Exempt A Client from OpenVPN Connection
-
I have a functional openvpn connection but would like to exempt a client from the connection.
I noticed that on starting the VPN connection, all outgoing traffic, including the servers (mail, etc), are through the VPN. I have had to include the VPN address in the SPF record for the mailserver. Perhaps, I could likewise exempt the server addresses as I would want to do for one of the clients on the network.Put simply, I have the following network addresses:
Server Frame route & Static IP: 164.24.76..2/29 & 164.24.76.34
Internal network: 192.168.1.0/24 with Pfsense admin@192.168.1.1
WAP network: 10.10.1.0/24
Exempt IP: 192.168.1.34 (and perhaps the server's too).In a more slightly complex case, the IP to be exempted is on another subnet - 10.10.1.0/24. There is a Wireless Access Point@10.10.1.0/24 on the PfSense and the client to be exempted is actually 10.10.1.34. But if I could just get the 192.168.1.34 exempted, that would be fine. Suggestions for the WAP would also be appreciated.
I have tried several options but none worked. For example, setting the default gateway from my ISP as the choice gateway for the exempted IP address (a PF rule at LAN1 interface). Another is the 'bypass policy routing' but no luck. I have invariably searched the forum but none of the potential solutions worked.
-
@lamia
You have to policy route the outbound traffic to the WAN gateway.To catch only upstream traffic, create an alias and add all RFC 1918 (private) networks to it, if you didn't already.
Then add a pass route to the top of the internal network interface, at source enter the servers IP (you can also use an alias here for multiple internal IPs), at destination check "Invert match" and state the RFC 1918 alias. You may restrict the destination ports if you want.
In the advanced options select the WAN gateway.This rule then only affects traffic destined to public IP destinations thanks to the RFC 1918 alias + invert.
Without that, with destination = any, you direct all traffic to the ISP gateway, hence the server cannot do e.g. DNS resolution, when using pfSense for DNS.You can add a rule like this also to other interfaces. Consider to restrict the traffic if desired.
-
@viragomann No luck.
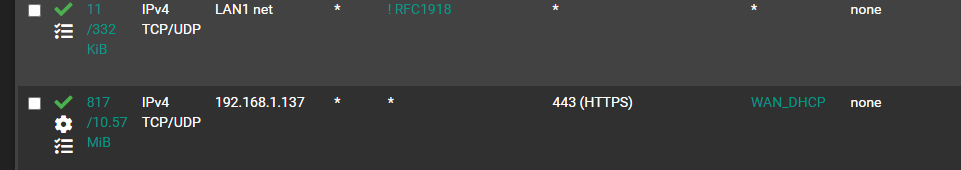
The client on the WAP still shows the VPN IP not the ISP's as its static address. I need sort this out before I can adjust the addresses to the server's. Kindly further assist. Kindly ignore that the WAP or IP network/address is different from the previously mentioned. The address to be exempted is now 192.168.1.137 (the entire WAP address on PFsense though it is a client on the WAP at 10.1.1.14 or so that is to be ONLY exempted in the long run).
-
@lamia
Your rules are not what I suggested. So the behavior is expected. -
@viragomann
0.0.0.0/1 10.6.40l.1 UGS 15 1500 ovpnc11
That is the new route created as soon as the VPN is started. Your suggestion is not working. I followed it and several others e.g. https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#figure-multiwan-bypass-policy-routing before posting the previous message.And I've tried running the VPN on various interfaces - lan1(igb0), opt5, etc but no luck. Please further assist.
-
@lamia said in Exempt A Client from OpenVPN Connection:
Your suggestion is not working. I followed it and several others e.g. https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#figure-multiwan-bypass-policy-routing before posting the previous message.
The screenshot of your rule set seems to be a mix of both, but a quite wrong one.
Read again my suggestion:
Then add a pass route to the top of the internal network interface, at source enter the servers IP (you can also use an alias here for multiple internal IPs), at destination check "Invert match" and state the RFC 1918 alias. You may restrict the destination ports if you want.
In the advanced options select the WAN gateway.and remove the alias from the LAN net rule.
At this time the LAN net rule is processed first and allow any upstream traffic to the default gateway which is the VPN.You have to include the alias into the exempt rule and put it to the top of the rule set.
-
It's interesting. I want to do the exact opposite of this. Leave the OpenVPN flexible for all users, apart from one IP address. Makes me wonder how to accomplish that.
-
@durgadas
I described a scenario of excluding one or multiple (with the help of an alias) IP from the default route. That's the TO's requirement I understood.
Why do you think we're talking about the opposite here?