How stable is OpenVPN?
-
@dominikhoffmann said in How stable is OpenVPN?:
I restarted the OpenVPN service (Status → OpenVPN), I was able to VPN in again.
Somewhere I saw something about a Watchdog daemon. Does the SG-2100 have that capability?
Was the service stopped?
In your case, with an access server, Watchdog can only monitor the service and restart it if it's not running.
-
Currently running it on a 6100 with 22.05 release.
You have some important questions to answer namely was the service stopped when you discovered the problem? What does the system logs show? Was the service running when you noticed the problem? Any logged in users? What does the system logs show? -
@dominikhoffmann said in How stable is OpenVPN?:
How stable is OpenVPN on pfSense+ (22.05-RELEASE [arm64]) currently?
I've had the same question a couple of month ago.
I know the pfSense OpenVPN server is ok, as I'm using it since day one : that's now a bit over 10 years. Note that I'm using it to remote admin pfSense, or gain access to my 'work' LAN so I can access security camera's, or fool around with the airco.
I never use it with "x" users that needed to work from home.I've been paying a commercial VPN service (XpressVPN for not to name the brand) for years, just to play with it. I never had to need use a VPN to change fixed ISP IPv4.
But I was asking to myself lately : why not route my captive portals users over the VPN client out the VPN ISP ? This way, my clients can not 'taint' my IPv4, because, after all, I am still responsible for whatever comes in and goes out of my IPv4.
So, I decided to really test XpressVPN, and I set up a VPN client also on pfSense.
I policy routed with an alias all captive portal clients out over the VPN client interface. I don't have to use this :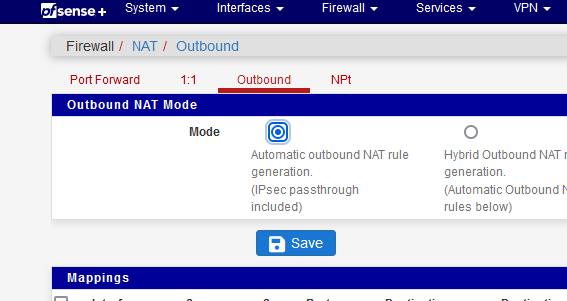
And guess what : the OpenVPN is up and running for 2 months now.
Bandwidth is ok, as my ADSL only gives me 24 Mbits down 2 Mbits up (2 Gbit fiber is coming next week - we'll see what happens then)
I know my clients do have some "web browse issues" as not every internet host plays well when it discovers a VPN IP is in use, but I didn't hear real complaints.I start to think this OpenVPN client is also rock solid.
Still, the ISP up-link quality is important here.
The VPN ISP quality is important also, as they are not all equal, except for the fact that they all manage to debit your credit card into perfection.Also : if you've been watching TV for the last 2 years or so, did you notice that half the planet was 'working from home' ?
So, employees used their equipment from home to connect to the company to continue working.
The software used was mostly : OpenVPN. So, if it could drive the planet, I guess it's pretty good.On the other hand, it is still 'close to rocket science' to set it up, as it includes the concept of server and client, and you only control well one side **. When working with stuff like, OpenVPN, you really start to abandon the pfSense Dashboard, when you login, you go straight to the main log menu, and that's where you are looking all day because that's the system's most important page.
** except when you set up a system where pfSense is the OpenVPN server : you can see the logs of both the server and client and test everything into perfection.
-
@maxk-0: The logs are empty between December 24 and January 3, when I restarted the OpenVPN process:
Dec 24 05:14:57 openvpn 62444 UDPv4 link local (bound): [AF_INET]192.168.1.250:1194 Dec 24 05:14:57 openvpn 62444 UDPv4 link remote: [AF_UNSPEC] Dec 24 05:14:57 openvpn 62444 Initialization Sequence Completed Jan 3 13:26:15 openvpn 62444 event_wait : Interrupted system call (fd=-1,code=4) Jan 3 13:26:17 openvpn 62444 /usr/local/sbin/ovpn-linkdown ovpns1 1500 0 192.168.18.1 255.255.255.0 init Jan 3 13:26:17 openvpn 62444 SIGTERM[hard,] received, process exiting Jan 3 13:26:18 openvpn 19435 OpenVPN 2.6_git aarch64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] [DCO] built on Sep 8 2022 -
@viragomann: It looked like it was stopped, but the first three log entries on January 3 have the same PID as the entries on New Year’s Eve and before had.
-
@michmoor said in How stable is OpenVPN?:
Any logged in users? What does the system logs show?
I am the only user using it, currently.
-
@gertjan said in How stable is OpenVPN?:
But I was asking to myself lately : why not route my captive portals users over the VPN client out the VPN ISP ? This way, my clients can not 'taint' my IPv4, because, after all, I am still responsible for whatever comes in and goes out of my IPv4.
Hmm..This is a good idea.
-
-
@Gertjan I had an existing 3rd party VPN operating so what the heck...switched over my Guest VLAN.
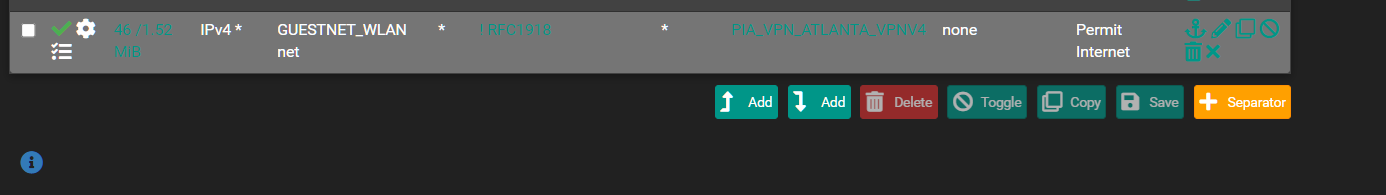
-
@dominikhoffmann We were discussing something different than the OpenVPN crashing issue.
What we are talking about is policy routing.
Our PFsense firewall is an OpenVPN client to a OpenVPN server (Nordvpn or PIA or insert 3rd party].
As that OpenVPN server is now enabled as a gateway, we can direct clients to that gateway via firewall rules , aka, policy routing.
So now users on our LAN or GuestNet or whichever interface will be routed out the OpenVPN connection. Any user that goes against our network policy will only be hurting the IP reputation of the VPN provider and leaving our IP that we own (or assigned to us) alone.
Its really not a bad idea. -
@michmoor: I get it now
Is there a tutorial somewhere, that you know of, that you would recommend, on how to set up a pfSense box as an OpenVPN client?
-
@dominikhoffmann said in How stable is OpenVPN?:
pfSense box as an OpenVPN client?
To where? Pretty much every vpn service has some "guide" on how to connect to their service - most of them have a section for pfsense.
-
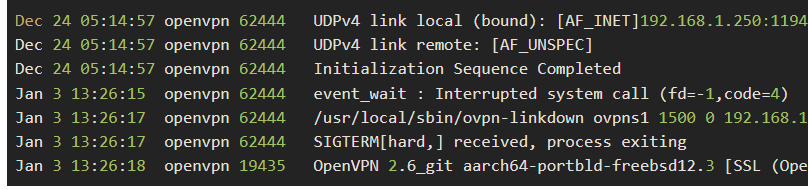
Not crashing.
62444 was signaled to stop. For the usual reasons like : an interface (WAN ?) went down.
I agree : it should restart when the that interface came back.edit : to see what happened, look in the main system log for events at that moment.
-
@gertjan said in How stable is OpenVPN?:
Not crashing.
62444 was signaled to stop.Correct! That was, when I restarted the service.
-
@dominikhoffmann
Ah, ok, so the openvpn server 62444 stayed silent - no log lines since last 24 December.
Do you have enforced your openvpn server vpn rule, like not using port 1194, or limited to a known list op source IPs ?
Normally, for a openvpn server, you would see ones in a while some log lines because your openvpn is "scanned". A bit scary at first, but actually quiet handy as you could see these tests as a sort of 'I'm still alive' tests.
Or, true : openvpn was running but not listening anymore, which is close to a dead process. -
@gertjan said in How stable is OpenVPN?:
Do you have enforced your openvpn server vpn rule, like not using port 1194, or limited to a known list op source IPs ?
The firewall rule is the default one generated by the setup wizard:
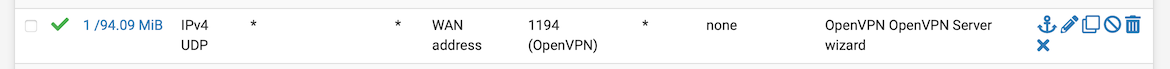
So, the answer is, no.
-
It went down again in the last couple of days. The OpenVPN logs did not show anything. Is there anything else I should check for?
-
D DominikHoffmann referenced this topic on
-
D DominikHoffmann referenced this topic on
-
When you try to connect with an external client do you see states created on the WANfor the incoming connection attempts?
I'm not aware of any issue in OpenVPN itself that behaves like that.
Steve
-
@stephenw10: I am not familiar with what states are and what that list would signify.
Do you mean entries like these:
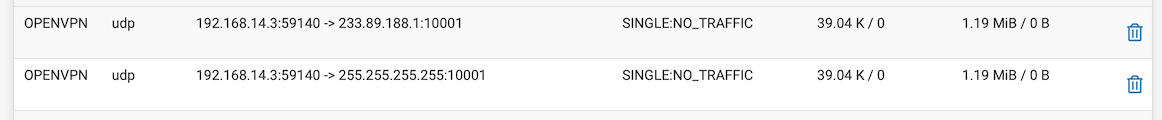
I don’t believe that there were any entries in the states table showing evidence of my failed attempts to connect to the OpenVPN server, before I restarted the service. However, I will need to verify this, when I encounter it being down the next time.
-
Nope, those are states on the OpenVPN interface, so inside the tunnel. What I would expect to see are states on the WAN on whatever port you're running OpenVPN on, UDP 1194 by default.
If you don't see those states then the VPN traffic from the clients is not arriving which would explain why there are no logs for connection attempts.