Wireguard forces all ICMP outbound ping traffic to peer
-
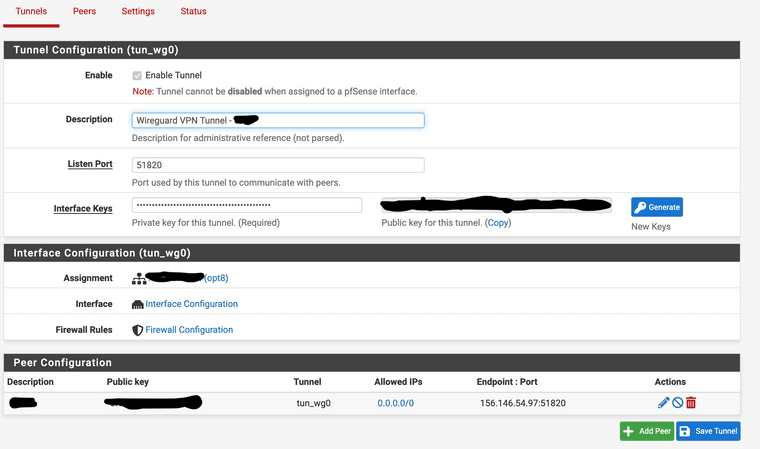
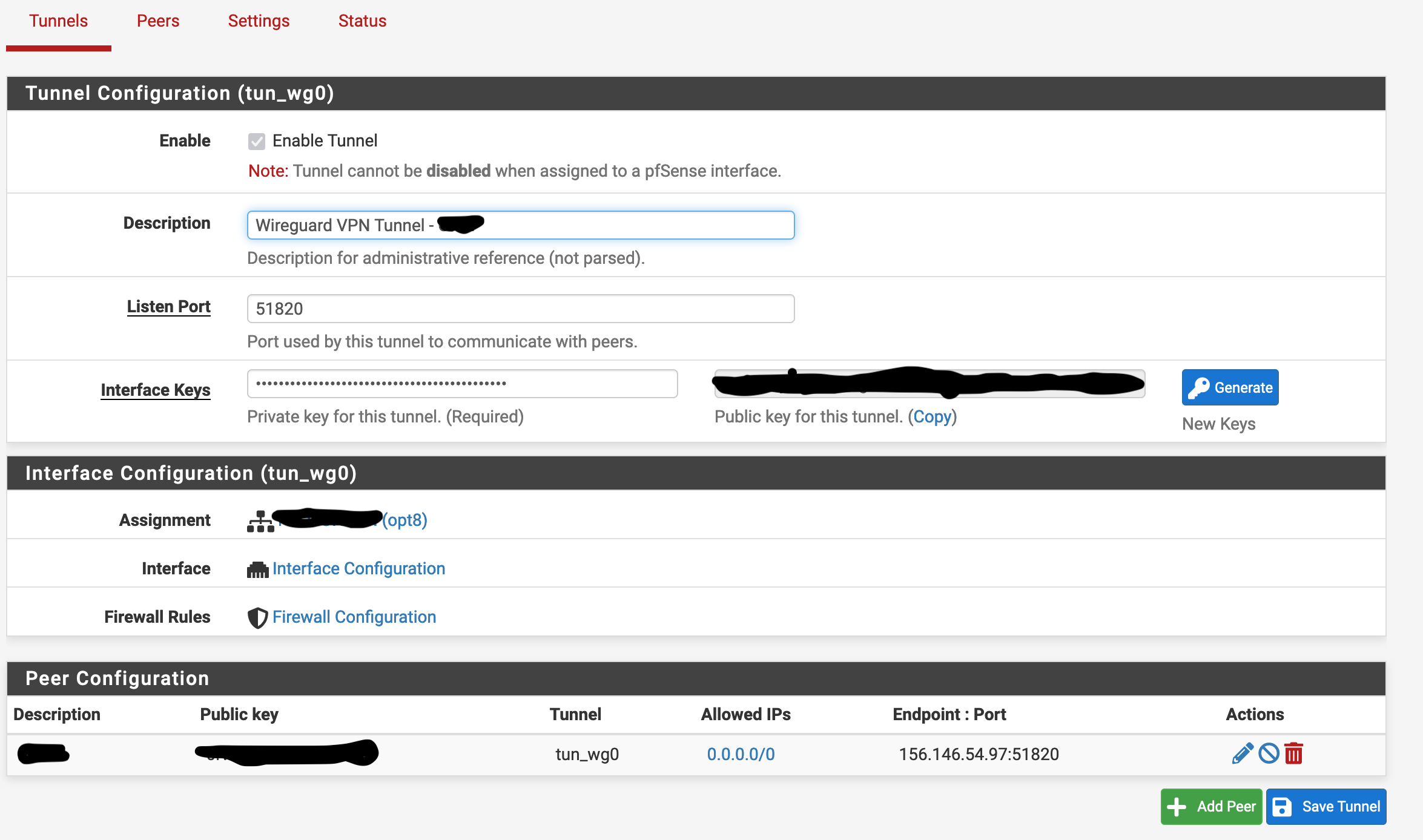
pfSense version 2.6.0, Wireguard package 0.1.6_2
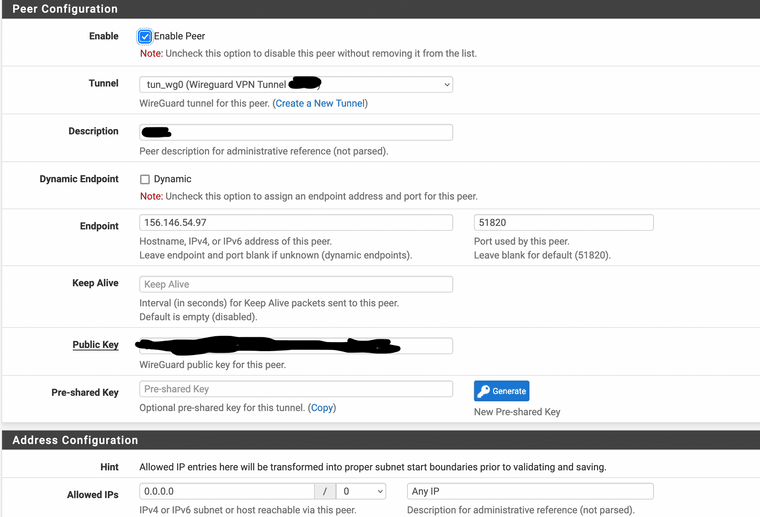
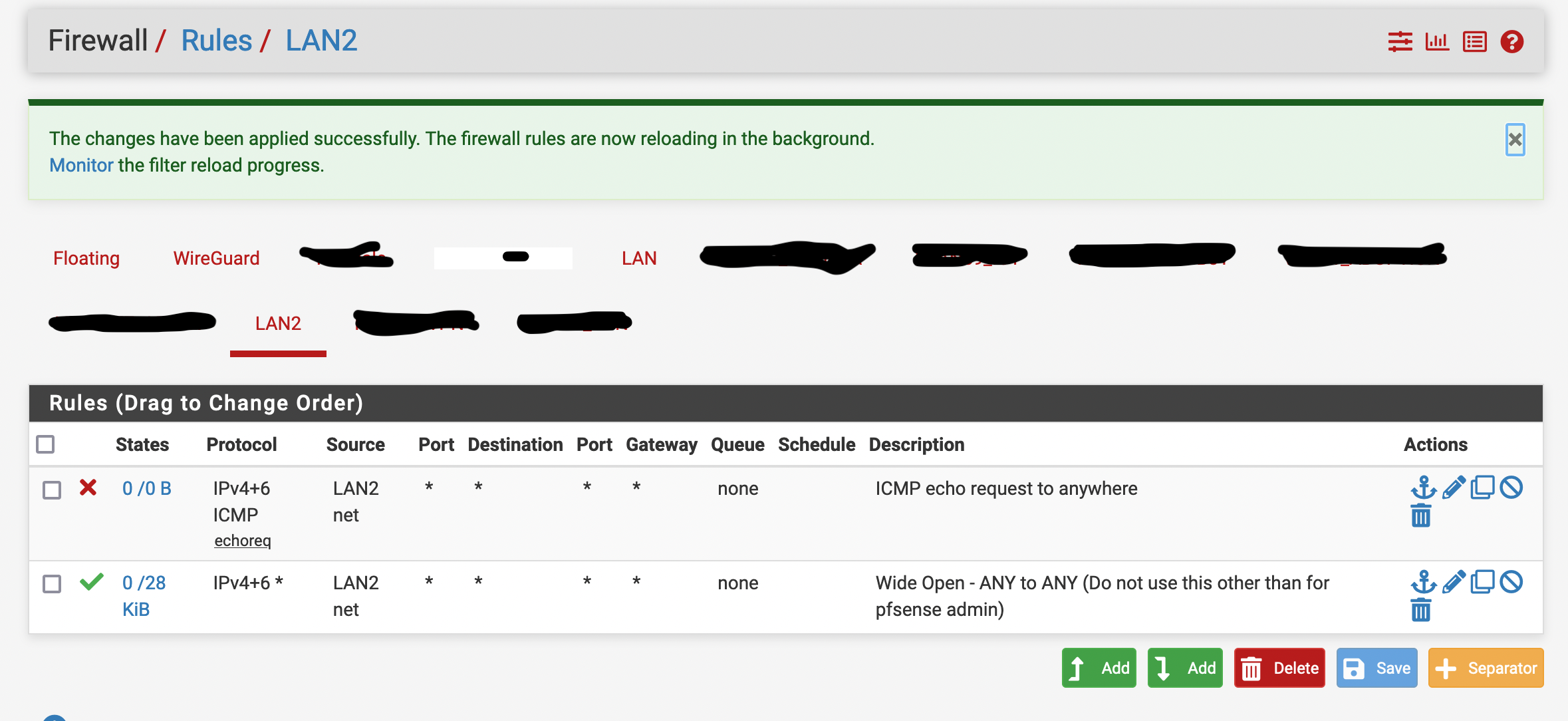
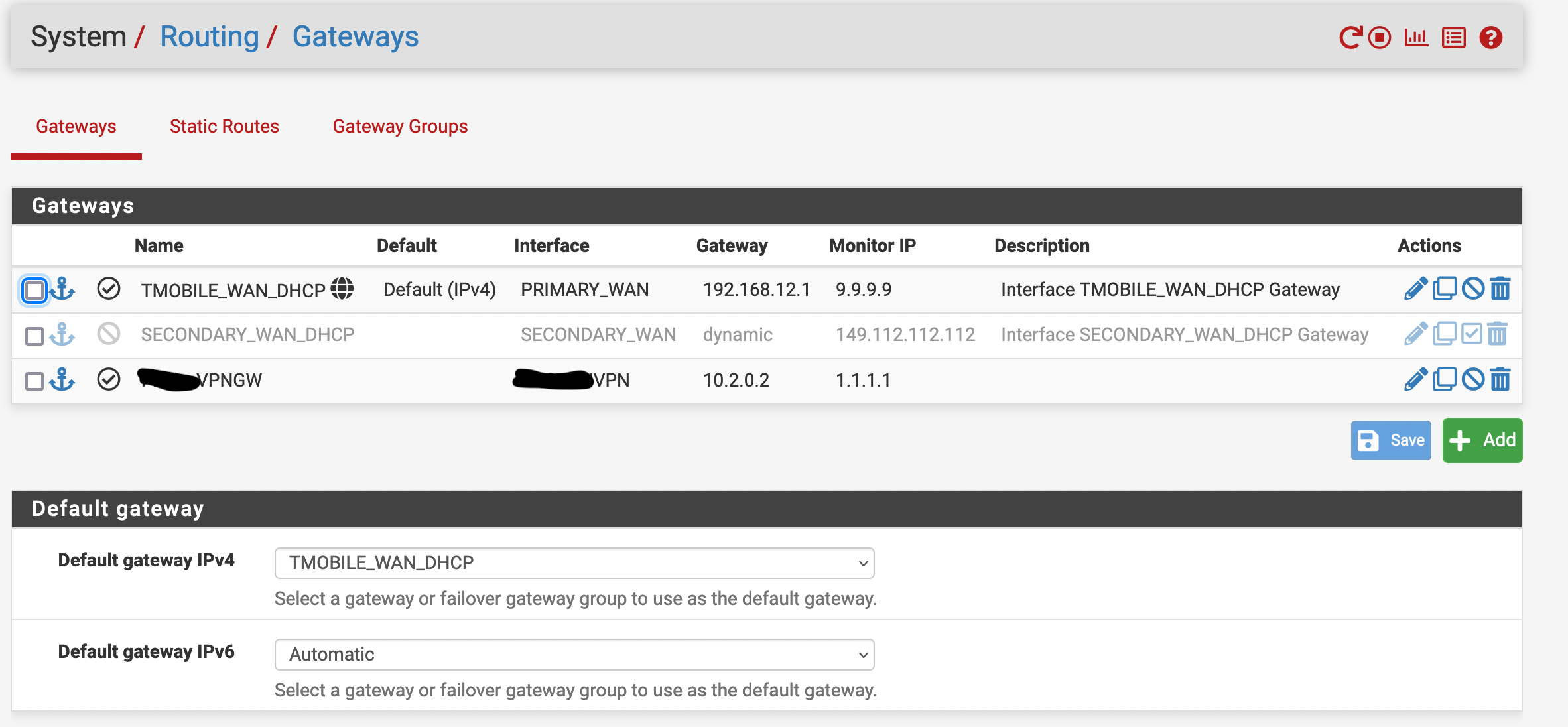
I have a Wireguard configuration setup to a commercial VPN provider. There are two gateways to the internet , the WAN (default gateway) and the Wireguard VPN. The Wireguard (non-default) gateway is meant to be used on a specific subnet to route traffic to the VPN. The outbound NAT is set to automatic. There are no custom routing rules. There are no floating rules active other than a rule to block IPv6. There are no rules on the Wireguard interface itself.
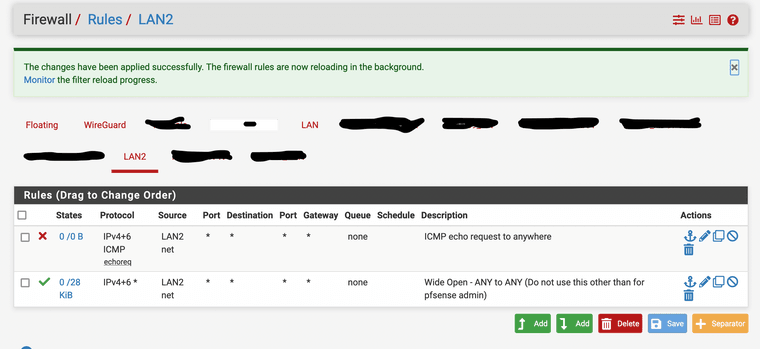
I tested on a wired connection to pfsense with only a single NIC active and only a single rule on that subnet to allow ICMP requests. This subnet should use the default WAN gateway for any traffic. If I explicitly block ICMP traffic (as the only rule) on the client's subnet, ping's still succeed as long as the Wireguard (non-default) peer is active! Once I disable the Wireguard peer, the ping fails.
If I explicitly set the default gateway in a rule to allow traffic the behavior is the same (ping's only work if the non-default gateway peer is active).
All other non-ICMP traffic seems to behave normally per the rules and defined gateways.
This seems like a bug but anybody have any other ideas?