Deny RFC 1918 properly
-
Hello,
I followed your procedure to DENY the RFC 1918 range of internal addresses, but I need some confirmation that it's working as expected.
My setup is the following:
ISP modem/router
PFSense Router
L2 Switch
APBasically, the PFSense WAN points to another LAN, reason why I was expecting that all the traffic would be blocked, but it's not being blocked.
These are the rules in one of the PVLAN (it works the same for another that is also used for the AP):
ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 53 (DNS)This is necessary because I use PFSense as DNSResolver, if this is not a good idea, please suggest a better one.
Also, if this exposes me to some security issue, please let me know, thanks.ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | port 853 (DNS)Same reasons as above, but it's not using DNS over TLS, but I'll leave this for later.
Moreover, what's the reason for using it if I own my infra?BLOCK ALL from_this_VLAN | ANY PROTOCOL | TO RFC 1918 rangeThis rule is supposed to block the traffic from any machine in that VLAN to any FW address, which means also the rest of the VLAN interface IPs which act as a point of access for the firewall, + other VLANs.
As a summary, I have VLANs isolation and FW access blocked, awesome.I didn't have any doubts on this, especially after having tested it with the IP address only, but it seems that only the order of these rules matters.
ACCEPT ALL from_this_VLAN | ANY protocol | TO RFC 1918 range (inverse rule / public range) | port 443 (HTTPS)ACCEPT ALL from_this_VLAN | ANY protocol | TO this Firewall | TO RFC 1918 range (inverse rule / public range) | port 500 + 4500 (ISAKMP + IPsec NAT-T)This rule ALLOWs all the traffic in public ranges, I use it for WiFi calling.
The funny story is that above my PFSense router, there is another LAN given by the ISP modem/router.
I was expecting that to be blocked, but I think that the story works in this way: this is a simple traffic routing, I'm not trying to reach an internal IP address with WiFi calling or HTTPS traffic on Internet, therefore, the routing is allowed outside the PFSense router, even though above there is another LAN.
Did I get it right? -
@jt40 said in Deny RFC 1918 properly:
followed your procedure to DENY the RFC 1918 range of internal addresses
Who's procedure?
Can you not just post images of your rules.. It is so much easier that way.. The whole tab so can see what order the rules are in, etc.
but it's not being blocked.
What exactly is not being blocked.. Order of rules matter, any rules on floating tab matter. If your using an alias with rfc1918 specified, what you actually put in it matter.. Existing States matter, this is common issues users run into when trying to put in block rules and testing that they are working.
example:
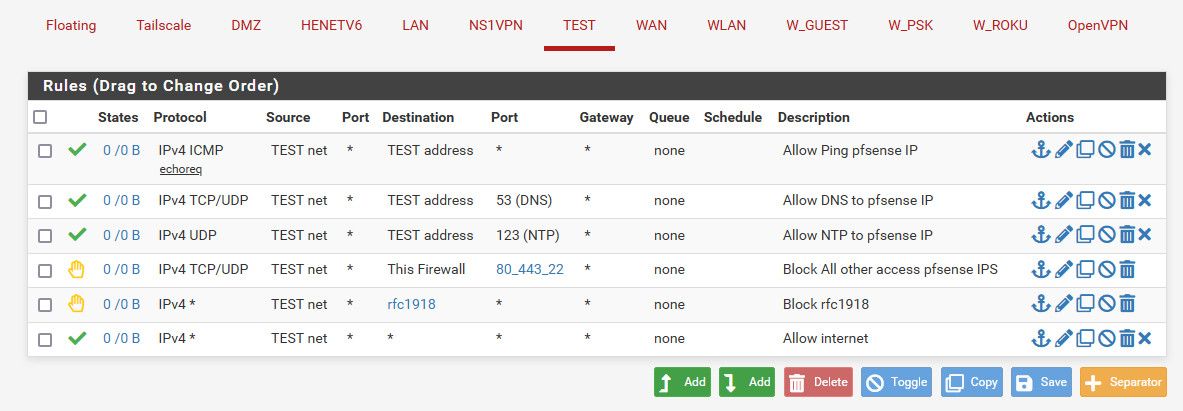
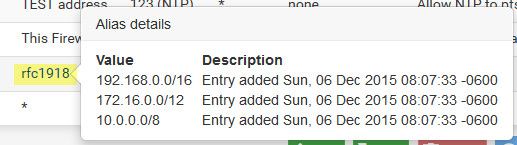
See how easy that is to interpret ;) And here you can see my rfc1918 alias
-
@johnpoz said in Deny RFC 1918 properly:
@jt40 said in Deny RFC 1918 properly:
followed your procedure to DENY the RFC 1918 range of internal addresses
Who's procedure?
Can you not just post images of your rules.. It is so much easier that way.. The whole tab so can see what order the rules are in, etc.
but it's not being blocked.
What exactly is not being blocked.. Order of rules matter, any rules on floating tab matter. If your using an alias with rfc1918 specified, what you actually put in it matter.. Existing States matter, this is common issues users run into when trying to put in block rules and testing that they are working.
example:

See how easy that is to interpret ;) And here you can see my rfc1918 alias

Thanks, I used this procedure: rfc1918-egress
I created an alias, I'm not using floating rules to make it easy for now, then I'll automate it with floating rules.I'm not sure about existing states, I'll reboot the firewall to make sure they don't give me the illusion that something is working or not working.
Anyway, my question was if my setup is ok, basically if it's working as expected due to the last point I mentioned in the first post "the routing is allowed outside the PFSense router, even though above there is another LAN, because this is a simple traffic routing to a public IP address." -
@jt40 said in Deny RFC 1918 properly:
I'm not using floating rules to make it easy for now
Well that policy is clearly a floating tab only rule, because it is egress
"Navigate to Firewall > Rules, Floating tab" From the procedure you just linked too.
If you had a rule that was actually being evaluated that contained rfc1918 and your destination was rfc1918 then it would be blocked, be it on pfsense wan, or upstream of that.. Now if your destination was actually a public IP, and pfsense has a rfc1918 transit then no it wouldn't be blocked..
If you want someone to take a look at your rules, and bless them or point out issues - posting pictures of the whole tab is going to get way more people interested in commenting..