OpenVPN Behind NAT ISP Router
-
@viragomann Yes my router have Static IP address assigned from ISP.
When I check the rules from nmap on the firewall I can see traffic passing. But when I check it outside, no traffic pass through it as per the WAN rule status.
-
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
I have configured my ISP router to forward UDP on port (1194) traffic into Pfsense WAN interface 192.168.100.1/30. and created the required WAN rules to allow UDP traffic on UDP port 1194 but still am not able to get OpenVPN to work.
My OpenVPN WAN 'pass' firewall rule :
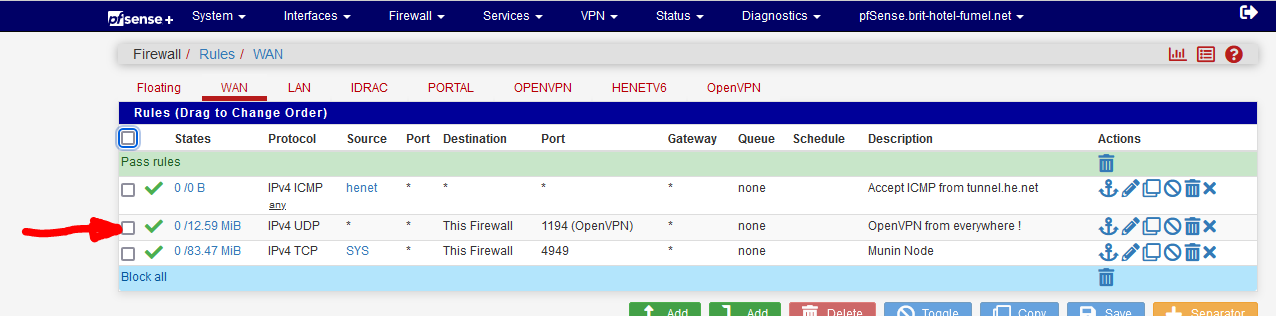
You see the counter (called States) in front of the rule ?
These show that the rules is 'used' == traffic comes in on my WAN IP, port 1194, UDP.If you see the same, you know that the traffic will 'hit' that port on pfSense, and the OpenVPN process is listening on that port.
Want to test if OpenVPN is really listening ?
[22.05-RELEASE][admin@pfSense.local.net]/root: sockstat | grep '1194' root openvpn 41927 7 udp4 192.168.10.5:1194 *:*So, yes, my openvpn is listening on IP 192.168.10.5, that is my WAN interface IP, port 1194, protocol UDP.
Btw : as you, I had to 'NAT' also any upstream routers == my ISP router.
Something like :
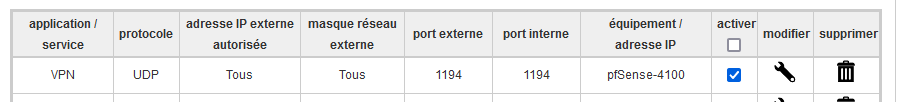
pfSense-4100 is a name for my pfSense WAN IP, 192.168.10.5
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
I have an ISP router with IP address of: 192.168.100.2/30 and my Pfsense WAN interface IP address is: 192.168.100.1/30.
This is .... strange.
Your ISP router has a LAN IP 192.168.100.2 ??
It should/would be 192.168.100.1 or, why not 192.168.100.254
"2" is strange here.
The net mask of /30 is also ... not common.My question is : you changed things. That's ok. But what did you change that you didn't mention that breaks things ?
My ISP router used to use the default 192.168.1.1/24, but as my pfSense also uses that network on one of its LAN interface, I had too (chose to) change the network of my ISP router, as you probably did.
I used 192.168.10.1/24 (because : why not) - and my pfSense uses DHCP (== the easy mode) obtain .... 192.168.10.5 as it's WAN IP, handed over by the DHCP server on my ISP router.@fadhel-ce said in OpenVPN Behind NAT ISP Router:
I have tested WireGuard and also am not able to get it work.
Wireguard is another animal.
I never used it so, but I do member it doesn't need a firewall rule at all to work, as it only initiates outbound traffic.
I might be wrong here. -
@gertjan I Have the same configuration but still it's not working. Without Pfsense from the ISP to local network port forwarding is working fine.
Below my ISP port portwading:
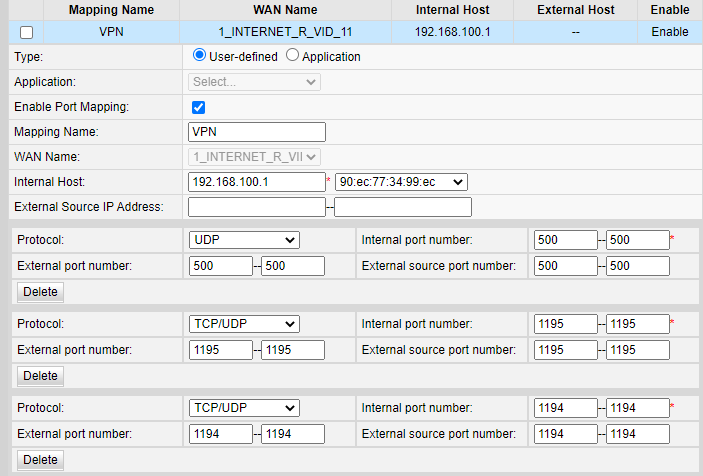
This my WAN rule:
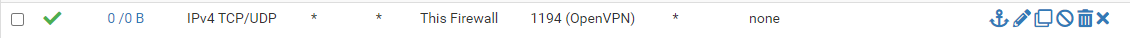
Still am not able to get it work I don't know what am missing or misconfiguring.
-
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
Without Pfsense from the ISP to local network port forwarding is working fine.
Cannot believer that.
You must not state external source port numbers! They are dynamic and hence can be any, but would never be what you state.
-
@viragomann I was using Fortinet FW with same ports forwarded and I have no issues. Does I need to change anything in NAT settings for for port-forwarding to work ?
-
@fadhel-ce
What's about what I wrote above?If you state source ports in the NAT rules the connection won't work at all, neither on Fortinet.
-
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
I was using Fortinet FW with same ports forwarded and I have no issues.
So, you confirm that :
If you use the Fortinet device as your router behind your USP router
and
Your Fortinet router has an IP WAN 192.168.100.1 (like pfSense now)
and
You change the 90:ec:xx:yy:ec for the Fortinet MAC (so, you change just one setting in your ISP router !)
then
The VPN server in Fortinet receives VPN traffic.I'm with @viragomann, I find that hard to believe.
You've set the external source port number.The VPN client, running on a device somewhere on the Internet uses your WAN (from the ISP router !) as a destination address.
Uses 500 or 1194 or 1195 as a destination port.
Uses UDP (or TCP ?) as a protocol.But it will use a random*** source port.
** Are you really binding your VPN client to a fixed source port, 500, 1194, 1195 ?*
-
@gertjan said in OpenVPN Behind NAT ISP Router:
Your Fortinet router has an IP WAN 192.168.100.1 (like pfSense now)
and
You change the 90:ec:xx:yy:ec for the Fortinet MAC (so, you change just one setting in your ISP router !)
then
The VPN server in Fortinet receives VPN traffic.I was using Fortinet FW and I don't have any issues. In fact am trying for replace Fortinet FW with Netgate. Fortinet VPN was working find with no issues.
I just replace Fortinet with Netgate and assign same IP for it. I just add new port-forwarding rules for UDP 1194/1195 for OpenVPN but seams it's not working. The rules status does not change, the strange thing is that if I use NMAP tool to test our public IP, the status changed. Am still not able to figure out how to solve this issue.
Thanks for all your helps
-
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
I was using Fortinet FW and I don't have any issues.
If Fortinet worked with the settings yo showed above then the traffic was successfully NATted trough your ISP router
That is, have/had to change the MAC on the NAT settings on your ISP router, as the pfSense WAN MAC is different as the Fortinet WAN MAC.That's all there is to do.
Now, goto here :
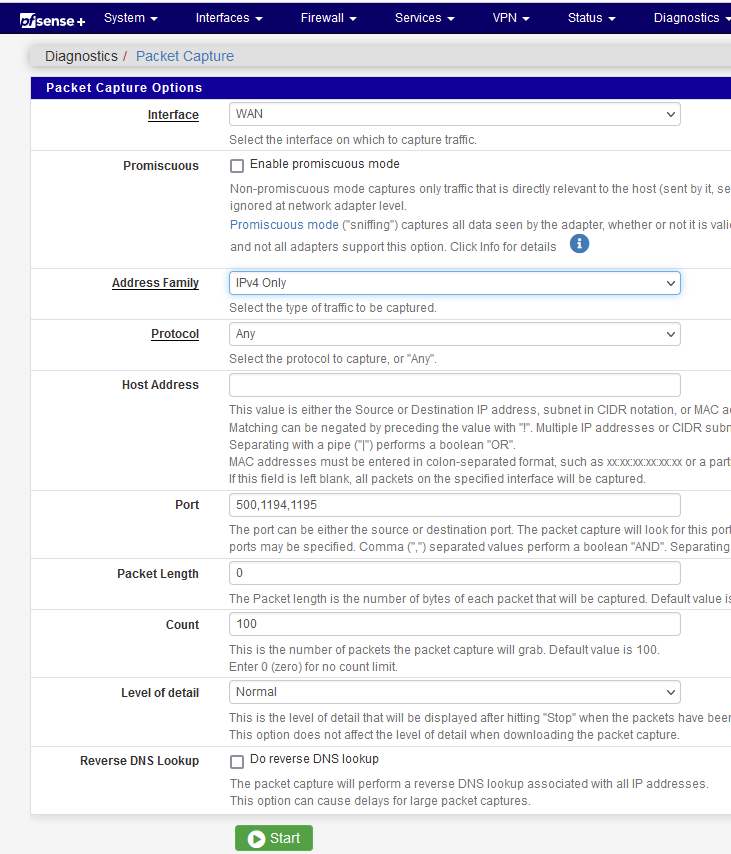
Your input :
Set the WAN interface.
Set "500,1194,1195" as port.And hit the green start button.
Now, use a VPN client "somewhere on the Internet - for example your phone with the help of a VPN app, and with Wifi de activated) , and connect to your pfSense VPN.
Wait some seconds.Hit the Orange stop button on pfSense = stop capturing.
If there are packets shown, check if they came from your phone = the source IP was your phone.
If there are, traffic reaches the pfSense WAN interface.
If not, traffic doesn't reach pfSense (and your issue is not pfSense related). -
@gertjan said in OpenVPN Behind NAT ISP Router:
If there are, traffic reaches the pfSense WAN interface.
If not, traffic doesn't reach pfSense (and your issue is not pfSense related).Many thanks for you help. However, still am not able to find the issue. I tried what said and I found the below:
- When I try access from a network outside my local network no traffic reach the WAN interface.
- When I try using public IP inside my network it work fine with no issues.
- I removed my port-forwarding rules and try through the public IP inside my network. It did not work which means port-forwarding is working and correct. But, why outside network traffic not reaching WAN interface I don't know!!
- I tried allowing all traffic though the WAN interface and still it does not work!
-
@fadhel-ce said in OpenVPN Behind NAT ISP Router:
When I try access from a network outside my local network no traffic reach the WAN interface.
Did you the packets capture on WAN as requested?
If you see nothing there the router doesn't forward the traffic properly.
Don't set any filter to ensure you see all traffic arriving on WAN!Did you update the MAC in the port mapping to that one of pfSense WAN interface?
-
@viragomann said in OpenVPN Behind NAT ISP Router:
Did you the packets capture on WAN as requested?
If you see nothing there the router doesn't forward the traffic properly.
Don't set any filter to ensure you see all traffic arriving on WAN!
Did you update the MAC in the port mapping to that one of pfSense WAN interface?Yes, I did on the WAN Interface.
I see traffic only when I try from local network using the public IP. If I delete the port-forwarding I see nothing even if I try from the local network using the public IP.
I didn't set any Block rules on the WAN Interface to test it.
The first step I did is to update the MAC address in the port-forwarding on ISP router.