Wireguard 22.05 4100
-
I have Wireguard setup on my 22.05 4100 appliance. Wireguard is linked up "green". However, it's not tunneling through. My ip still shows as my ISP ip.
Sometimes I can get it to route over the tunnel by fiddling around with some settings, but I don't really ever change any settings to get it to work. What I do is fiddle with the routing, bounce an interface, restart the wireguard process, etc.
I know this sounds bad, but I can't figure out what actually makes it route over the tunnel except that I think it may have something to do with the routing. If I setup routing to only go through the wireguard interface, it can't get internet. I have my routing setup to use the wireguard interface at priority 1 and the wan as priority 2 (or 5), it will at least route over WAN and sometimes over wireguard. I could be misinterpreting this, but if I only have it set to route over the wireguard interface, nothing will route, if I setup a loadbalanced route, it will route over the normal WAN, but if I just disable/enable the routes, thus getting it to think the wan is down, it will route over the wireguard, which then tunnels (as expected) through the wan.
I obviously have something wrong, but I can't figure out what because it WILL work. The key is that I don't actually change anything permanently, when it works, all the settings are the exact same when it only goes out the WAN or tunnels correctly.
I have the single firewall rule in the wireguard tab to allow all traffic, but I don't touch that between when it works to when it doesn't (if that helps).
Side note, I can enable/disable the openvpn tunneling and it works as expected, but I have that off when I am trying to get the wireguard to work. Also, I'm using nordvpn if that matters.
Any suggestions would be greatly appreciated.
-
I got mine to work. There are definitely some steps missing from the official docs. Here are some screen shots of my config that might help. It's possible all these are not needed, but it works for me and I've been using it instead of tinkering with it since I got it to work.
NAT Outbound set to Hybrid with the following
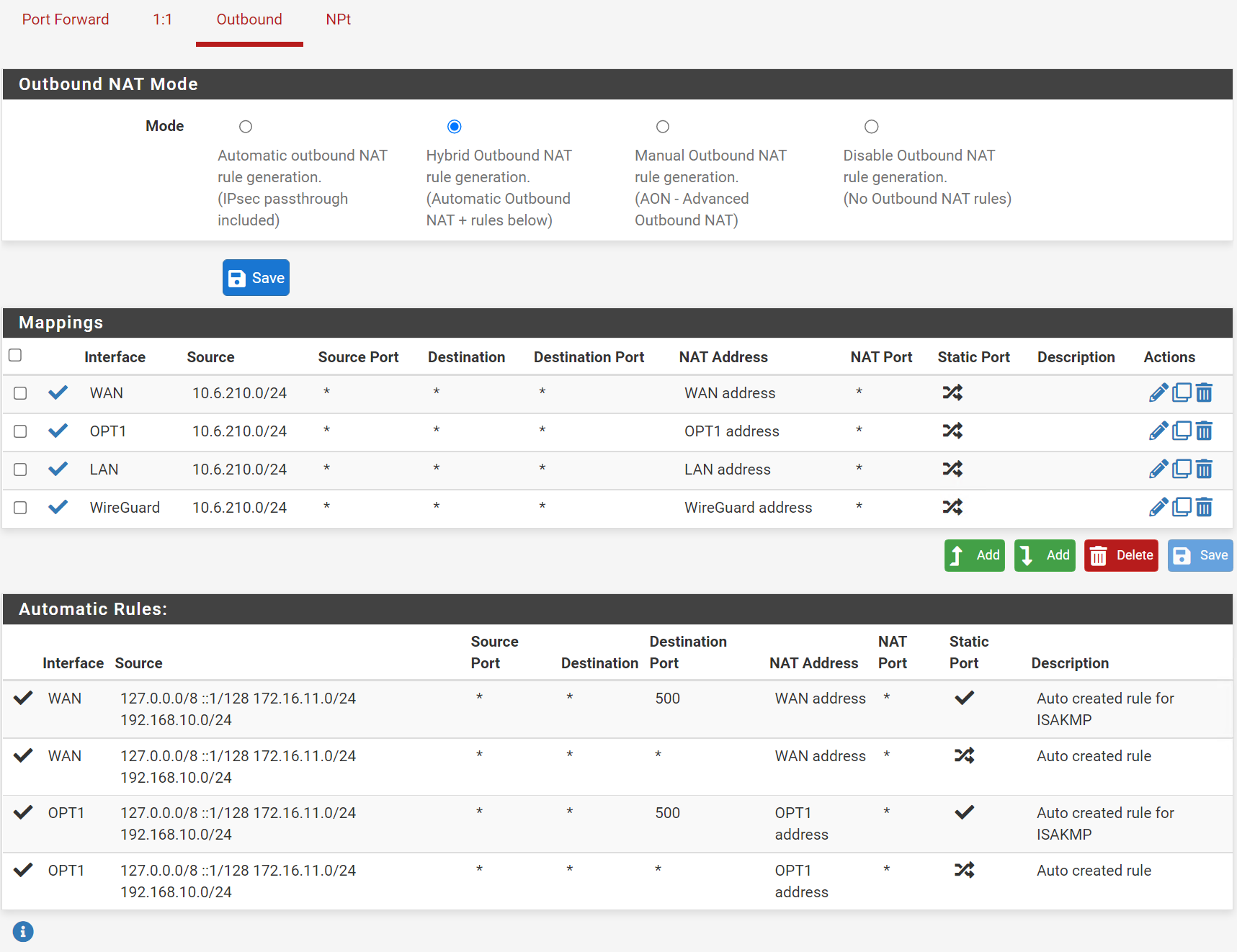
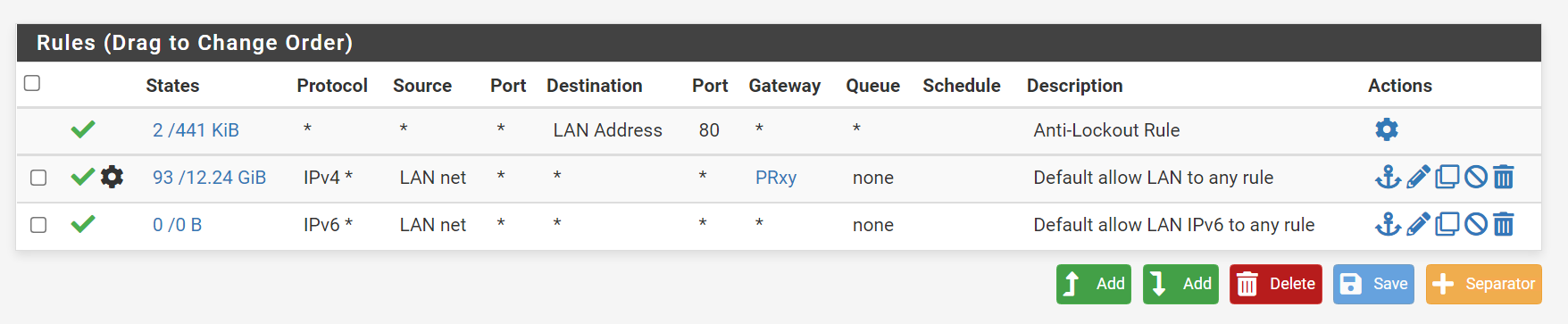
Firewall Rules Lan
This is the local net of your peer
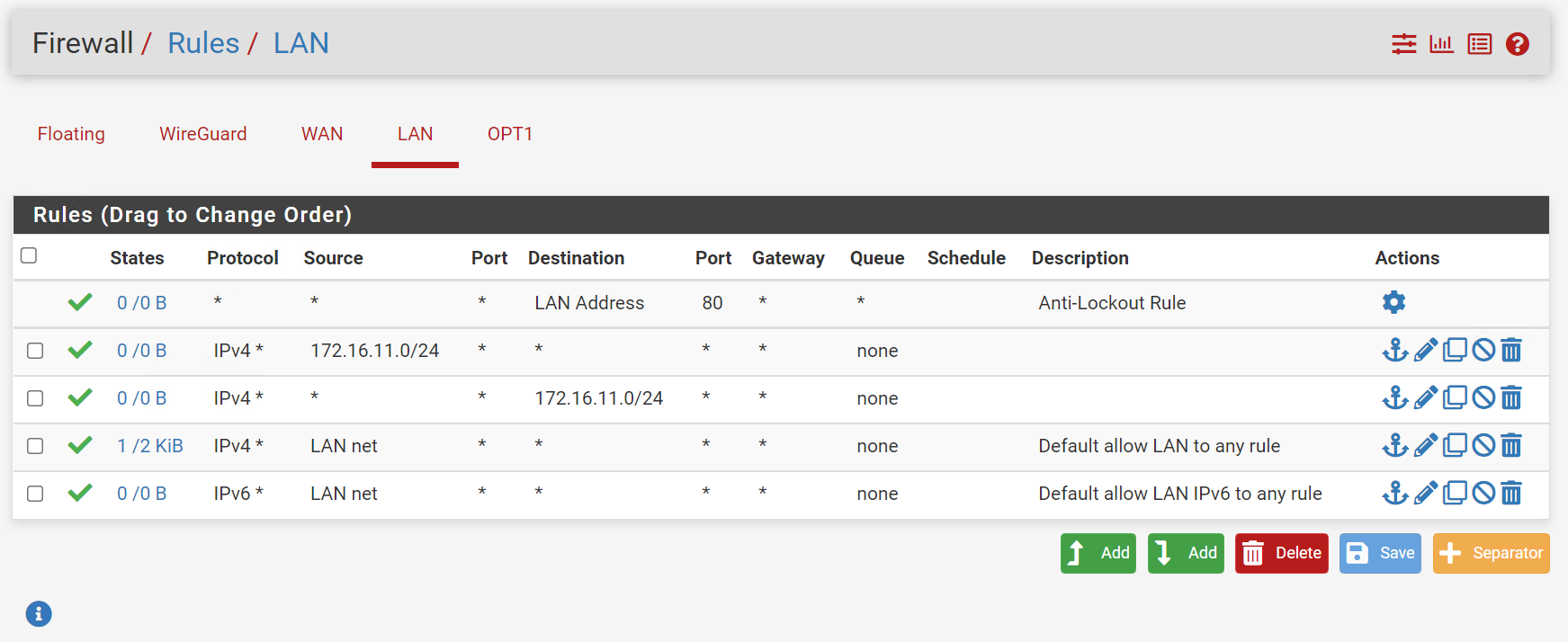
Need static routes on both ends, so flip this on the other tunnel
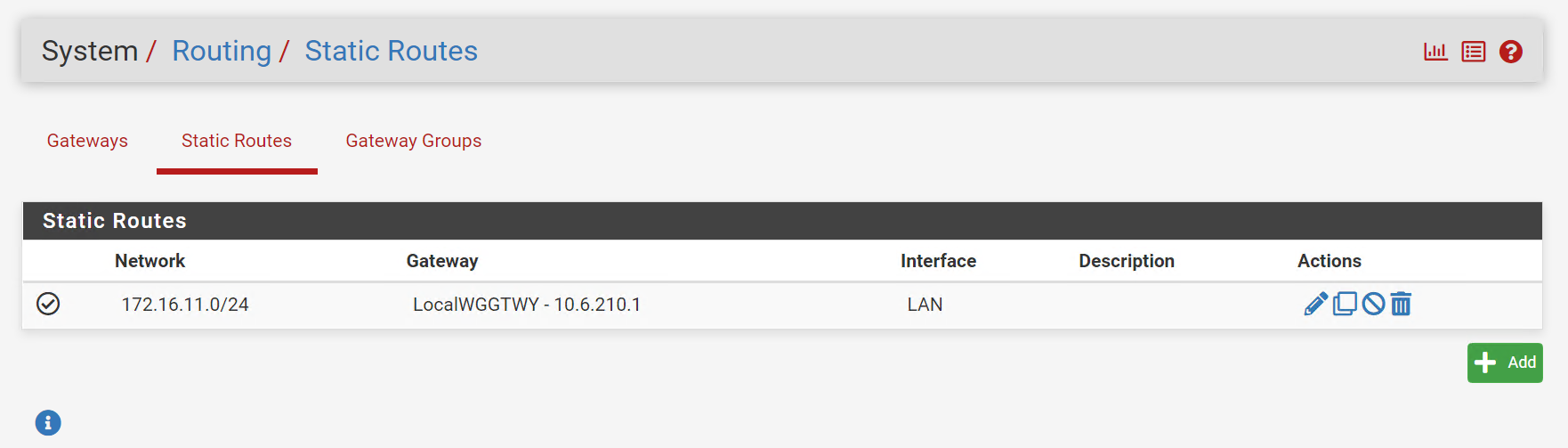
Four routing I implemented routing with the firewall rule on the LAN
Hope this helps!
-
Where do you have the 172.16.11.0/24 private address (originally) setup? In the peer? The screen shots are great, btw.
-
@davidstoll Yes, that's the local subnet of the peer.
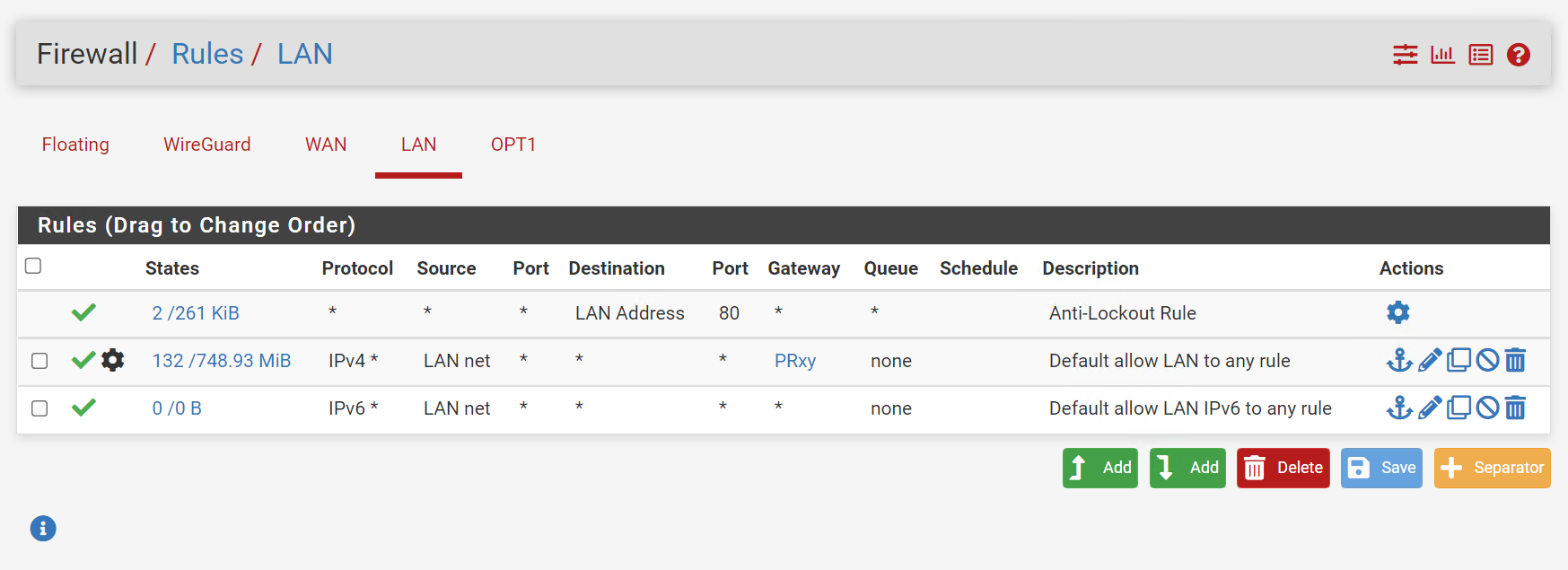
I have the same configuration on the peer, but with the local subnet of the host (pictured)
This is a screenshot of the lan rules on the peer. You could try this same rule on the host (without the source/ destination subnets) set. I was trying everything and anything trying to get it to work. But I think what helps is allowing the peer's subnet on the local subnet on the host because once the packets come out of the tunnel, they're on the local lan of the host hitting that gateway.
Advanced setting with the local wiregaurd gateway/IP the .2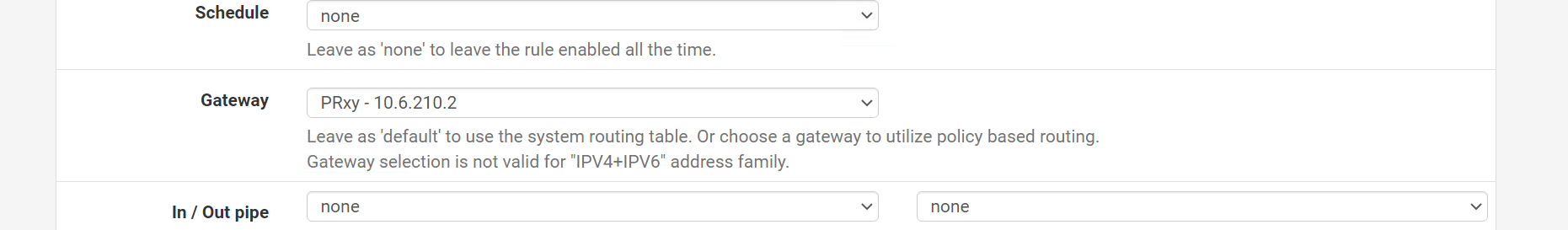
-
S seanv referenced this topic on
-
@davidstoll said in Wireguard 22.05 4100:
Also, I'm using nordvpn if that matters.
Any suggestions would be greatly appreciated.
That should have been your first sentence, not your last. Because it depends on the Privacy-VPN-Provider and, as far as I know, that one is not officially supporting it in generic clients.
-
So, (ignoring the wireguard or any kind of vpn), if you connect a device on your local lan, please clarify for me what your private IP is?
-
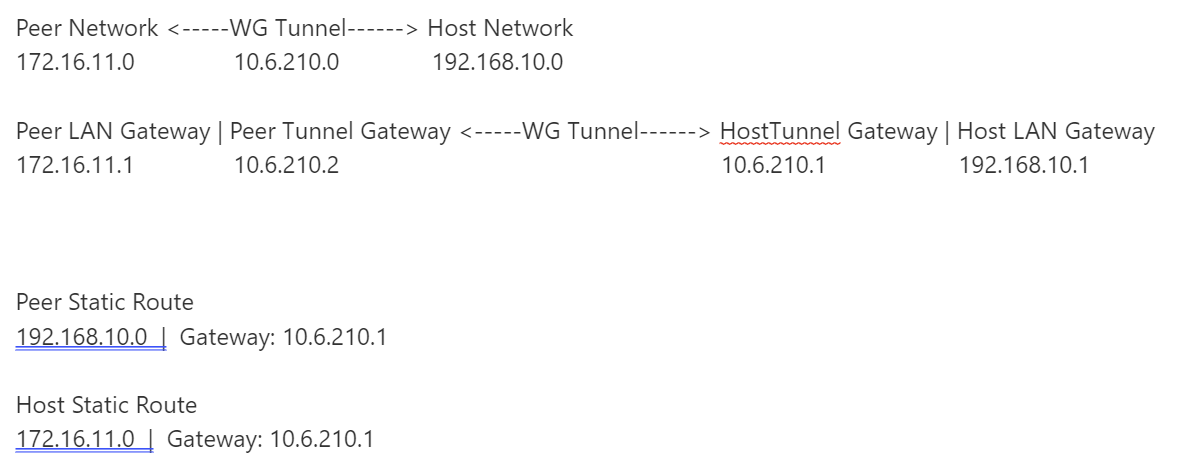
Peer Network <-----WG Tunnel------> Host Network
172.16.11.0 10.6.210.0 192.168.10.0Peer LAN Gateway | Peer Tunnel Gateway <-----WG Tunnel------> HostTunnel Gateway | Host LAN Gateway
172.16.11.1 10.6.210.2 10.6.210.1 192.168.10.1Peer Static Route
192.168.10.0 | Gateway: 10.6.210.1Host Static Route
172.16.11.0 | Gateway: 10.6.210.1