Remote admin via HTTPS
-
@bob-simmons said in Remote admin via HTTPS:
https://docs.netgate.com/pfsense/en/latest/recipes/remote-firewall-administration.html#example-firewall-rule-setup
See here for allowing on the wan
Clearly showing wan address in the rule on the wan.. This firewall is set on the lan side interfaces.. That would allow you to hit any IP on pfsense.
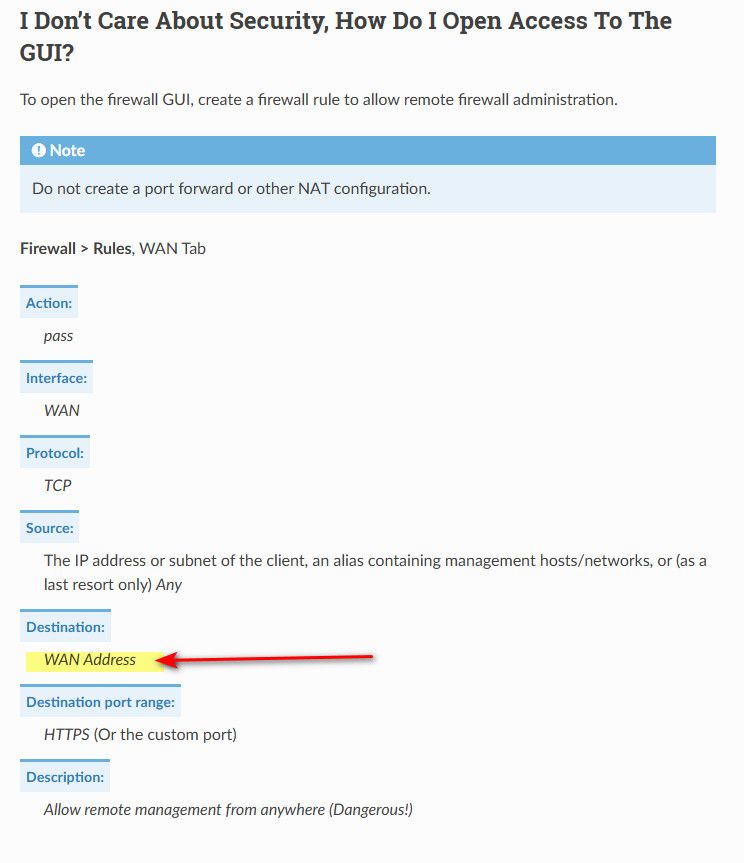
-
@johnpoz Well ... I finally got past this issue. Went on-site again yesterday and drilled into the AT&T router and found that they had not setup IP Passthrough (bridge mode) properly. I got that fixed and then I could access the pFsense router remotely. Moving forward this morning installing packages and doing other config tasks. By the way, "this firewall" as the destination address in the policy works fine. I suspect that either "wan address" or "this firewall" would work. Thanks for your help guys!
-
@bob-simmons "this firewall" is an alias that includes all IPs. So for instance if one set up rules like:
block from LAN to pfSense-LAN-IP
...LAN devices could connect to the pfSense WAN IP.
I didn't reread all the above but you'll want to limit access to your own IP as the Source.
-
@steveits Thanks. Yes, I did set up an alias for the 2 IPs that I want to have remote admin access and only those source addresses are allowed in the policy.