Add SSL DH Parameters
-
Hi,
I am running HAproxy/ACME on my pfSense box for a while now.
In HAproxy the frontend is set to SSL Offloading on port 443
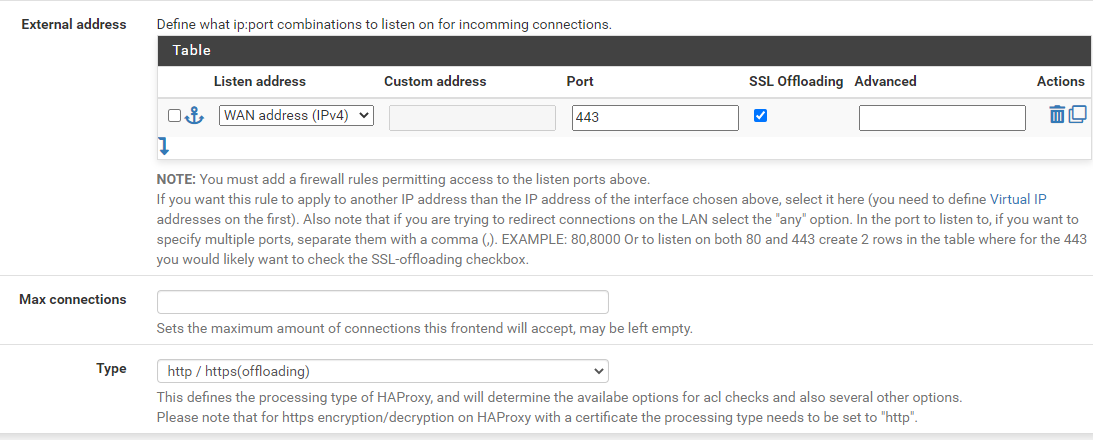
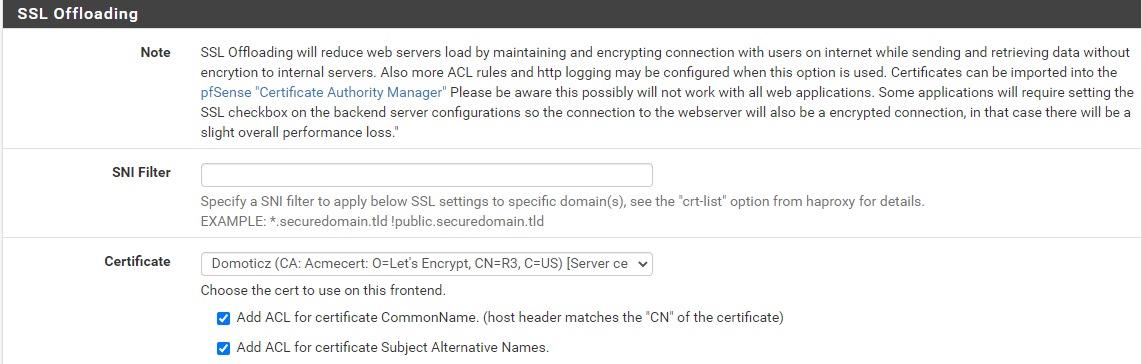
The Backend to the Domoticz (Domotica Software) Webserver is configured like this:
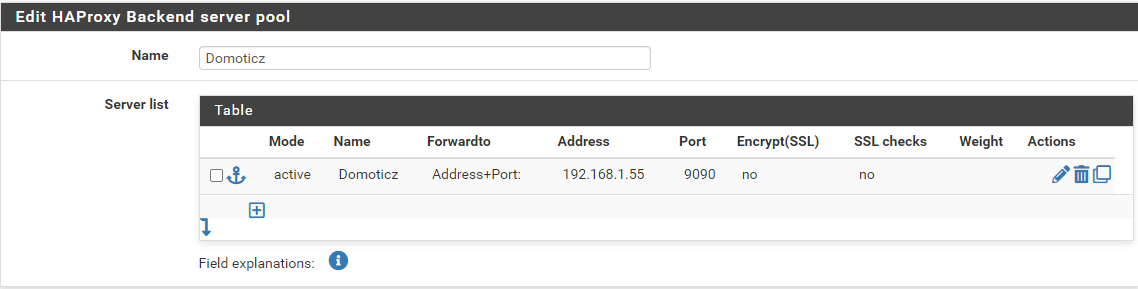
Now last week I had to re-install Domoticz which is domotica software.
Domoticz has a build in webserver which can also be accessed from the outside world. There is a default server_cert.pem file which is used to login secure (to get a login page).Apparently is for Domoticz the HAProxy/ACME my current setup not sufficient (I have the same setup for another webserver and this runs fine with HTTP).
This is because Domoticz needs the local server_cert.pem to get a login page at all.
So I copied the generated PEM file by ACME from my pfSense box (conf/acme/) to the Domoticz directory on my Raspberry pi, and renamed it to server_cert.pem. But when I tested the Domoticz connection I got the following error:
2023-01-03 14:13:20.467 [76f21040] Error: [web:443] missing SSL DH parameters from file ./server_cert.pem 2023-01-03 14:13:20.485 [76f21040] Status: WebServer(SSL) startup failed on address :: with port: 443: bind: Permission denied [system:13], trying :: 2023-01-03 14:13:20.486 [76f21040] Debug: [web:443] Enabled ciphers (TLSv1.2) ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384 2023-01-03 14:13:20.488 [76f21040] Error: [web:443] missing SSL DH parameters from file ./server_cert.pem 2023-01-03 14:13:20.489 [76f21040] Status: WebServer(SSL) startup failed on address :: with port: 443: bind: Permission denied [system:13], trying 0.0.0.0 2023-01-03 14:13:20.490 [76f21040] Debug: [web:443] Enabled ciphers (TLSv1.2) ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384 2023-01-03 14:13:20.493 [76f21040] Error: [web:443] missing SSL DH parameters from file ./server_cert.pem 2023-01-03 14:13:20.494 [76f21040] Error: WebServer(SSL) startup failed on address 0.0.0.0 with port: 443: bind: Permission denied [system:13] 2023-01-03 14:13:20.494 [76f21040] Error: WebServer(SSL) check privileges for opening ports below 1024My question is how can I add "SSL DH parameters" to the PEM file?
-
Well ... ask the :
@gschmidt said in Add SSL DH Parameters:
Domoticz has a build in webserver
For example, with Apache 2.4.x you could add :
SSLOpenSSLConfCmd DHParameters /etc/ssl/dh/RSA4096.pemand all you have to do is generating a 'big' 4096 RSA DH file.
It could be possible to just 'add' this file to the existing "server_cert.pem" file, but again, it depends on the program used.
-----BEGIN DH PARAMETERS----- MIICCAKCAgEAn6LLHESX0I8vuBInxy5jWgrOb48JSOh+sh5xuvSxhY9krevMlMTe R+3qx+0K2Ub17/l3Vm1DT2KNinhlBORnD5RHUEXOquGeq9qFFAuxIv/Q5A1Gtgdy LIHyZBmFqYOQ0LzF5kJ5GvogusWWwYg0jMIhDPW7C+0JGmB6rm0Dm4RJ5a7ona/f ..... cqjepqOH2k55+XQbcICSiIXCI/rRRBgRp8jjO/sI9Bu/h5gN3Mka4PpiLOJNjdqr 2VePTuezInE8OYex7OFbInnZtz2uIoGAWG5F4FNkTtayFsyqLelJ05MCAQI= -----END DH PARAMETERS-----edit : Install Google ! It send me to the domoticz wiki page :
https://www.domoticz.com/wiki/Native_secure_access_with_Lets_Encrypt#Add_the_certificate_to_Domoticz -
the PEM file needs to be renewed, so manually adding the SSL DH parameters would could to update the PEM file each time it is renewed.
This is not desirable -
@gschmidt said in Add SSL DH Parameters:
the PEM file needs to be renewed, so manually adding the SSL DH parameters would could to update the PEM file each time it is renewed.
This is not desirableThat's info for Domoticz.
Btw : I'm using server processes myself that need to have the DH content added to cert.pem file.
As I'm using Letencrypt also, and the 'real' acme.sh' on a debian mail/web server, I coded myself a script that, upon successful cert renewal, executes, and "does what it need to do".The pfsense acme.sh also allow you to do so :
#!/bin/sh set -e if [[ -z "${Le_Domain}" ]]; then Le_Domain=${_main_domain} fi echo $Le_Domain echo $CERT_KEY_PATH echo $CERT_PATH echo $CA_CERT_PATH echo $CERT_FULLCHAIN_PATH check_path="/root/.acme.sh/${Le_Domain}/${Le_Domain}.conf" destination="/etc/ssl/" destinationdir=${destination}${Le_Domain} if [ -f $check_path ]; then if [ ! -d $destinationdir ]; then mkdir $destinationdir fi # Note : $CERT_KEY_PATH is needed here as courier-(pop/imap)-ssl have to find all in one pem file # cat $CERT_KEY_PATH $CERT_FULLCHAIN_PATH ${destination}dh/RSA4096.pem > ${destinationdir}/${Le_Domain}.pem cat $CERT_KEY_PATH $CERT_FULLCHAIN_PATH > ${destinationdir}/${Le_Domain}.pem cp $CERT_KEY_PATH ${destinationdir}/${Le_Domain}.key chmod 400 ${destinationdir}/${Le_Domain}.pem chmod 400 ${destinationdir}/${Le_Domain}.key chown courier ${destinationdir}/${Le_Domain}.pem service apache2 reload >/dev/null service postfix reload >/dev/null # courier will also use these certs. service courier-pop-ssl force-reload >/dev/null service courier-imap-ssl force-reload >/dev/null # exception - extra treatment : if [ "$Le_Domain" == "monit.one-of-my-own-domains.tld" ]; then service monit reload >/dev/null service webmin restart >/dev/null fi ACCOUNT_EMAIL=my@gmail.com cat <<-EOF | mail -r acme@one-of-my-own-domains.tld -s "Certificates renewed" $ACCOUNT_EMAIL Renewed the following certificate(s): Host: $Le_Domain $(/root/.acme.sh/acme.sh --version 2>&1) EOF fiYou can use this script to 'coook' something for yourself.
There is a commented line that shows where I 'cat' the RSA4096 DH file to the cert.pem file.
File paths have to be changed of course, as they are different on pfSense.
With this option set :
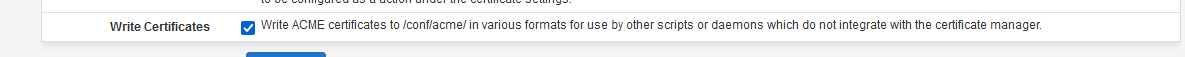
you can find the latest cert version in a known place.
Btw : some more investigation will be needed, as : where does the HA proxy startup code gets the cert info from when preparing for a HA Proxy start ?
In the past, the trick of modifying the main 'cert.pem' was used by many processes, but these days, as my apache2 example, it has become a separate setting in a config file.
I hope "Domoticz" will also adopt that method.
See the wiki page again : Domoticz has its own deploy script : you can also use that one as an example. -
@gertjan said in Add SSL DH Parameters:
You can use this script to 'coook' something for yourself.
There is a commented line that shows where I 'cat' the RSA4096 DH file to the cert.pem file.
you can find the latest cert version in a known place.Btw : some more investigation will be needed, as : where does the HA proxy startup code gets the cert info from when preparing for a HA Proxy start ?
In the past, the trick of modifying the main 'cert.pem' was used by many processes, but these days, as my apache2 example, it has become a separate setting in a config file.
I hope "Domoticz" will also adopt that method.
See the wiki page again : Domoticz has its own deploy script : you can also use that one as an example.Thanx for the example man, very interesting!
Sadly my linux skills are like "trial and error" ;-)
Especially (secured) SSL is quite difficult to understandDomoticz has a build-in HTTP (9090) and HTTPS (443) server and also the possibilty to pass the login inside the local network with an option in the settings: 192.168.1.*.
This allows all computers inside the local network, starting with this ip address, to pass the login of domoticz.
The problem with this login pass option is that also the outside world doesn't have to login because of the HTTP connection in the backend of HAproxy. Therfore I currently did not set this option to protect the webapplication.On the other hand the advantage of the current configuration allows me to turn off the HTTPS 443 ssl connection in the startup file of domoticz (I just figured out). This way I don't get certificate and https errors in domoticz anymore because everything is handled by the HAproxy server and ACME
I have to think about it, thanx anyway for the info!