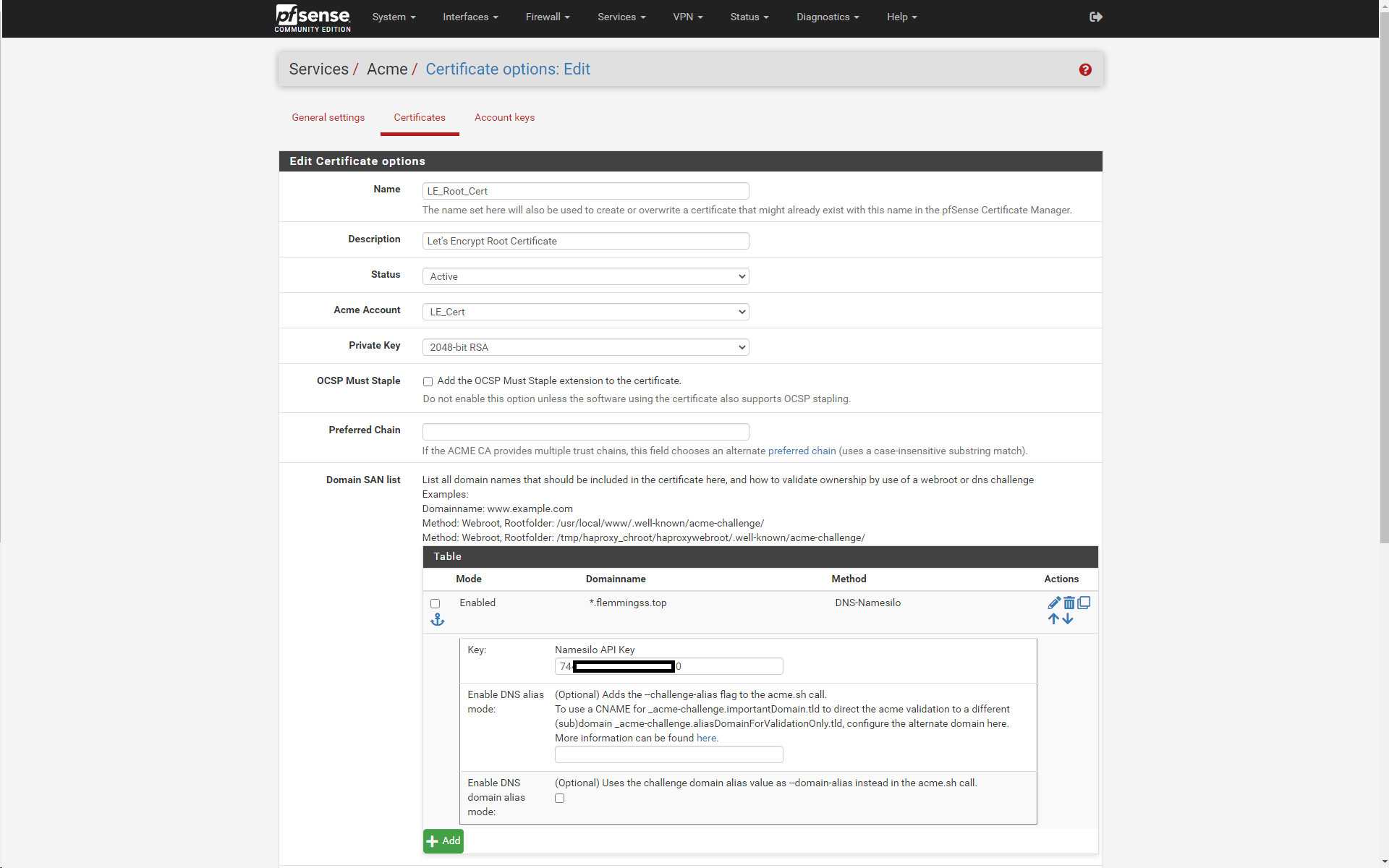
anyone can point to whats wrong here?
-
@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
anyone can point to whats wrong here?
What, no.
But where you can find more info about what went wrong :@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.log
The domain name you've shown above is an example, right ?
edit :
If you want a wild card cert, you have to 2 SAN, not one :
test-domain.tld
and
*.test-domain.tld@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
but it is not working (has worked before)
Remember : small and big systems, know or less known, they can have issues ones in a while.
I'm using a "Certificate renewal after" like 40 days or so. Gives me plenty of time if there are upstream issues.
-
Thank you, does this help? The log, idk if it is the right part.
https://pastebin.com/ydrhemvg -
@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
https://pastebin.com/ydrhemvg
[Thu Oct 20 15:13:45 CEST 2022] Adding txt value: 7Dfbx**********************Gs5Mk for domain: _acme-challenge.flemmingss.top
....
[Thu Oct 20 15:13:46 CEST 2022] ret='0'
....
[Thu Oct 20 15:13:48 CEST 2022] Successfully added TXT record, ready for validation.
[Thu Oct 20 15:13:48 CEST 2022] The txt record is added: Success.So that looks fine.
The detailed log doesn't show the same things as your initial :
"Unable to add the DNS record."[Thu Oct 20 15:14:08 CEST 2022] You can use '--dnssleep' to disable public dns checks
What have you set as a "dns sleep" ?
Make that 120 or so.
You have 'none' or 0 ???Cloudflare is used to check the TXT record for "_acme-challenge.flemmingss.top" ..... but Cloudflare has a hard time finding the zone info.
Btw : Are you sure about he domain name ??
It's a 'mess' : https://www.zonemaster.net/result/417e30f2d6147744 -
@gertjan
I am sure about the domain. I use it for self-hosted services at home.https://<services>.flemmingss.topDNS sleep option was empty, tried to set it to 120 now
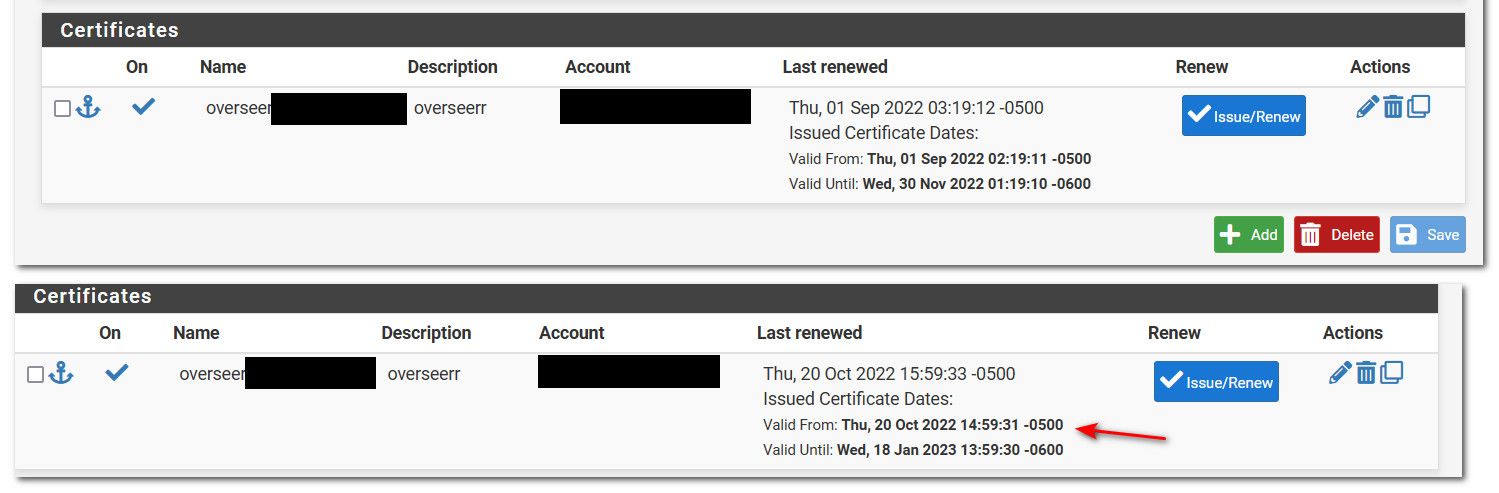
Now I got this respons:LE_Root_Cert Renewing certificate account: LE_Cert server: letsencrypt-production-2 /usr/local/pkg/acme/acme.sh --issue --domain '*.flemmingss.top' --dns 'dns_namesilo' --home '/tmp/acme/LE_Root_Cert/' --accountconf '/tmp/acme/LE_Root_Cert/accountconf.conf' --force --reloadCmd '/tmp/acme/LE_Root_Cert/reloadcmd.sh' --dnssleep '120' --log-level 3 --log '/tmp/acme/LE_Root_Cert/acme_issuecert.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [Namesilo_Key] => 74436e5aea2722010efa30 ) [Thu Oct 20 17:33:34 CEST 2022] Using CA: https://acme-v02.api.letsencrypt.org/directory [Thu Oct 20 17:33:34 CEST 2022] Single domain='*.flemmingss.top' [Thu Oct 20 17:33:34 CEST 2022] Getting domain auth token for each domain [Thu Oct 20 17:33:36 CEST 2022] Getting webroot for domain='*.flemmingss.top' [Thu Oct 20 17:33:36 CEST 2022] Adding txt value: 7Df*********************************5Mk for domain: _acme-challenge.flemmingss.top [Thu Oct 20 17:33:38 CEST 2022] Successfully added TXT record, ready for validation. [Thu Oct 20 17:33:38 CEST 2022] The txt record is added: Success. [Thu Oct 20 17:33:38 CEST 2022] Sleep 120 seconds for the txt records to take effect [Thu Oct 20 17:35:38 CEST 2022] Verifying: *.flemmingss.top [Thu Oct 20 17:35:39 CEST 2022] Pending, The CA is processing your order, please just wait. (1/30) [Thu Oct 20 17:35:41 CEST 2022] Removing DNS records. [Thu Oct 20 17:35:41 CEST 2022] Removing txt: 7Df*********************************5Mk for domain: _acme-challenge.flemmingss.top [Thu Oct 20 17:35:44 CEST 2022] Successfully retrieved the record id for ACME challenge. [Thu Oct 20 17:35:45 CEST 2022] Successfully removed the TXT record. [Thu Oct 20 17:35:45 CEST 2022] Removed: Success [Thu Oct 20 17:35:41 CEST 2022] *.flemmingss.top:Verify error:No TXT record found at _acme-challenge.flemmingss.top [Thu Oct 20 17:35:45 CEST 2022] Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.logStill say "Valid Until: Fri, 28 Oct 2022 02:36:04 +0200", maybe I have to wait a little?
-
Okay, 1-2 h has past and still the same.
New test and new log:
/tmp/acme/LE_Root_Cert/acme_issuecert.log -> https://pastebin.com/nJSPpPS8×LE_Root_Cert Renewing certificate account: LE_Cert server: letsencrypt-production-2 /usr/local/pkg/acme/acme.sh --issue --domain '*.flemmingss.top' --dns 'dns_namesilo' --home '/tmp/acme/LE_Root_Cert/' --accountconf '/tmp/acme/LE_Root_Cert/accountconf.conf' --force --reloadCmd '/tmp/acme/LE_Root_Cert/reloadcmd.sh' --dnssleep '120' --log-level 3 --log '/tmp/acme/LE_Root_Cert/acme_issuecert.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [Namesilo_Key] => 74436e5aea2722010efa30 ) [Thu Oct 20 19:29:41 CEST 2022] Using CA: https://acme-v02.api.letsencrypt.org/directory [Thu Oct 20 19:29:41 CEST 2022] Single domain='*.flemmingss.top' [Thu Oct 20 19:29:41 CEST 2022] Getting domain auth token for each domain [Thu Oct 20 19:29:43 CEST 2022] Getting webroot for domain='*.flemmingss.top' [Thu Oct 20 19:29:43 CEST 2022] Adding txt value: oJ3***********6A4 for domain: _acme-challenge.flemmingss.top [Thu Oct 20 19:29:45 CEST 2022] Successfully added TXT record, ready for validation. [Thu Oct 20 19:29:45 CEST 2022] The txt record is added: Success. [Thu Oct 20 19:29:45 CEST 2022] Sleep 120 seconds for the txt records to take effect [Thu Oct 20 19:31:45 CEST 2022] Verifying: *.flemmingss.top [Thu Oct 20 19:31:46 CEST 2022] Pending, The CA is processing your order, please just wait. (1/30) [Thu Oct 20 19:31:48 CEST 2022] Removing DNS records. [Thu Oct 20 19:31:48 CEST 2022] Removing txt: oJ3Es*********V6A4 for domain: _acme-challenge.flemmingss.top [Thu Oct 20 19:31:50 CEST 2022] Successfully retrieved the record id for ACME challenge. [Thu Oct 20 19:31:51 CEST 2022] Successfully removed the TXT record. [Thu Oct 20 19:31:51 CEST 2022] Removed: Success [Thu Oct 20 19:31:48 CEST 2022] *.flemmingss.top:Verify error:No TXT record found at _acme-challenge.flemmingss.top [Thu Oct 20 19:31:51 CEST 2022] Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.log -
@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
[Thu Oct 20 19:29:45 CEST 2022] Sleep 120 seconds for the txt records to take effect
I ran into a sleep thing while back with cloudflare. I changed my sleep value to 180, and that seemed to clear up the issues I was having.
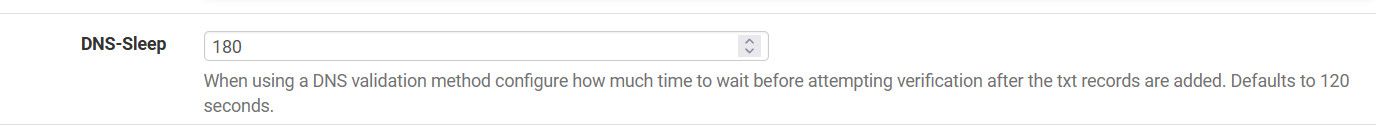
edit: I just updated to the latest acme 0.7.3 and updated my cert, didn't have any issues - use dns-cloudflare.
-
Thanks, but not here :[]
Testet with 1000 and 500 yesterday, 180 today.

-
Your request can't really work out.
Last two examples had no issue to add the two names for your certificate request.
Be aware, you are asking a cert for xxx.flemmingss.top, wjhatever.flemmingss.top, www.flemmingss.top etc, but not "flemmingss.top", as I've already said above. This might be intentional.
Anyway : about the second try you posted above :[Thu Oct 20 19:29:45 CEST 2022] The txt record is added: Success.So the master domain name server has accepted the adding of a text TXT record for this host name : _acme-challenge.flemmingss.top. Good.
Normally, to proof for yourself that you've understood that it works, you should take a break, and test. This is called fact-checking ^^
Like, on the pfSense console :
dig _acme-challenge.flemmingss.top TXTYou have the time to do so, because this one is counting down for 120 seconds :
[Thu Oct 20 19:29:45 CEST 2022] Sleep 120 seconds for the txt records to take effectNow comes the issue : look at the time stamps :
Your request isn't pausing 120 seconds, it goes on right away.
Or, a wait, for 120 seconds or so, is mandatory as domain name servers (at least 2, probably more) need to sync with the master domain name server.
This takes time.What happens next : the text record is removed, and this succeeds.
Then there is a fail :
[Thu Oct 20 17:35:41 CEST 2022] *.flemmingss.top:Verify error:No TXT record found at _acme-challenge.flemmingss.top [Thu Oct 20 17:35:45 CEST 2022] Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.logThis is strange : it was testing after the TXT record was removed ???
The first log shows the good sequence : There is a 120 sec wait here :
[Thu Oct 20 17:33:38 CEST 2022] Sleep 120 seconds for the txt records to take effect [Thu Oct 20 17:35:38 CEST 2022] Verifying: *.flemmingss.topBut :
[Thu Oct 20 17:35:38 CEST 2022] Verifying: *.flemmingss.top [Thu Oct 20 17:35:39 CEST 2022] Pending, The CA is processing your order, please just wait. (1/30)Then, :
[Thu Oct 20 19:31:50 CEST 2022] Successfully retrieved the record id for ACME challenge. [Thu Oct 20 19:31:51 CEST 2022] Successfully removed the TXT record. [Thu Oct 20 19:31:51 CEST 2022] Removed: Success [Thu Oct 20 19:31:48 CEST 2022] *.flemmingss.top:Verify error:No TXT record found at _acme-challenge.flemmingss.toSo, first the TXT record gets deleted.
Then, some generic error :*.flemmingss.top:Verify error:No TXT record found at _acme-challenge.flemmingss.topand as usual, we are looking at the generic non conclusive GUI logs (without the needed details).
So, back to[Thu Oct 20 19:31:51 CEST 2022] Please check log file for more details: /tmp/acme/LE_Root_Cert/acme_issuecert.logfor the real answers.
I guess the real error now is :
You had to many attempts ( max 5 per day or so !!) so any further attempts just fail. -
I tried again today with DNS-Manual. The 2 minutes wait according to documentation resulted in no TXT found.
Last try worked (i think), i did a "issue", added the TXT manually at namesilo, waited 30 minutes and did a renew. Now it is showing like this:
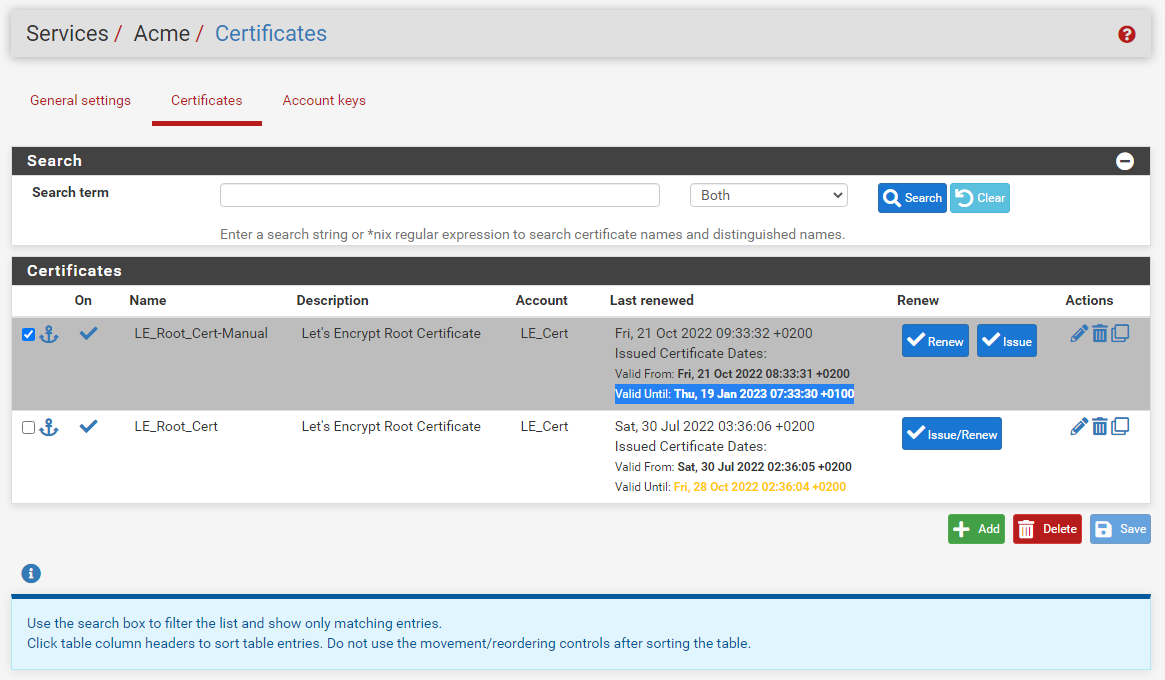
Browser still show the old date:
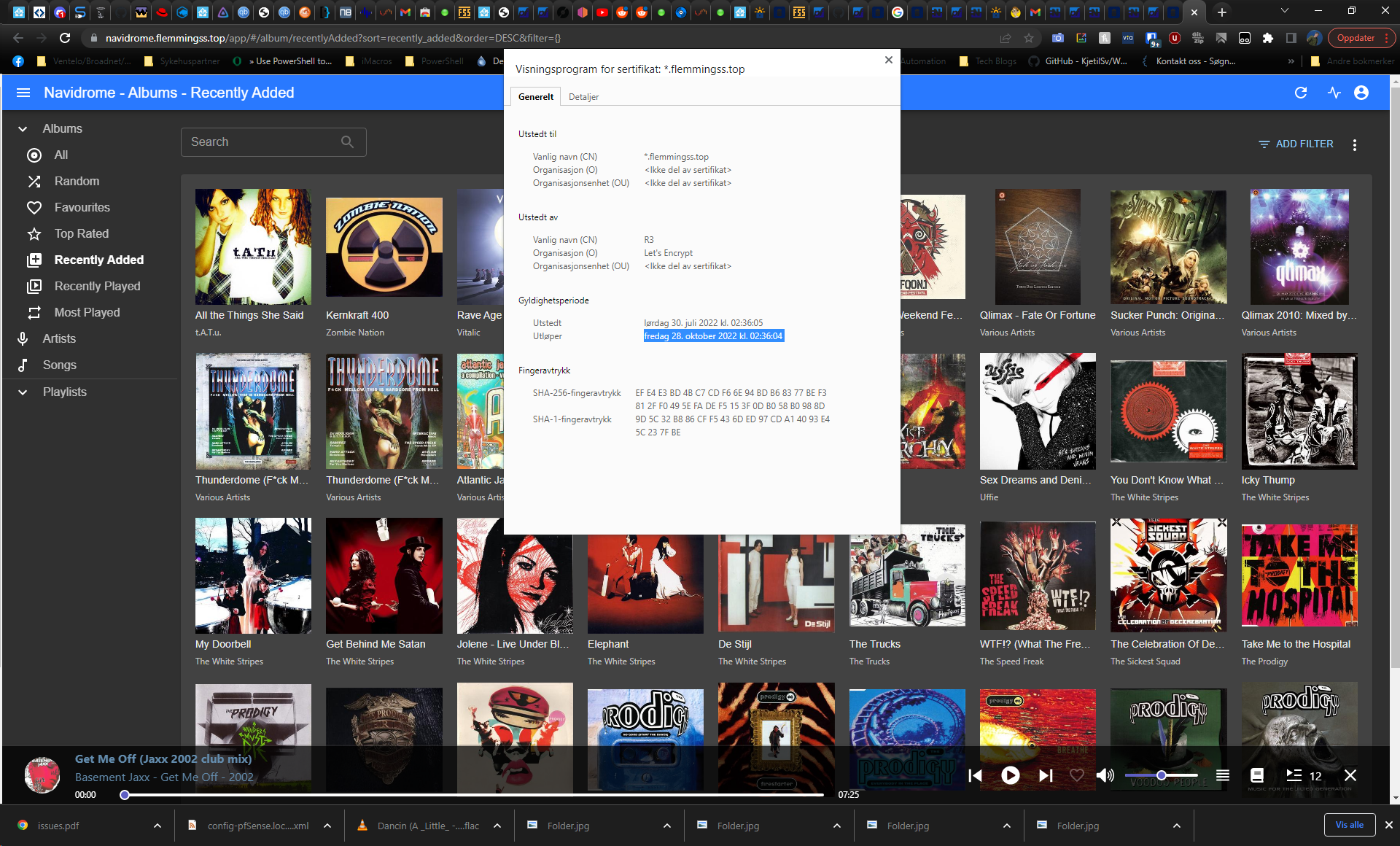
-
@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
Last try worked (i think), i did a "issue", added the TXT manually at namesilo, waited 30 minutes and did a renew
You've started to understand how things work

You should always do a manual request first. acme.sh has the manual mode for that.
This makes you understand how Letsencrypt does the test that proves that you 'own' that domain name.@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
waited 30 minutes and did a renew
The wait period is defined and known, as you can test it.
I told you to dig for it.
As soon as the returned TXT record obtained from all ( !) your domain name servers the correct 'secret' TXT value, you know the domain name servers are synced with the latest info, and you can proceed.Example :
My domain :
test-domain.frSo I ask the list of all domain name servers :
dig test-domaine.fr NS +short ns3.test-domaine.fr. ns2.test-domaine.fr. ns1.test-domaine.fr.I also want to know who the master is :
dig test-domaine.fr SOA +short ns1.test-domaine.fr. postmaster.test-domaine.fr. 2021034612 14400 7200 1209600 43200Ok, ns1 is the master.
The master will be the domain name server that gets updated using the acme.sh "method"
Let's test :dig @ns1.test-domaine.fr _acme-challenge/test-domaine.fr TXT +shortas soon as you get an answer, like :
7Df*********************************5Mkyou should test your other domain name servers :
dig @ns2.test-domaine.fr _acme-challenge/test-domaine.fr TXT +shortdig @ns3.test-domaine.fr _acme-challenge/test-domaine.fr TXT +short( for me, 3 tests as I have 3 domain name servers for my domain )
They should all return the same :
7Df*********************************5MkIf this is the case, the wait is over.
@flemmingss said in Unabl to renew cert / Unable to add the DNS record (NameSilo):
Browser still show the old date:
That's another story.
Your browser gets the certificate from the (a) web server.
The web server can do 'https' for you if it has the cert.
Upon web server startup, it reads the cert files, and now it can offer "https".
So, to get rid of the issue : easy : goto : System > Certificate Manager > Certificates and export both PEM files (key and crt), and/or the P12 file.
Now, as you are the admin of your web server, do your job : import the P12 or both PEM files.
When done, restart the web server.
And then ..... by magic ..... it works.You'll say : hey ? Do I have to do this every time my cert renews ?
Answer : yes.
The good news is : like acme.sh, a scripts that requests a new certificate, you can make you own scrip that :
Gets the certificate files from pfSense, as you know where they are stored :
I mean : a script on pfSense could copy these files to your device, and then inform your device that the web server should restart as certs have changed.
The bad news :
It's your pfSense.
It's your "navidrome" device (whatever that might be).
Up to you to discover if the "navidrome" has a (for example) SSH access, which could permit you to copy over the files by a script you have to write up from the ground.
With a bit of luck there is even a way to 'restart' the web server on that device.
Doing so, you automate the entire process.Yes, you might call this 'programming'.
I've done so myself for my synology disk station, and I managed to do so also for one of our networked printers, as I wanted to know if it could be done.
( it was tedious, with a nice good old fashioned learning curve )You could also check if this the "navidrome" device has it's own Letsencrypt/acme.sh tools build in. In that case, use it to renew navidrome.yourdomain.tld on that device. Most probably, when succeeded, it will restart the services that use the obtained certificate. case solved.
If this is not possible, you will be GUI bound : do it yourself, with the mouse and your fingers, every 60 days or so.
-
@gertjan Thank you for a very informative reply. I will read it in more detail when I have more time.
In my usecase I use HAProxy (reverse proxy) and all my services uses http behind my firewall. I did this change and it is now showing the "new" cert in browser: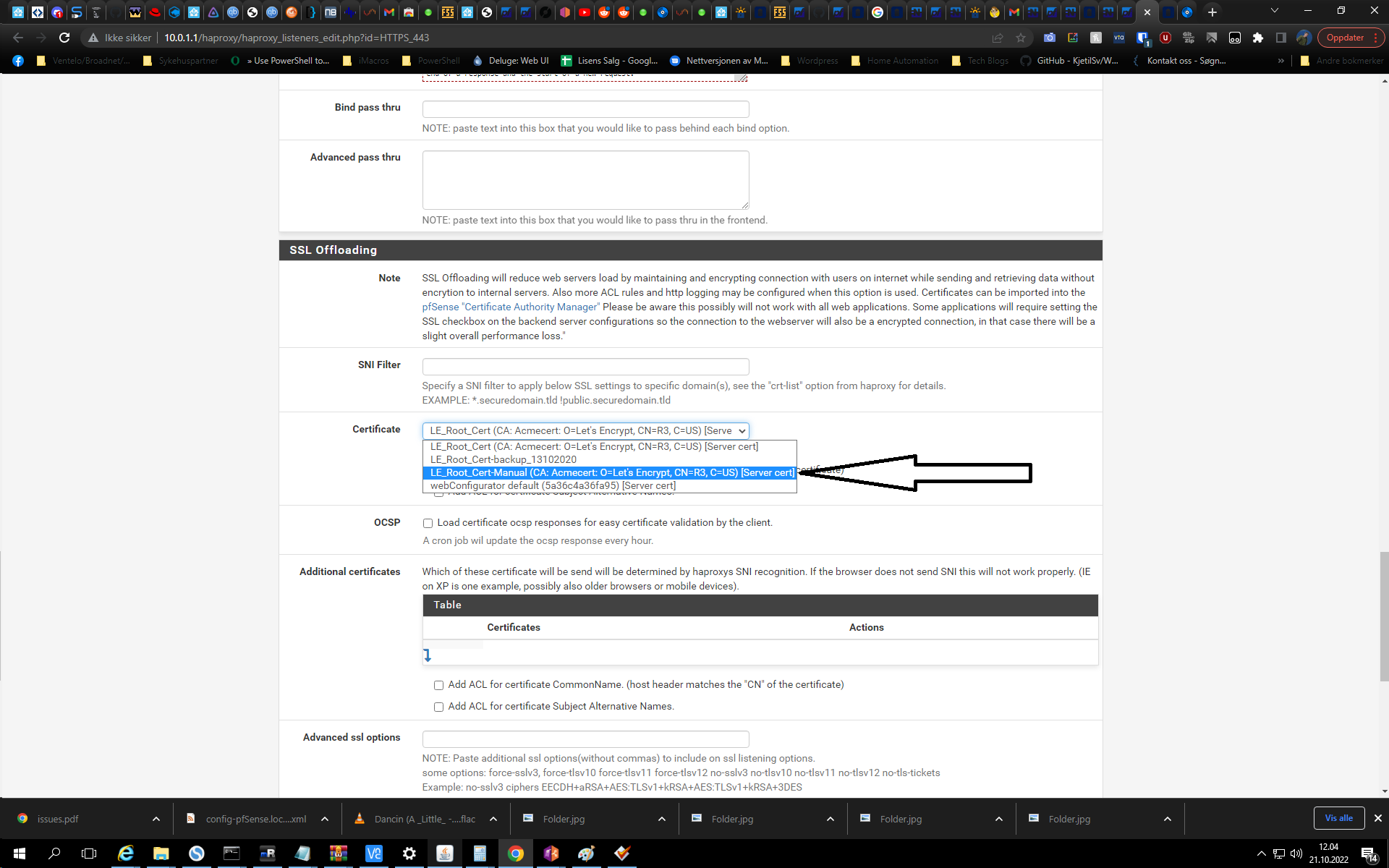
-
Aha : You are using the pfSense HAproxy package.
Go back to the
page, and start reading.
This time, up until the bottom.You will find the very important dns sleep.
That's why it's there.And also this one :
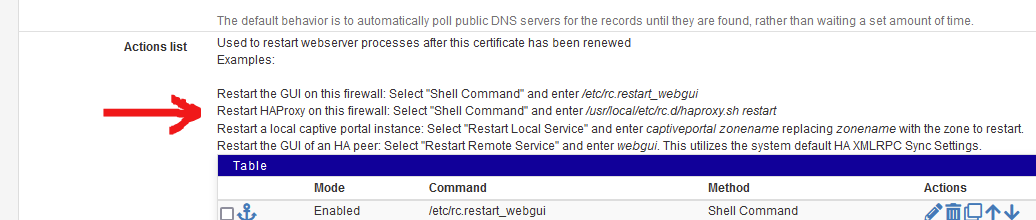
as it was made for you.
The certificate name will not change when it is renewed. No need to select 'another' cert in the HA Proxy settings.
Now, when acme.sh successfully renewed the certificate, it will also restart HAproxy. So it takes in account the renewed certificate.
And you can go back to the admin's main task : constantly ( ) checking if all automated tasks are correctly executed.
) checking if all automated tasks are correctly executed.