Help configuring Split Routing of subnets with OpenVPN
-
Hello all.
I'm working on setting up an OpenVPN connection and am having trouble with the routing of my VPN designated subnet using OpenVPN while keeping the non-VPN designated subnets from using the OpenVPN connection.
I have two subnets that internal to my network:
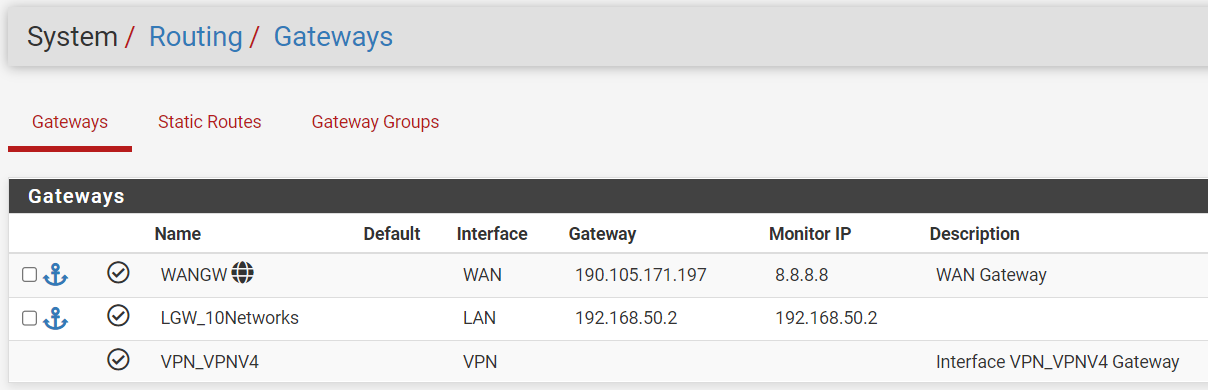
10.10.0.0/16 = Non-VPN traffic that will use the standard WAN gateway.
10.20.0.0/24 = VPN destined traffic that is to only use the OpenVPN connection.The status of the OpenVPN connection is good.
I have the 10.10.0.0/16 traffic working on the WAN gateway with no issues. It simply comes down to I can't figure out how to design the rules specifically for the 10.20.0.0/24 network to only go out the OpenVPN.
After trying a number of rules and setting up the NAT I have been unable to get it routed correctly. I've reloaded the configuration to the point in which I have not created any new firewall rules. Can someone help me to design these rules correctly?
Here is screenshots for reference:
Thanks!
-
@malicair
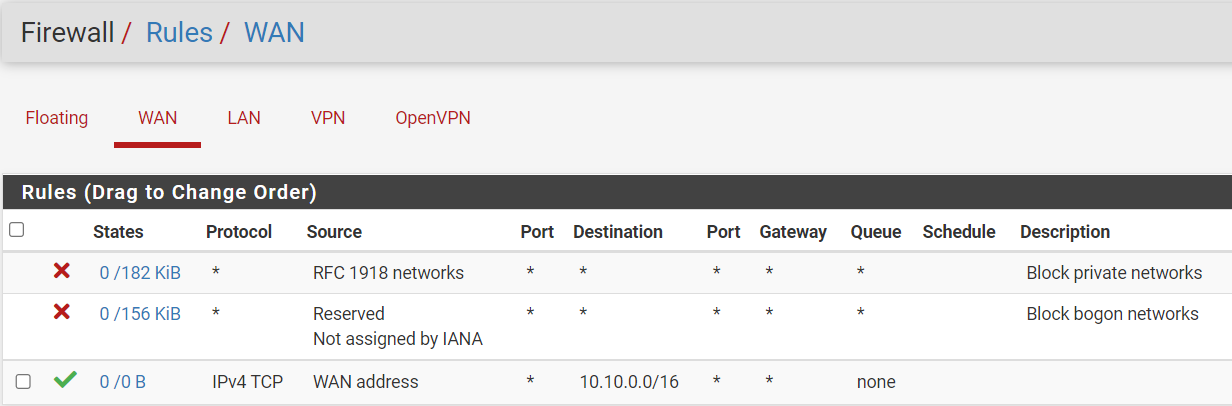
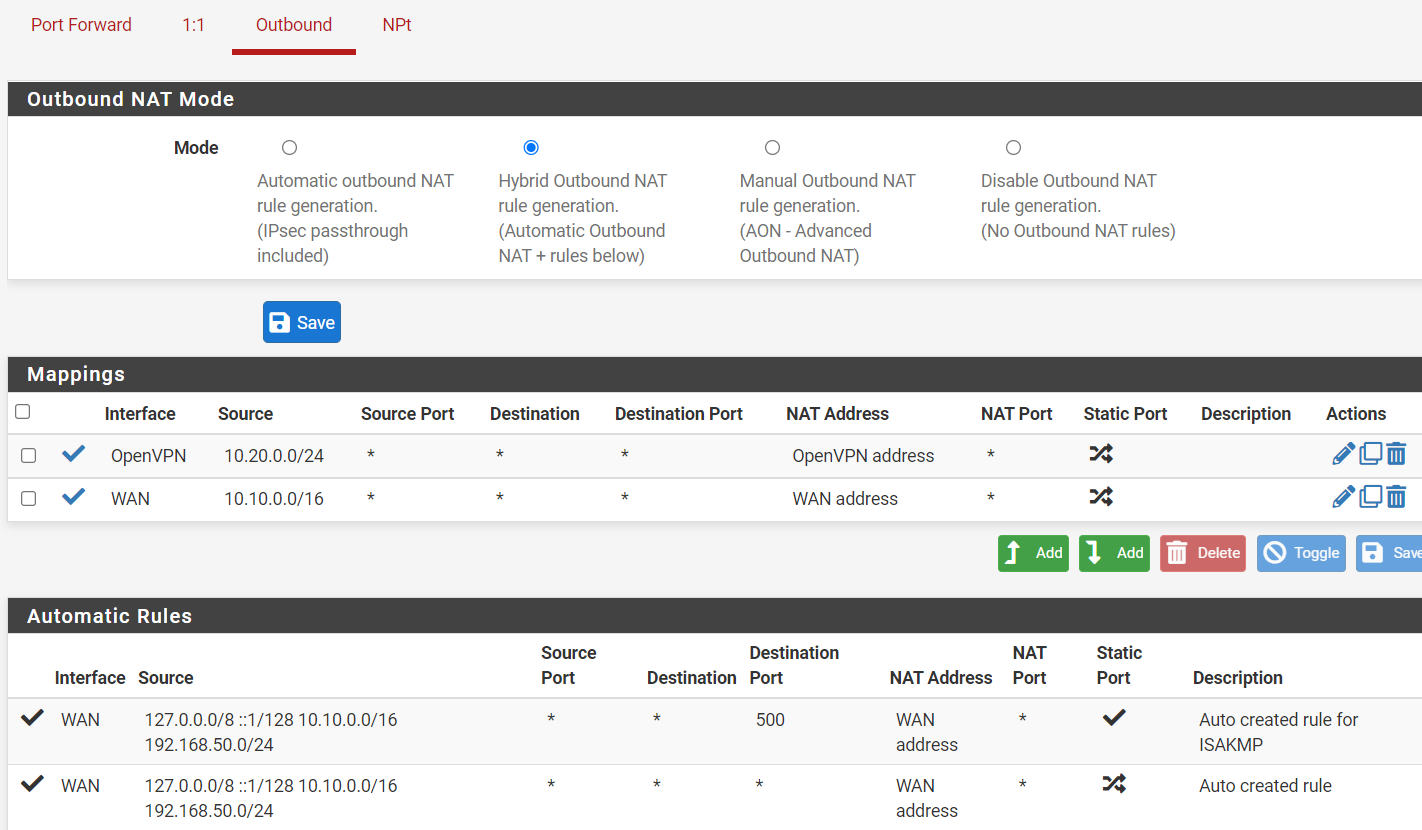
Huh. Bevor you go on you should clean up your existing rules.The pass rule on the WAN seems useless. It allows access from the WAN IP to 10.0.0.0/16.
If even the pfSense WAN IP need access to that network, which I'm in doubt, it won't pass the WAN interface. So the rule will never be applied.The manually added outbound NAT rule for WAN is superfluous.
There is an automatic generated rule for this subnet anyway. Additionally the manual rule overrides the automatic rule for ISAKMP.Also please clarify your network and what you're intending.
I have two subnets that internal to my network:
10.10.0.0/16 = Non-VPN traffic that will use the standard WAN gateway.
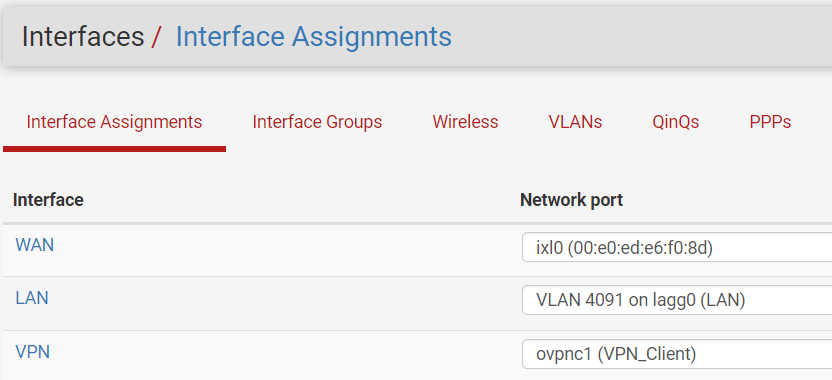
10.20.0.0/24 = VPN destined traffic that is to only use the OpenVPN connection.Which interface are these subnets assigned to:
10.10.0.0/16
10.20.0.0/24
192.168.50.0/24
?Is 10.20.0.0/24 the VPN tunnel network?
What are you intending? Are you running an OpenVPN server and want route the clients out to WAN or to somewhere specific?
Or are you running a VPN client connecting to a provider and want route specific subnets to him? -
@viragomann, Thanks for the response!
Both of the 10.x networks are managed by the 192.168.50.2 switch. For reference I have this design as it is easier for me to manage and moving all these networks to the PFSense router is not something I want to do.
Here is a parsed down diagram of my network which shows the basic equipment.
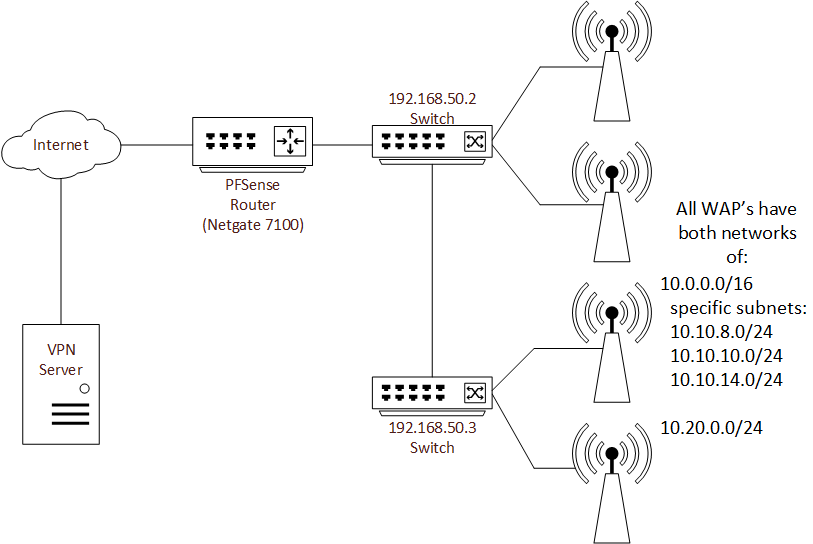
The router has a single WAN interface connected and is configured with a VPN client to a provider. This connection is good as I have validated that it is authenticated in Status > OpenVPN.
For simplicity I grouped three subnets within a 10.10.0.0/16 range together which are:
10.10.8.0/24, 10.10.10.0/24 & 10.10.014.0/24. None of the devices connected to these subnets are to utilize the VPN connection.I have the 10.20.0.0/24 which is only for devices that are to utilize the VPN connection to the provider.
The 192.168.50.2 switch is connected to the router via ethernet port 1. The WAN connection is via a fiber connection utilizing one of the SFP ports.
As for the rules and NAT configuration this is not something that I am that good at. I've been more of a design person which managed teams before I retired that did all the implementation work. But with that I can manage to get myself through configuring equipment within CLI and now learning the GUI interface of PFSense. Therefore specific help with the NAT and rules is greatly appreciated.
-
@malicair
Thanks, pretty clear now.You can securely the superfluous firewall an outbound NAT rules, I mentioned above, anyway.
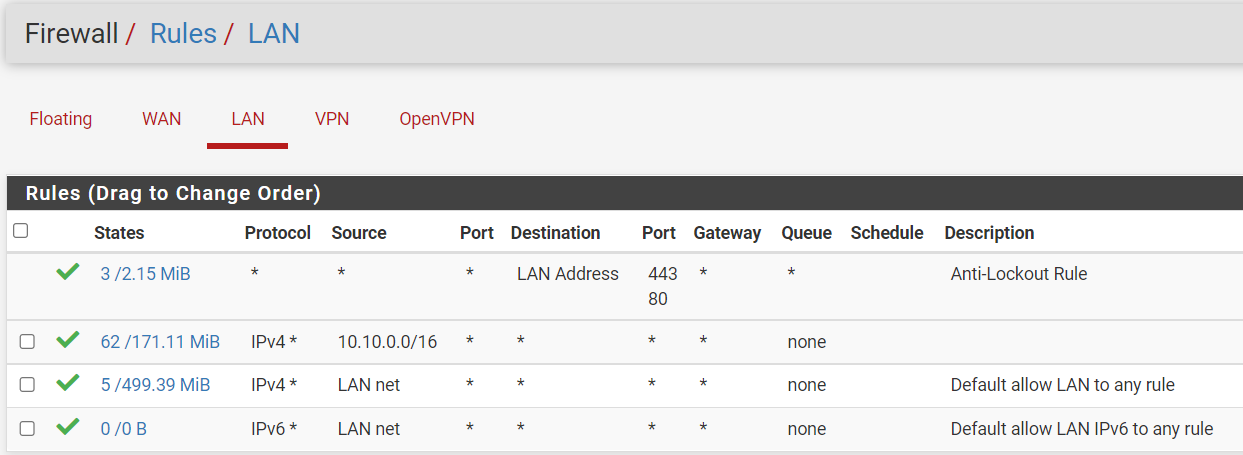
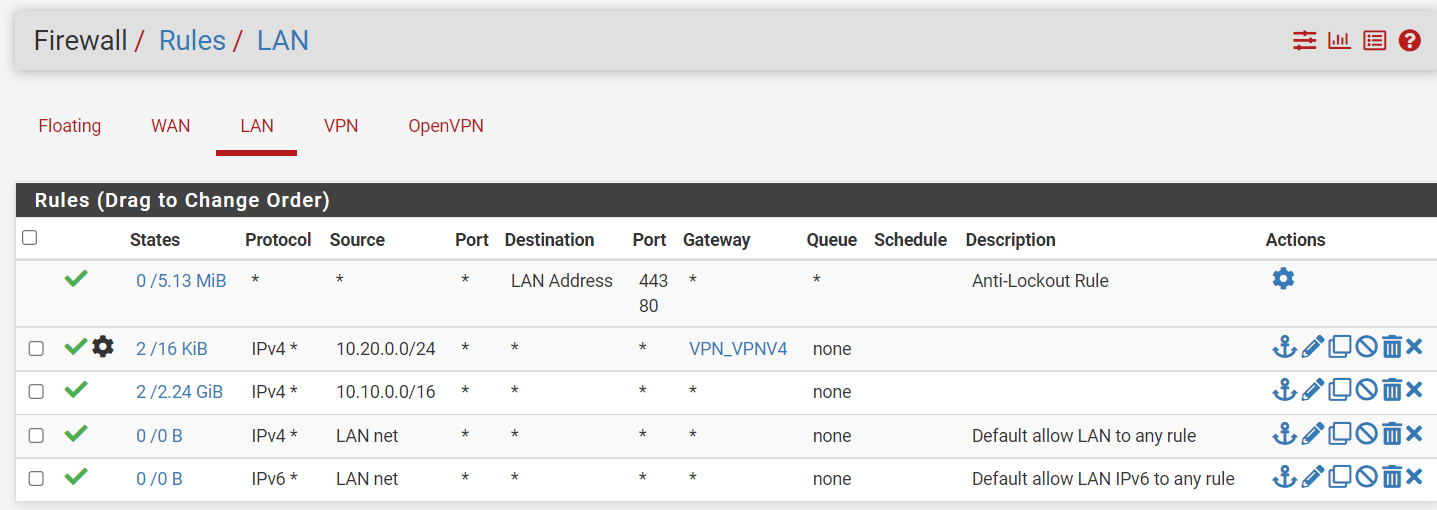
For routing the subnet to the VPN server you need a policy routing rule. That is a firewall pass rule on the LAN:
source: 10.20.0.0/24
destination: any
Open the advanced options, go down to gateway and select the VPN gateway, save.This rule then routes any traffic from the respective subnet to the VPN server.
But there is a thing more to clarify: Does 10.20.0.0/24 also need to access anything on the LAN or on pfSense?
The latter could happen if the device use the DNS resolver on pfSense. Or do you need to avoid DNS leaks from the subnet?
The rule above doesn't allow any internal access. -
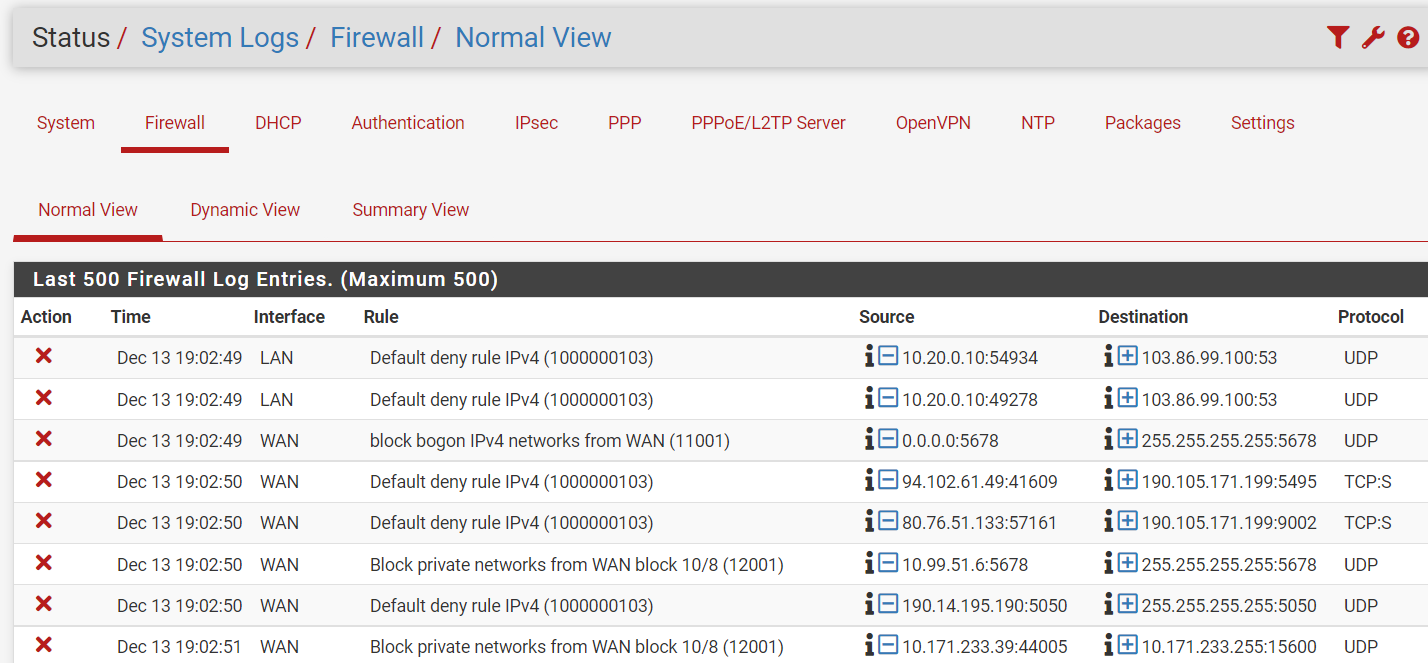
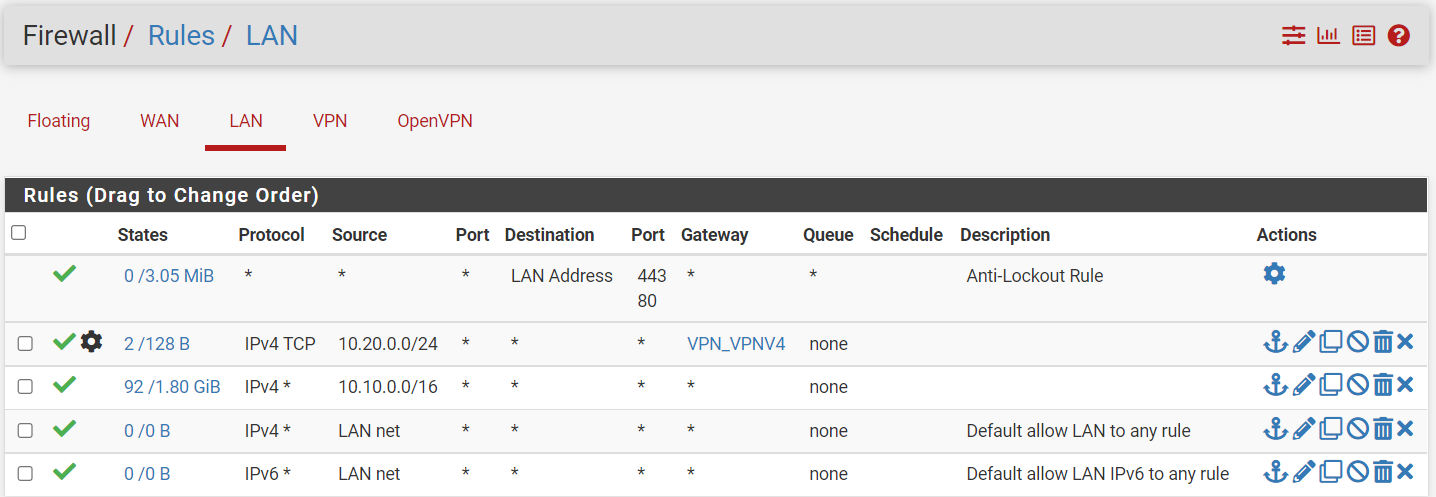
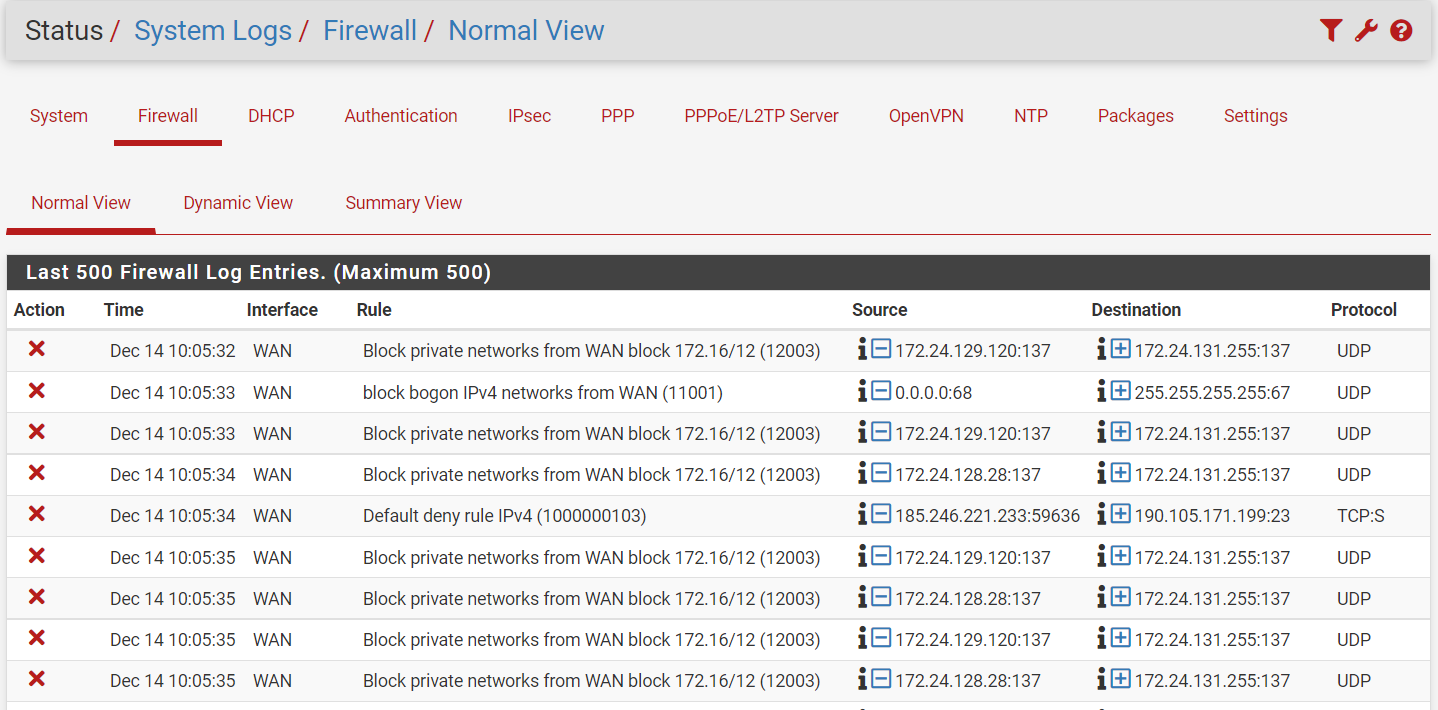
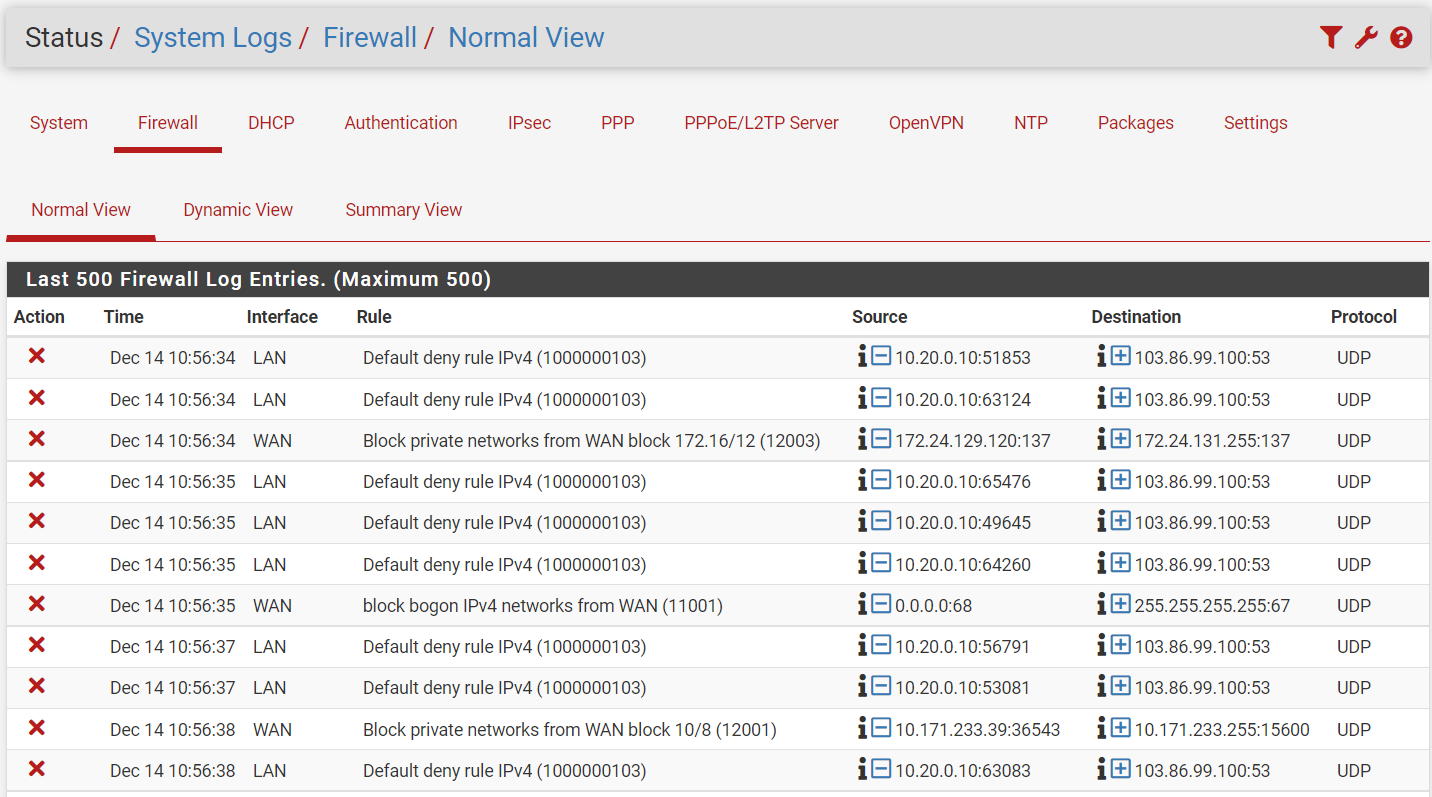
Ok added the rule as you suggested. But I'm still not getting any connection through the VPN. When looking at the system logs for the firewall I'm seeing a bunch of blocks happening.
Also in an earlier post you suggested I clean up other rules.
-
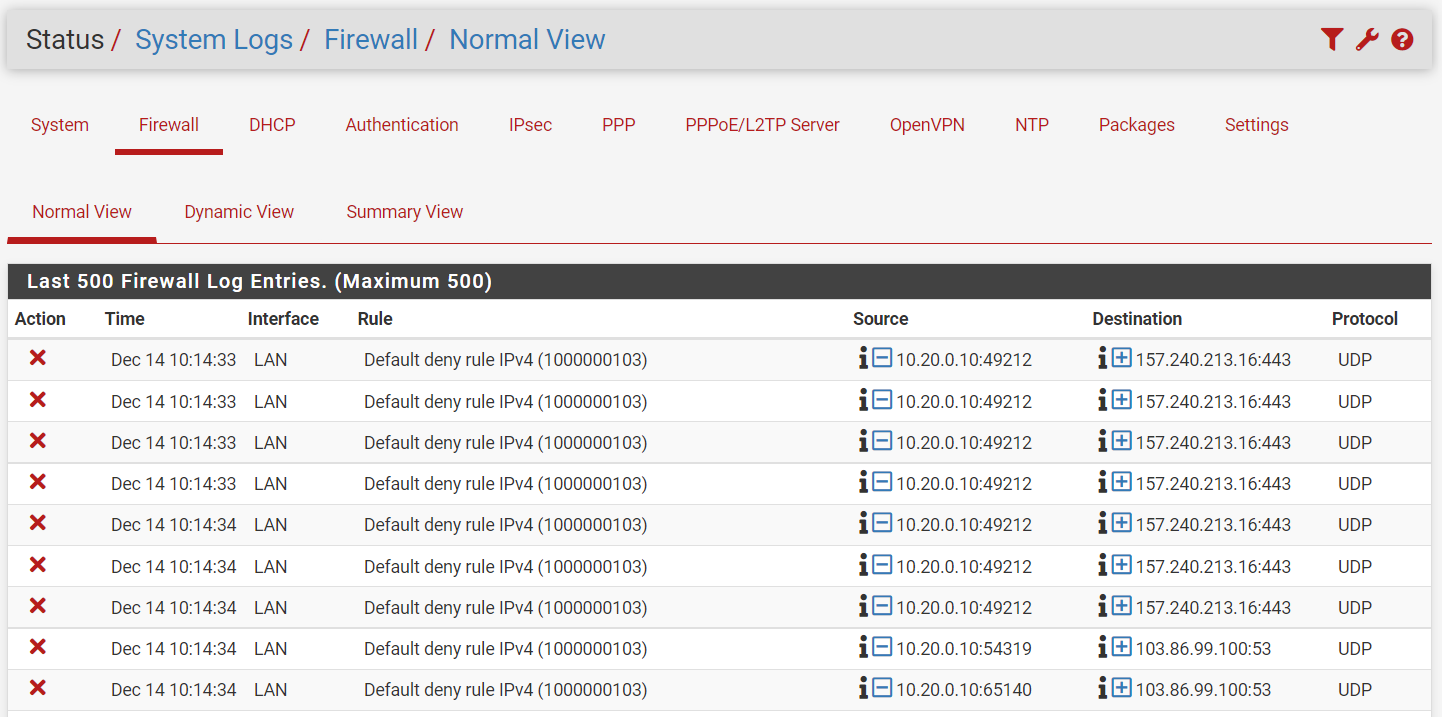
@viragomann,
I am also getting blocks on the LAN interface for the 10.20.
-
@malicair
You should answer my question before you go on testing.The blocks on WAN are private IPs. From your diagram I don't expect to see private IPs on WAN, but maybe that doesn't show all.
In the rule for the VPN subnet you only allowed TCP protocol. Hence all other as UDP here is blocked by the default deny rule.
-
@viragomann, Since you stated that the rule you outlined was not going to allow internal access then that would be correct, since why I implemented the rule.
The VPN client is setup with a UDP connection. I can switch it to a TCP if necessary or should I just switch the rules to TCP/UDP?
Suggestions for next move?
-
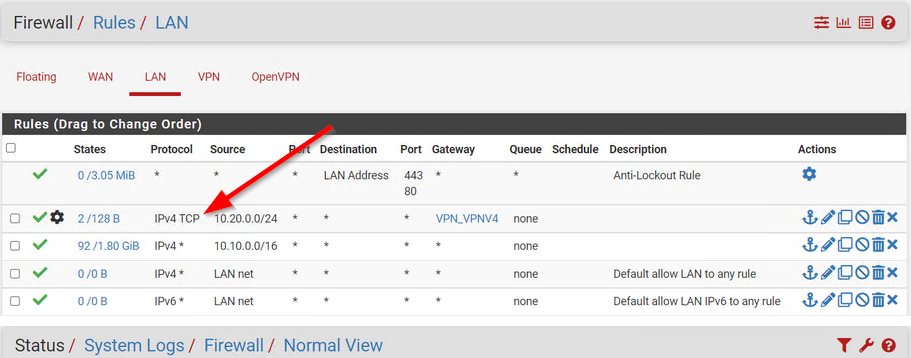
@malicair
I'm talking about this
-
@viragomann, AH.. yes that should be "any". I've changed it to "any" now so it looks like the 10.10 rule below it.
Still receiving firewall block errors.
-
Just a second... I need to backup as I just realized that last night when I finished working I had to disable the VPN client as it was grabbing the 10.10 traffic and causing me to not have internet access. I forgot to turn it back on this morning and much of what we have done is compounded by not having the VPN up and running.
So, first off I need to fix the routing issue that is allowing the VPN client to hijack the 10.10 traffic and subsequently killing it's connectivity.
The tough part is it also kills my 192.168.50.x connection to the internet so when I have to continue to turn it off/on to work on the problem, while checking email/post updates.
So can you please step back to the beginning and give me advice on how to fix the rules for 10.10 and 192.168.50 so they won't be caught up with the VPN client setup?
-
@malicair
Add a check here and save:
System > Advanced > Miscellaneous > Skip rules when gateway is down -
@viragomann, ok that check has been added and now internet has been restored for 10.10.
So back to getting the 10.20 connection working
Where do I go next?
-
@malicair
Did you try with the VPN connected to the server?Without the suggested check, the rule is omitted if the gateway is down. So the blocks are expected.
Also ensure that the VPN gateway state is online.
-
@viragomann
Within Status it shows the VPN has been authenticated:
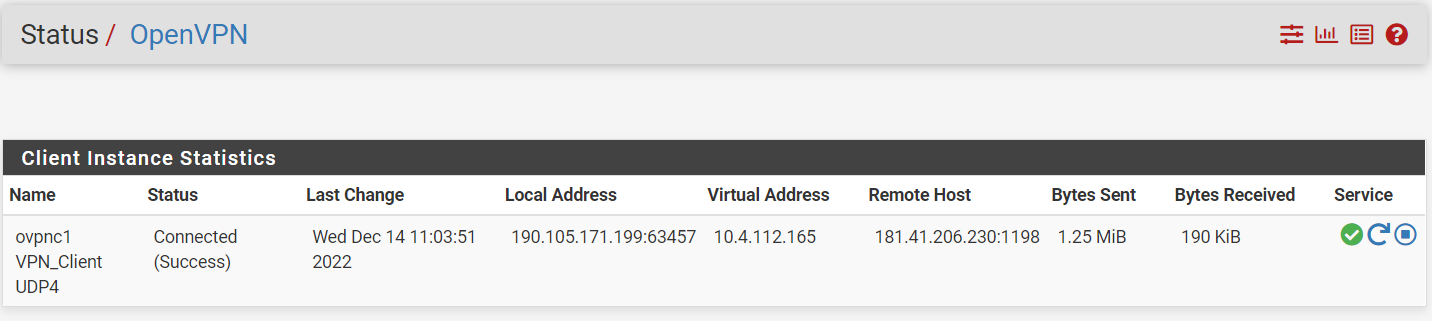
What/how else should I check to verify?
-
@malicair
Check Status > Gateways, please. -
@viragomann
Status > Gateways.. Pending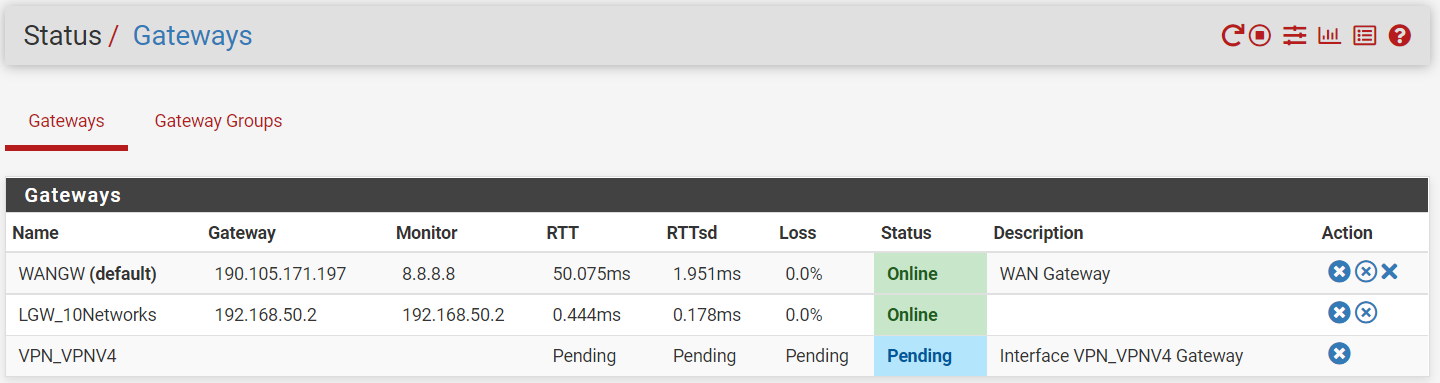
-
@malicair
Rules with gateway are only applied if it's online naturally.The gateway state is detected by pinging it's IP. Obviously it doesn't respond. So you have to change the monitoring IP to any other in the internet, which is responding.
But it has to be another than 8.8.8.8, since this is already in use by the WAN gw and hence pfSense has added a static route to it. -
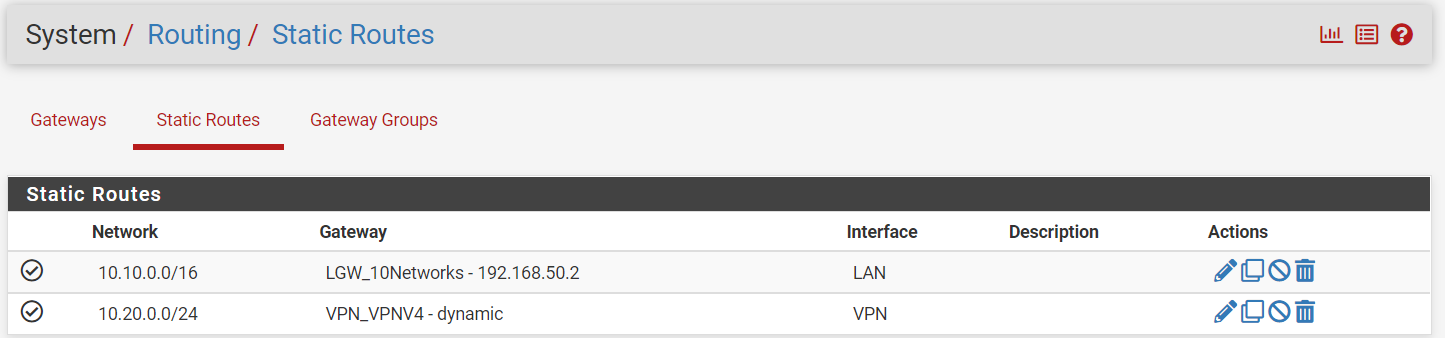
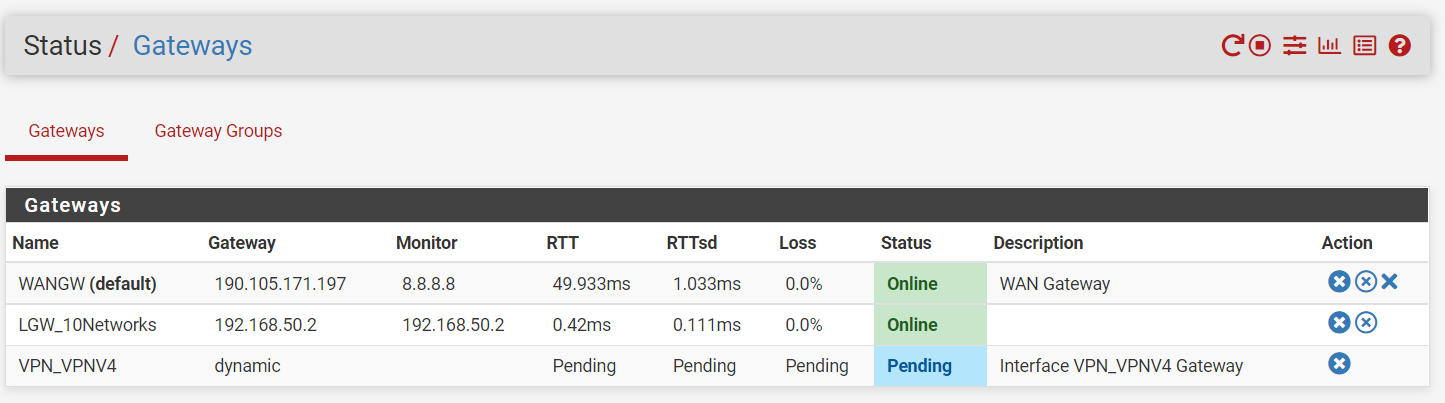
I added a monitoring IP of 9.9.9.9 which is Quad9 to the VPN.
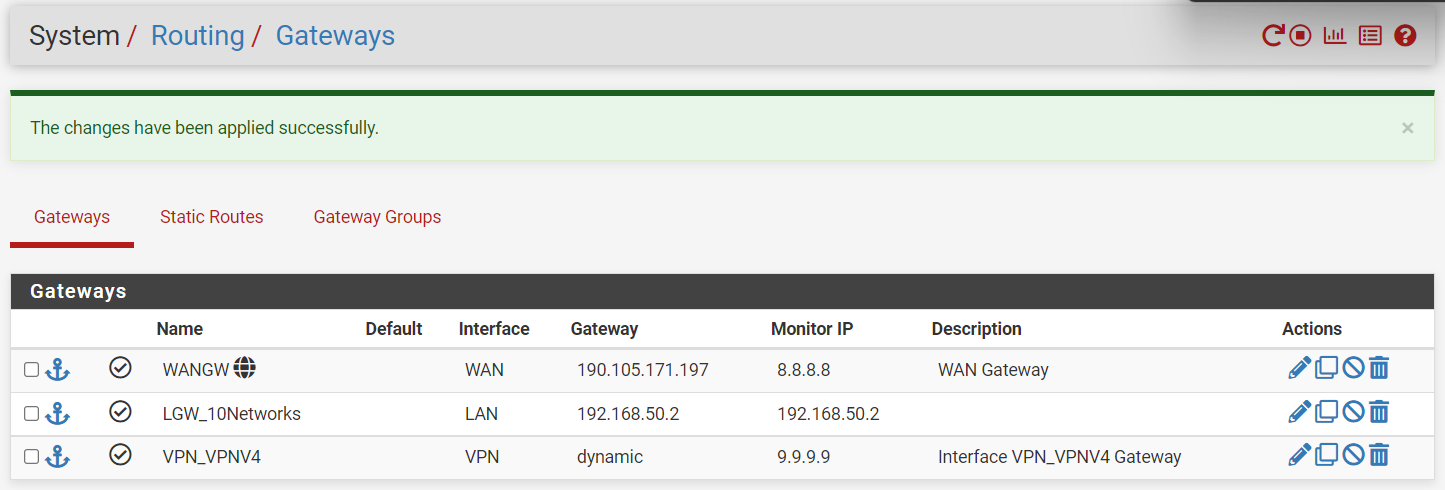
Are these routes correct or needed?
The Gateway status still shows as pending.
I sure wish I knew this stuff better, but simply don't need these skills hardly at all anymore. Subsequently I greatly appreciate your help and If I could buy you a drink I definitely would!
-
@malicair said in Help configuring Split Routing of subnets with OpenVPN:
I added a monitoring IP of 9.9.9.9 which is Quad9 to the VPN.
You should better test before if the server is responding. It doesn't obviously.
ping 9.9.9.9
1.1.1.1 does for instance.
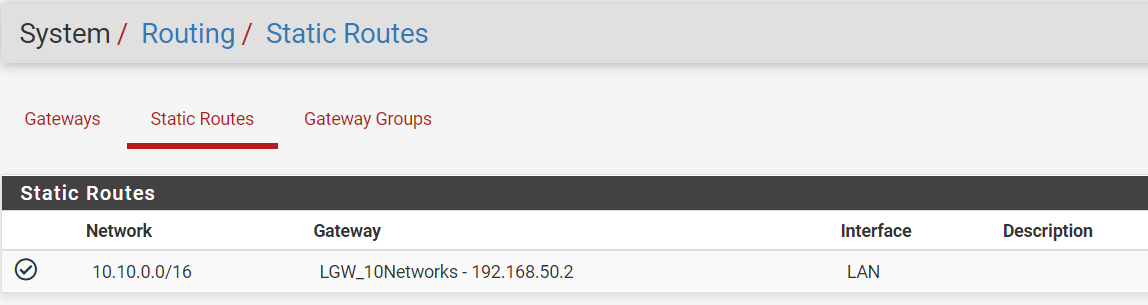
Are these routes correct or needed?
The route for the VPN should must be deleted.
The other is needed for directing the 10.10.0.0/16 to the switch.