Route VPN traffic to other VLAN
-
Hi there,
I have an OpenVPN server running successfully but would like to keep this traffic out of my network as much as possible and only make a specific port accessible on a server.
There are multiple VLANs set up and they have different IP address ranges. Until now, if I absolutely wanted to allow a certain connection between the networks, I did this via a firewall rule with specification of the IP and the port.
In the OpenVPN settings of the server there is the parameter "Local IPv4 networks" to make a local network, or an IP range accessible via the VPN connection.
I could now specify the server directly with 192.168.10.10/32 to make only this accessible.
However, my goal is to enable access only to this particular port, not all open ports under this IP address. Also, in the future, I would like to possibly make other ports, or even other IPs accessible from the Internet.I don't quite understand how I can solve this via a firewall rule.
This is my setup:
WAN (allow openVPN is setup here)
VLAN A (10.0.1.0/24)
VLAN B (192.168.10.0/24)
VLAN C (192.168.20.0/24)
OpenVPN (tunnel 10.0.8.0/24)When I set up a firewall rule in OpenVPN and allow connection to 192.168.10.10:1234 it doesn't seem to work. However, if I instead specify 192.168.10.10/32 in the server settings of OpenVPN under locally attached networks, I get to the server.
I assume that all clients connecting via VPN get an internal IP address from the tunnel network (10.0.8.0/24). Therefore I don't understand how I can make it so that the client can also get to the IP 192.168.10.10:1234. I would have expected this to be set up in the Firewall Rules under OpenVPN.
Can you please enlighten me here and put me on the right track?
Thanks a lot
Newbow -
@newbow
No, OpenVPN does not permit or block any access. This has to be done by firewall rules.The "local networks" box give you the ability to push routes to the clients. So yes, you need to enter the networks here, which the client should be able to access, because this instructs the client to add routes for theses networks.
You can specify a single IP with a /32 mask (the entries must be in CIDR notation).But consider, that this is no security option. The client can route to the VPN server whatever he want on his own, apart from the pushed routes.
So you have to state firewall rules to allow access to your resources at all.
If you ran through the wizard, it has added a rule to the OpenVPN tab to allow any. If your want to restrict access you have to delete / modify this rule.The clients get any virtual IP out of the tunnel network.
If you need to permit a specific client to access specific resources, you have to add client specific overrides (CSO) therefor. -
@viragomann
thank you very much for the answer.If I understood you correctly, under OpenVPN I need to adjust the Autmatically generated rule under "Allow all rule" to allow only one one connection? As for example like this:

I enter all networks in the OpenVPN server under local networks
10.0.1.0/24, 192.168.10.0/24, 192.168.20.0/24
and then restrict this access by rule?
So in the above example rule I would get access only to the single IP 192.168.10.10:1234 not to the other networks (10.0.1.0/24, 192.168.10.0/24, 192.168.20.0/24)?EDIT:
Okay, that seems to be the right way. It now works as intended. I can unblock individual IP addresses and ports, otherwise everything is blocked if there is no rule for it.The only thing I don't quite understand is the separate column for the interface. It would be nice if someone could enlighten me.
I don't understand the description in the manual. What is the use of connecting the interface?
/EDITWhat is not quite clear to me, if I set up under the interfaces the VPN connection appears a new column with VPN. Why are there then two places where I set up the rules for VPN? What are the differences?
Okay I get that the client get's a tunnel IP address in the range 10.0.8.0/24 but were do I set up the rules in the VPN (Interface) or the OpenVPN (OpenVPN incomming traffic?). If no rule is setup the incoming traffic would not get through even tho the networks are entered in the local networks section of the OpenVPN?
Sorry, have mercy this is kind of confusing to me at the moment.
Thanks
Newbow -
@newbow said in Route VPN traffic to other VLAN:
So in the above example rule I would get access only to the single IP 192.168.10.10:1234 not to the other networks (10.0.1.0/24, 192.168.10.0/24, 192.168.20.0/24)?
Yes. But there is no need to push routes to networks, which you don't allow access. So if you only permit access to this hos it's sufficient to enter 192.168.10.10/32 into local networks.
Consider that if you provide a local DNS server to the client, you have also allow access to it.
The only thing I don't quite understand is the separate column for the interface. It would be nice if someone could enlighten me.
I don't understand the description in the manual. What is the use of connecting the interface?There is no need to assign an interface to an access server, but can be done.
The OpenVPN tab is an implicitly added interface group. It appears if you run any OpenVPN instances (server or client) on pfSense and includes all.
Consider that rule on an interface group (OpenVPN tab) are probed before interfaces rules. So if a rule matches to a traffic, it will be applied and interface rules will be ignored then. -
@viragomann said in Route VPN traffic to other VLAN:
Consider that rule on an interface group (OpenVPN tab) are probed before interfaces rules. So if a rule matches to a traffic, it will be applied and interface rules will be ignored then.
one question: for example this default route on OpenVPN tab
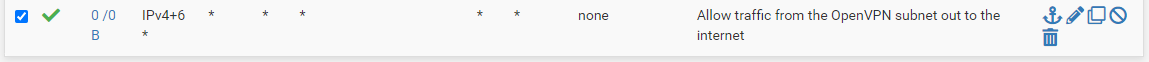 will "override" all interface rules (for example a rule on LAN " allow special-ip:port from tunnel to lan-ip:port)? or does it mean "overrides" all interface rules for interfaces in the "OpenVPN tab implicitly added interface group"? where can i see the members of the "OpenVPN group"? under interface groups are no groups available.
will "override" all interface rules (for example a rule on LAN " allow special-ip:port from tunnel to lan-ip:port)? or does it mean "overrides" all interface rules for interfaces in the "OpenVPN tab implicitly added interface group"? where can i see the members of the "OpenVPN group"? under interface groups are no groups available.thx christian
-
@chris1284 said in Route VPN traffic to other VLAN:
for example this default route on OpenVPN tab
That is not a route but a firewall rule. It is applied to every OpenVPN Connection. So every OpenVPN Connection is allowed to go everywhere in your network.
-
@chris1284
No not all rules on all interface, but only interfaces which are included in the OpenVPN group. The group only includes OpenVPN instances, you cannot modify it.
Rules on an interface group even on OpenVPN tab have prio over rules on the OpenVPN instances.
You should consider this, when you have rules on this tab.