OpenVPN not connecting
-
Hello, I have pf sense and have openvpn installed. I set it up a while ago and everything worked fine off my home network and using open vpn from a different area to connect back to my home network. I recently noticed that it stopped working and wont connect how it normally would. I dont recall any changes being made so I'm not sure why it won't connect anymore. Recently I logged into pf sense (2.6.0-RELEASE (amd64) ) and updated open vpn (1.6_8), Then i logged onto my laptop and uninstalled the old version open vpn and downloaded the most recent one from pf sense and the config file. Then I connected my laptop to my mobile hotspot and tried connecting to open vpn using the old config file and it took a minute before saying it couldn't connect. Then i tried the new config file (no changes made just new since the newest version install) and that gave a quicker almost immediate bounce back of 'cant connect'.
I can upload pics if needed but I am not sure what to upload. I looked at all the settings and nothing seemed to change so im not sure where to start troubleshooting this nor what I can troubleshoot anymore.Any ideas would be great. Thanks.
-
The usual tests :
Your client uses a host name. Does it point to the pfSense WAN IP ?
You have a firewall rule on WAN that lets in the OpenVPN traffic. Can you see the state counters getting bigger :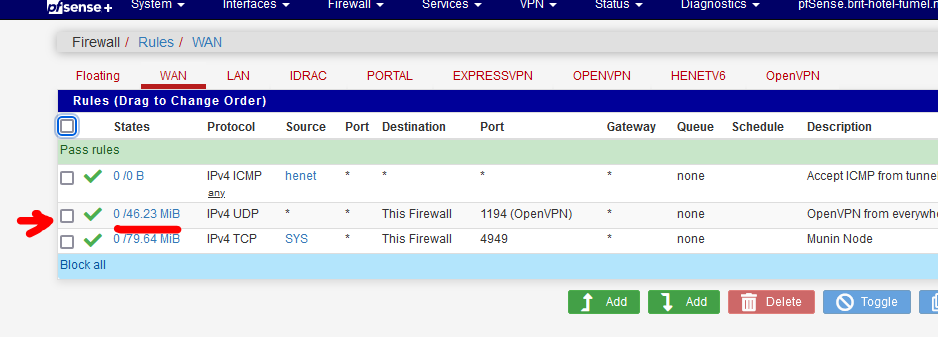
and as always : See the OpenVPN log.
-
@gertjan Thank you for the picture and info.
Here are my rules I have setup.
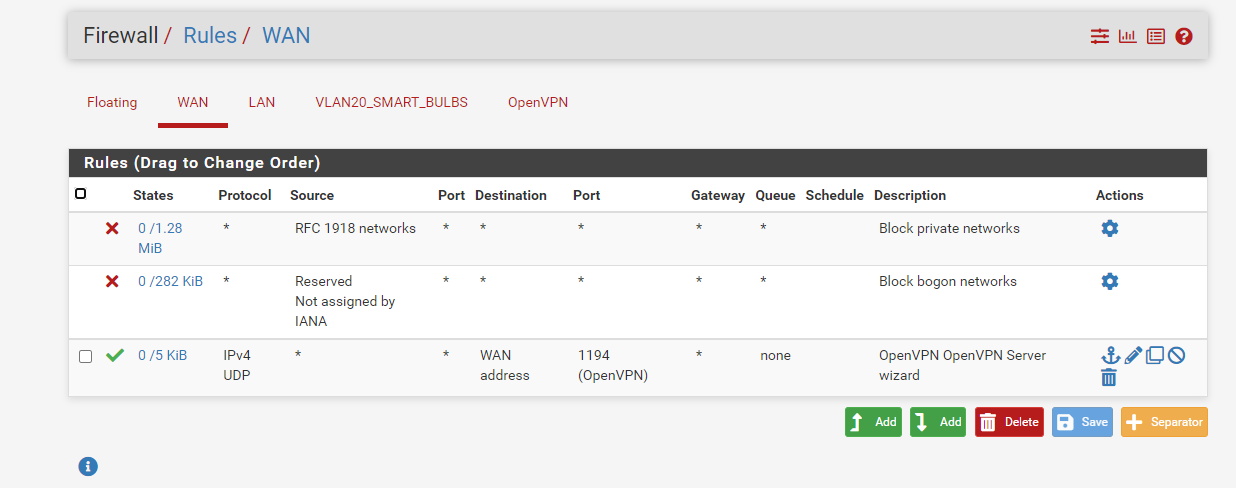
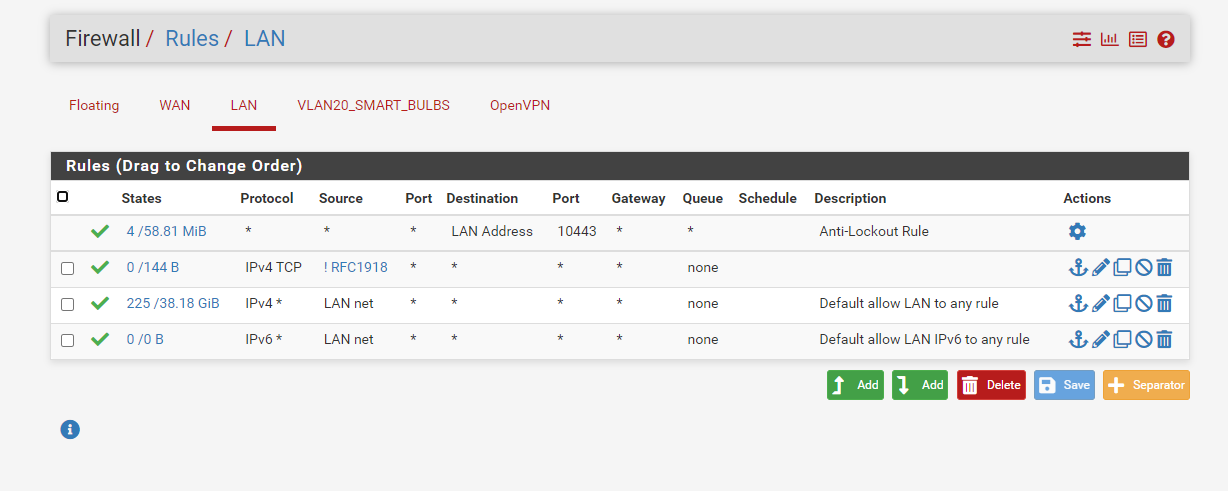
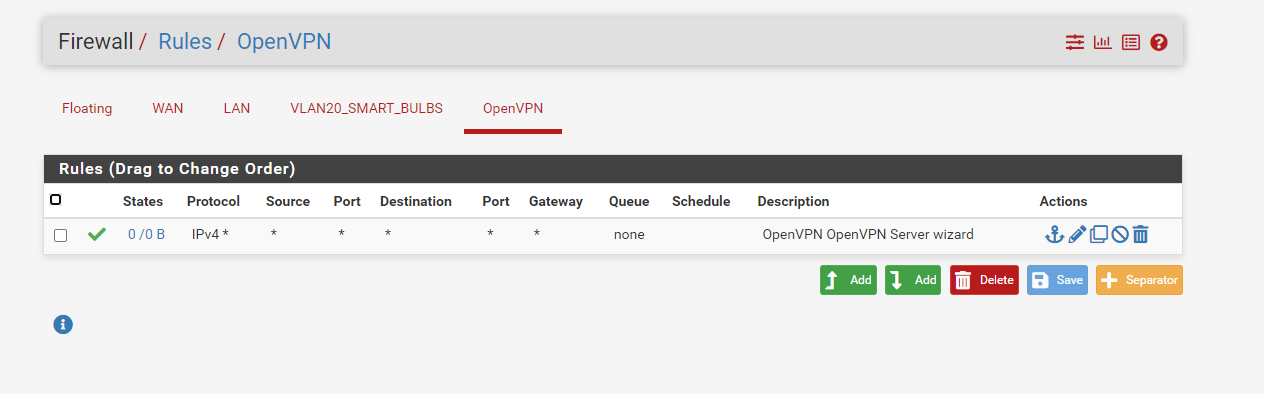
I do believe everything is setup correctly but not 100% sure. -
These first two rule :
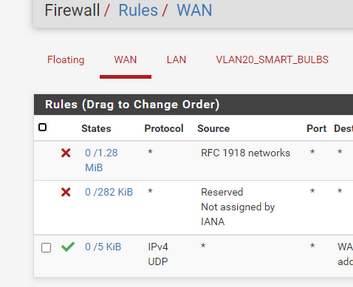
can be de activated on the WAN interface.
The OpenVPN rule looks fine.The packet/state counter even shows that traffic did come in, the rule was used.
So : go check the OpenVPN log and see what OpenVPN (server) did with that traffic.
When a remote OpenVPN client logs in to your OpenVPN server, you see many log lines.Your LAN and OpenVPN rules look fine.
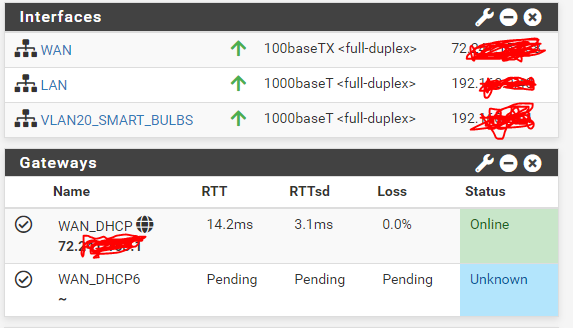
You've set up DHCP6 on your WAN interface.
Make a choice : finish the IPv6 if your WAN (ISP) supports it, or disable IPv6 on the WAN.
The goal is :
Make this 'green' == ok, or remove the non work IPv6 gateway.
-
@gertjan thanks for the info and pictures. I decided to disable IPV6. I clicked the disable check box (not show that i clicked it in the pic) but then reflected in the nxt pic is it showing disabled.
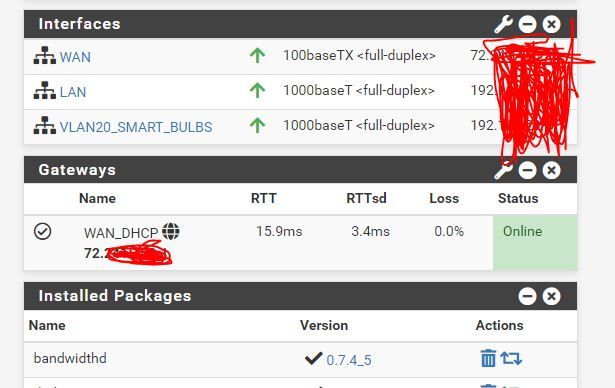
OpenVPN is still not working. The changes I attempted last friday night caused a rukus of issues making my wireless devices disconnect and having me reset everything.
Below are my current settings and the past logs/changes.
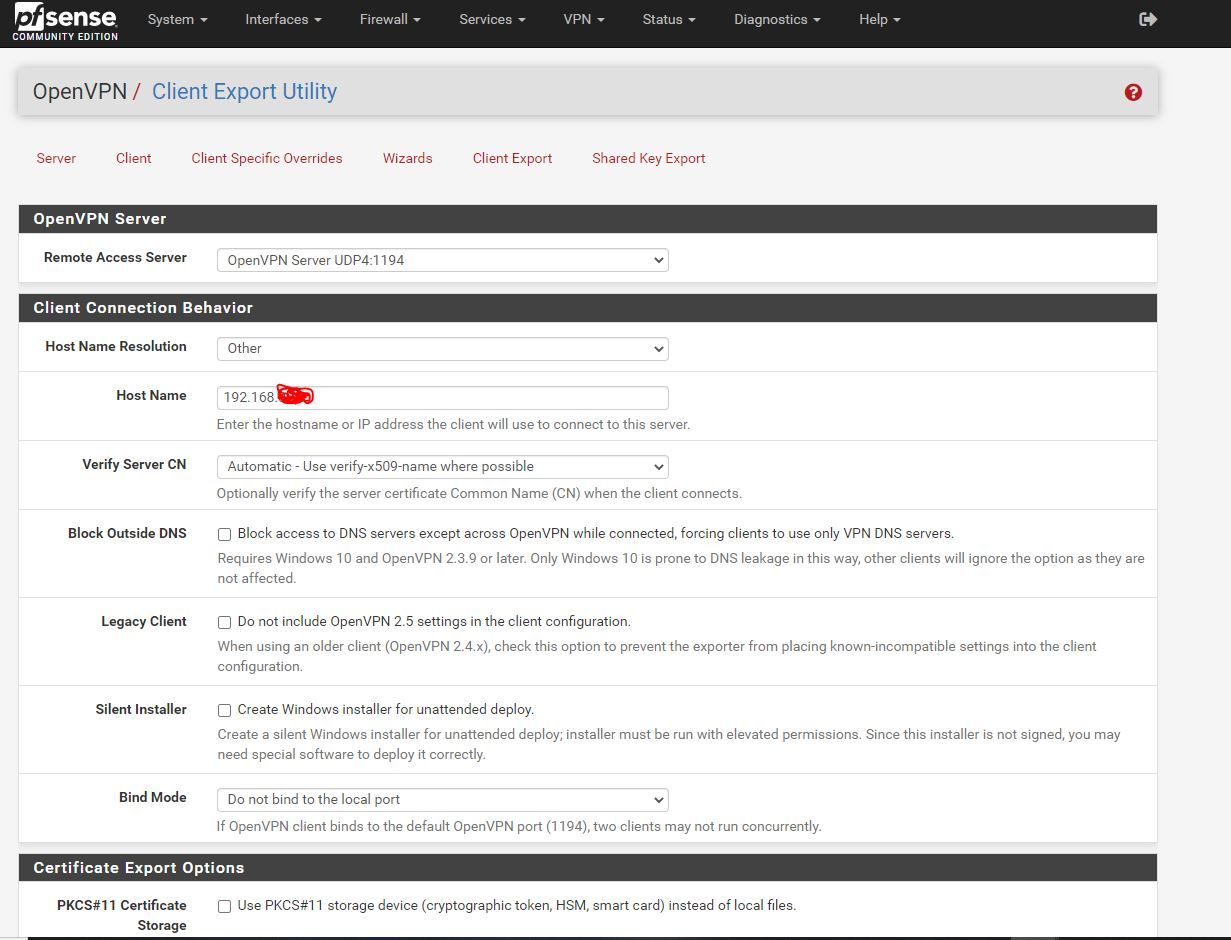
current open vpn settings below:
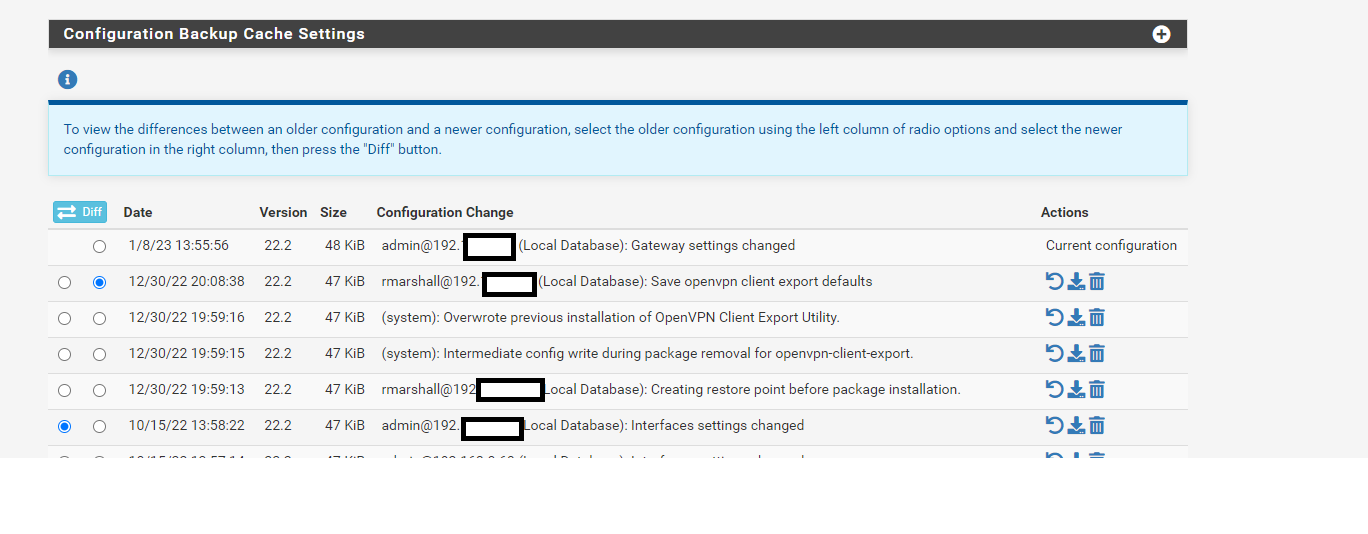
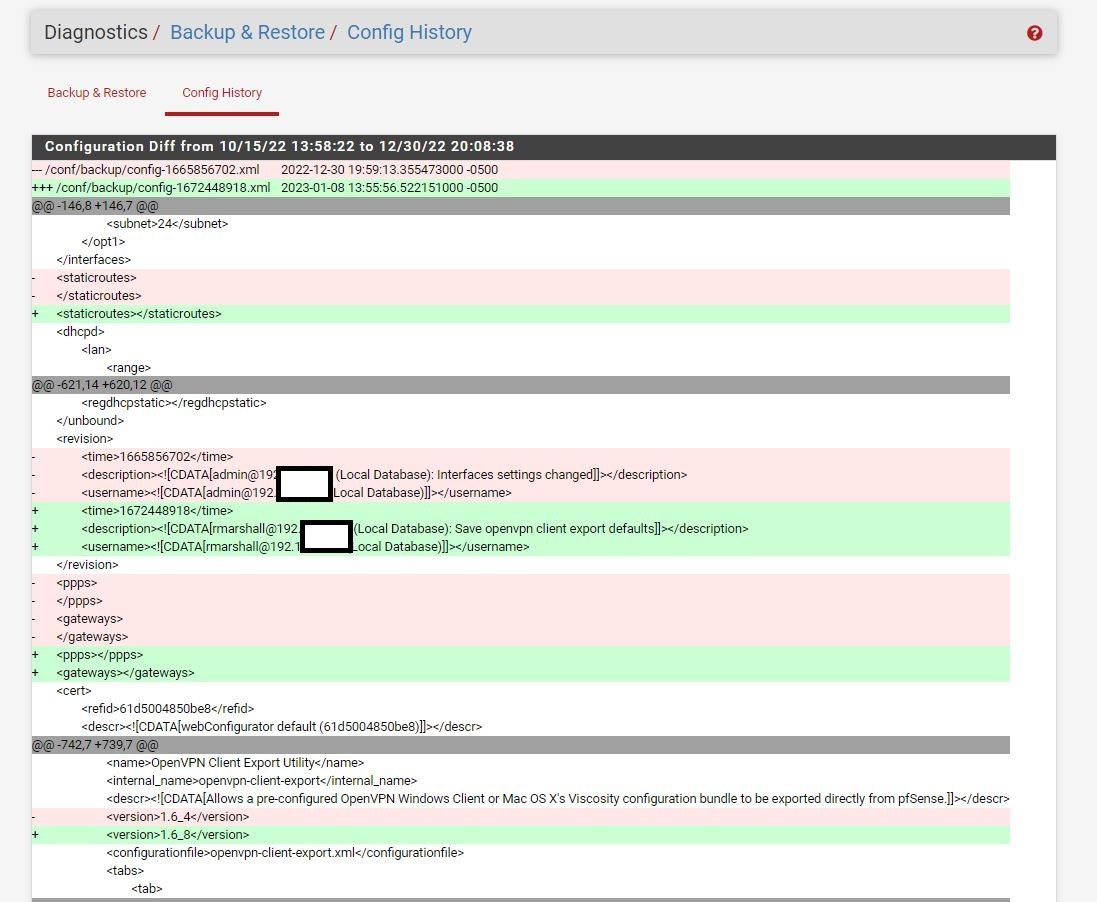
here is the config history. below this screen shot in the nxt 2 pics is the difference of the two radial dialed options selected but idk how to read it.
Currently, the OpenVPN service is not even starting and I dont know if I even want to start it back up.
I am not sure w/the above if i should make any changes to OpenVPN or just delete it completely and start over w/open vpn. I know when i created it, i got it to work and was able to test it back in august i believe it was fine. Then around thanksgiving i realized something was wrong and i couldnt connect using open vpn again so i was attempting to fix it last friday and apparently whatever i did or didn't do made my devices go off line (mentioned in another post, but that issue is now resolved by reconnecting or hard resetting devices).
-
T TravelMore referenced this topic on
-
T TravelMore referenced this topic on
-
Time to look and show the OpenVPN log :
@gertjan said in OpenVPN not connecting:
So : go check the OpenVPN log and see
Also, compare your setup with this video : Configuring OpenVPN Remote Access in pfSense Software
-
@gertjan Thank you for replying. Sorry, its been so long since I've been able to respond but I am now at a point where I can respond and work on this.
Today, before I started making any changes I went back through the settings and an old post (below) of when I originally set this up, to see if everything was still the same or not.
https://forum.netgate.com/topic/174037/openvpn-on-pfsense/18While I was looking at the settings that I currently have and what I had on that post I noticed in VPN, Open VPN, Client Export, the Host Name Resolution drop-down was set to other, whereas in that link the person mentioned changing it to Interface IP address instead of other.
So I changed it to Interface IP address and then downloaded a new config file and uploaded it on a laptop and tried connecting to my home network from a hotspot and I was able to connect w/no issues.So, I think it is safe to say this issue is resolved. As I was going through this I remembered the weird error I stated in this post originally that I had a weird issue where all my devices got kicked off my network one night for some unknown reason and I had to reconnect a good majority of them all back (tv,printer, cameras,a phone (not my phone), speakers, etc.) (like when you buy a new device and bring it home and have to enter in the wifi password for the first time).
To this day I still have no clue what the heck happened or why my network kicked numerous devices offline (which still creeps me out because I think maybe it's a hacker but knowing thats way over thinking about it and it was probably just a fluke thing because nothing else happened/nothing was acting weird before/after/during that aside from just having to connect devices back on the network). -
@travelmore said in OpenVPN not connecting:
to other, whereas in that link the person mentioned changing it to Interface IP address instead of other.
Be careful with this :
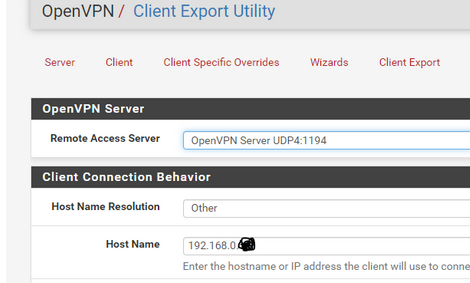
as that a hostname like (RFC1918 like 192.168.0.b) this will be wrong in 99,x % of all cases.
When you are out, somewhere in the wild, surround by the hostile Internet, and you want to connect to 'home' over VPN, you have to connect to your ISP WAN IPv4. Certainly not to your RFC1918 like 192.168.0.x as shown in the image above, which can't be routed over the net.
So : second best choice : the ISP WAN as a host name.
Host name is your tunnel end point, and as the comment says : it could be an IP or a host name. If you shose the latter, it should be resolvable there where you are now. Said differently : it should be resolvable anywhere on the internet.
So : best : set up a DYNDNS so that a known 'hostname' always points to your ISP WAN. This is valid and useful if you have a dynamic IP and/or a static WAN IP.