Firewall destination port vs NAT
-
Hi, I am starting with PFSENSE and I am a bit confused regarding firewall destination port rules. I am trying to access ssh from the outside world. Lets say I have created a port forwarding on my router to accept incoming requests on port 45678 and redirect it to 192.168.1.2:45678 (WAN interface on my pfsense).
Now, on my pfsense, I have defined this firewall rule:

But I never get to connect to ssh (I have already activated ssh, by the way). The same happens whenever I try to get https working to access via GUI.
Am I missing something? Am I wrong considering this rule acts like a port forwarding too that gets incoming requests on port 45678 and redirects it to the same firewall on port 22? Or do I need a NAT forwarding too?
Thanks in advance,
Jose -
@kankamuso if you have a router in front of pfsense that you are forwarding traffic to pfsense from - and you don't get to pfsense, then there is something wrong upstream.
Notice your rule there with the 0/0 B - means that pfsense never saw any traffic to that rule to allow it.
Also keep in mind that you need to be testing really from out side.. If your trying to hit your wan public IP from some network on your pfsense lan - your edge router would need to do a nat reflection.
The easiest test is to go to say can you see me . org - send some traffic on this port. Does pfsense it? Either via rule showing hits, or do a simple sniff on pfsense wan.. Do you see that traffic?
Here simple test, I don't have anything setup for that port on pfsense - but I can test if pfsense sees traffic to that port via a packet capture on its wan
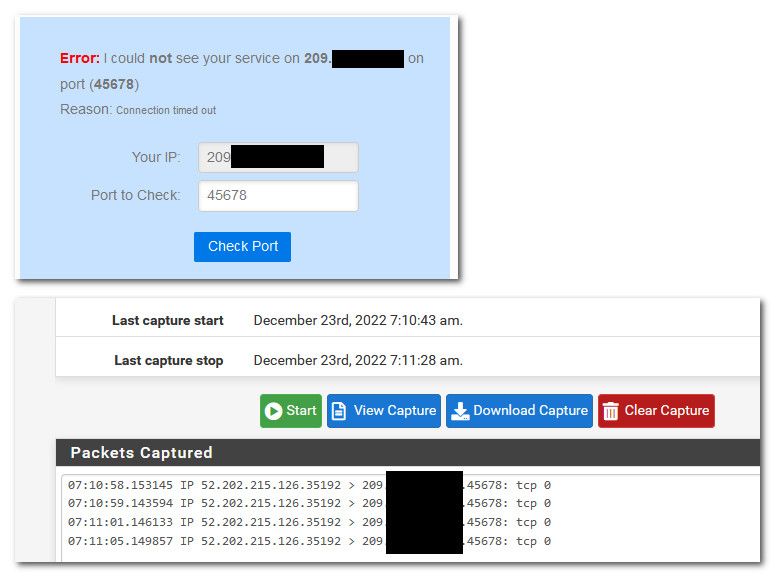
-
@kankamuso said in Firewall destination port vs NAT:
Lets say I have created a port forwarding on my router to accept incoming requests on port 45678 and redirect it to 192.168.1.2:45678 (WAN interface on my pfsense).
If pfSense is listening on port 22 for SSH forward the packets to port 22 on the router.
Otherwise you can as well state an alternative SSH port in System > Advanced > Admin AccessNow, on my pfsense, I have defined this firewall rule:
This rule allows only source port 45678 to access port 22 on pfSense WAN. This might not be what you want at all.
The source port has to be any, since it's dynamic. -
@viragomann good catch.. Yeah that rule is not a valid firewall rule even to access ssh running on pfsense.
Unless the source was 45678, which is highly highly unlikely to be the case..
-
@viragomann so what is wrong is my missunderstanding of the meaning of source port. It is not the port where I reach the WAN through but the port on my computer?
I am new to pfsense and almost to firewall filtering. I studied it while on the university but I didn't need until now!
Thanks!
-
@kankamuso "Source port" is the port the remote computer uses to connect out to the server, in this case SSH on port 22. Source ports are typically random and higher than 1024. By setting the source port to 45678 you'd have a roughly 1/64000 chance of it working. If you set the source port to any and leave the destination the same it will allow any inbound connection.
accept incoming requests on port 45678 and redirect it to 192.168.1.2:45678 (WAN interface on my pfsense)
If it was being redirected to an internal server that would be a NAT rule not a firewall rule. A firewall rule is still needed but note by default NAT forwards create a linked firewall rule to allow the NAT to work.
However that's not what you're describing. To get pfSense to listen on 45678 you'll either need to change the listening port on its SSH server, or you could try forwarding WANIP:45678 to LANIP:22.
I'd recommend not allowing connections from the world though.
https://docs.netgate.com/pfsense/en/latest/recipes/ssh-access.html#ssh-daemon-security. If you really need remote access from a non-static IP you could set up a dynamic DNS hostname and allow connections only from that hostname.