pfBlockerNG-devel v3.1.0_19/10
-
Yes did a clean fresh install of the PfblockerNG package 3 times with the keep settings uncheck
but the error is still showing up , I notice under the Report unified Geoip is unk but under Alert Geoip/ASN list country,
the packages i have installed are PfblockerNG, Suricata and Cron (memory usage 8% ), (MBUF Usage 3%), (State table size 0%) ( cpu usage 4%) (Swap space 0%) Service Status all green,
did some test clear the Dns Resolver log under( system logs/system/dns resolver/) these 2 lines
unbound 21493 [21493:0] notice: init module 0: python
unbound 21493 [21493:0] info: [pfBlockerNG]: pfb_unbound.py script loaded
reappear go to the dashboard the DNSBL turns yellow and gives the error
|ERROR| [pfBlockerNG]: Failed to load python module 'maxminddb': No module named 'maxminddb'
|ERROR| [pfBlockerNG]: Failed to load python module 'sqlite3': No module named '_sqlite3' -
@smoke_a_j said in pfBlockerNG-devel v3.1.0_19/10:
DNSBL Source Definitions, Line 1: Invalid URL or Hostname not resolvable!
Either DNS isn't working on your box or something is blocking those urls.
-
@yorke I would backup you config and install a fresh copy of pfSense. Followed by a restore of the config.
-
@bbcan177 Gracias, at first I thought it was seeming similar to the inbound permit saving issue. Regardless of having most of these feeds already whitelisted, tracked it down to about 1500 some lines of regex I had came across and added a while back, most of which seemed to not be populating any alerts but invisibly blocking at random until matching the suffix/prefix portions of the code to match known alerting lines started populating the rest. I trimmed out 1300 lines to whats working, I then realized the entire 1500 lines I found were basically a reflection of the DNSBL TLD Group 1 & 2 lists. Went back to just my first 680 lines of regex and no more ghosted double filtering and running smooth
-
@smoke_a_j If you can pm or email that regex list, I can check it out to see if there is some code improvement required.
-
@yorke said in pfBlockerNG-devel v3.1.0_19/10:
pfBlockerNG-devel 3.1.0_11 |ERROR| python module 'maxminddb
Pfsense 2.6.0-RELEASE
I upgraded pfBlockerNG-devel to 3.1.0_11 and got some issue before i upgraded everyting was work but now after the upgrade I am geting the errors listed below,
2023-01-20 18:16:12,627|ERROR| [pfBlockerNG]: Failed to load python module 'maxminddb': No module named 'maxminddb'
2023-01-20 18:16:12,627|ERROR| [pfBlockerNG]: Failed to load python module 'sqlite3': No module named '_sqlite3'I got the same error on pfSense v2.6.0 since the upgrade to pfBlockerNG v3.1.0_11. I have cleared the error in py_error.log. Lets see if it comes back.
The report tab showns traffic being pass/block
the dashboard for DNSBL the packets stay at 0 the counter do not move, but the ip counter worksSame issue with IP Counter. It shows number of blocked IPs for a while, but when you refresh the page, counter goes to 0. This issue happens if you apply this patch via system patches package.
More details here.
If you revert this change, counter starts working as it should and it doesnt reset to 0 after some time.
-
@bbcan177 said in pfBlockerNG-devel v3.1.0_19/10:
Add "application/json" to list of allowed file download mime-types
I had hoped this might let pfBlocker directly download a JSON list like the one found at Microsoft Azure IPs. This is a file I manually download and then use pfSense's GUI CMD interface to upload for pfBlocker (I set the format to AUTO). Ran this on 3.1.0_11 just now.
It didn't work. So what JSON-related things were enabled with this change?
Thanks!
-
It happened again after after update.
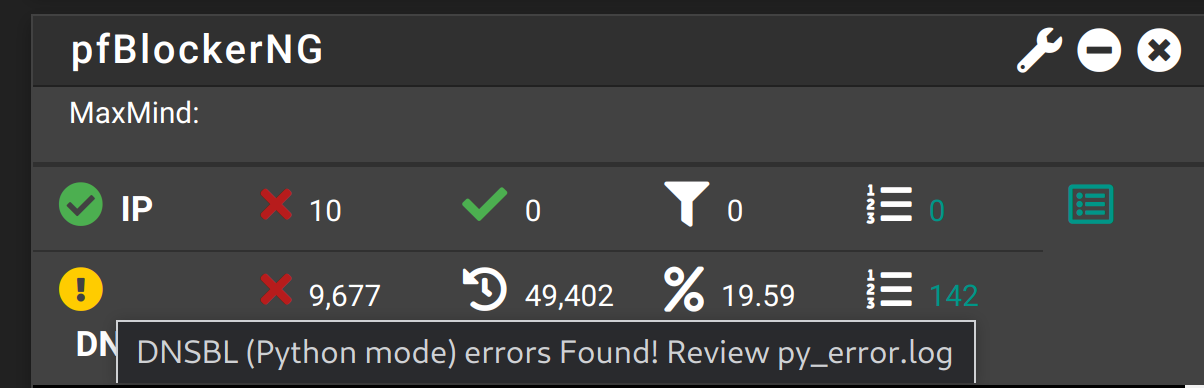
This is the content of py_error.log
2023-01-24 16:36:57,206|ERROR| [pfBlockerNG]: Failed to load python module 'maxminddb': No module named 'maxminddb' 2023-01-24 16:36:57,206|ERROR| [pfBlockerNG]: Failed to load python module 'sqlite3': No module named '_sqlite3'Despite these errors, everything is working fine.
-
-
@cmcdonald
Same problem on my side.[22.05-RELEASE][admin@firewall.home]/root: pkg info py* unbound
pkg: No match. -
-
@cmcdonald said in pfBlockerNG-devel v3.1.0_19/10:
Sorry, try this:
pkg info "py*" unboundHere it is:
[2.6.0-RELEASE][admin@pfSense.home.arpa]/root: pkg info "py*" unbound py38-ply-3.11 py38-setuptools-57.0.0 py39-maxminddb-2.0.3 py39-setuptools-57.0.0 py39-sqlite3-3.9.9_7 python38-3.8.12_1 python39-3.9.9 unbound-1.13.2 -
@nimrod Thanks. I see the problem. Testing a fix. Standby
-
@nimrod can you also share
pkg info unbound? -
@cmcdonald said in pfBlockerNG-devel v3.1.0_19/10:
@nimrod can you also share
pkg info unbound?Of course. Here it is:
[2.6.0-RELEASE][admin@pfSense.home.arpa]/root: pkg info unbound unbound-1.13.2 Name : unbound Version : 1.13.2 Installed on : Mon Jan 31 21:24:27 2022 CET Origin : dns/unbound Architecture : FreeBSD:12:amd64 Prefix : /usr/local Categories : dns Licenses : BSD3CLAUSE Maintainer : jaap@NLnetLabs.nl WWW : https://www.nlnetlabs.nl/projects/unbound Comment : Validating, recursive, and caching DNS resolver Options : DEP-RSA1024 : off DNSCRYPT : off DNSTAP : off DOCS : off DOH : on ECDSA : on EVAPI : off FILTER_AAAA : off GOST : on HIREDIS : off LIBEVENT : on MUNIN_PLUGIN : off PYTHON : on SUBNET : off TFOCL : off TFOSE : off THREADS : on Shared Libs required: libexpat.so.1 libnghttp2.so.14 libpython3.8.so.1.0 libevent-2.1.so.7 Shared Libs provided: libunbound.so.8 Annotations : FreeBSD_version: 1203500 build_timestamp: 2022-01-12T15:27:10+0000 built_by : poudriere-git-3.3.99.20211130 cpe : cpe:2.3:a:nlnetlabs:unbound:1.13.2:::::freebsd12:x64 port_checkout_unclean: no port_git_hash : 8df9544dcbab ports_top_checkout_unclean: yes ports_top_git_hash: 7046b65c0d41 repo_type : binary repository : pfSense Flat size : 7.99MiB Description : Unbound is designed as a set of modular components, so that also DNSSEC (secure DNS) validation and stub-resolvers (that do not run as a server, but are linked into an application) are easily possible. Goals: * A validating recursive DNS resolver. * Code diversity in the DNS resolver monoculture. * Drop-in replacement for BIND apart from config. * DNSSEC support. * Fully RFC compliant. * High performance, even with validation enabled. * Used as: stub resolver, full caching name server, resolver library. * Elegant design of validator, resolver, cache modules. o provide the ability to pick and choose modules. * Robust. * In C, open source: The BSD license. * Smallest as possible component that does the job. * Stub-zones can be configured (local data or AS112 zones). Non-goals: * An authoritative name server. * Too many Features. WWW: https://www.nlnetlabs.nl/projects/unbound -
@nimrod Can you now try reinstalling pfBlockerNG-devel on 22.05/2.6, and repeat the above command
pkg info "py*" unbound -
@cmcdonald said in pfBlockerNG-devel v3.1.0_19/10:
@nimrod Can you now try reinstalling pfBlockerNG-devel on 22.05/2.6, and repeat the above command
pkg info "py*" unboundI reinstalled it and here is the output:
[2.6.0-RELEASE][admin@pfSense.home.arpa]/root: pkg info "py*" unbound py38-maxminddb-2.0.3 py38-ply-3.11 py38-setuptools-57.0.0 py38-sqlite3-3.8.12_7 py39-maxminddb-2.0.3 py39-setuptools-57.0.0 py39-sqlite3-3.9.9_7 python38-3.8.12_1 python39-3.9.9 unbound-1.13.2 -
@nimrod That should be correct now. Clear the unbound errors and try again.
-
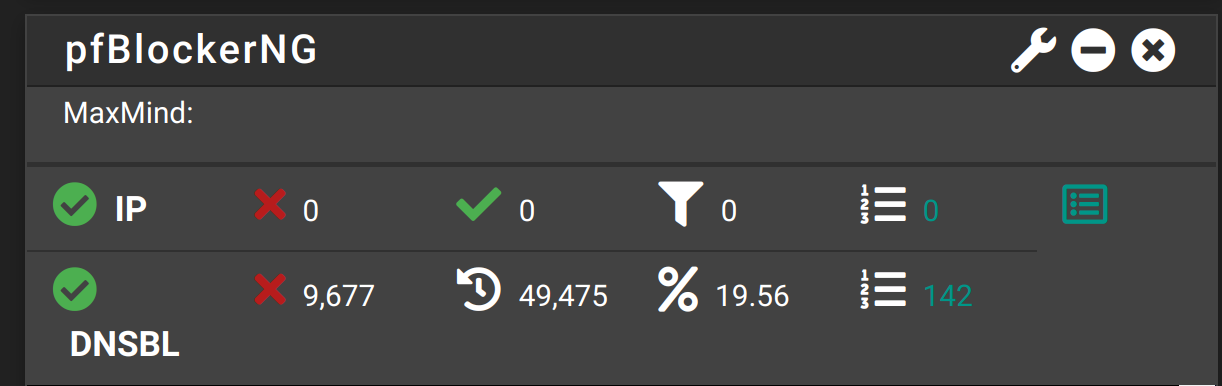
@cmcdonald said in pfBlockerNG-devel v3.1.0_19/10:
@nimrod That should be correct now. Clear the unbound errors and try again.
Yup. That fixed it. Thank you sir.
-
@draco said in pfBlockerNG-devel v3.1.0_19/10:
I had hoped this might let pfBlocker directly download a JSON list like the one found at Microsoft Azure IPs. This is a file I manually download and then use pfSense's GUI CMD interface to upload for pfBlocker (I set the format to AUTO). Ran this on 3.1.0_11 just now.
The Link you posted is the HTML page. You need to use the direct link:
https://download.microsoft.com/download/7/1/D/71D86715-5596-4529-9B13-DA13A5DE5B63/ServiceTags_Public_20230123.json
Keep in mind that this will parse all IPs in the json file. You could also create a new shell script to parse this JSON and get more refinement on which IPs to pull ( "Advanced Tunables - Post-Script Script" feature.)