How to customize the block page message of pfBlockerNG
-
@s-hasan-0 said in How to customize the block page message of pfBlockerNG:
@bmeeks thank you for your satisfactory clarification about HTTPS over SSL, but this is not what I am looking for. what I want to achieve is to redirect the users to a custom block page and I am sure that can be done in Pfsense, but I don't know how, as I am new at this.
the below documentation will demonstrate my point better:
https://docs.umbrella.com/umbrella-user-guide/docs/redirect-to-a-custom-block-page#thank you
Cisco's Umbrella cloud product uses a cloud-based proxy server to accomplish the redirect/blocking. That means your local machines (phones, desktops, and servers) must be provided with the proxy server's SSL cert and told to trust it. The local browser connects first to the proxy server for any outbound web requests because it is configured to always ask the proxy for remote URLs. The proxy server then establishes the actual SSL connection to the requested remote site (twitter.com in your example) for itself. As the data comes back from twitter.com over SSL, the proxy server decrypts it, can inspect the cleartext if configured to do so, then re-encrypts the traffic using the proxy server's own SSL cert and returns it to your local browser (remember the browser on your local machines has been told to trust the proxy server's SSL cert implicitly). This is called man-in-the-middle (MITM) SSL interception. The proxy server can also choose to block the attempted website access and return an error message to the user by redirecting them to a custom block page. But that only works because the local clients have been given an SSL cert for the proxy server and told to trust it.
Yes, you can configure this on pfSense, but it requires installing a proxy server package and configuring the MITM certs and distributing them to all of your local assets.
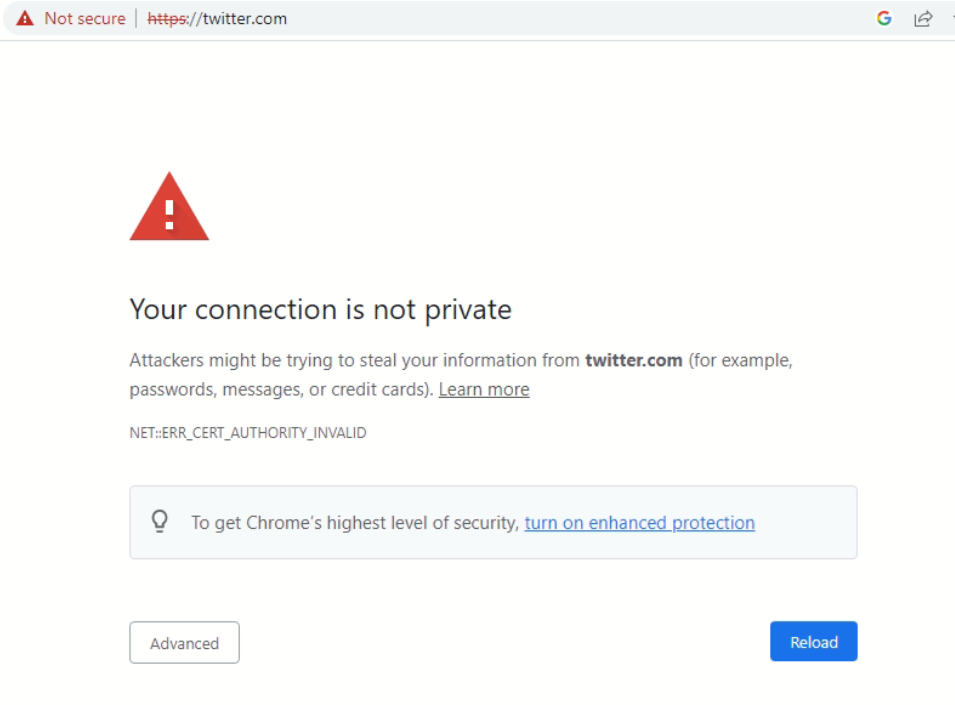
The error message screen you posted in your original post is coming direct from the Chrome web browser. It is not coming from pfSense nor from pfBlockerNG. Chrome is saying "I asked for https://twitter.com, but something else answered that I cannot authenticate as being twitter.com, and I therefore do not trust the site that responded". Chrome cannot authenticate the pfBlockerNG "block website" because it does not have an SSL cert identifying it as "twitter.com". And it never can because it would need twitter.com's private SSL key in order to do that.
The Cisco product whose documentation you linked is a totally different level of beast. It requires you to place additional trusted SSL certs on all of your local client devices, and then configure those devices to route all of their web requests through a proxy server. For the Cisco product, that seems to be their cloud-based server they provide as part of the package you can purchase from them. With that proxy server in place, your local web browsers ask the proxy server to get the website data for them and then relay it to them over a second trusted SSL connection using the proxy server's SSL cert.
Lastly, you can alter the content of the default "blocked website" page in pfBlockerNG. But that page will only display when your users are accessing an HTTP site in cleartext (without SSL encryption). Since almost no website today uses plain HTTP, that "blocked website" page is hardly every going to be called upon.
-
@s-hasan
Sorry I listed the wrong file to edit as dnsbl_active.php
The correct file to edit is dnsbl_default.php
Sorry for any confusion.
Take Care and Enjoy!
-
@s-hasan What your company should do is create a domain with an SSL certificate, example https://block.xzy.com (xyz is the company name) and substitute that page for the pfBlockerng so that when clients go to a page on the company's block list they get the company's beautiful design website apologizing that company policy doesn't allow clients to visit the domain they're attempting to reach.
-
 for the suggestion.
for the suggestion.
But I have question
If you, and thus your browser, wants to visit a blocked domain name, let's say https://www.microsoft.com, do you think a browser would accept a web page coming from a server that says "Hi, I'm https://block.xzy.com" ?
That web server certificate, signed by a trusted certificate authority and valid dates etc, will not contain a SAN that says "microsoft.com" so your browser will say :
NO !If redirecting https was a thing, every bank, tax, government, whatever else site would have been spoofed by know, and the Internet as a communication tools would be forgotten before the end of the year.
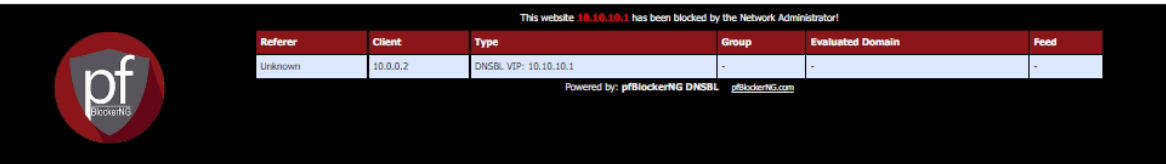
IMHO : the pfBlockerng-devel web server on (default) 10.10.10.1 showing a blocked domain name, works very well for "http", that's the protocol nobody uses anymore these day, it's a thing of the past !
It would only works if the browser, or the entire device, was set up to use pfSense as a proxy, so pfSense would do the lookup of the https page on behalf of the device.
Now, the browser would accept whatever it receives from pfSense. It would show the content of the blocked https://www.microsoft.com : you would see the beautiful "https://block.xzy.com" telling you "microsoft.com" is not possible. -
Thank you guys
Yes, its only can be done through using pfsenes as aproxy server and install internal CA issued by pfsense on each and every device in the network, only then you can have your customised block page. I try it, but pfsense blocked me from the internet. The good thing that the default block page is different with proxy and pfsense is giving you an option to add administratior email as a contact in that page.However, I gave up on the this setup because my boss didnt like the idea of installing CA on each device in the network so, we abandoned on doing it, but it was a great experience.
Thank you very much guys again
I have learned alot from you

-
@gertjan I made an assumption that everyone with pfSense used it for DNS server...thanks for pointing that out.
-
@s-hasan said in How to customize the block page message of pfBlockerNG:
its only can be done through using pfsenes as aproxy server and install internal CA issued by pfsense on each and every device in the network,
No, you need the certificate only on pfSense...not on any other device...don't give up...it's pretty cool company policy to implement. You just need a firewall rule to force all devices (company computers) to use pfSense for DNS.
-
@nollipfsense said in How to customize the block page message of pfBlockerNG:
No, you need the certificate only on pfSense...not on any other device...don't give up...it's pretty cool company policy to implement. You just need a firewall rule to force all devices (company computers) to use pfSense for DNS.
This is not correct. For a cert generated by the internal CA on the firewall, you will have to install that cert on each device and tell the device to trust it. Only then will it trust the pfSense cert without attempting to verify it with a remote certificate authority.
With HTTPS, the browser must trust the cert it receives, or else be able to validate the received cert via one of the public authentication sites (Verisign or other similar ones). For an internal CA cert, you will need to install that cert on each internal device and tell the device to "trust" that cert (in other words, tell the browser not to go out and try to validate the cert with a public certificate authority - just take it as is).
Think about it for a moment -- if it was simply a matter of generating an internal cert of your own and then have any browser on any device trust it without validating it, scammers would be king of the world and there would be no way to stop them from impersonating any bank or financial institution in the world. Fortunately that's not how HTTPS works
 .
. -
@bmeeks said in How to customize the block page message of pfBlockerNG:
For a cert generated by the internal CA on the firewall
Since it's a business, I assume they would get a paid SSL for less than $50 per year. For my business I pay about $25 per year. Apologize for not making that clear.
-
@nollipfsense said in How to customize the block page message of pfBlockerNG:
they would get a paid SSL for less
Why would you use a certificate that you have to pay ?
It's ok of course, but not needed.
No need for a certificate that has been signed by a known or trusted authority.
The CA that pfSEnse has to be imported (installed) into the (every !) device.
From that moment, it is trusted, signed by a known trusted certificate authority, or not. -
@s-hasan said in How to customize the block page message of pfBlockerNG:
However, I gave up on the this setup because my boss didnt like the idea of installing CA on each device in the network so, we abandoned on doing it, but it was a great experience.
@gertjan He said above that was a show stop and since its a business, and the cost is less than $50 per year, which would be less than $5 per month, not $50,000. The paid SSL must be the way to go if the company truly wants to implement a policy allowing only certain domain on their equipment at the office. I am sure with this info his boss would approve.
-
 N NollipfSense referenced this topic on
N NollipfSense referenced this topic on