DNSBL and 127.0.0.1
-
Hello,
I have seen that the DNS blocker also blocks many queries from 127.0.0.1, so from the pfsense box itself.
Example logs:
ns.inwx.de,127.0.0.1,Python,DNSBL_A,DNSBL_AD_AND_MALWARE,ns.inwx.de,blocklistproject,+ dns1.easydns.com,127.0.0.1,Python,DNSBL_A,DNSBL_AD_AND_MALWARE,dns1.easydns.com,blocklistproject,+ dns2.easydns.net,127.0.0.1,Python,DNSBL_A,DNSBL_AD_AND_MALWARE,dns2.easydns.net,blocklistproject,-Mainly it seems to be DNS servers (unbound is not in "forwarding mode")
I guess that unbound is so not able to resolve all requests, right?
Is this a normal behavior?
How can I fix this without having to put all the domains on the "DNSBL Whitelist"?
Python Group Policy"doesn't seem to work with 127.0.0.1... -
Where is the file you saw these lines ?
@beerman said in DNSBL and 127.0.0.1:
Python Group Policy"doesn't seem to work with 127.0.0.1...
I've added :
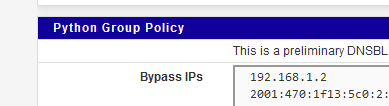
Both IPs are used by the PC I use right now.
The thing is : pfBlockerng-devel doesn't block any DNS from my (this) PC any more.
So, I tend to say : it works for me.
My PC is for a DNS is 192.168.1.1, that is pfSEnse, and 2001:470:1f13:5c0........) the IPv6 of my LAN. -
@gertjan
First I saw it in the "Reports" tab.I have the appropriate logs from Splunk, or they are in the file "dnsbl.log".
ns2.footprintdns.com,127.0.0.1,Python,DNSBL_AAAA,DNSBL_AD_AND_MALWARE,ns2.footprintdns.com,Domains__oisd_nl,+When I add 127.0.0.1 to "Python Group Policy", I still see blocks. (Even after a complete update)
Why is 127.0.0.1 blocked at all?
-
hmm, "Python Group Policy" seems to work after all.
"Python Group Policy" enabled for 127.0.0.1:
[22.05-RELEASE][admin@pfsense]/root: nslookup ns1.footprintdns.com Server: 127.0.0.1 Address: 127.0.0.1#53 Non-authoritative answer: Name: ns1.footprintdns.com Address: 13.107.6.1"Python Group Policy" disabled for 127.0.0.1:
[22.05-RELEASE][admin@pfsense]/root: nslookup ns1.footprintdns.com Server: 127.0.0.1 Address: 127.0.0.1#53 Name: ns1.footprintdns.com Address: 10.255.255.254 ** server can't find ns1.footprintdns.com: SERVFAILHowever, I still get alerts for 127.0.0.1, even with "Python Group Policy" enabled for 127.0.0.1.
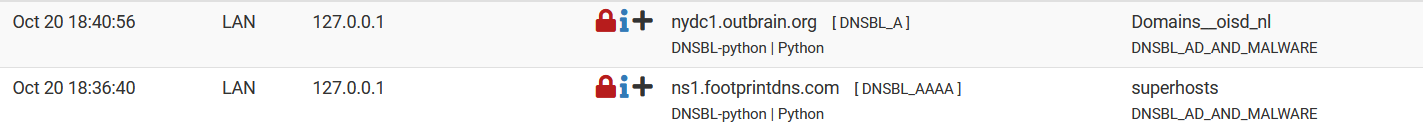
-
@beerman said in DNSBL and 127.0.0.1:
hmm, "Python Group Policy" seems to work after all.
"Python Group Policy" disabled for 127.0.0.1:
However, I still get alerts for 127.0.0.1, even with "Python Group Policy" enabled for 127.0.0.1.

I have "Python Group Policy" disabled on my system, check box unchecked.
I see a similiar thing in the logs on my system, except on mine, 127.0.0.1 resolves to "pfsense.local.lan" which is the name of my pfsense firewall/router.
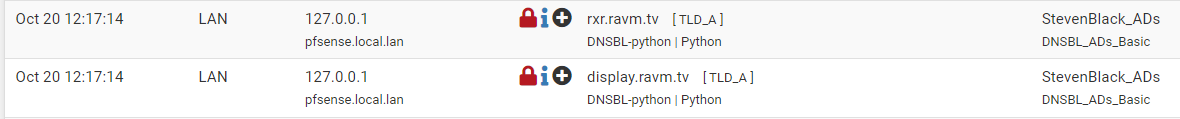
I'm running on pfSense CE 2.6.0.
-
The origin of the request was from your "LAN" interface.
But it was unbound itself that generated the request.
I can only offer an example why you see the 127.0.0.1 (localhost) :
A dns request came in on the LAN interface, port 53.
It was a A request.
The A was resolved, and points to a CNAME.
Ok, unbound re-curses, throws out a DNS request to itself (= 127.0.0.1) to get the CNAME.
That CNAME was found in a block list, thus blocked.I agree that a line like this :
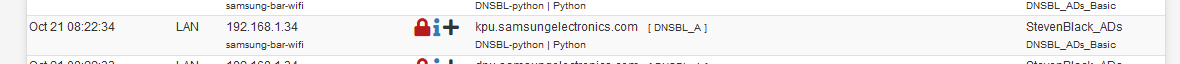
is more logic. You can see that my TV was asking for an A record, and it was blocked.