Ping from IOT still works?
-
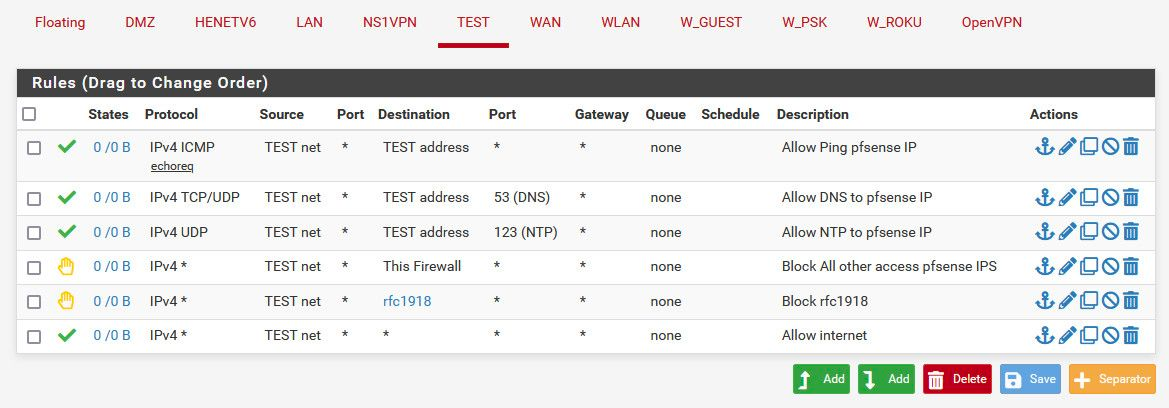
Hi Gurus, I implemented the rules from a topic that I found on the forum done by @johnpoz
If I use the ping from diagnostic and do ping to a computer that is in the rfc1918 alias rule with source address the IOT vlan the packages are received. But I would asume that the packages would be lost. Even when I Disable the first rule that allows ping between test net and test address there still received. Am I doing something wrong?
-
@freek_box Kill the firewall states and try again.
-
@nogbadthebad What do you mean, sorry I'm a noob.
-
@freek_box said in Ping from IOT still works?:
If I use the ping from diagnostic
Why would you thinking pinging from pfsense would be blocked?
To test a firewall rule on network X, you would need to be testing from network X. Not the diagnostic tool in pfsense.
There are hidden rules that allow pfsense to go anywhere.
# let out anything from the firewall host itself and decrypted IPsec traffic pass out inet all keep state allow-opts ridentifier 1000013065 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts ridentifier 1000013066 label "let out anything IPv6 from firewall host itself" -
@johnpoz hi John thank you so much for replying. On this moment I have no computer in the network that I can use to do a ping from it to a different computer so thats why I assumed I could do that from Pfsense. Just wanted to make sure I implemented your rules correctly :)
-
@freek_box well your going to need to put something on the network your wanting to lock down to test. Interface rules are not evaluated when you test from pfsense itself.
To block pfsense from going somewhere you would have to use a floating rule and in the outbound direction.
So for example if I wanted to stop pfsense from pinging say 192.168.9.100 in my lan.
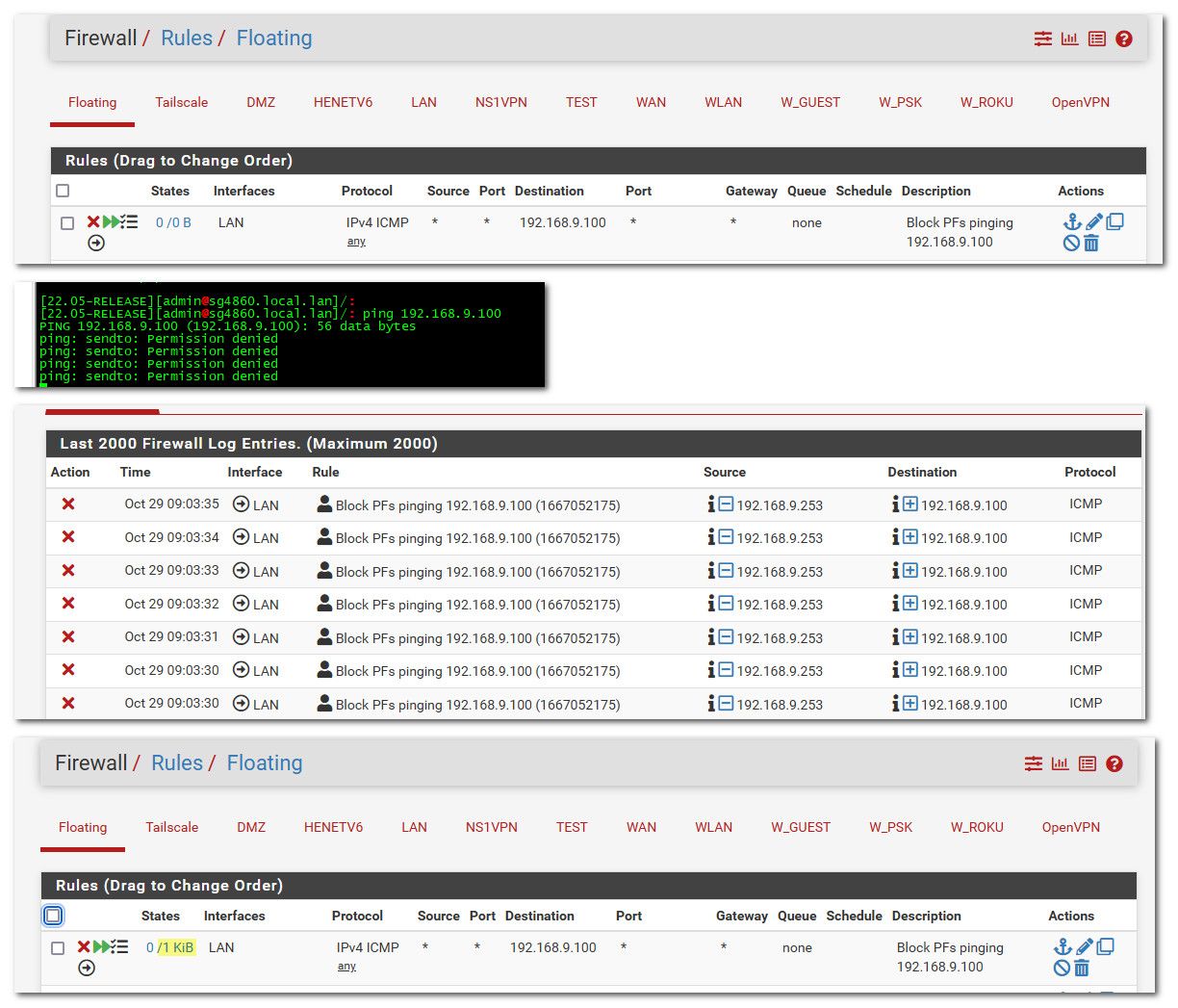
Notice how its logged, and also after I tried you see that rule shows that it has been evaluated, the 0/0 is no longer 0/0
-