Blocking effectively the firewall access from VLAN
-
Hello,
I finally succeeded to block the access to the FW from certain VLANs.
I blocked it from whatever address coming from whatever VLAN, awesome, really what I wanted.So why are you even asking? :D
Wait, let me finish
The issue is that it's not very clear to me how did I reach this result, so I think that I don't know how exactly PFsense works...
The rules are:
1. ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 53 (DNS)This is necessary because I use PFSense as DNSResolver, if this is not a good idea, please suggest a better one.
Also, if this exposes me to some security issue, please let me know, thanks.2. ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 853 (DNS)Same reasons as above, but I don't think it's using DNSSEC, but I'll leave this for later.
3. BLOCK ALL from_this_VLAN | ANY PROTOCOL | TO this FirewallThis rule is supposed to block the traffic from any machine in that VLAN to any FW address, which means also the rest of the VLAN interface IPs which act as a point of access for the firewall.
I didn't have any doubts on this, especially after having tested it with the IP address only, but it seems that only the order of these rules matters.4. ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 443 (HTTPS)Easy, I wanted to enable the HTTPS traffic to Internet, but I don't understand why this is working now, considering that it was denied before... (rule 3)
So, either "this firewall" means only the access to the Firewall for real, or I'm not sure how the firewall is processing the rules.
Why do I say that? Because it took 1y to casually find the solution, and it seems just for the order of the rules...
Now, I quickly tested it, this is the result:
- Inverting the order for the rule 3 and 4.
Result? HTTPS traffic works everywhere, LAN and Internet, but that's expected, if you don't consider that the last rule blocks it, even though the target is different from the previous rule. So, the order matters and the evaluation process gets out from the pile or rules when it finds the valid one.
Does it work in this way?
Obviously, this is not what I wanted, so at the moment, I left it in the original order I mentioned above, with rules in the following order: 1,2,3,4.
The next step would be to use floating rules, or to copy all the rules the to other VLANs, I'll see what's the easiest to manage...
Also, I need to setup the rules for every port/protocol, this looks quite painful... One reason I mentioned is here redirection-when-traffic-goes-to-port-80 , but it may be the only one with this requirement...
- Inverting the order for the rule 3 and 4.
-
@jt40
You can restrict all pass rules to TCP/UDP protocol. No others needed here.Port 853 is meant for DNS over TLS. DNSSEC is something else.
Yes, the rule order matters. The 4th rule is useless, since the 3rd already blocks any access to "This firewall".
- ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 443 (HTTPS)
Easy, I wanted to enable the HTTPS traffic to Internet,
That's not the way to do that. This rule, if you put it up above of the block rule, would only allow access to the pfSense itself.
If you want to allow access to the internet, but no internal, add an alias and include all private network ranges to it (RFC1918).
Use this alias in the pass rule at destination with "invert match" checked. So it will allow only access to public IP addresses, but not to your internal private networks. -
@viragomann said in Blocking effectively the firewall access from VLAN:
@jt40
You can restrict all pass rules to TCP/UDP protocol. No others needed here.Port 853 is meant for DNS over TLS. DNSSEC is something else.
Yes, the rule order matters. The 4th rule is useless, since the 3rd already blocks any access to "This firewall".
- ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 443 (HTTPS)
Easy, I wanted to enable the HTTPS traffic to Internet,
That's not the way to do that. This rule, if you put it up above of the block rule, would only allow access to the pfSense itself.
If you want to allow access to the internet, but no internal, add an alias and include all private network ranges to it (RFC1918).
Use this alias in the pass rule at destination with "invert match" checked. So it will allow only access to public IP addresses, but not to your internal private networks.Thanks.
Regarding the DNS, you're right, but it doesn't use the port 853, I'm not sure why... Probably it's specified as a secondary service, I'll check.
Unfortunately the 4th rule is necessary, the traffic doesn't pass, by default it blocks everything.
I can only query a DNS service and nothing else.
This is also why I had some doubt about the order of those rules, or if the order matters at all...
Anyway, I found the way to block the internal IP addresses: https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html
The only issue with it is that I have the ISP router before... I'm planning to remove it, but not anytime soon...
So, at the moment I think I'll need to add another rule to allow the traffic to the IP of the ISP router (or modem), but this is not exactly possible because I don't need to connect there, I need the traffic to pass through that Router/Gateway.
I'm not sure how to set this rule... -
@jt40 said in Blocking effectively the firewall access from VLAN:
Regarding the DNS, you're right, but it doesn't use the port 853, I'm not sure why...
You will configure the clients to use DoT. However, I can't see the need to use it within your local network.
It probably makes sense for DNS requests going out to the internet.If you really want to use DoT on the DNS Resolver, you need to provide an SSL certificate, which the clients are trusting.
Unfortunately the 4th rule is necessary, the traffic doesn't pass, by default it blocks everything.
Can't imagine that it makes any difference if both rules have "This firewall" as destination set, as you stated above.
Anyway, I found the way to block the internal IP addresses: https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html
This only blocks private traffic to IPs from going out to WAN. This would be the case if you request an IP that isn't part of any of pfSense networks.
But it doesn't block access to other internal networks.I need the traffic to pass through that Router/Gateway.
I'm not sure how to set this rule...I mentioned above already, how this could be done using an RFC1918 alias.
Looks like this on my pfSense:
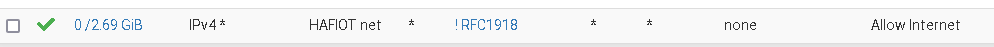
To allow access to your modem, you need to add an additional pass rule above of this.
-
@viragomann said in Blocking effectively the firewall access from VLAN:
@jt40 said in Blocking effectively the firewall access from VLAN:
Regarding the DNS, you're right, but it doesn't use the port 853, I'm not sure why...
You will configure the clients to use DoT. However, I can't see the need to use it within your local network.
It probably makes sense for DNS requests going out to the internet.If you really want to use DoT on the DNS Resolver, you need to provide an SSL certificate, which the clients are trusting.
Unfortunately the 4th rule is necessary, the traffic doesn't pass, by default it blocks everything.
Can't imagine that it makes any difference if both rules have "This firewall" as destination set, as you stated above.
Anyway, I found the way to block the internal IP addresses: https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html
This only blocks private traffic to IPs from going out to WAN. This would be the case if you request an IP that isn't part of any of pfSense networks.
But it doesn't block access to other internal networks.I need the traffic to pass through that Router/Gateway.
I'm not sure how to set this rule...I mentioned above already, how this could be done using an RFC1918 alias.
Looks like this on my pfSense:

To allow access to your modem, you need to add an additional pass rule above of this.
I didn't enable the DNS forwarder, so only PFsense can resolve domains.
In the setup of DNS over TLS I see the option for the certificate, it's set by default and it's the default one from PFSense, but it doesn't work with that port&protocol, even if I set up only DNS over TLS.
It seems not listening on that port at all, just looking at the answer of "dig".I need to make a correction, the 4th rule now is this:
ACCEPT ALL from_this_VLAN | with ANY protocol | TO RFC1918 (inverse rule) | port 443 (HTTPS)It allows internet traffic on port 443 with HTTPS.
Thank you, I followed your suggestion to use only that alias to make it easy (inverse or not), but it's also the correct way to do it.
In future, I'll try to automate everything with floating rules, I have something like 15 VLANs.