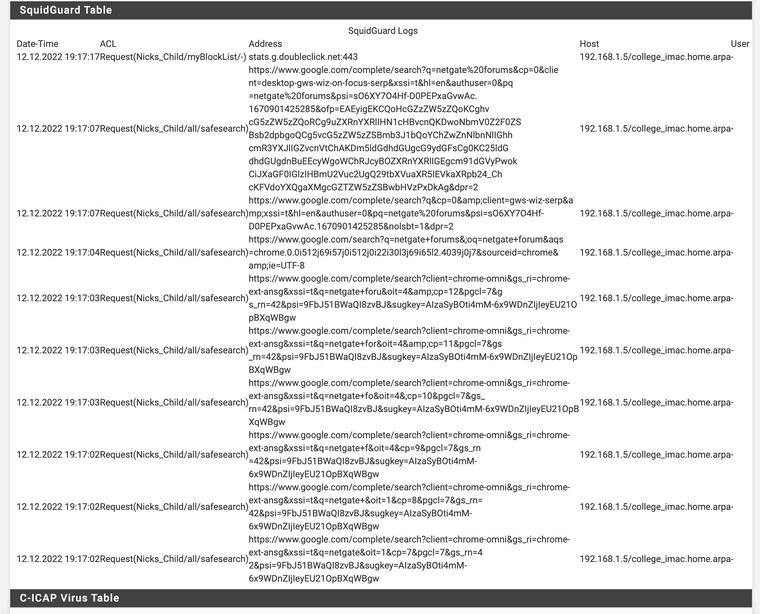
SquidGuard blacklist now bypassing
-
@jeffrey_223 any time I make changes I have to save, and apply. Once it takes the settings, I always restart the firewall. Squidguard integrates into the Squid proxy. So any changes require the reboot to fully work. It's not really meant to have on the fly changes, changes are meant for after hours. That's the only drawback, it is literally filtering the whole internet in real time and blocking specific items. It's meant to run without interrupting once it's configured. Doesn't mean changes can't be done, it just doesn't do them instantly. Glad you got it working.
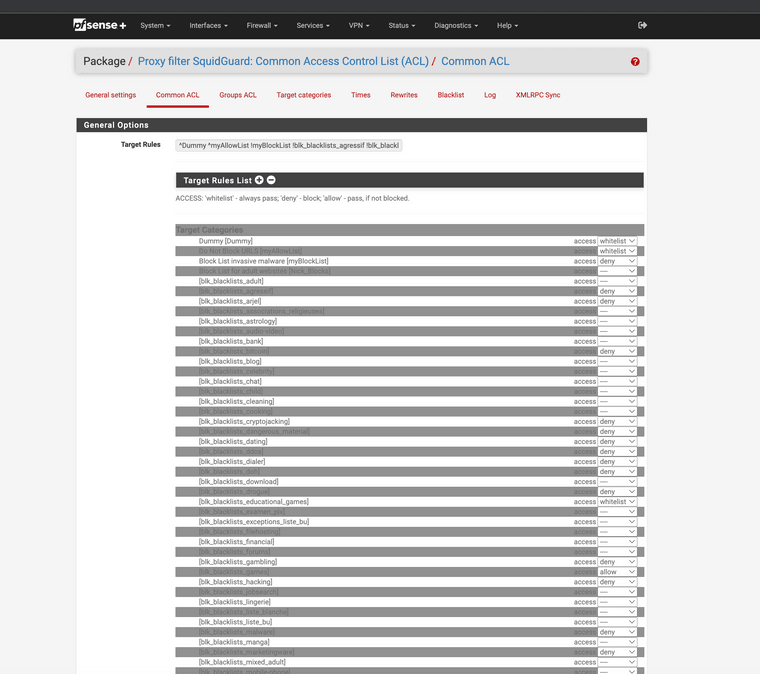
(Image: Blacklist loaded)
http://dsi.ut-capitole.fr/blacklists/download/blacklists_for_pfsense_reducted.tar.gz
I use the above blacklist, that is why I have categories.
-
This is how I got my allow list to work
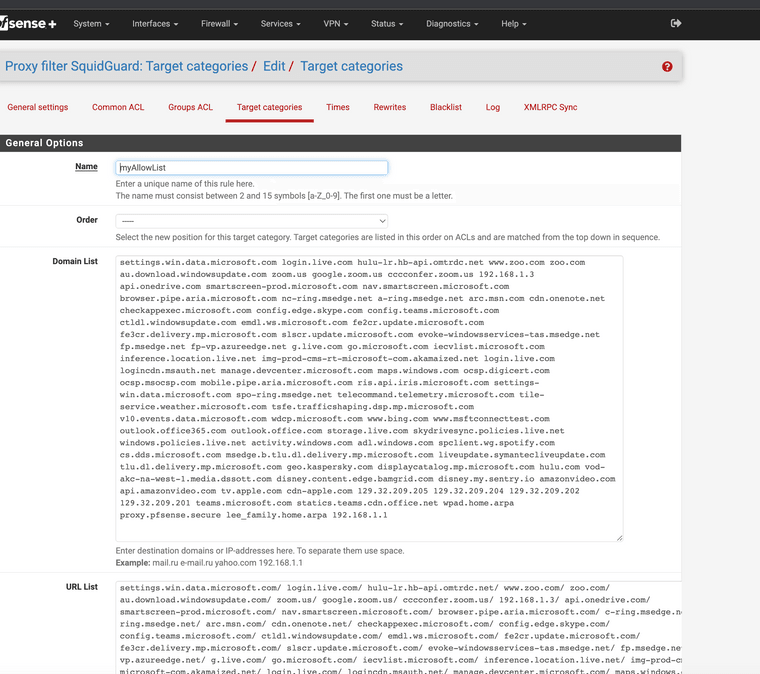
Example:
settings.win.data.microsoft.com login.live.com hulu-lr.hb-api.omtrdc.net www.zoo.com zoo.com au.download.windowsupdate.com zoom.us google.zoom.us cccconfer.zoom.us 192.168.1.3 api.onedrive.com smartscreen-prod.microsoft.com nav.smartscreen.microsoft.com browser.pipe.aria.microsoft.com nc-ring.msedge.net a-ring.msedge.net arc.msn.com cdn.onenote.net checkappexec.microsoft.com config.edge.skype.com config.teams.microsoft.com ctldl.windowsupdate.com emdl.ws.microsoft.com fe2cr.update.microsoft.com fe3cr.delivery.mp.microsoft.com slscr.update.microsoft.com evoke-windowsservices-tas.msedge.net fp.msedge.net fp-vp.azureedge.net g.live.com go.microsoft.com iecvlist.microsoft.com inference.location.live.net img-prod-cms-rt-microsoft-com.akamaized.net login.live.com logincdn.msauth.net manage.devcenter.microsoft.com maps.windows.com ocsp.digicert.com ocsp.msocsp.com mobile.pipe.aria.microsoft.com ris.api.iris.microsoft.com settings-win.data.microsoft.com spo-ring.msedge.net telecommand.telemetry.microsoft.com tile-service.weather.microsoft.com tsfe.trafficshaping.dsp.mp.microsoft.com v10.events.data.microsoft.com wdcp.microsoft.com www.bing.com www.msftconnecttest.com outlook.office365.com outlook.office.com storage.live.com skydrivesync.policies.live.net windows.policies.live.net activity.windows.com adl.windows.com spclient.wg.spotify.com cs.dds.microsoft.com msedge.b.tlu.dl.delivery.mp.microsoft.com liveupdate.symantecliveupdate.com tlu.dl.delivery.mp.microsoft.com geo.kaspersky.com displaycatalog.mp.microsoft.com hulu.com vod-akc-na-west-1.media.dssott.com disney.content.edge.bamgrid.com disney.my.sentry.io amazonvideo.com api.amazonvideo.com tv.apple.com cdn-apple.com 129.32.209.205 129.32.209.204 129.32.209.202 129.32.209.201 teams.microsoft.com statics.teams.cdn.office.net wpad.home.arpa proxy.pfsense.secure lee_family.home.arpa 192.168.1.1
Example URL list:
settings.win.data.microsoft.com/ login.live.com/ hulu-lr.hb-api.omtrdc.net/ www.zoo.com/ zoo.com/ au.download.windowsupdate.com/ zoom.us/ google.zoom.us/ cccconfer.zoom.us/ 192.168.1.3/ api.onedrive.com/ smartscreen-prod.microsoft.com/ nav.smartscreen.microsoft.com/ browser.pipe.aria.microsoft.com/ c-ring.msedge.net/ a-ring.msedge.net/ arc.msn.com/ cdn.onenote.net/ checkappexec.microsoft.com/ config.edge.skype.com/ config.teams.microsoft.com/ ctldl.windowsupdate.com/ emdl.ws.microsoft.com/ fe2cr.update.microsoft.com/ fe3cr.delivery.mp.microsoft.com/ slscr.update.microsoft.com/ evoke-windowsservices-tas.msedge.net/ fp.msedge.net/ fp-vp.azureedge.net/ g.live.com/ go.microsoft.com/ iecvlist.microsoft.com/ inference.location.live.net/ img-prod-cms-rt-microsoft-com.akamaized.net/ login.live.com/ logincdn.msauth.net/ manage.devcenter.microsoft.com/ maps.windows.com/ ocsp.digicert.com/ ocsp.msocsp.com/ mobile.pipe.aria.microsoft.com/ ris.api.iris.microsoft.com/settings-win.data.microsoft.com/spo-ring.msedge.net/ telecommand.telemetry.microsoft.com/ tile-service.weather.microsoft.com/ tsfe.trafficshaping.dsp.mp.microsoft.com/ v10.events.data.microsoft.com/ wdcp.microsoft.com/ www.bing.com/ www.msftconnecttest.com/ outlook.office365.com/ outlook.office.com/ storage.live.com/ skydrivesync.policies.live.net/ windows.policies.live.net/ activity.windows.com/ adl.windows.com/ spclient.wg.spotify.com/ cs.dds.microsoft.com/ msedge.b.tlu.dl.delivery.mp.microsoft.com/ liveupdate.symantecliveupdate.com/ tlu.dl.delivery.mp.microsoft.com/ geo.kaspersky.com/ displaycatalog.mp.microsoft.com/ hulu.com/ vod-akc-na-west-1.media.dssott.com/ disney.content.edge.bamgrid.com/ disney.my.sentry.io/ amazonvideo.com/ api.amazonvideo.com/ tv.apple.com/ cdn-apple.com/ 129.32.209.205/ 129.32.209.202/ 129.32.209.201/ 129.32.209.204/ teams.microsoft.com/ statics.teams.cdn.office.net/ wpad.home.arpa/ proxy.pfsense.secure/ lee_family.home.arpa/ 192.168.1.1/
Example Reg Expression:
(^.prod.do.dsp.mp.microsoft.com.|^.update.microsoft.com.|^.windowsupdate.com.|^.wns.windows.com.|^.dl.delivery.mp.microsoft.com.|^.storecatalogrevocation.storequality.microsoft.com.|^.arc.msn.com.|^.blob.core.windows.net.|^.displaycatalog.mp.microsoft.com.|^.licensing.mp.microsoft.com.|^.pti.store.microsoft.com.|^.watson.telemetry.microsoft.com.|^.au.download.windowsupdate.com.|^.msedge.b.tlu.dl.delivery.mp.microsoft.com.|^.liveupdate.symantecliveupdate.com.|^.delivery.mp.microsoft.com.|^.geo.kaspersky.com.|^.192.168.1.3.|^.displaycatalog.mp.microsoft.com.|^.hulu.com.|^.vod-akc-na-west-1.media.dssott.com.|^.disney.content.edge.bamgrid.com.|^.disney.my.sentry.io.|^.amazonvideo.com.|^.api.amazonvideo.com.|^.tv.apple.com.|^.cdn-apple.com.|^.teams.microsoft.com.|^.wpad.home.arpa.|^.proxy.pfsense.secure.|^.lee_family.home.arpa.|^.192.168.1.1.$)
-
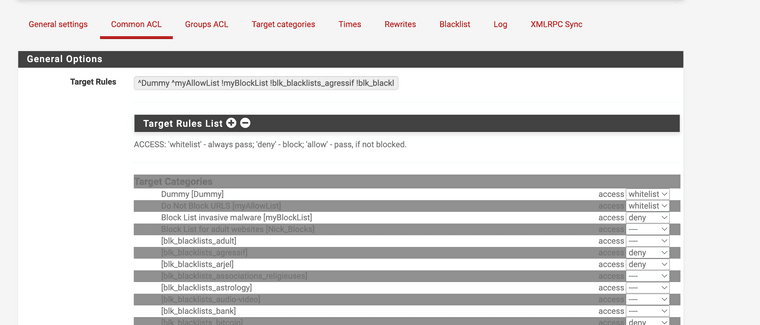
Note I have them marked whitelist that means they are always allowed.
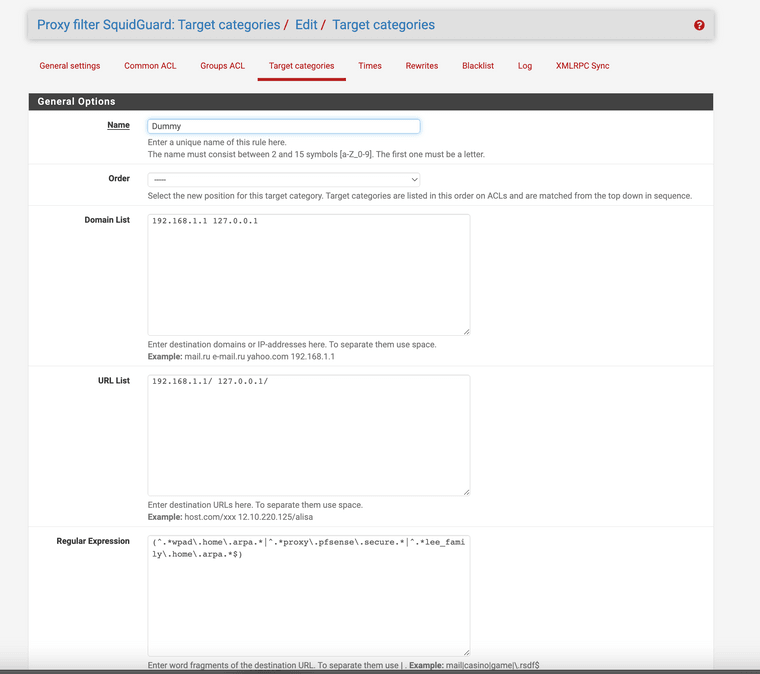
(image Dummy list showing loopbacks)
-
Make sure you make group ACLS this is just the IP addresses of specific requirements
Example loopback:
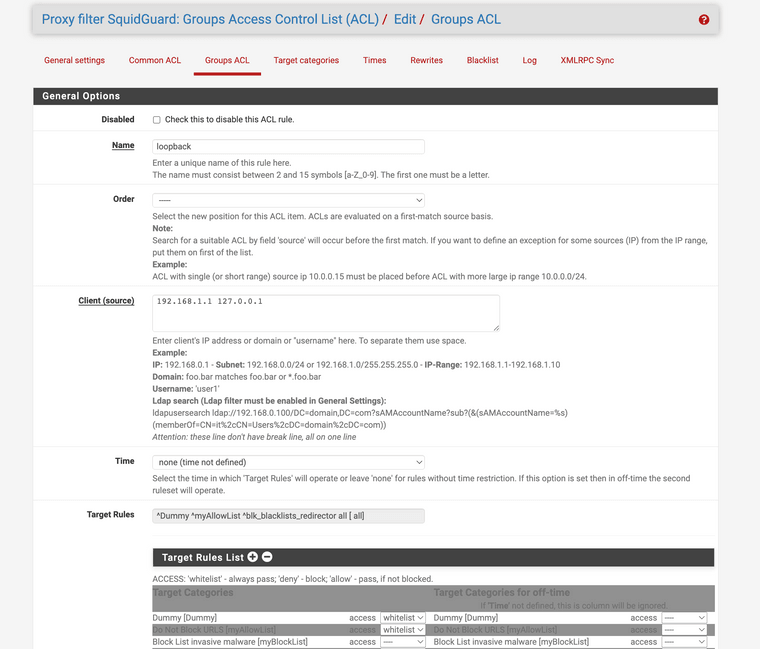
Example Protected Child Group ACL:
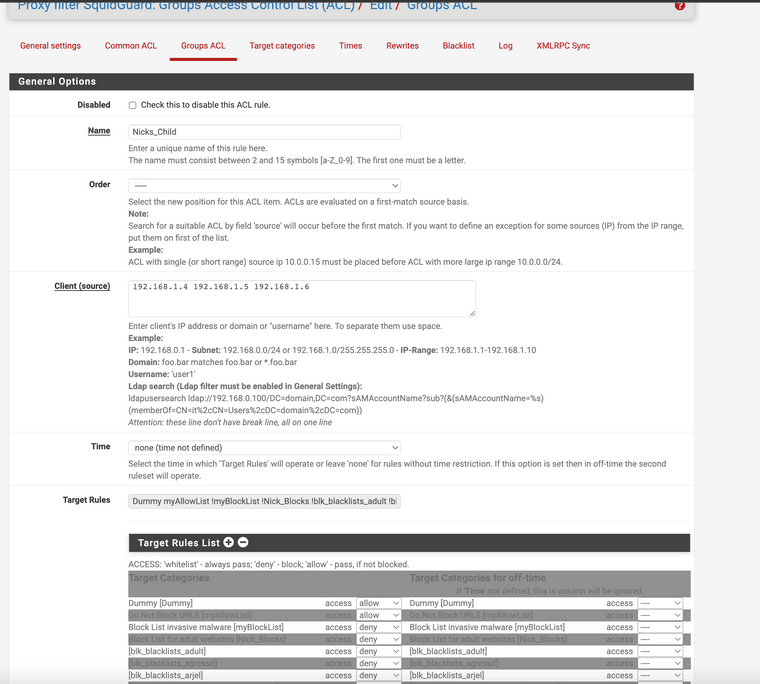
note the deny items.
Targets are what you want to filter approve or block they would show in the Target rule list
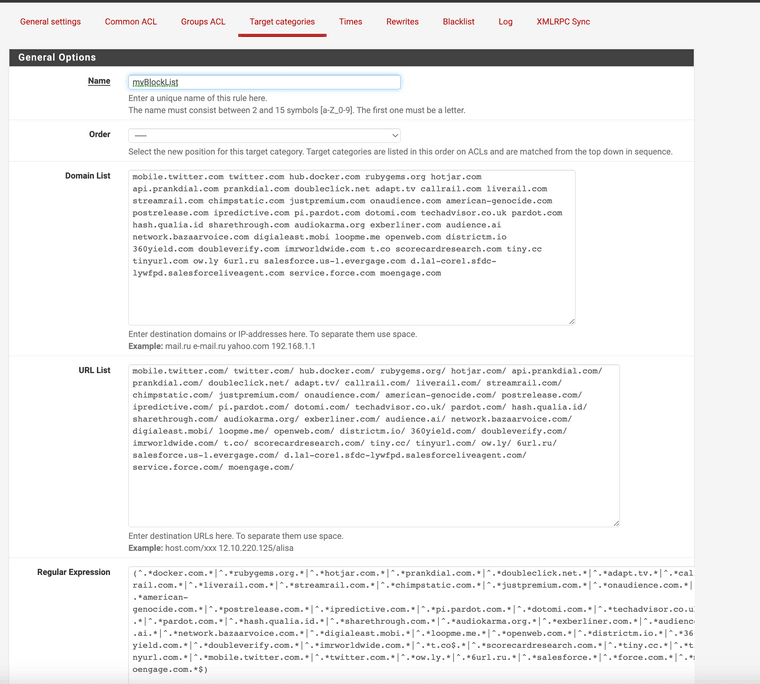
Example: I block docker rubygems prakdial, callrail. -
-
Check this location for ACLS
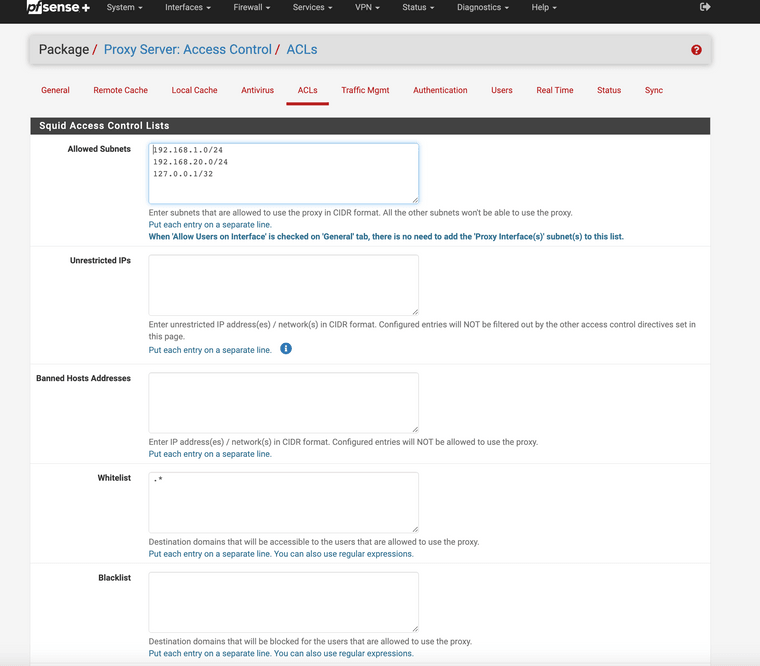
I have two subnets one for the xbox one for the rest notice whitelist .* it will let everything work unless the Squidgard blocks it.
You have approved access to your proxy in the firewall ACLs?
Example:
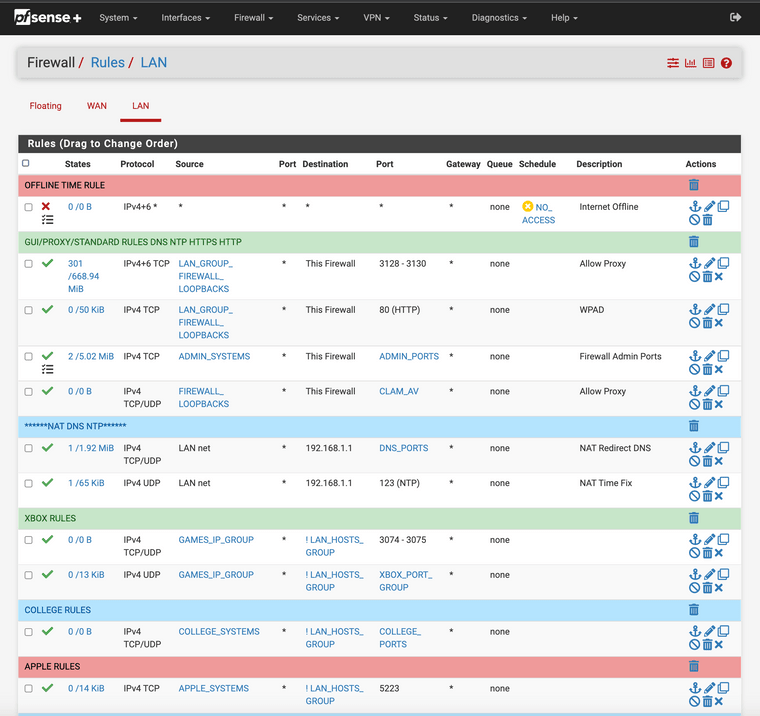
(ignore the offline timer I have a schedule offtime for our house at 12:30am or we become zombies)
Line two port 3128-3130
Line three is for use with my WPAD make sure you enable WPAD before you make a port 80 rule or you will get locked out.https://docs.netgate.com/pfsense/en/latest/recipes/http-client-proxy-wpad.html
Best Document for explaining WPAD ->
I am testing this WPAD today
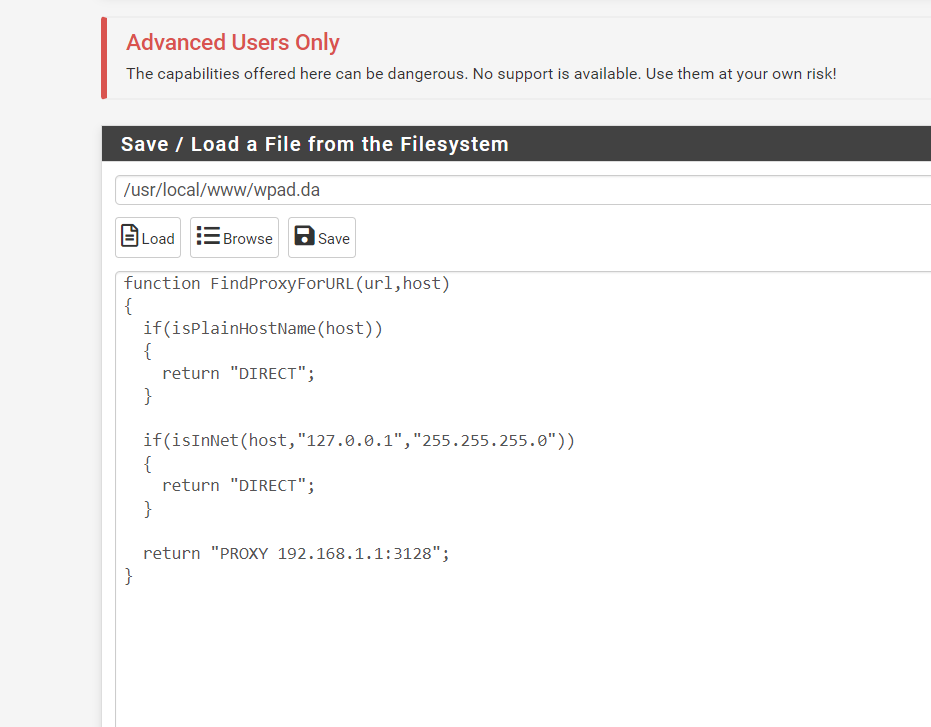
-
@jonathanlee Thanks for all the extra info.
Wow, restart the firewall after new changes didn't think of doing that.
Will do my initial setup and try it again.
All my DNS is running off a Domain Controller.As I'm using this in a work environment and only need to apply this to users, is there a way to make the proxy run on specific subnets?
I thought I had this right but now not so sure.
e.g. filer on 10.10.10.0/24 and 10.10.40.0/24 but exclude all my other subnets. -
@jeffrey_223 I only have 4gb ram some Netgate systems have more memory and can do better on the fly changes. Squid guard let's you do different target categories that can be IP address specific.
-
@jeffrey_223 make sure you run squid check in the command area
this is what I get I just learned about this today
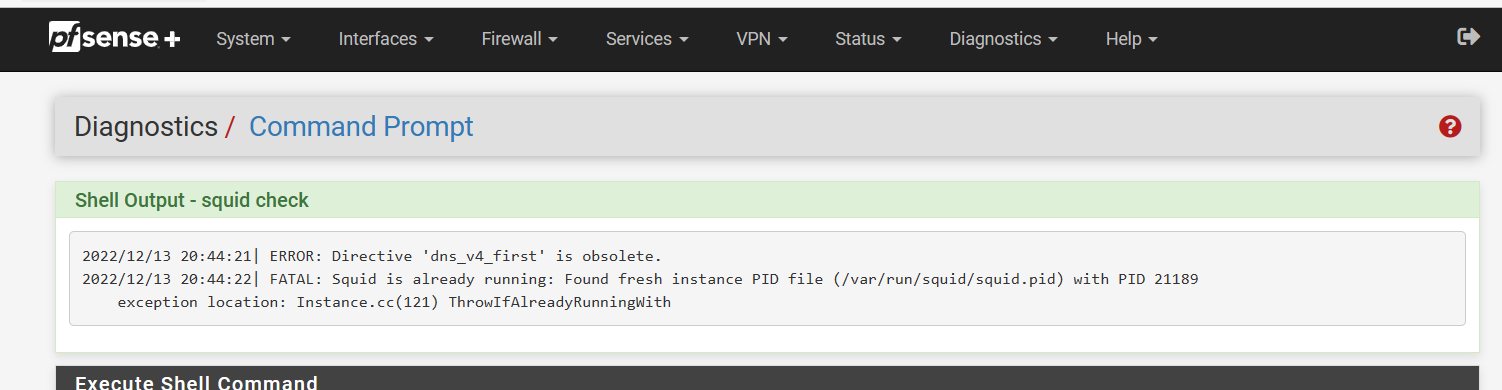
it will show you configuration errors if you have any in squid
-
@jeffrey_223 One last note,
for Wpad to work with the blocked sites like this. . .
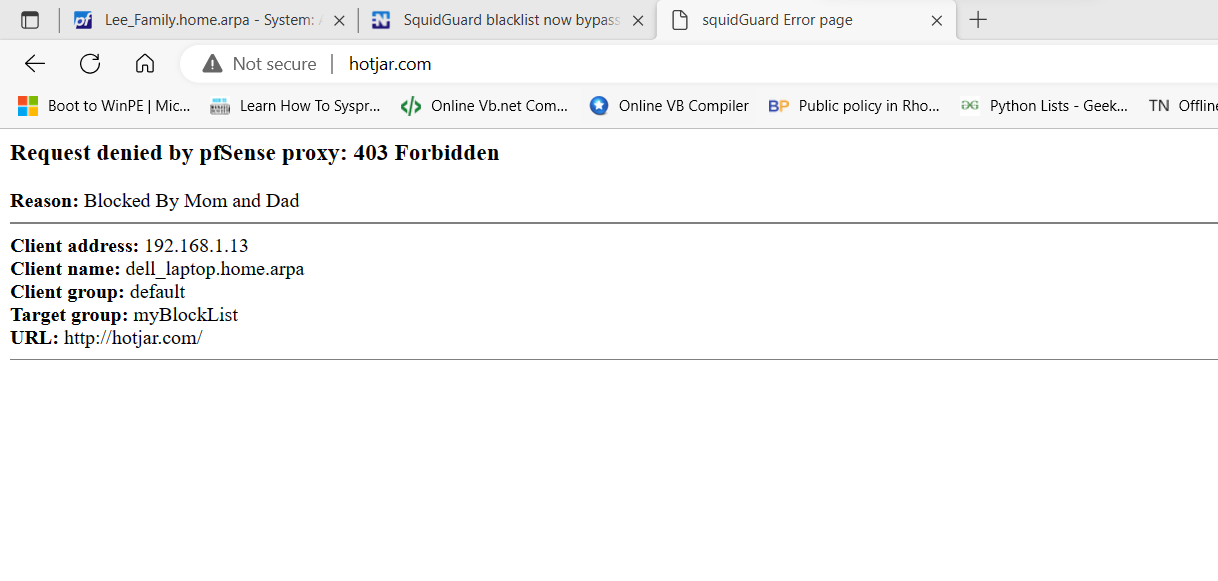
(Image: Hotjar blocked and splash screen showing)
You have to adapt the admin access certificate to be a intermediate, it must use the ca that you created with Squid, or it will give common name errors. Or use a PfSense CA and make a intermediate just for admin access