Route from pfSense to GL.iNet Slate not working
-
@viragomann said in Route from pfSense to GL.iNet Slate not working:
Why don't you simply connect the RPi to the switch with pfSense LAN? What is the sense of having it behind the Slate?
Because i don't want to handle/switch different IPs (home or not home) on the phone.
And everything will be in one box. I don't want to replug cables.
Just one cable i can connect to the switch and not unplugging the cable inside the box from the RPi.Also it would be nice the settings UI from the Slate would be reachable from the workstation (pfSense LAN).
-
@mrglasspoole
So put the GL.iNet Slate into a transit network, as already suggested above and all routing should work properly. -
@viragomann Yep i already googled "transit network" when you first mentioned it but found nothing.
-
I carry the Slate around. Its main purpose is a
portable music player.Ok this is more better to know first for us. Thnx.
If I would in your or situation I would really consider
one of the next solutionsSolution 1
DMZ Switch- Netgear GS105Ev3 ~25 € (5 Port)
- Netgear GS108Ev3 ~35 € (8 Port)
- Or an equivalent TP-Link model for less money
Another PCIe NIC
- Intel i350-T4 - cheap on eBay (4 GB Ports)
- Intel i340-T4 - Cheap on eBay (4 GB Ports)
-- 4 GB LAN Ports
-- Supported well in pfSense
-- Not the need of one more PCIe slots or Card
-- 2 x WAN | 1 x DMZ | 1 x LAN port are available
-- You may add the Slate in front of the pfSense
WAN too (If needed)
A WiFi card
- A cheap wireless N card for 12 €
- Antennas for less then for 10 €
Soition 2
Building Vlans might be cheaper and faster was to
work around, but even connecting the Slate into the
LAN and perhaps one day later into the WAN makes
the things not much more easy.With the first solution you let the Slate in the bag and connect only here and there the RAPI, but you own
WiFi and nothing must be changed on top of all also
perhaps the VLANs must not really be! And if really
needed you could set up (connect) the Slate into
the second available WAN Port if you will use it. -
@mrglasspoole
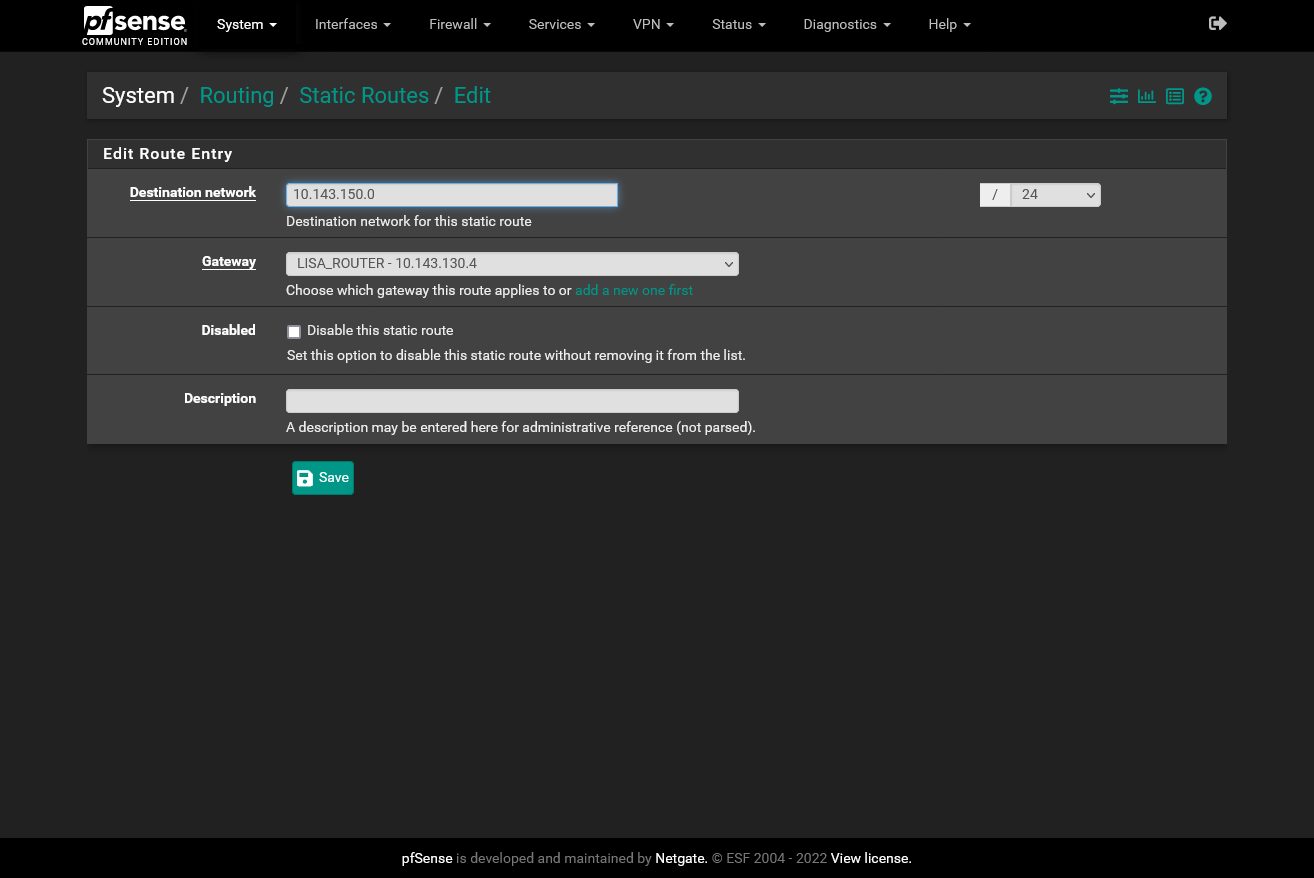
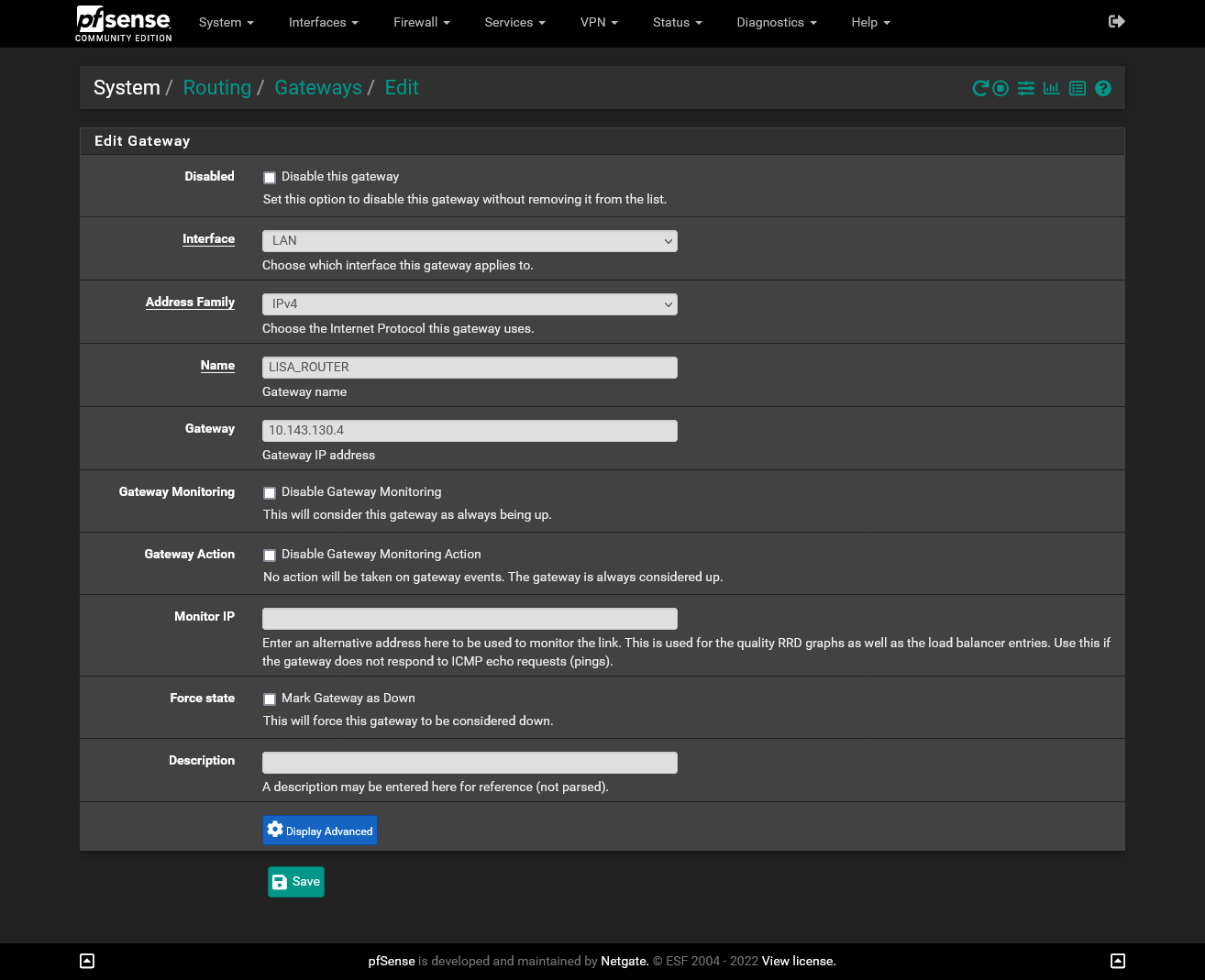
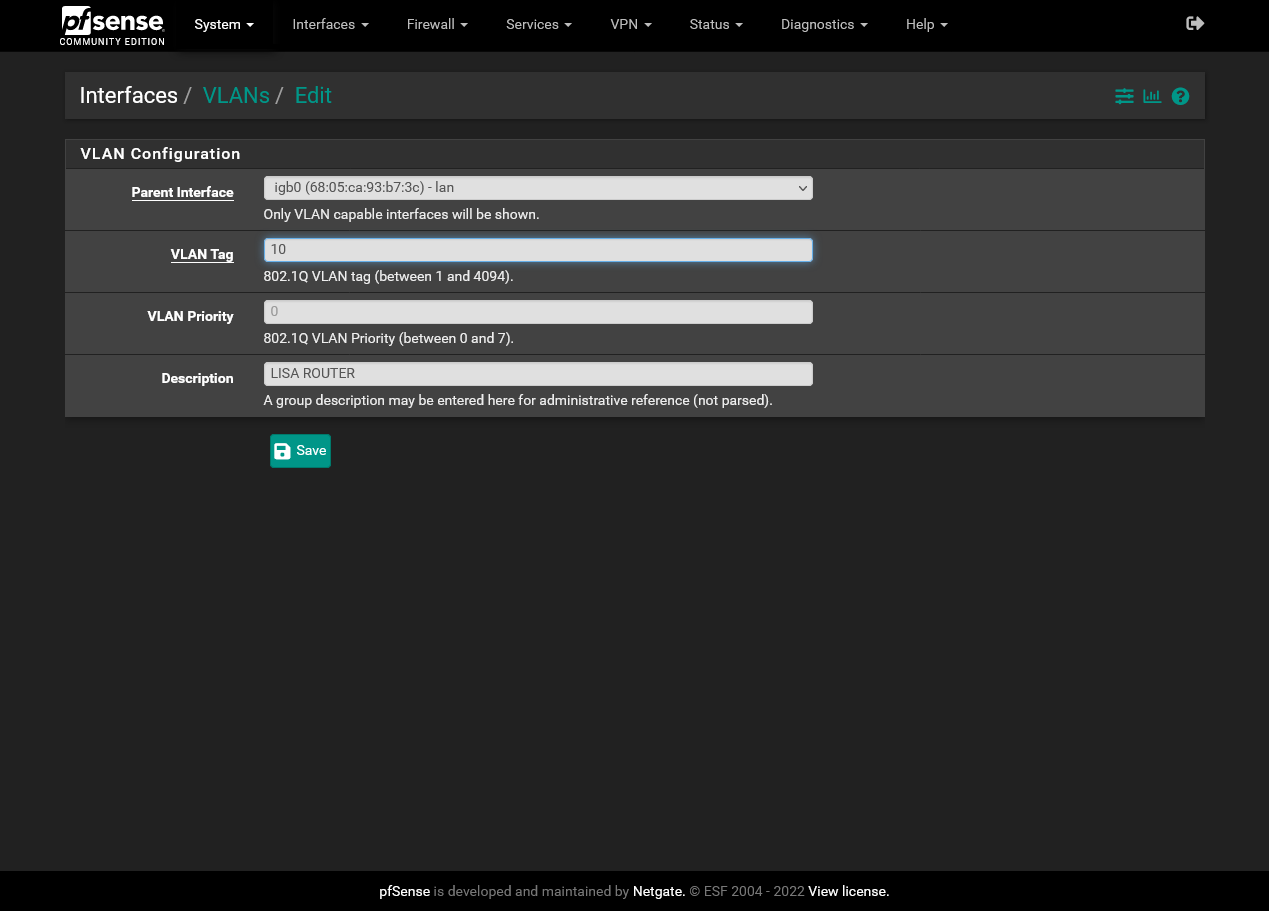
That's nothing special than an additional network segment between pfSense (default gateway in the network) and the GL.iNet Slate, segregated from your LAN.You can leave the hardware as it is and do this with a VLAN.
Configure a VLAN on the pfSense LAN port and as well on the switch, both tagged and assign the respective switch port to it as untagged. Here connect the Slate.Configure the static route on pfSense for the network behind it.
-
@viragomann sorry i can't figure it out.
100 tutorials later and they are all different.Some use routing, some not, some have 100 Firewall settings, some have both, one says "VLAN routing is automatically configured" if you create a VLAN...
The VLAN interface has its own IP, the routing gateway has one, also the VLAN has its own DHCP server.
I don't look through :-(
-
@mrglasspoole
The transit network is simply a segregated network segment. You have to configure two devices: pfSense and the switch:
Are there any difficulties?VLAN routing might be a term of virtualization. As I got your setup, there is no one involved.
DHCP? The Slate should have a static IP. If it needs DHCP, because you want to attach it also to other networks then use static mapping, since it needs a static IP as you want to route traffic to it.
-
@viragomann sure there are difficulties because I'm trying to make sense of all this:
https://www.linuxsysadmins.com/setup-vlan-on-pfsense/
https://www.wundertech.net/how-to-setup-vlans-in-pfsense/
https://techexpert.tips/pfsense/pfsense-vlan-configuration/I never did setup VLANs before.
-
@mrglasspoole
First you should learn the basics of VLANs to understand, what it is and how it works. -
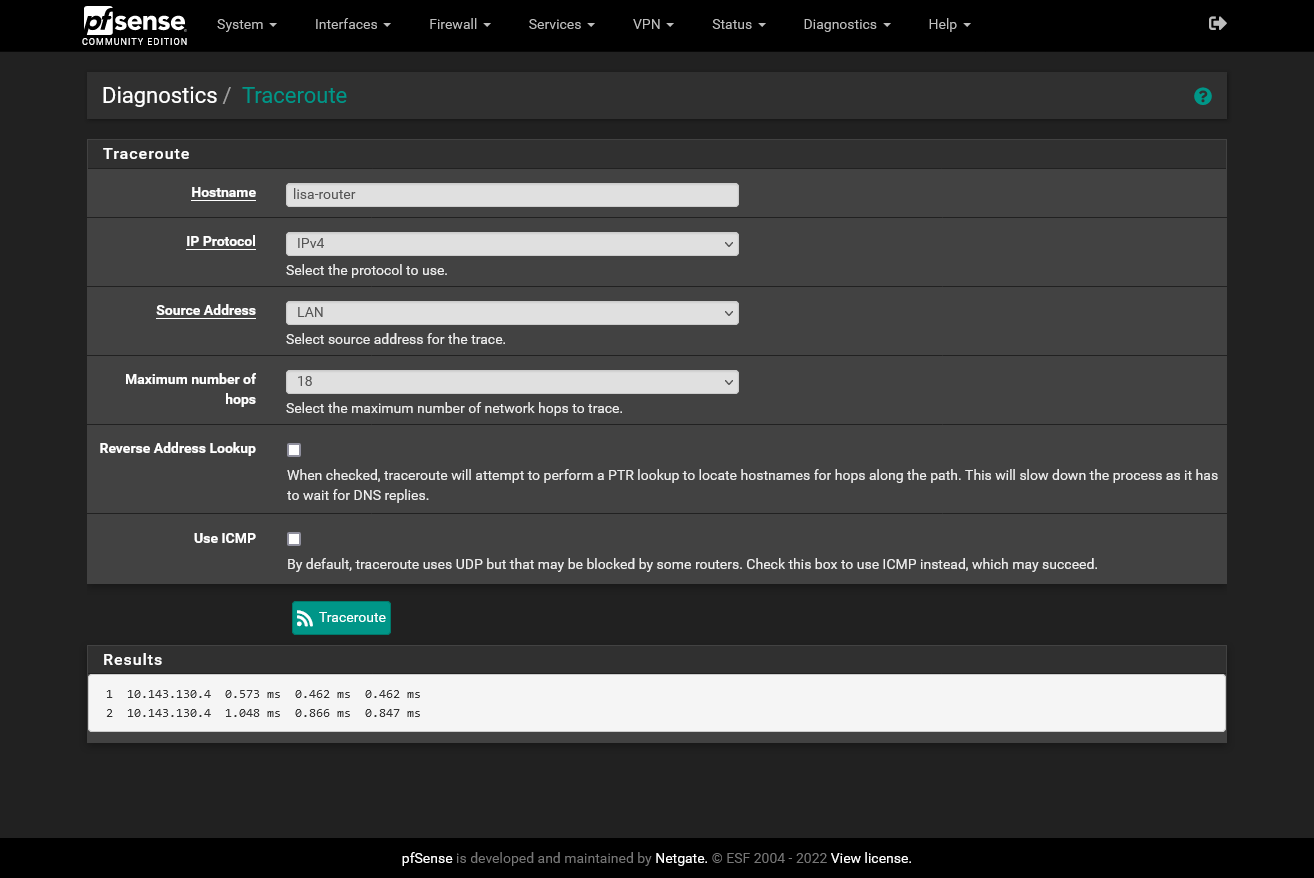
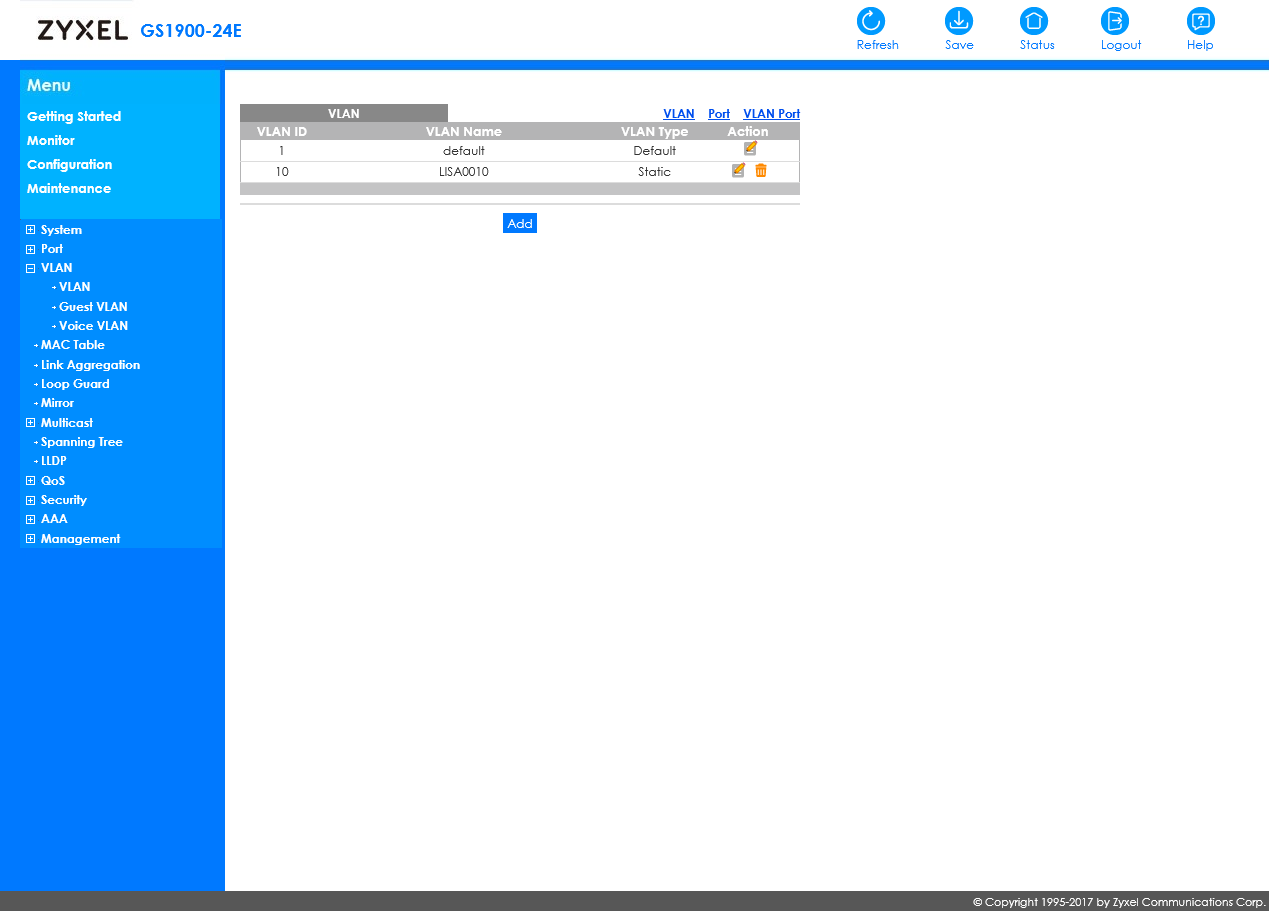
Can't figure it out.
The Slate LAN port gets an IP from the pfSense LAN DHCP server or nothing.
I guess there is some setting wrong on the switch.
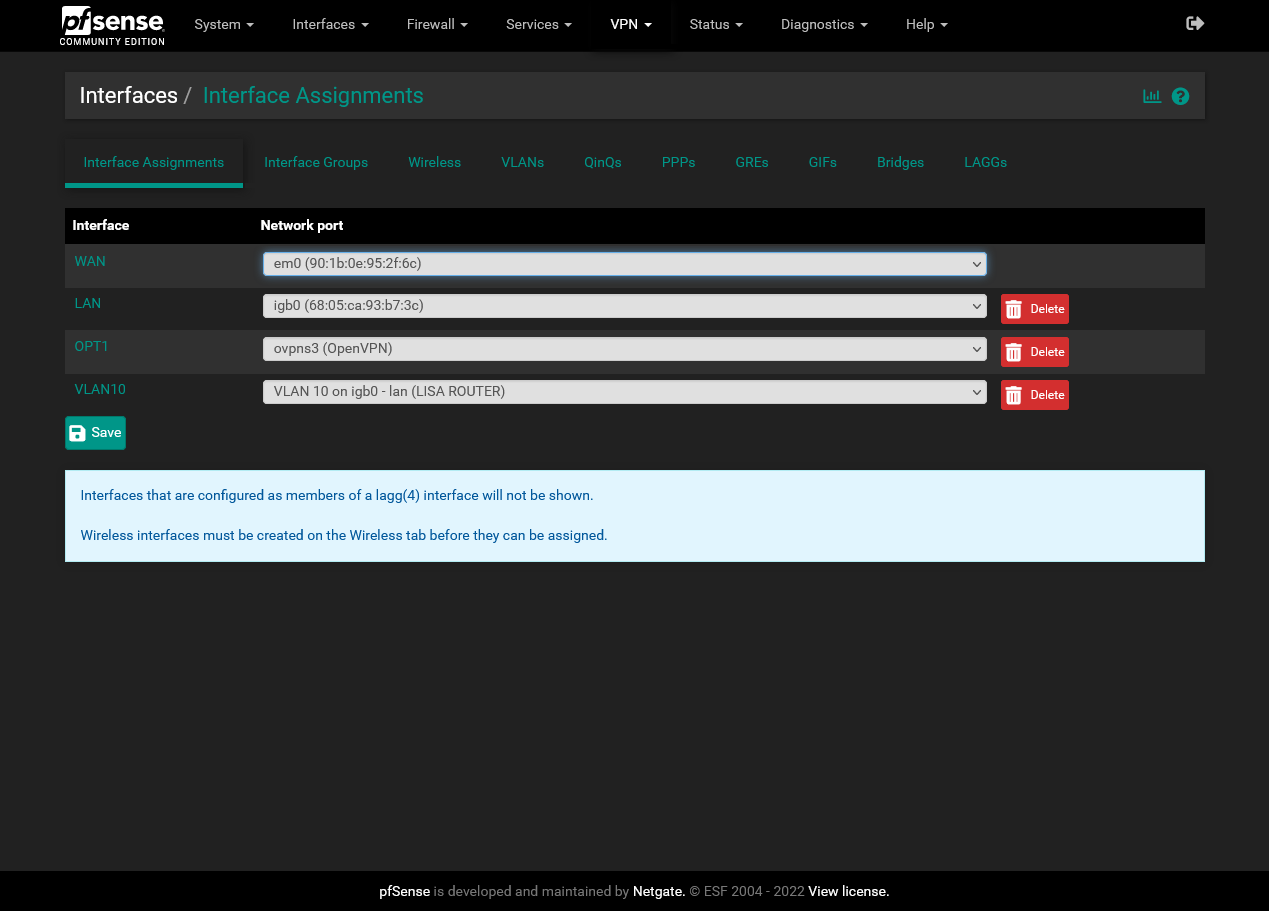
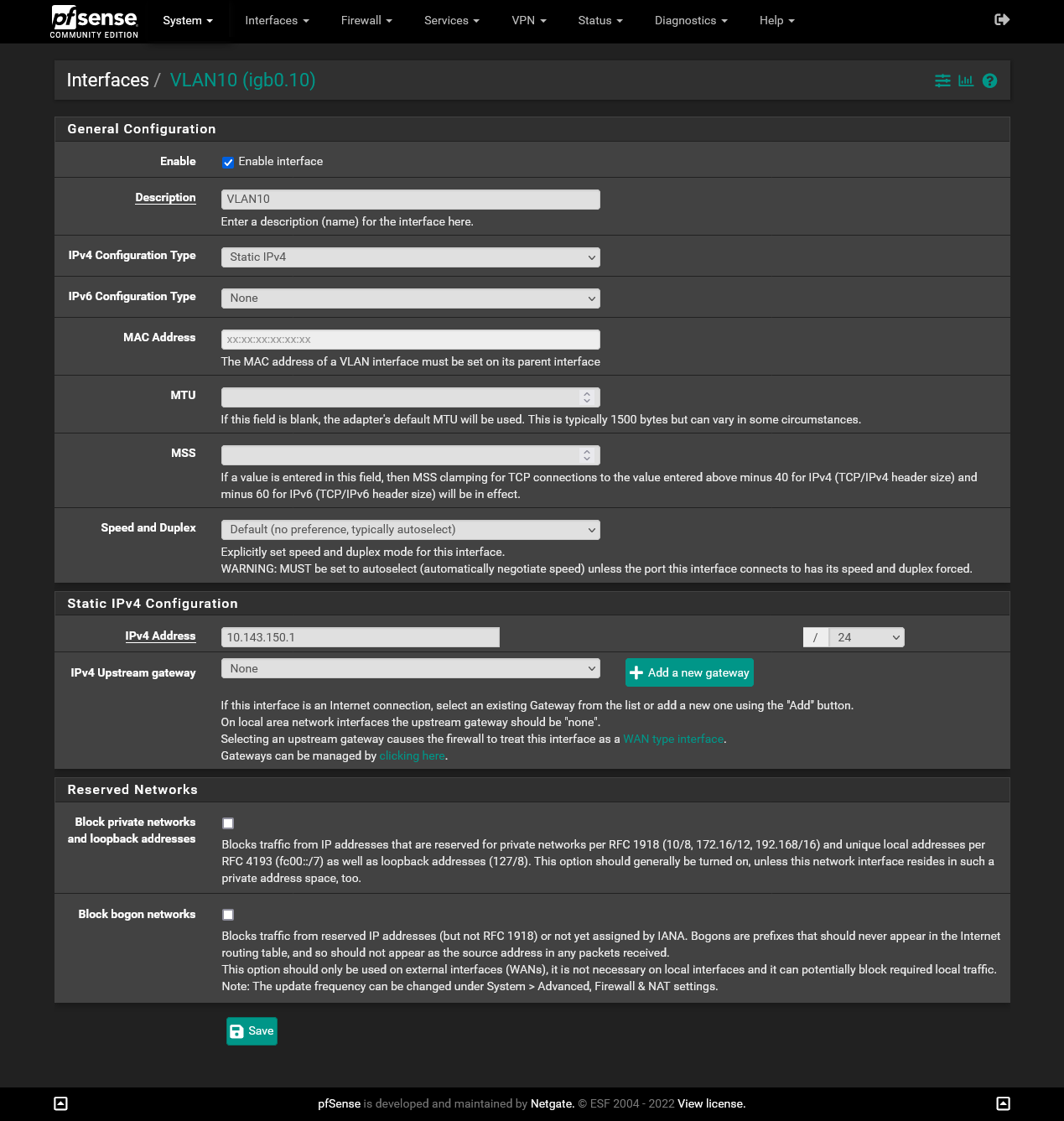
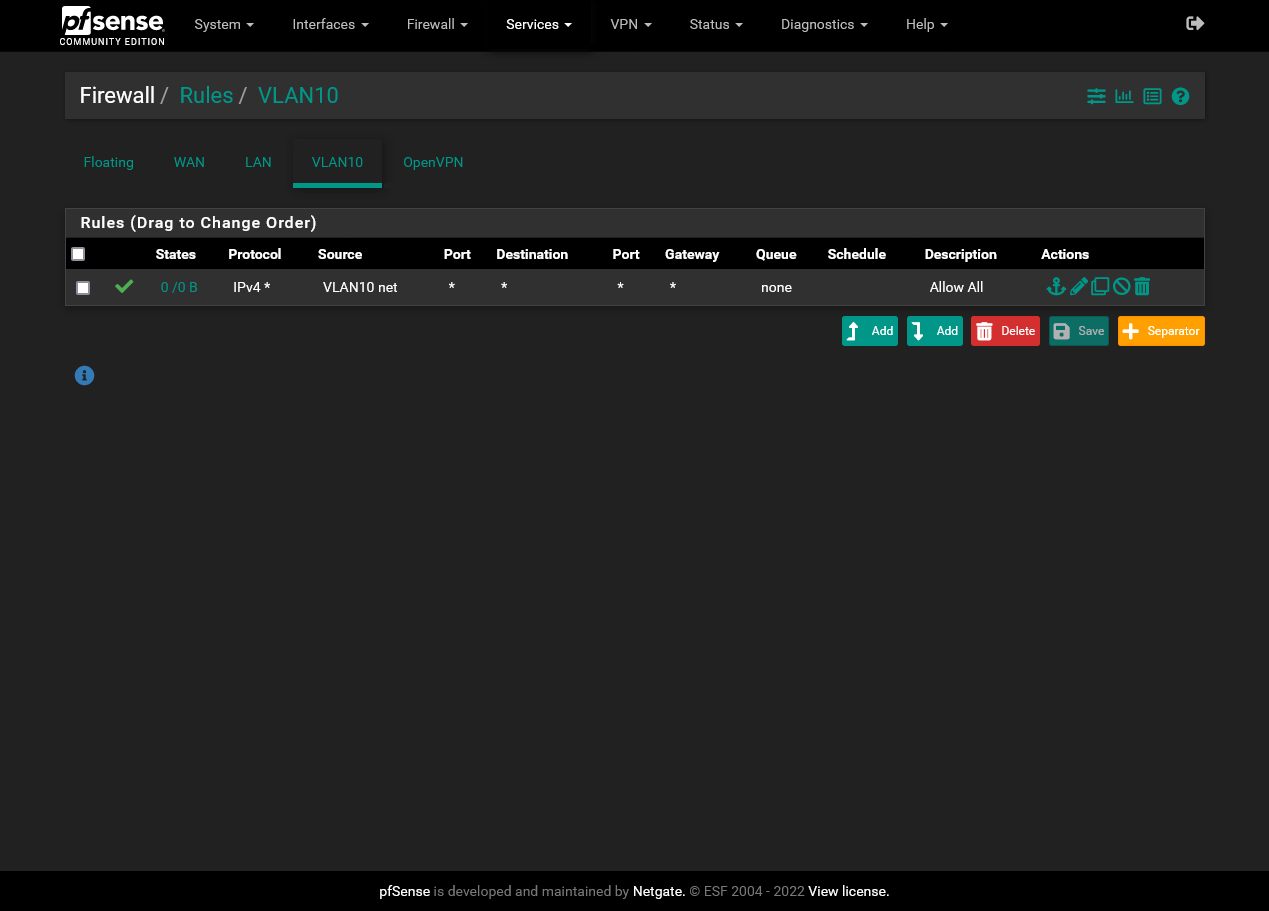
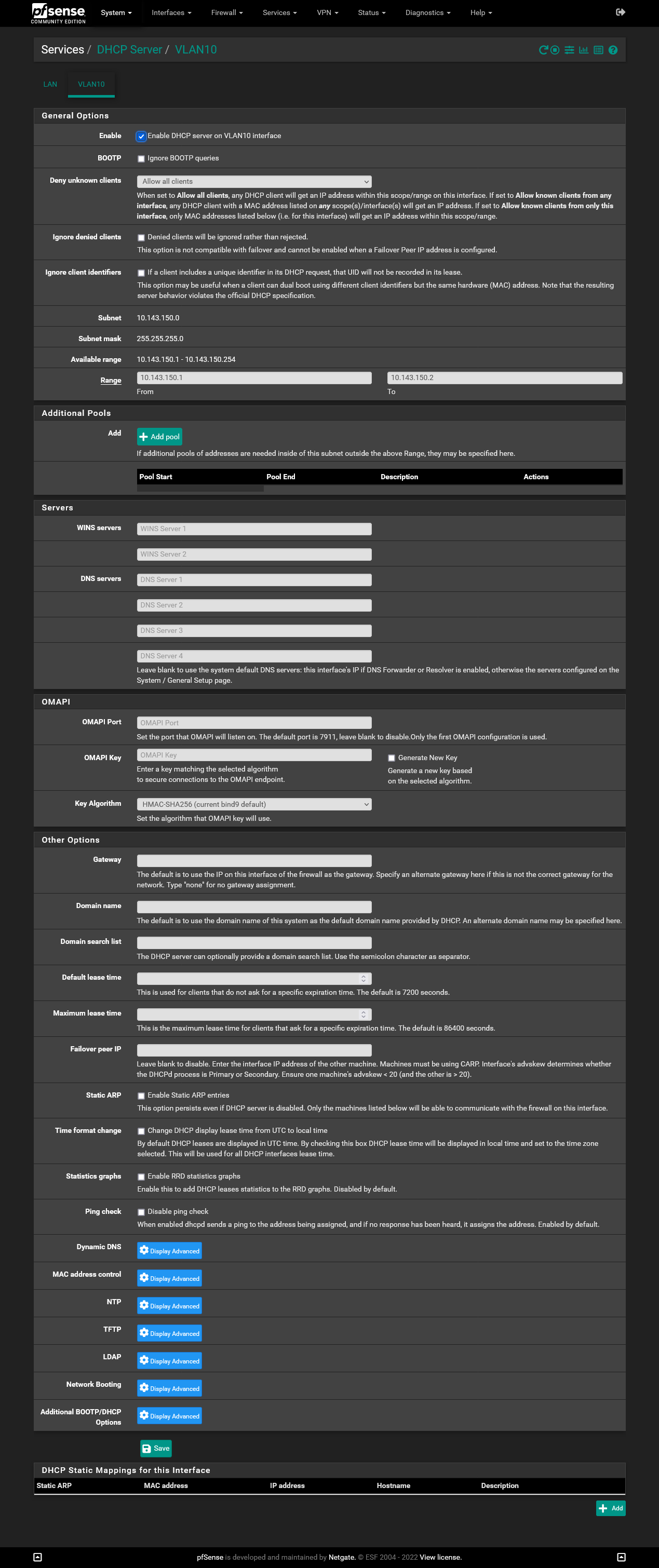
-
@mrglasspoole
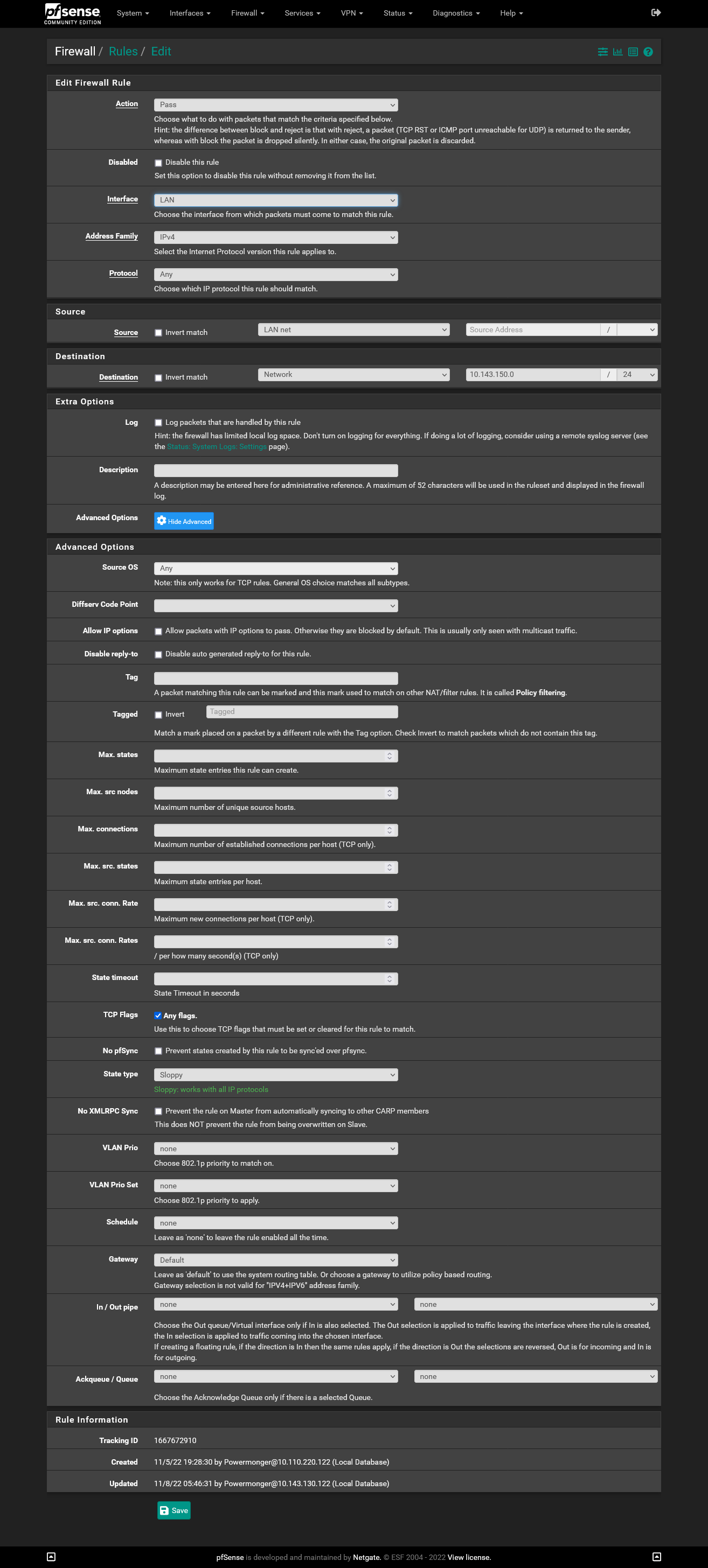
Since the network 10.143.150.0/24 is on the LAN of the GL.iNet Slate, you cannot assign it to the WAN side as well, which you connect to pfSense.
Take any other network.Also you include 10.143.150.1, which is the interface IP on pfSense, into the DHCP range.
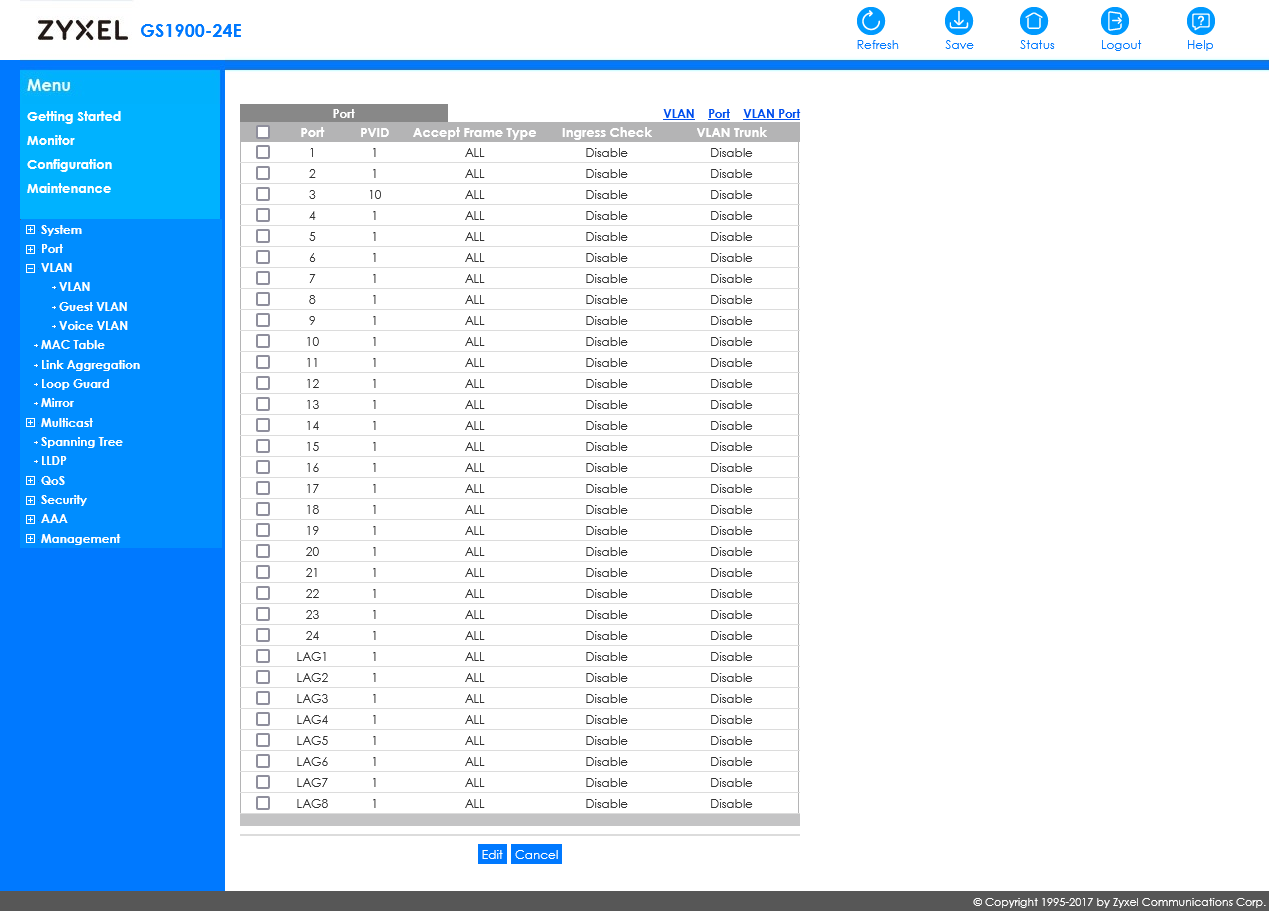
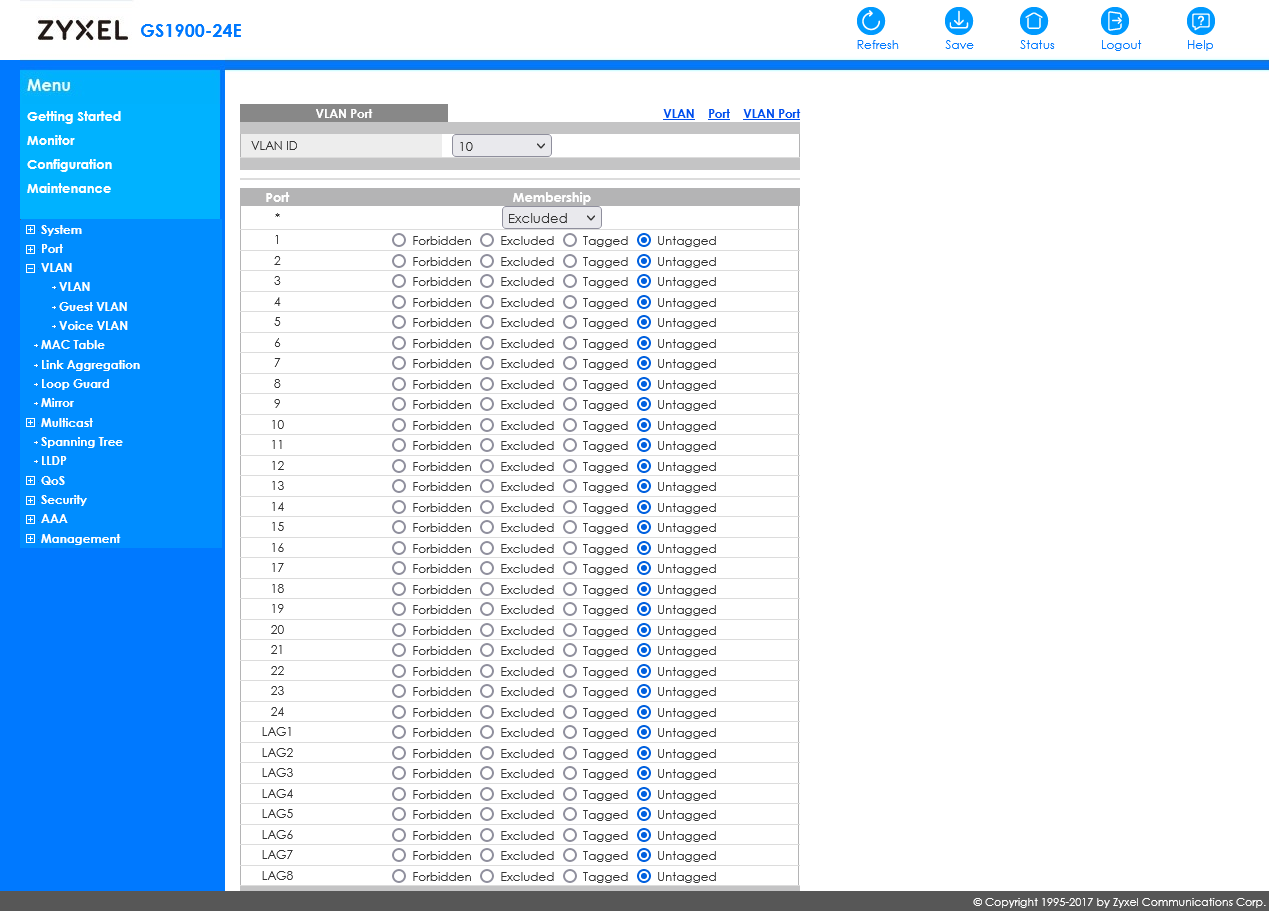
On the switch one port is connected to pfSense, which is the LAN. Let's say this is port 1.
Then, let's say on port 3, you connect the GL.iNet Slate.So both, 1 and 3 have to be assigned to VLAN10.
Port 1 as tagged, port 3 as untagged.
Additionally you need to set the PVID for port 3 to 10. -
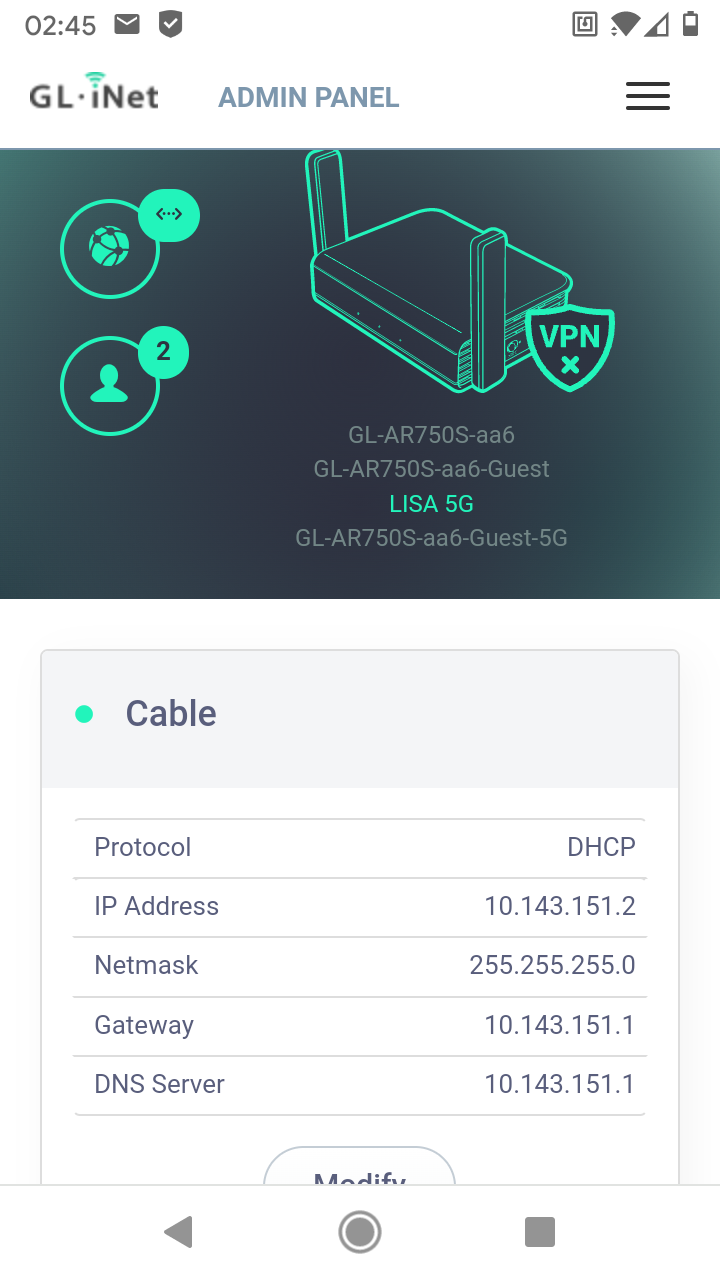
Ok the Slate is now getting the IP 10.143.151.2 on his WAN port.
Now I did set the VLAN IP to 10.143.151.1/24 and the VLAN DHCP Server to 10.143.151.1 - 10.143.151.5
But there is still something missing.
The devices on the Slate have no internet access.
And I can't ping 10.143.150.1 (Slate LAN) from my workstation.Is it right that the Slates WAN has 10.143.151.1 as Gateway and DNS Server? Or must it be 10.143.130.1 (pfSense)?
Is there something i need to to on the Slate? I guess not.
@viragomann said in Route from pfSense to GL.iNet Slate not working:
Also you include 10.143.150.1, which is the interface IP on pfSense, into the DHCP range.
Do you mean i did and its wrong or I have to?
-
@mrglasspoole said in Route from pfSense to GL.iNet Slate not working:
The devices on the Slate have no internet access.
What IP does the device have?
Does the Slate masquerading (NAT) on outbound traffic?
I guess, it should do this, since you also want to connect to the internet, when the Slate is connected to your phone, right?And I can't ping 10.143.150.1 (Slate LAN) from my workstation.
Does it allow access from outside of its subnet?
Is it right that the Slates WAN has 10.143.151.1 as Gateway and DNS Server? Or must it be 10.143.130.1 (pfSense)?
Yes, it uses pfSense for this.
But you need to allow access on pfSense. By default on a new interface nothing is allowed other as on LAN.
You need a firewall to allow internet traffic.Also you include 10.143.150.1, which is the interface IP on pfSense, into the DHCP range.
Do you mean i did and its wrong or I have to?
Again, .1 is the interface IP of pfSense, so it shouldn't be part of the DHCP range.
But obviously pfSense is smart enough to not hand out its own IP. -
What i did was setting "DNS servers" in the VLANs DNS server to pfSense (10.134.130.1).
Then the Slate WAN is:
IP....................: 10.143.151.1
Gateway......: 10.143.151.1
DNS Server: 10.134.130.1and internet on the Slate works.
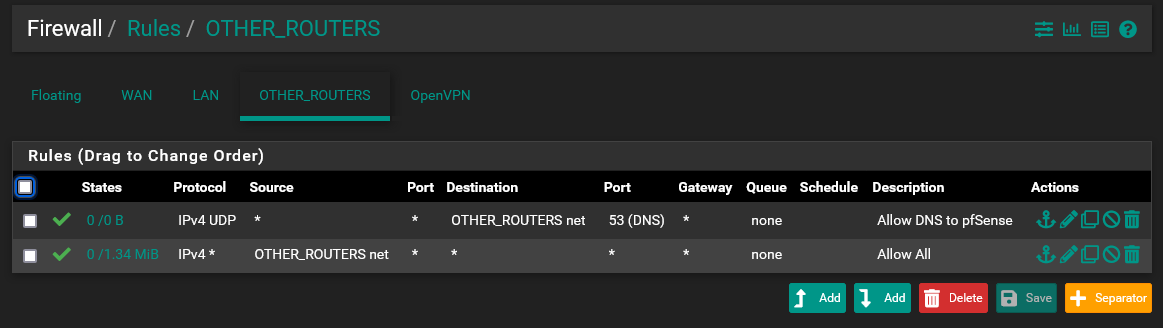
From your explanation I need a "Allow DNS to pfSense" rule and the "DNS servers" in the VLANs DNS server is not needed?
Where do i need it?
This does not work (no internet on the Slate):
-
@mrglasspoole
I suspect, you use the DNS Resolver on pfSense, which is enabled by default, but it isn't listening on the new interface IP.
You have to go into the Resolver settings and add the interface in the "Network Interfaces" box.The shown rules should allow both DNS server IPs, since your second allows any protocol to any destination from the subnet.
BTW: For DNS you should allow "TCP/UDP" rather the UDP only.
-
Funny
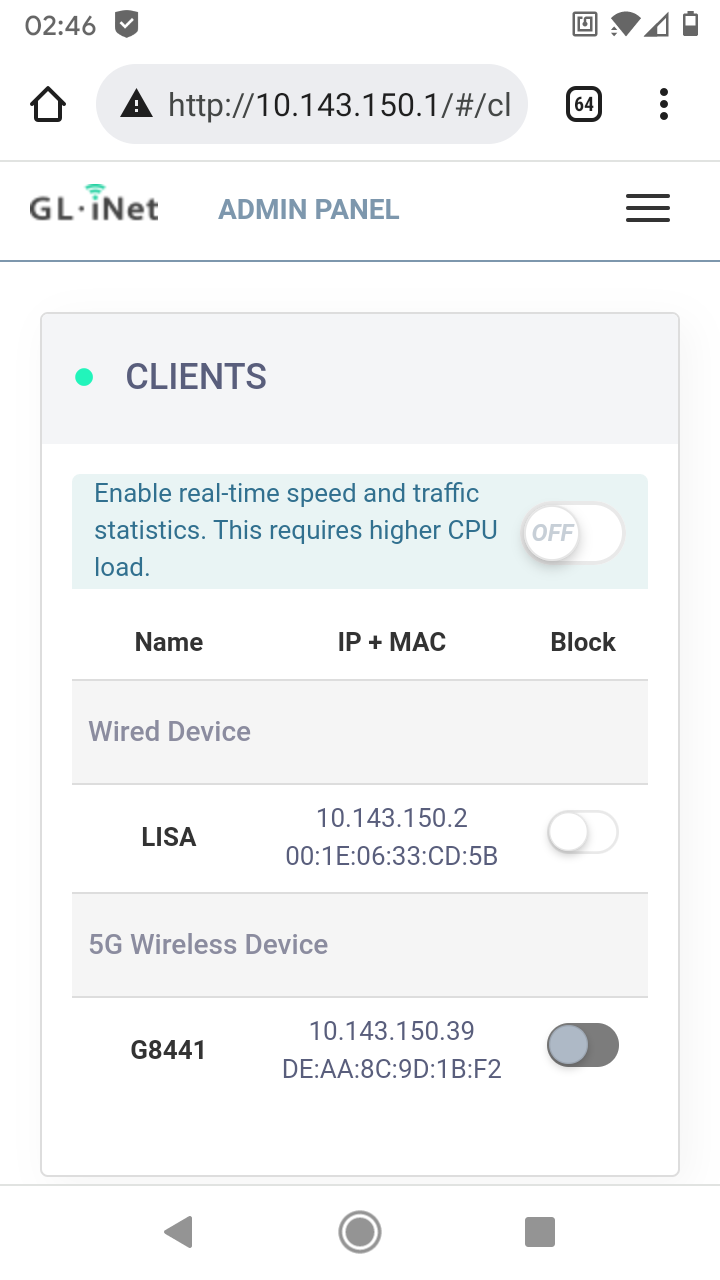
I can't reach the player behind the Slate from my workstation with the IP I did set (10.143.150.2).
But I can reach it with 10.143.151.2 ?Also I can't reach the admin panels of my APs anymore (R7800 & WNDR4300).
But I can reach the Gigaset behind the WNDR4300 and the APs are working.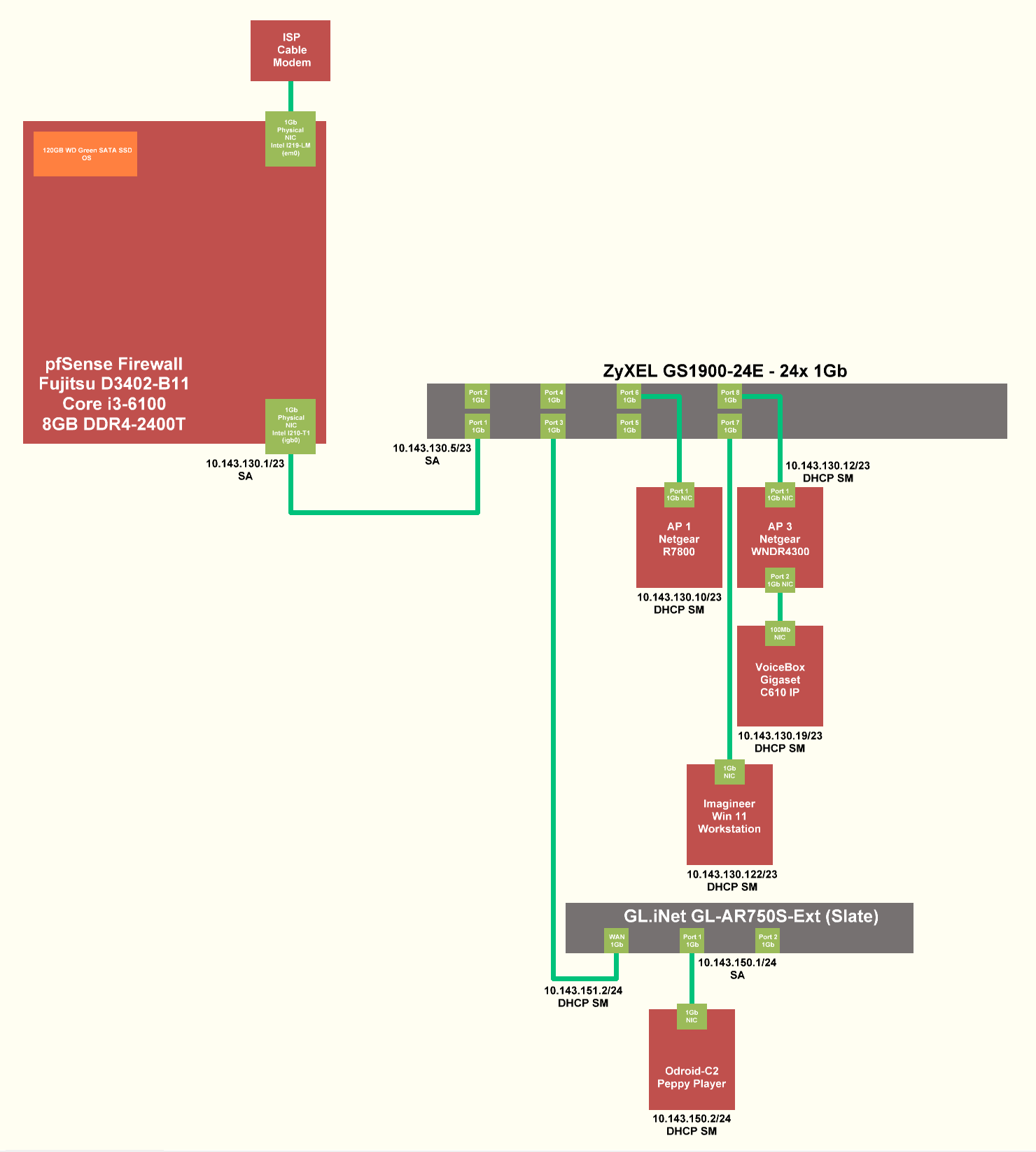
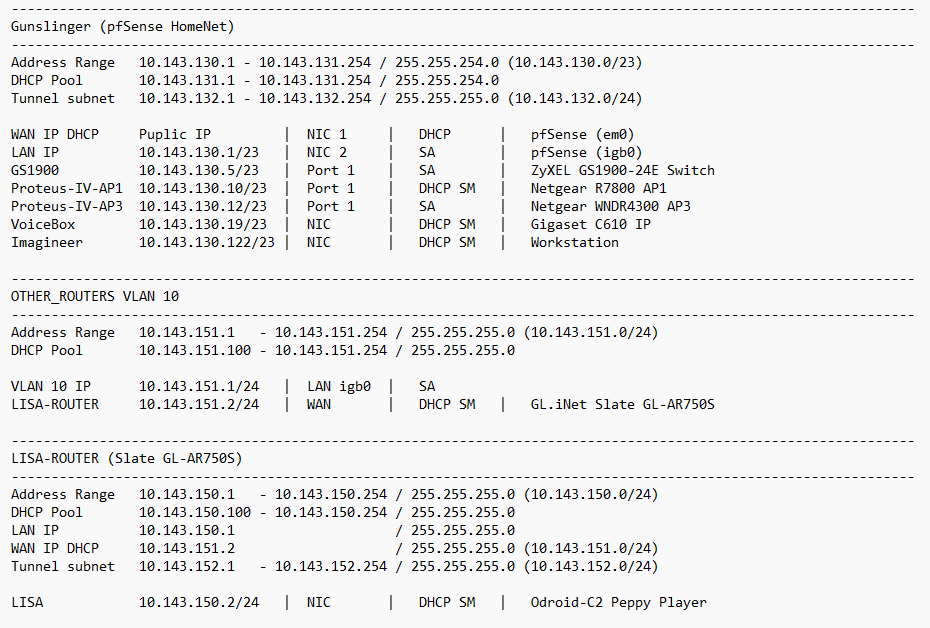
And this is the Slate:
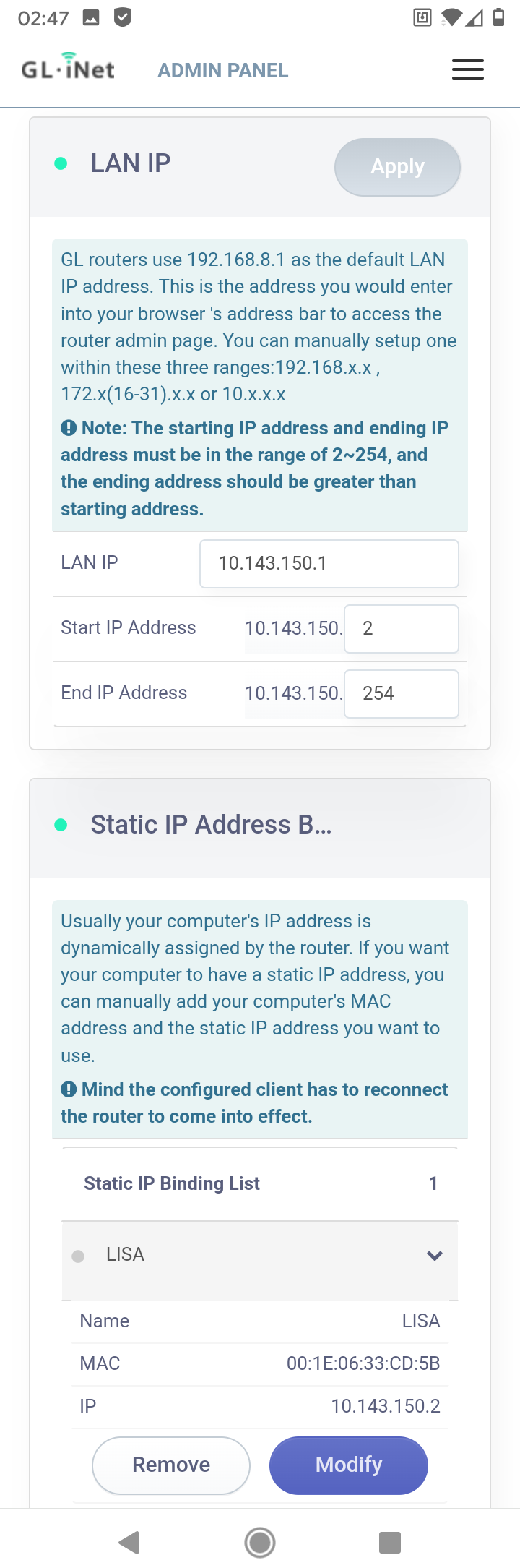
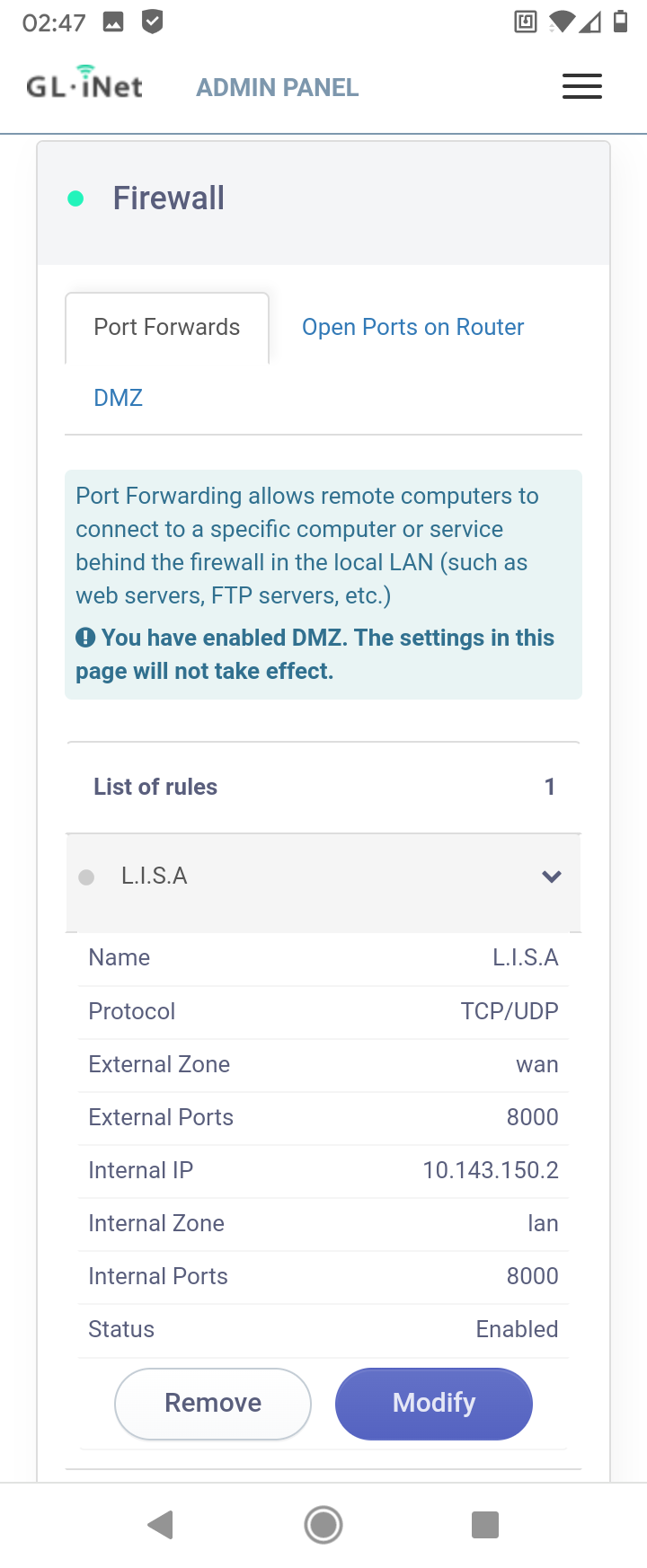
-
Can't figure it out.
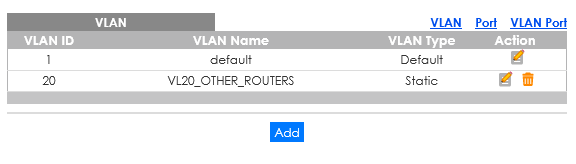
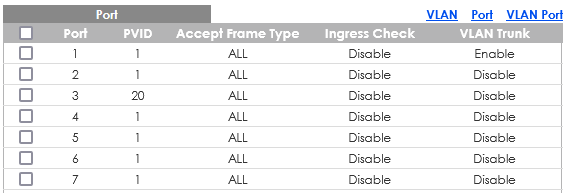
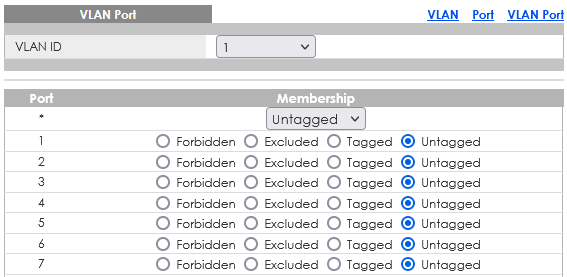
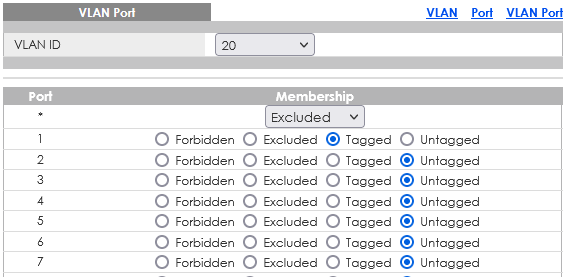
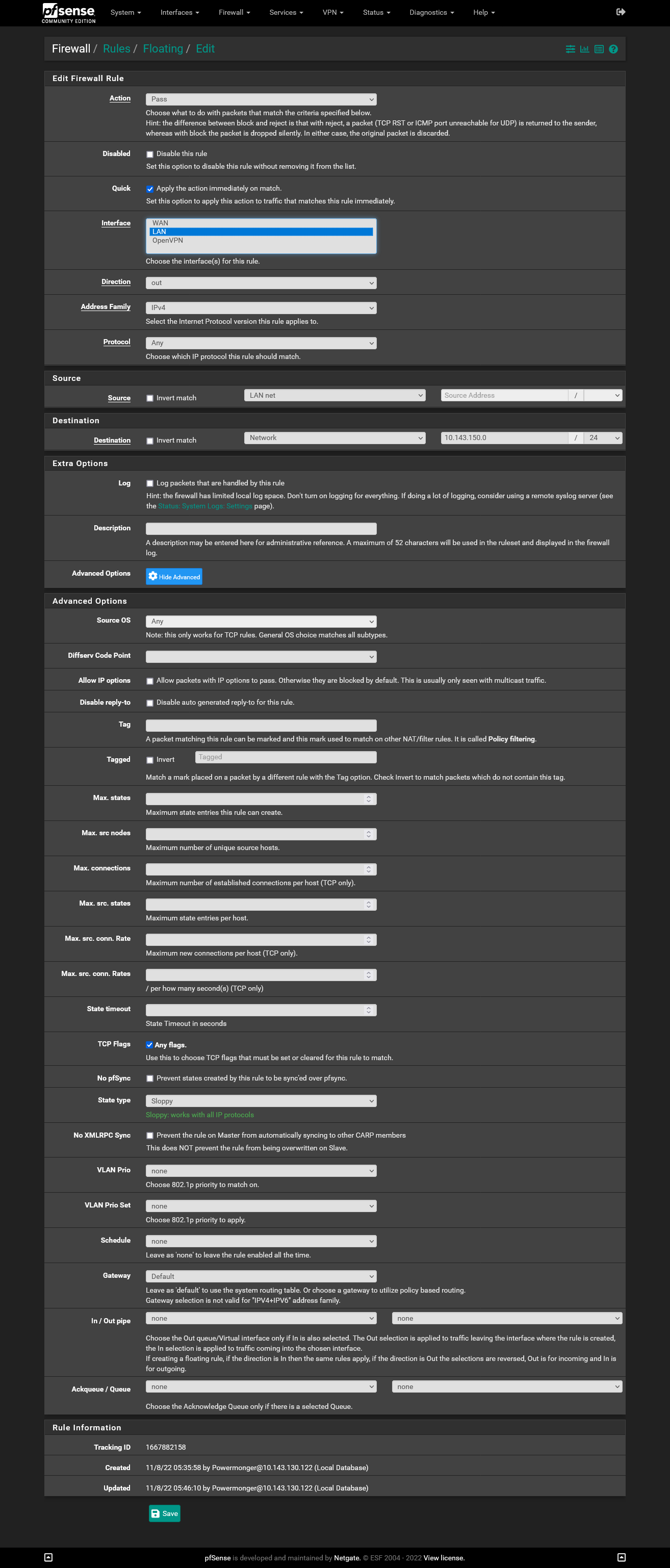
Since i believe what i need is called router-on-a-stick i made Port 1 to pfSense a trunk.
But no matter what i try in the switch settings i cant open the Slate GUI (10.145.130.1) or the Player (10.145.130.2) on my Workstation.
Port 1: pfSense
Port 3: Slate
Port 6: WorkstationWhat is the correct setting: