pfSense Blocking Roborock app
-
@bmeeks Hey No problem I will keep plugging away at anything I can think of or read on. I really appreciate your help on this for sure. I just cant conceive of any issue that would cause this at all. Its well beyond my limited knowledge of home networking for sure.
-
@bmeeks Just so we have it here is the package capture with full detail when trying to log into the app for only my phone IP
14:04:17.884291 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 106: (tos 0x0, ttl 64, id 56173, offset 0, flags [none], proto UDP (17), length 92) 192.168.1.245.62132 > 192.168.1.1.53: [udp sum ok] 64387+ Type65? api-slb-1106974124.us-east-1.elb.amazonaws.com. (64) 14:04:17.885232 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 106: (tos 0x0, ttl 64, id 38167, offset 0, flags [none], proto UDP (17), length 92) 192.168.1.245.61663 > 192.168.1.1.53: [udp sum ok] 12878+ A? api-slb-1106974124.us-east-1.elb.amazonaws.com. (64) 14:04:17.964276 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 202: (tos 0x0, ttl 64, id 38567, offset 0, flags [none], proto UDP (17), length 188) 192.168.1.1.53 > 192.168.1.245.61663: [udp sum ok] 12878 q: A? api-slb-1106974124.us-east-1.elb.amazonaws.com. 6/0/0 api-slb-1106974124.us-east-1.elb.amazonaws.com. A 54.91.129.233, api-slb-1106974124.us-east-1.elb.amazonaws.com. A 44.199.12.174, api-slb-1106974124.us-east-1.elb.amazonaws.com. A 52.44.149.220, api-slb-1106974124.us-east-1.elb.amazonaws.com. A 52.22.51.41, api-slb-1106974124.us-east-1.elb.amazonaws.com. A 34.192.137.33, api-slb-1106974124.us-east-1.elb.amazonaws.com. A 52.20.64.186 (160) 14:04:17.969458 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x8868 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160136033 ecr 0,sackOK,eol], length 0 14:04:17.987740 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 188: (tos 0x0, ttl 64, id 45996, offset 0, flags [none], proto UDP (17), length 174) 192.168.1.1.53 > 192.168.1.245.62132: [udp sum ok] 64387 q: Type65? api-slb-1106974124.us-east-1.elb.amazonaws.com. 0/1/0 ns: us-east-1.elb.amazonaws.com. SOA ns-1119.awsdns-11.org. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 60 (146) 14:04:18.947754 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x847c (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160137037 ecr 0,sackOK,eol], length 0 14:04:19.950539 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x8094 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160138037 ecr 0,sackOK,eol], length 0 14:04:19.950560 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x7fc2 (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914208927 ecr 0,sackOK,eol], length 0 14:04:20.953663 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x7bd6 (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914209931 ecr 0,sackOK,eol], length 0 14:04:20.954454 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x7ca8 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160139041 ecr 0,sackOK,eol], length 0 14:04:21.951029 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x7fa2 (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488740973 ecr 0,sackOK,eol], length 0 14:04:21.952962 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x78bf (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160140042 ecr 0,sackOK,eol], length 0 14:04:21.952981 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x77ed (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914210932 ecr 0,sackOK,eol], length 0 14:04:22.960759 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x7bb5 (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488741978 ecr 0,sackOK,eol], length 0 14:04:23.008603 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x74d4 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160141045 ecr 0,sackOK,eol], length 0 14:04:23.008627 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x7402 (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914211935 ecr 0,sackOK,eol], length 0 14:04:23.968055 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x7018 (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914212937 ecr 0,sackOK,eol], length 0 14:04:23.968057 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xde5c (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621493416 ecr 0,sackOK,eol], length 0 14:04:23.968059 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x77cb (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488742980 ecr 0,sackOK,eol], length 0 14:04:24.965452 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x6d02 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160143047 ecr 0,sackOK,eol], length 0 14:04:24.965454 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x73e3 (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488743980 ecr 0,sackOK,eol], length 0 14:04:24.965454 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xda74 (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621494416 ecr 0,sackOK,eol], length 0 14:04:24.965475 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x6c30 (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914213937 ecr 0,sackOK,eol], length 0 14:04:25.967205 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x6ff6 (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488744985 ecr 0,sackOK,eol], length 0 14:04:25.967207 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xd687 (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621495421 ecr 0,sackOK,eol], length 0 14:04:25.968328 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xf5d4 (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458830294 ecr 0,sackOK,eol], length 0 14:04:26.958670 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x645f (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914215938 ecr 0,sackOK,eol], length 0 14:04:26.967270 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xf1eb (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458831295 ecr 0,sackOK,eol], length 0 14:04:26.967273 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xd29f (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621496421 ecr 0,sackOK,eol], length 0 14:04:26.967278 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x6c0e (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488745985 ecr 0,sackOK,eol], length 0 14:04:28.026426 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xceb4 (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621497424 ecr 0,sackOK,eol], length 0 14:04:28.026429 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x693a (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332711101 ecr 0,sackOK,eol], length 0 14:04:28.026432 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 76) 192.168.1.245.62072 > 17.253.7.205.443: Flags [P.], cksum 0xcb8b (correct), seq 3038464547:3038464571, ack 3982235061, win 2048, options [nop,nop,TS val 2969241129 ecr 646053392], length 24 14:04:28.026461 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 192.168.1.245.62072 > 17.253.7.205.443: Flags [F.], cksum 0xc001 (correct), seq 24, ack 1, win 2048, options [nop,nop,TS val 2969241129 ecr 646053392], length 0 14:04:28.026473 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xee03 (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458832295 ecr 0,sackOK,eol], length 0 14:04:28.066810 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 55, id 24693, offset 0, flags [DF], proto TCP (6), length 64) 17.253.7.205.443 > 192.168.1.245.62072: Flags [.], cksum 0xacc9 (correct), seq 1, ack 0, win 252, options [nop,nop,TS val 646076778 ecr 2969210974,nop,nop,sack 1 {24:25}], length 0 14:04:28.066817 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 55, id 24694, offset 0, flags [DF], proto TCP (6), length 52) 17.253.7.205.443 > 192.168.1.245.62072: Flags [.], cksum 0x6bab (correct), seq 1, ack 25, win 252, options [nop,nop,TS val 646076778 ecr 2969241129], length 0 14:04:28.067431 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 55, id 24695, offset 0, flags [DF], proto TCP (6), length 52) 17.253.7.205.443 > 192.168.1.245.62072: Flags [F.], cksum 0x6baa (correct), seq 1, ack 25, win 252, options [nop,nop,TS val 646076778 ecr 2969241129], length 0 14:04:28.163295 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 76) 192.168.1.245.62072 > 17.253.7.205.443: Flags [FP.], cksum 0x6f74 (correct), seq 0:24, ack 1, win 2048, options [nop,nop,TS val 2969241317 ecr 646076778], length 24 14:04:28.163318 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 192.168.1.245.62072 > 17.253.7.205.443: Flags [.], cksum 0x63ea (correct), seq 25, ack 2, win 2048, options [nop,nop,TS val 2969241317 ecr 646076778], length 0 14:04:28.958647 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62073 > 44.199.12.174.443: Flags [S], cksum 0x5d61 (correct), seq 3373424508, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 3160147048 ecr 0,sackOK,eol], length 0 14:04:28.963121 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x643e (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488747985 ecr 0,sackOK,eol], length 0 14:04:28.967073 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xcacb (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621498425 ecr 0,sackOK,eol], length 0 14:04:28.967075 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xea1a (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458833296 ecr 0,sackOK,eol], length 0 14:04:28.969766 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x6551 (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332712102 ecr 0,sackOK,eol], length 0 14:04:29.977014 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x6167 (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332713104 ecr 0,sackOK,eol], length 0 14:04:29.977034 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xe62d (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458834301 ecr 0,sackOK,eol], length 0 14:04:30.966164 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62074 > 54.91.129.233.443: Flags [S], cksum 0x54bc (correct), seq 1033444204, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 914219941 ecr 0,sackOK,eol], length 0 14:04:30.969138 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62076 > 52.22.51.41.443: Flags [S], cksum 0xc2fa (correct), seq 2443986731, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 621500426 ecr 0,sackOK,eol], length 0 14:04:30.973274 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xe244 (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458835302 ecr 0,sackOK,eol], length 0 14:04:30.973296 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x5d7e (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332714105 ecr 0,sackOK,eol], length 0 14:04:31.895547 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 105: (tos 0x0, ttl 233, id 23671, offset 0, flags [DF], proto TCP (6), length 91) 3.142.229.116.443 > 192.168.1.245.62042: Flags [P.], cksum 0xf3f6 (correct), seq 2959089295:2959089334, ack 838566967, win 477, options [nop,nop,TS val 487961176 ecr 3140854179], length 39 14:04:31.986202 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x5991 (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332715110 ecr 0,sackOK,eol], length 0 14:04:32.195900 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 105: (tos 0x0, ttl 233, id 23672, offset 0, flags [DF], proto TCP (6), length 91) 3.142.229.116.443 > 192.168.1.245.62042: Flags [P.], cksum 0xf2ca (correct), seq 0:39, ack 1, win 477, options [nop,nop,TS val 487961476 ecr 3140854179], length 39 14:04:32.483928 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 105: (tos 0x0, ttl 233, id 23673, offset 0, flags [DF], proto TCP (6), length 91) 3.142.229.116.443 > 192.168.1.245.62042: Flags [P.], cksum 0xf1aa (correct), seq 0:39, ack 1, win 477, options [nop,nop,TS val 487961764 ecr 3140854179], length 39 14:04:32.590838 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 192.168.1.245.62042 > 3.142.229.116.443: Flags [.], cksum 0x5a9b (correct), seq 1, ack 39, win 2047, options [nop,nop,TS val 3141034833 ecr 487961476], length 0 14:04:32.601283 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 105: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 91) 192.168.1.245.62042 > 3.142.229.116.443: Flags [P.], cksum 0x21b2 (correct), seq 1:40, ack 39, win 2048, options [nop,nop,TS val 3141034833 ecr 487961476], length 39 14:04:32.601306 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 76) 192.168.1.245.62042 > 3.142.229.116.443: Flags [P.], cksum 0x3aea (correct), seq 40:64, ack 39, win 2048, options [nop,nop,TS val 3141034834 ecr 487961476], length 24 14:04:32.601309 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 192.168.1.245.62042 > 3.142.229.116.443: Flags [F.], cksum 0x5a59 (correct), seq 64, ack 39, win 2048, options [nop,nop,TS val 3141034834 ecr 487961476], length 0 14:04:32.626901 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62042 > 3.142.229.116.443: Flags [F.], cksum 0x8504 (correct), seq 64, ack 39, win 2048, options [nop,nop,TS val 3141034857 ecr 487961764,nop,nop,sack 1 {0:39}], length 0 14:04:32.637635 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 233, id 23674, offset 0, flags [DF], proto TCP (6), length 64) 3.142.229.116.443 > 192.168.1.245.62042: Flags [.], cksum 0xbc07 (correct), seq 39, ack 1, win 477, options [nop,nop,TS val 487961918 ecr 3141034833,nop,nop,sack 1 {64:65}], length 0 14:04:32.637641 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 233, id 23675, offset 0, flags [DF], proto TCP (6), length 64) 3.142.229.116.443 > 192.168.1.245.62042: Flags [.], cksum 0xbbe0 (correct), seq 39, ack 40, win 477, options [nop,nop,TS val 487961918 ecr 3141034833,nop,nop,sack 1 {64:65}], length 0 14:04:32.637644 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 233, id 23676, offset 0, flags [DF], proto TCP (6), length 52) 3.142.229.116.443 > 192.168.1.245.62042: Flags [.], cksum 0x5ec2 (correct), seq 39, ack 65, win 477, options [nop,nop,TS val 487961918 ecr 3141034834], length 0 14:04:32.637647 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 233, id 23677, offset 0, flags [DF], proto TCP (6), length 76) 3.142.229.116.443 > 192.168.1.245.62042: Flags [P.], cksum 0xfa1e (correct), seq 39:63, ack 65, win 477, options [nop,nop,TS val 487961918 ecr 3141034834], length 24 14:04:32.637650 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 233, id 23678, offset 0, flags [DF], proto TCP (6), length 52) 3.142.229.116.443 > 192.168.1.245.62042: Flags [F.], cksum 0x5ea9 (correct), seq 63, ack 65, win 477, options [nop,nop,TS val 487961918 ecr 3141034834], length 0 14:04:32.652089 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 129: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 115) 192.168.1.245.62042 > 3.142.229.116.443: Flags [FP.], cksum 0xb778 (correct), seq 1:64, ack 39, win 2048, options [nop,nop,TS val 3141034904 ecr 487961918], length 63 14:04:32.652109 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40) 192.168.1.245.62042 > 3.142.229.116.443: Flags [R], cksum 0x59b8 (correct), seq 838567031, win 0, length 0 14:04:32.652112 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40) 192.168.1.245.62042 > 3.142.229.116.443: Flags [R], cksum 0x59b8 (correct), seq 838567031, win 0, length 0 14:04:32.663468 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 233, id 23679, offset 0, flags [DF], proto TCP (6), length 64) 3.142.229.116.443 > 192.168.1.245.62042: Flags [.], cksum 0xbb7d (correct), seq 64, ack 65, win 477, options [nop,nop,TS val 487961943 ecr 3141034857,nop,nop,sack 1 {64:65}], length 0 14:04:32.687222 a0:36:9f:8c:00:de > 2a:87:3e:21:c1:b4, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 233, id 0, offset 0, flags [DF], proto TCP (6), length 40) 3.142.229.116.443 > 192.168.1.245.62042: Flags [R], cksum 0x4177 (correct), seq 2959089334, win 0, length 0 14:04:32.752081 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40) 192.168.1.245.62042 > 3.142.229.116.443: Flags [R], cksum 0x59b8 (correct), seq 838567031, win 0, length 0 14:04:33.056290 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62079 > 52.20.64.186.443: Flags [S], cksum 0x55a9 (correct), seq 3857833468, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1332716110 ecr 0,sackOK,eol], length 0 14:04:33.056296 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62075 > 52.44.149.220.443: Flags [S], cksum 0x549a (correct), seq 22052766, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488751989 ecr 0,sackOK,eol], length 0 14:04:33.056314 2a:87:3e:21:c1:b4 > a0:36:9f:8c:00:de, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64) 192.168.1.245.62077 > 34.192.137.33.443: Flags [S], cksum 0xda74 (correct), seq 1300251584, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 458837302 ecr 0,sackOK,eol], length 0 -
Just cause I downloaded OPNsense to test and see if I got different results. Shocker OPNsense behaved the exact same way as pfsense so no change in firewall behavior. I reloaded pfsense and will continue banging my head against this brick wall. I reached out to roborock support just to see if they knew anything and of course they just told me that to use their products I must disable my firewall completely. Guy had absolutely no idea how things work so that’s basically a dead end.
-
Very strange if pfSense and OPNsense both exhibit the same behavior and only the Netgear router works. I would say that somewhat vindicates the FreeBSD-based firewall (pfSense and OPNsense).
I would concentrate my efforts on seeing what is possibly different in the configuration now of the Netgear versus the two FreeBSD-based firewalls. Logic and the process of elimination kind of now points to something being configured differently somehow. In an earlier post you mentioned a way to "bypass" the pfSense firewall by using the wireless on the Netgear. Are you 100% sure your vacuum and/or phone app are not trying to use the Netgear's wireless, and so when the Netgear is out of the picture they see no network? From the description you have provided, that would be where I would start looking. I would make sure without a shadow of a doubt that the vacuum and your phone app were both using the UniFi AP both when using the Netgear router and when pfSense is in the loop. The fact your Netgear likely has a available Wi-Fi network that may be enabled makes a sort of "bypass" pathway conceivable. And when the Netgear was unhooked, the "bypass" Wi-Fi pathway would be missing for the vacuum and/or the phone app.
-
@kahodges1721 said in pfSense Blocking Roborock app:
package capture with full detail
Full detail is only so helpful; you could have done with just regular detail for visibility. For next time :)
-
@bmeeks sorry I should have been more clear. When I say bypass I mean I took pfsense out of the loop. Exactly how the network diagram shows above. The WiFi for the NETGEAR was disabled so no chance of bypassing the APs but I agree it makes sense. Unfortunately that wasn’t the case here. The biggest red flag to me is that nothing changed in my setup except a possible update to the app. I won’t pretend to know how it all works but if the update brought a change to the server settings on their end I’m curious if I make a pfsense machine and take it to a buddies house and hook it up if I get the same results.
While you were out I did try to get fancy with it and connected the NETGEAR after the pfsense in the chain. Added some port forward rules for the router activated the WiFi on the NETGEAR and nothing still same result. I expected that but I think I’ve reached the point where I just am out of things to try. I even started just going through all the documentation and trying random settings just to see what would happen haha.
-
@rcoleman-netgate understood! My bad! Luckily this is my first time this deep into the logs to solve a problem!
-
@kahodges1721:
I am rapidly running out of ideas. I'm not there actually touching the firewall nor able to see all the configuration, but if you say that other devices plugged into the network switch shown in your diagrams work fine through pfSense, and if your phone- when connected through the UniFi AP shown in your diagram- can surf the web and connect to social media sites with pfSense in the path, then all of that together indicates the firewall configuration is fine.Things that the scenario I described validate are:
- DHCP scope is correct and clients are getting the proper subnet mask and gateway
- DNS Resolver is up and running and properly resolving hostnames to IP addresses
- The default firewall rules are in place that allow LAN clients to go anywhere.
Is there any other software method available besides a phone app? Is there something you could download and install on a Windows PC or a Mac. That would take the phone app out of the picture.
-
@bmeeks This gave me a new idea. With Home assistant I can run the integration for the roborock. This asks for the app credentials. I would assume it's making the same "call home". The home assistant is running on a VM and is part of my unraid server. The unraid server itself has an IP of .235 while the Home assistant VM is .238. I ran the integration while doing a packet capture. Ill put the results below. This has the same failure but could possible be compared to the iPhone packet capture to narrow things down a little. For reference the path of the Unraid PC is Modem -> pfSense -> 24port Switch -> UnraidPC -> VM instance of Home assistant. Ill also attached a screenshot showing all the other connected devices working except Roborocks failure. There seems to be a ton of back and forth between 192.168.1.1 and the HA instance at .238 not sure what this indicates
08:44:11.110372 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 0 08:44:11.110374 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 95 08:44:11.110379 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 0 08:44:11.110379 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 98 08:44:11.110383 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 0 08:44:11.110509 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 76 08:44:11.110514 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 0 08:44:11.110732 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 1460 08:44:11.110840 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 963 08:44:11.110903 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 372 08:44:11.111067 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 0 08:44:11.111071 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 0 08:44:11.111282 IP 192.168.1.1.443 > 192.168.1.50.57565: tcp 1460 08:44:11.111491 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 0 08:44:11.111602 IP 192.168.1.50.57565 > 192.168.1.1.443: tcp 0 08:44:11.260634 IP 35.213.232.93.443 > 192.168.1.50.57519: tcp 0 08:44:11.260786 IP 192.168.1.50.57519 > 35.213.232.93.443: tcp 0 08:44:11.281915 IP 192.168.1.108.44715 > 44.195.125.201.443: tcp 33 08:44:11.307143 IP 44.195.125.201.443 > 192.168.1.108.44715: tcp 31 08:44:11.310780 IP 192.168.1.108.44715 > 44.195.125.201.443: tcp 0 08:44:11.440024 IP 192.168.1.235.59185 > 239.255.255.250.1900: UDP, length 101 08:44:11.452702 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 0 08:44:11.452704 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 0 08:44:11.452763 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 0 08:44:11.452770 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 0 08:44:11.452783 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 0 08:44:11.452784 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 0 08:44:11.452802 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 0 08:44:11.452803 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 0 08:44:11.452808 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 0 08:44:11.452819 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 0 08:44:11.452948 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 0 08:44:11.452997 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 0 08:44:11.453032 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 0 08:44:11.453033 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 0 08:44:11.453040 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 0 08:44:11.453061 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 0 08:44:11.453089 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 0 08:44:11.453388 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 0 08:44:11.453533 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 315 08:44:11.453546 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 0 08:44:11.453622 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 313 08:44:11.453629 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 0 08:44:11.453764 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 284 08:44:11.453765 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 317 08:44:11.453771 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 0 08:44:11.453778 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 0 08:44:11.453805 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 288 08:44:11.453811 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 0 08:44:11.453840 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 319 08:44:11.453848 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 0 08:44:11.453860 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 512 08:44:11.453868 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 0 08:44:11.453889 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 298 08:44:11.453897 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 0 08:44:11.453907 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 518 08:44:11.453912 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 0 08:44:11.453966 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 296 08:44:11.453972 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 0 08:44:11.454002 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 534 08:44:11.454007 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 0 08:44:11.454013 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 292 08:44:11.454017 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 0 08:44:11.454017 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 267 08:44:11.454020 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 0 08:44:11.454033 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 0 08:44:11.454100 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 586 08:44:11.454107 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 305 08:44:11.454108 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 0 08:44:11.454115 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 0 08:44:11.454116 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 281 08:44:11.454119 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 0 08:44:11.454122 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 0 08:44:11.454147 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 529 08:44:11.454152 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 0 08:44:11.454192 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 520 08:44:11.454196 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 0 08:44:11.454234 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 0 08:44:11.454371 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 0 08:44:11.454389 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 0 08:44:11.454392 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 0 08:44:11.454497 IP 192.168.1.238.46156 > 192.168.1.1.2189: tcp 0 08:44:11.454510 IP 192.168.1.1.2189 > 192.168.1.238.46156: tcp 0 08:44:11.454900 IP 192.168.1.238.46140 > 192.168.1.1.2189: tcp 0 08:44:11.454901 IP 192.168.1.238.46154 > 192.168.1.1.2189: tcp 0 08:44:11.454909 IP 192.168.1.1.2189 > 192.168.1.238.46140: tcp 0 08:44:11.454913 IP 192.168.1.1.2189 > 192.168.1.238.46154: tcp 0 08:44:11.455389 IP 192.168.1.238.46174 > 192.168.1.1.2189: tcp 0 08:44:11.455389 IP 192.168.1.238.46170 > 192.168.1.1.2189: tcp 0 08:44:11.455395 IP 192.168.1.1.2189 > 192.168.1.238.46174: tcp 0 08:44:11.455396 IP 192.168.1.1.2189 > 192.168.1.238.46170: tcp 0 08:44:11.455398 IP 192.168.1.238.46126 > 192.168.1.1.2189: tcp 0 08:44:11.455404 IP 192.168.1.1.2189 > 192.168.1.238.46126: tcp 0 08:44:11.493205 IP 192.168.1.1.1900 > 192.168.1.235.59185: UDP, length 363 08:44:11.576010 IP 54.175.191.203.443 > 192.168.1.238.53800: tcp 0 08:44:11.576799 IP 192.168.1.238.53800 > 54.175.191.203.443: tcp 0 08:44:11.711770 IP 192.168.1.50.54401 > 162.254.192.87.27024: tcp 113 08:44:11.730535 IP 192.168.1.245.59178 > 34.117.13.189.443: tcp 296 08:44:11.755106 IP 34.117.13.189.443 > 192.168.1.245.59178: tcp 0 -
Ok So In testing the integration I went to the github page. Looks like I am not the only one with the issue. Here is a link to the problem someone else is having. I would bet anything he is also using a FreeBSD router. The plot thickens...
Similar issue found on github integration with Home Assistant
-
@kahodges1721 said in pfSense Blocking Roborock app:
Ok So In testing the integration I went to the github page. Looks like I am not the only one with the issue. Here is a link to the problem someone else is having. I would bet anything he is also using a FreeBSD router. The plot thickens...
Similar issue found on github integration with Home Assistant
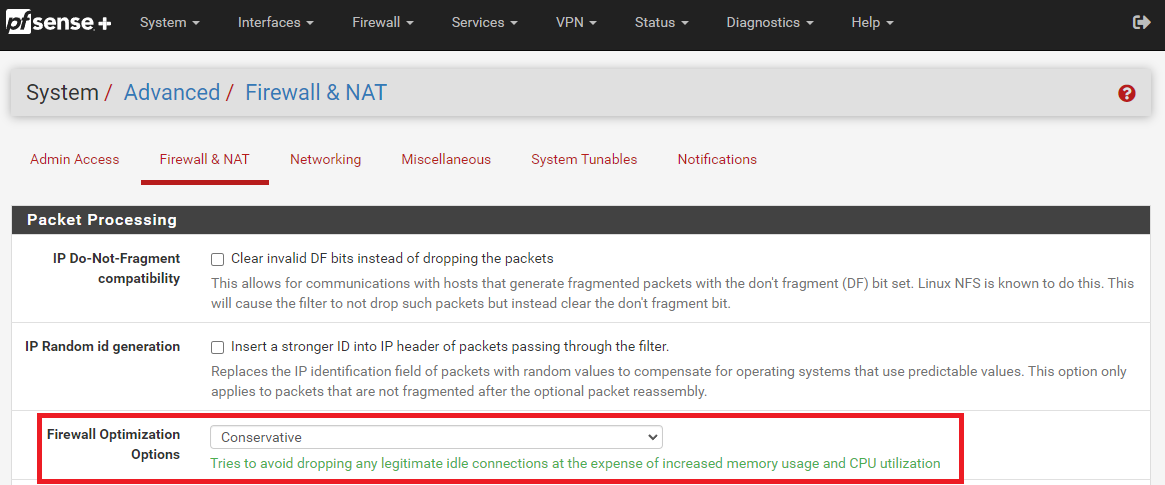
Read through that chain on Github. I lean towards an app update being the problem, but why it works via Wi-Fi with the Netgear in place, but fails with pfSense and OPNsense in place, is a mystery. Might be subtle differences in how states are handed between the Netgear firewall engine and FreeBSD. State timeouts can be configured in pfSense. Perhaps setting the firewall optimization to "Conservative" might help. That option is here:
-
@bmeeks I gave the change a try and its a no go. I agree that it must be a change on the side of roborock. I guess the reason I am concerned is the population of users with pfSense and roborock devices might not be large enough to warrent a change from Roborock. Meaning I am left either leaving pfSense which I really dont want to do or get a different robot which this one is by far the best I have used so I dont want to do that either! I keep going back to the fact that the netgear works. This has to give us some clues. At first I considered that Roborock flagged my IP or something bc it didnt like the integration through HA but that cant be the case since it works through the Netgear. The only thing left is there is some difference either in DNS handling or firewall rules that is blocking the communication. With pfSense being so open to the user vs a standard router I feel there is a fighting chance to find the setting and configure it. Hopefully posting in the github brings more users with issues to light.
-
Some good information learned from the github link that I thought would be worth sharing here for ideas.
I believe the apps (Mi Home and Roborock) work slightly different. One thing I noticed is the Mi Home app connects using both their servers and locally to the device whereas the Roborock app connects to the device through their cloud MQTT service on port 8883 (in addition to TCP connections on 443). I don't believe the Mi Home app ever used MQTT since I explicitly had to allow that on my firewall to get the Roborock app to work. I haven't used pfSense or OPNsense for a while but I wonder if there's something weird when it comes to MQTT?
I also noticed my Sophos XG logs shows the MQTT connections with the Roborock MQTT broker as "SSL Traffic over Non-SSL Ports".
-
usiot.roborock.com is apparently the culprit. I got a message on the other forum from the developer of the integration and that’s the site that is being used for the api. It seems pfsense will not resolve it. I’ve never had this issue so not sure why or what to do to fix it but it at least pin points the problem. I’m curious if it resolves on anyone else running pfsense
-
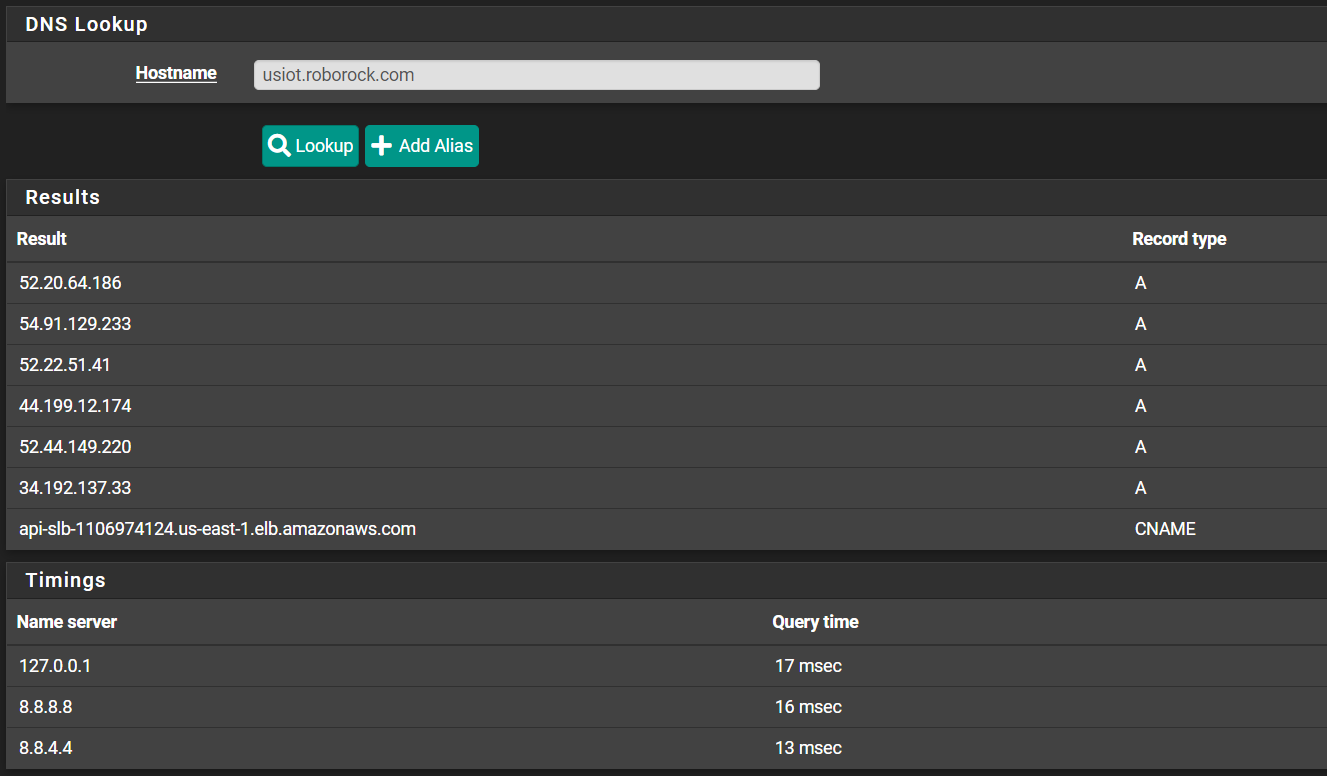
@kahodges1721
It resolved here just fine.
-
@jarhead yes it shows “resolved“ on mine also but when I try to navigate to it I don’t get anything. I may be using the wrong terminology here. Basically I type in the aggress into a web browser and can’t reach it. Navigating to the other api euiot.roborock.com seems to not get blocked and opens a white page. I also ran a trace route below is what I got.
10.157.0.1 8.118 ms 7.113 ms 7.503 ms
2 209.196.177.66 7.205 ms 7.788 ms 8.731 ms
3 207.255.30.160 25.315 ms 24.719 ms 29.381 ms
4 99.83.89.162 28.368 ms
99.83.68.84 23.760 ms 24.622 ms
5 * * *
6 * * *
7 52.93.29.98 31.090 ms
52.93.29.92 33.040 ms
52.93.29.82 25.631 ms
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * * -
This is what I get with the USIOT and Euiot address
Sorry for using the links but I can’t get to the computer right now and linking an image from my phone I couldn’t figure out how
-
The usiot.roborock.com hostname resolves fine on my pfSense box:
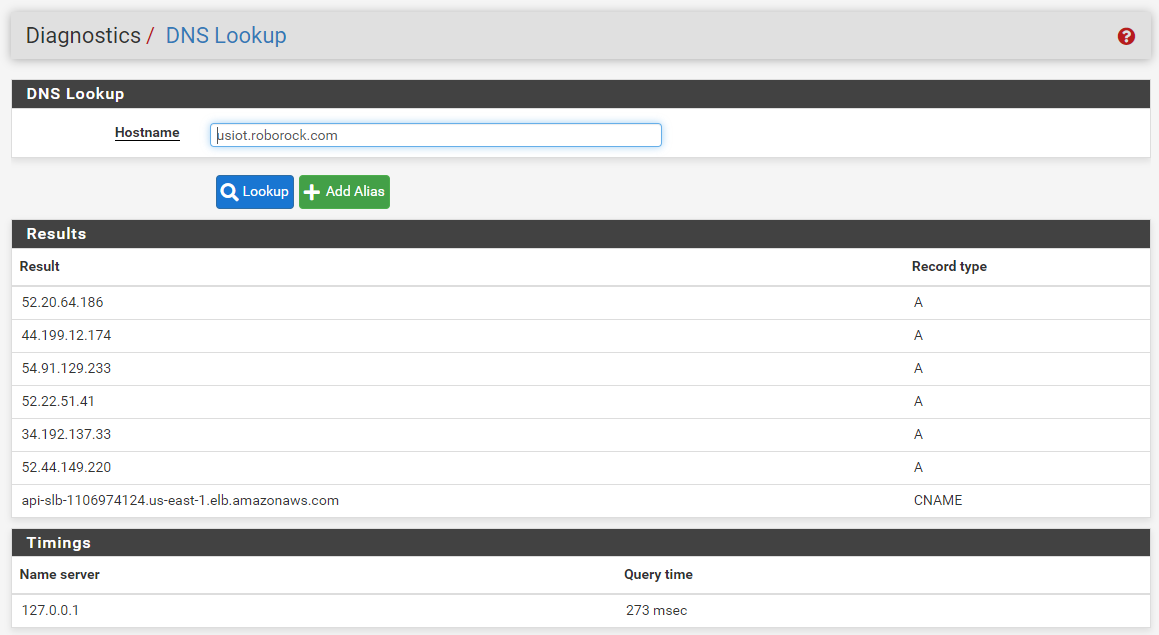
You said "usiot.roborock.com" in your first post, but then in the follow up with the link to Imgur you show both usiot and euiot. Which one is correct? Do both resolve properly on your firewall?
Go to DIAGNOSTICS > DNS Lookup in the pfSense menu and enter both hostnames, one at the time, hitting Lookup between attempts. Post back the output from the results window as I did above.
-
@bmeeks both resolve fine According to the test. I guess I was assuming it wasn’t resolving since when I type them into the web browser the US gives the server stopped responding error and the EU works just fine. Switching to LTE both work just fine and display a blank white page as expected.
Both are used for the api according to the developer of the integration. I focused only on the U.S. bc that seems to be the culprit of the issue
This is the post that lead to the testing:
Starting with the basics. Is your router resolving DNS euiot.roborock.com? (Which is the default base url to discover the real api to be used based on your account country). And, if your account from US, is it also solving usiot.roborock.com ?
-
@bmeeks dns lookup results