pfBlockerNG-devel Not Blocking Malvertizing on LAN
-
Hello...I have pfBlockerNG-devel configured to block/reject malvertizing on all of my interfaces - WAN, LAN, WLAN. Interestingly, when I check emails using my iPhone on my WLAN there is missing images, etc., however, when I check my emails using my desktop computer connected to my LAN, I see everything in the emails. Here are my settings -
Any ideas why there is a difference between what I see checking emails on my LAN versus checking emails on my WLAN? Thanks.
-
@newuser2pfsense Are you using a browser that uses DoH? That would bypass any DNS server.
-
@steveits I checked my Firefox Network Settings and the default was set to "Use system proxy settings." I changed this setting to "No proxy" and this seems to have worked. Thanks.
-
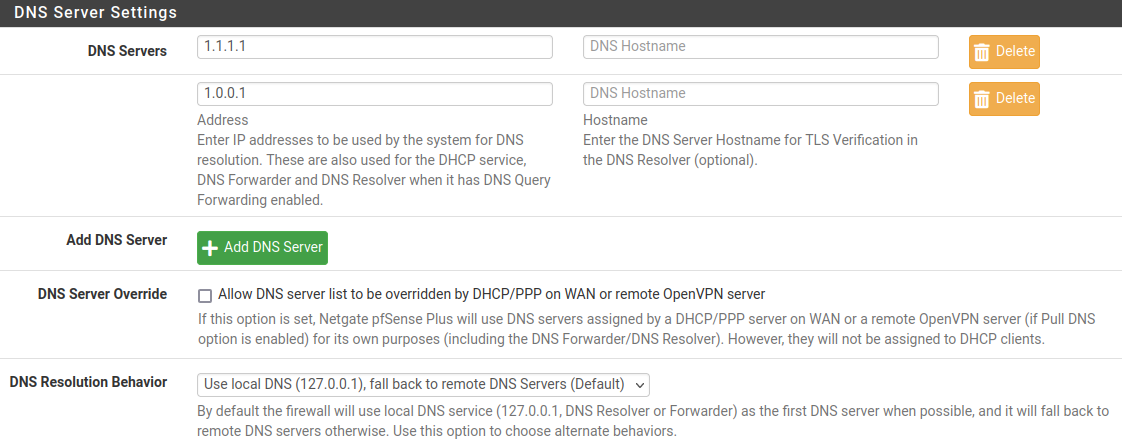
Under pfBlockerNG>DNSBL>DNSBL SafeSearch
Here you can Enable Block DoH and DoT, so that the User is forced to use the System DNS. This works for us pretty good.
-
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
I checked my Firefox Network Settings and the default was set to "Use system proxy settings.
That's just one step to check.
But it could inform you that traffic generated to show web pages uses the system settings.
DNS could be handled differently.And then there is your "system", the PC.
Open a cmd windows, and type nslookup.
On the second line, it should show the DNS server being used by your PC.
Typically, this is 192.168.1.1 (or the IPv6 of your pfSense LAN).Test also like this : visit a web site you have never visited before : example : www.knmi.nl
Now have a look at the pfBlockerng-devel DNS Reply page, and look (serach, Ctrl-F) for the word "knmi" : it should be there.
This is a solid proof that pfBlockerNG-devel handles your DNS request.You should also see the host names of the sites that gave you the images in the spam mails.
If these host names do not show up on the Unified or Alerts page, this means the host names used were not found in any of the lists/dns feeeds.
-
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
@steveits I checked my Firefox Network Settings and the default was set to "Use system proxy settings." I changed this setting to "No proxy" and this seems to have worked. Thanks.
Scroll further down to see the DNS option...
-
@OpIT-GmbH DoH/DoT Blocking is enabled and I've chosen every entry in the list; probably a little overboard but what the heck.
@Bob-Dig The "Enable DNS over HTTPS" in the Firefox browser is not checkmarked.
@Gertjan www.knmi.nl was found in the DNS Reply page and the Unified page. In my Linux terminal, when I typed nslookup and hit enter, the next line only showed a > symbol.
-
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
In my Linux terminal, when I typed nslookup and hit enter, the next line only showed a > symbol.
If you just run "nslookup" it runs the program and acts like its own shell. Run "nslookup google.com" or some other hostname to do a lookup and exit.
-
Did you also add a Portforward Rule to force all DNS (Port 53) Triffic to pfSense
-
@steveits said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
If you just run "nslookup" it runs the program and acts
Add to that, when you run nslookup without parameters, it shows the DNS 'source' to be used.
And it it will wait with its own command line '>' so you can enter (example) knmi.nl.C:\Users\gwkro>nslookup Serveur par défaut : pfSense.local.net Address: 192.168.1.1 >So, for me, 192.168.1.1 is where every LAN device 'should' (could) addresses itself for DNS requests.
192.168.1.1 is of course my pfSense.Type
helpor
set allto see more info.
-
I'd like to start by saying that I'm NO network guru, so please allow a little Grace for the following -
With an nslookup with no options, I get the following:

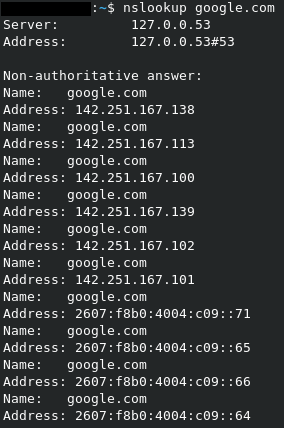
With an nslookup for the google, I get the following:
With an nslookup for pfSense.local.net, I get the following:
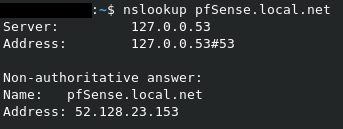
I'm not sure if this means anything to anyone. Not sure why I got a 52. address which is nowhere near what my WAN IP address is.
-
Now it seems like no matter what settings I choose in Firefox, what my WLAN iPhone does not display in emails, my LAN desktop does.
-
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
With an nslookup for pfSense.local.net, I get the following:
Image
I'm not sure if this means anything to anyone. Not sure why I got a 52. address which is nowhere near what my WAN IP address is.
Euh ..... pfSense.local.net was an example.
You should use your pfsense host name, and the network.pfSense.local.net points to 52.128.23.153, that's ok.
-
@gertjan Ok. Tried with my pfSense host name and received the following:
Server: 127.0.0.53
Address: 127.0.0.53#53Non-authoritative answer:
Address: 192.168.1.1 -
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
127.0.0.53
What is this IP? Usually anything 127.x.x.x is "localhost" or "myself" indicating your computer is asking itself. Especially if 192.168.1.1 is your pfSense LAN IP. Double check what DNS servers are configured on your computer, and only set 192.168.1.1.
-
@steveits said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
What is this IP?
Dono.
It sad : non-authoritative answer: so not pfSense.
@newUser2pfSense You should know on what system you are running the nslookup command (right ?) :
[22.05-RELEASE][admin@pfSense.whatever.net]/root: nslookup > pfsense Server: 127.0.0.1 Address: 127.0.0.1#53 Name: pfsense.whatever.net Address: 192.168.1.1 Name: pfsense.whatever.net Address: 2001:470:dead:beef:2::1 -
-
@newuser2pfsense said in pfBlockerNG-devel Not Blocking Malvertizing on LAN:
I have always set 192.168.1.1 for all of my LAN computers DNS servers
nslookup (and therefore your PC) doesn't seem to be using that...? Try giving it a specific server:
nslookup google.com 192.168.1.1
-
@steveits Here is the output to nslookup google.com 192.168.1.1
nslookup google.com 192.168.1.1
Server: 192.168.1.1
Address: 192.168.1.1#53Non-authoritative answer:
Name: google.com
Address: 172.253.122.138
Name: google.com
Address: 172.253.122.102
Name: google.com
Address: 172.253.122.139
Name: google.com
Address: 172.253.122.101
Name: google.com
Address: 172.253.122.113
Name: google.com
Address: 172.253.122.100
Name: google.com
Address: 2607:f8b0:4004:c1b::8b
Name: google.com
Address: 2607:f8b0:4004:c1b::8a
Name: google.com
Address: 2607:f8b0:4004:c1b::71
Name: google.com
Address: 2607:f8b0:4004:c1b::65 -
@newuser2pfsense OK. And if you try a hostname you think should be blocked what do you get?
So far what we seem to have established is your test computer is using 127.0.0.53 for its DNS not the pfSense. Perhaps some sort of VPN or security software? Whatever it is, it is likely not using the pfSense DNS Resolver and hence you are not seeing sites be blocked.