No WLAN Administering pfSense Box
-
LAN network - x.x.1.0 , LAN DNS - x.x.1.1
WLAN network - x.x.2.0 , WLAN DNS - x.x.2.1I would like to keep the computers attached to my WLAN network from being able to administrate my pfSense box. I created a firewall rule on the WLAN to block connections to x.x.2.1 and another rule to block connections to x.x.1.1 as I have a couple of rules allowing access to the LAN network from the WLAN. This doesn't work as I use x.x.2.1 and x.x.1.1 as my DNS server addresses on each network respectively. I have no internet on WLAN when I block the x.x.2.1; I'm blocking my DNS server.
I haven't been able to come up with an answer searching the internet. Anyone have any ideas how to accomplish keeping any computers on my WLAN network from being able to administrate my pfSense box or from my WLAN through to my LAN? Any suggestions would be most helpful. Thank you.
-
You need a Int Group to scale if you got more and more VLANs and the Ruleset:
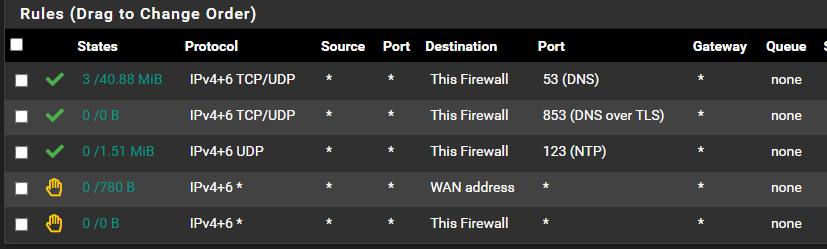
-
@newuser2pfsense rules are evaluated top down, first rule to trigger wins.
If you want your wlan to use pfsense for dns, then allow that. Below that block access to "this firewall" this will prevent any other access to any pfsense IP. then below that allow all, ie the internet.
Here is a sample set of rules, that allows say ping, dns and ntp to the pfsense IP on that interface, then blocks all other access to any pfsense IP, also blocking access to any other network/vlan you might be running on rfc1918 space.
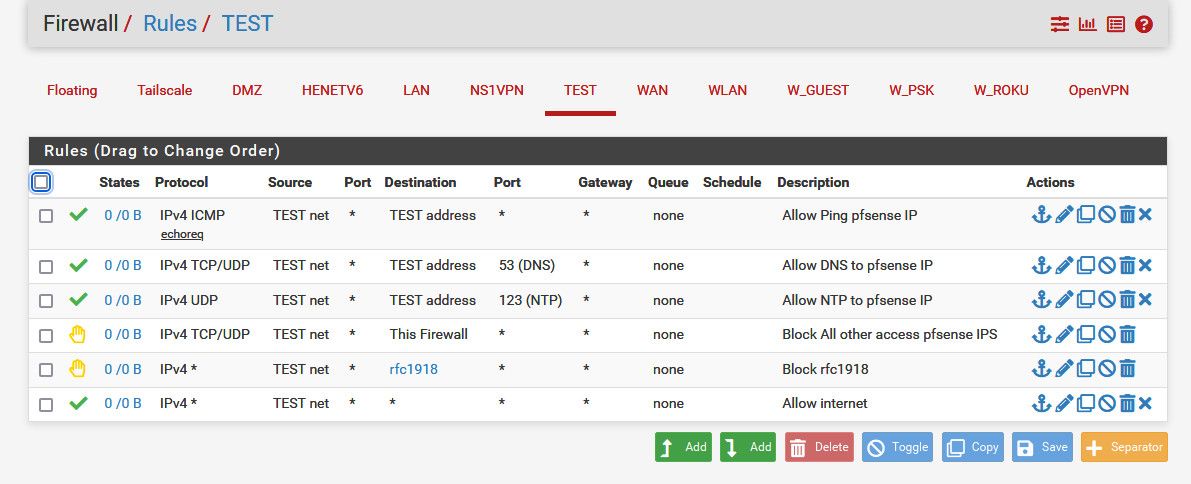
-
@NOCling Thank you for your reply.
@johnpoz I think this is where I'm getting my rules mixed up. My pfSense LAN and WLAN interfaces are x.x.1.1 and x.x.2.1 respectively; of course each interface has it's own RJ45 port on the pfSense box. I use Linux OS on my computers so I manually set the Gateway and DNS server on each. Example -
Computer 1 -
IPv4 Address: x.x.1.11
Netmask: 24
Gateway: x.x.1.1
DNS Server: x.x.1.1Computer 2 -
IPv4 Address: x.x.2.100
Netmask: 24
Gateway x.x.2.1
DNS Server: x.x.2.1As well, each pfSense interface is connected to it's own Layer 2 switch. These 2 switches are not connected to each other in any way. What I find interesting is that when I'm on my WLAN computer, I can access my LAN components without setting any WLAN rules for them. I actually have to set WLAN block rules for the LAN components that I don't want any of my WLAN computers to have access to. I have no rules on my WLAN giving access to my LAN other than being able to ping (ICMPany) from my WLAN to a destination of any. I can even access my LAN network administration IP (x.x.1.1) from my WLAN network.
-
@newuser2pfsense said in No WLAN Administering pfSense Box:
. What I find interesting is that when I'm on my WLAN computer, I can access my LAN components without setting any WLAN rules for them
Not possible how you describe - just not.. You have some part of the puzzle missing. Did you bridge these interfaces? What exactly is this wlan providing wifi.. And do you have anything else connected to this wifi on your lan, etc.
If there are no rules on your wlan interface. It would not be possible for wlan devices to connect through pfsense and talk to lan devices. Unless you had bridge setup and not filtering where you think your filtering, or you actually disabled the firewall on pfsense.
What exactly is this pfsense box?
if your saying if you set a specific on wlan interface it blocks? Maybe you setup a bridge - if so are you filtering on members, or the bridge? There is default deny, I just do not see how you could of disabled that without completely disabled the firewall completely..
#--------------------------------------------------------------------------- # default deny rules #--------------------------------------------------------------------------- block in inet all ridentifier 1000000103 label "Default deny rule IPv4" block out inet all ridentifier 1000000104 label "Default deny rule IPv4" block in inet6 all ridentifier 1000000105 label "Default deny rule IPv6" block out inet6 all ridentifier 1000000106 label "Default deny rule IPv6"View your full rule set
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.htmlDid you edit /etc/inc/filter.inc
-
@johnpoz I agree with you totally. I shouldn't be able to cross interface traffic from my WLAN to my LAN unless a rule is set. I"m running pfSense 22.05 and the WLAN is for my wireless. There are no wireless components on my WLAN connected to my LAN. I don't have anything physically bridged. I just checked a tube video and I have no pfSense interface bridges set; I didn't know you could do that. I haven't edited any files in pfSense.
At one point I did have a computer with 2 nics where I had one nic connected to the LAN and one nic connected to the WLAN thereby bridging the two which is why I had the WLAN rules blocking access to the LAN components. I have since disconnected the LAN nic connection from this computer and it's only connected to the WLAN now. Even though the computer's LAN nic is disconnected and I disabled the WLAN firewall rules blocking access to the LAN components, I can still access the LAN components. When I re-enable the WLAN firewall rules blocking access to the LAN components, I can't reach the components from the WLAN.
Could pfSense be keeping a setting somewhere from this previously bridged computer allowing the WLAN to reach the LAN? Just a thought.
-
@newuser2pfsense please post a picture of your rules on this wlan interface, and do you have any floating rules.
What your saying is just not possible.. There is a piece of the puzzle that is missing.
But as I showed you - the default rules are deny.. It is not possible if the firewall is actually running for traffic to pass through pfsense. Without a rule to allow it, or a previous state that allows the traffic.
Did you clear the states?
When you say you can talk to pfsense to get to lan -- look at the state table - let see the traffic in the state table. if the firewall is running and allowing traffic through it, then there is a state, etc.
If I had to guess you got some rule on floating that is not marked quick and allowing traffic until you create a specific block rule on the interface..
-
@johnpoz I believe it's not possible as well. I have no floating rules entered into pfSense. I reset the firewall state table and tested again and I'm still able to reach 3 of my LAN components by way of my WLAN; seen currently blocked in the below image. (I disabled those three rules when I was testing.) I just saw a double entry for .14, I'll fix that later.
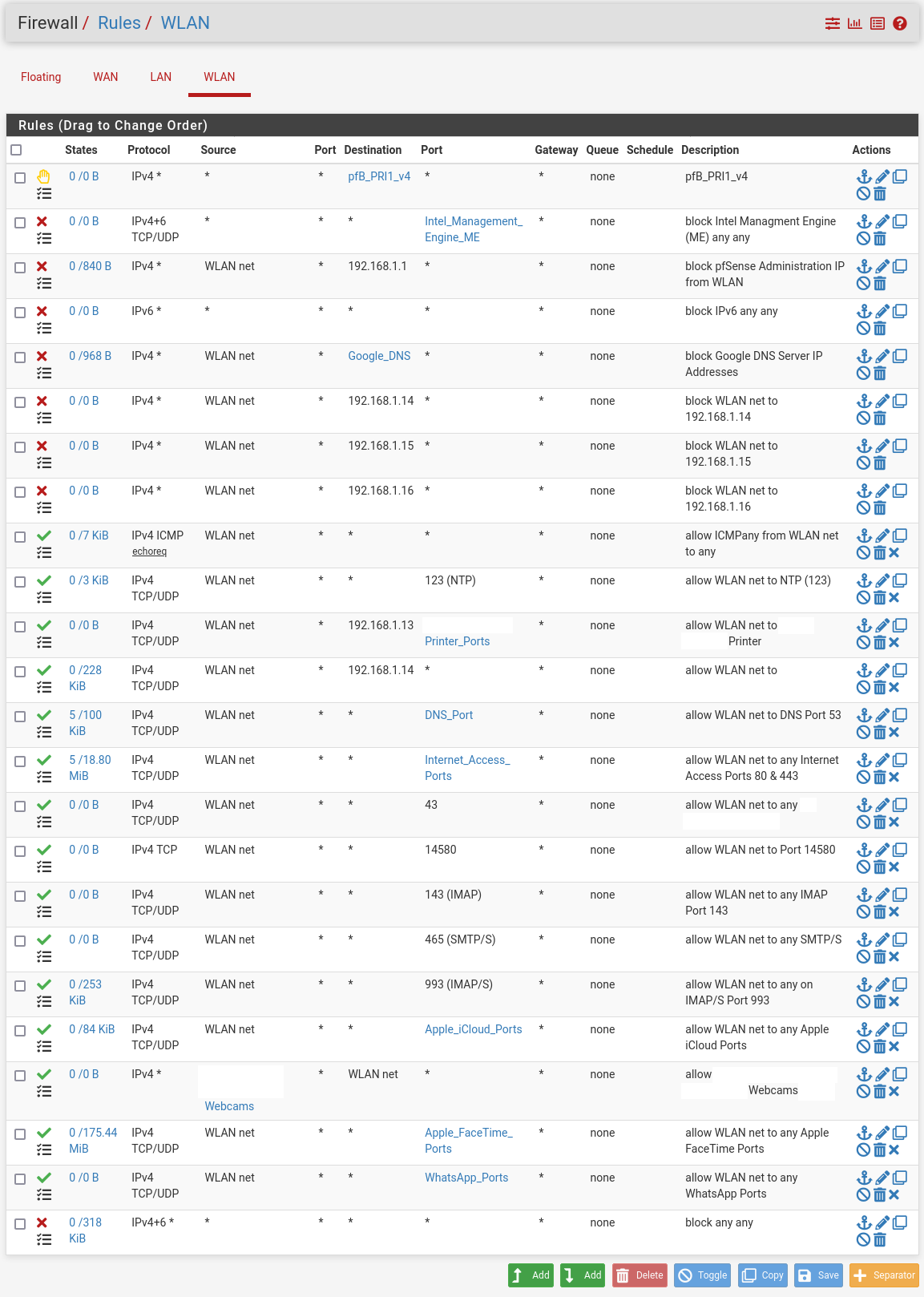
The x.x.2.100 is the computer sitting on my WLAN network that I've been using to see if I can reach my 3 LAN components. The state table below is for this computer (a snapshot in time).
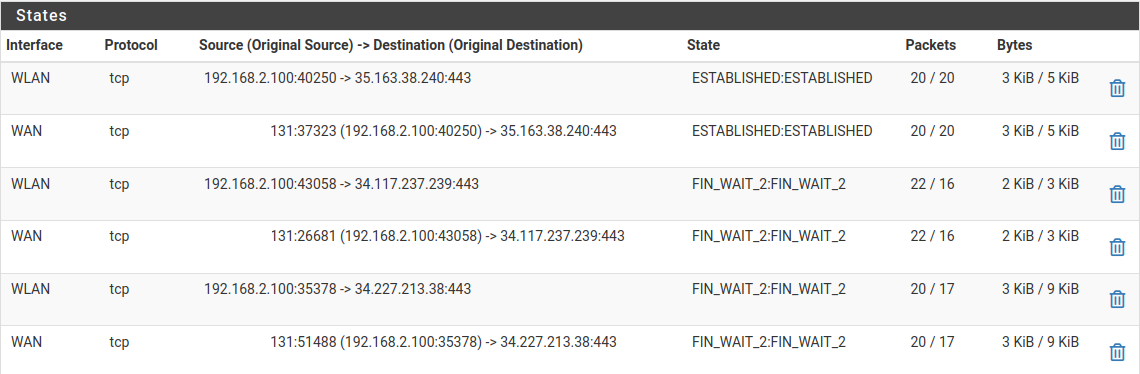
-
@newuser2pfsense well your saying this 2.100 box was talking to some 1.x box at the time you looked at the states - it clearly didn't go through pfsense to get there..
How exactly do you think a stateful firewall allowed traffic through itself without creating a state?
What port are you talking to these devices on your 1 network - you have lots of rules there with allowing traffic.. But again - how did you route through pfsense without a state?? Just not possible when clearly other states are being made.
What makes more sense is your not routing through pfsense.. Lets see a traceroute to an IP an IP in the 1 network..
Example here is my lan 9.100 talking to 2.12
$ tracert -d 192.168.2.12 Tracing route to 192.168.2.12 over a maximum of 30 hops 1 <1 ms <1 ms <1 ms 192.168.9.253 2 1 ms <1 ms <1 ms 192.168.2.12 Trace complete.if I ping this 2.12 you can see a state
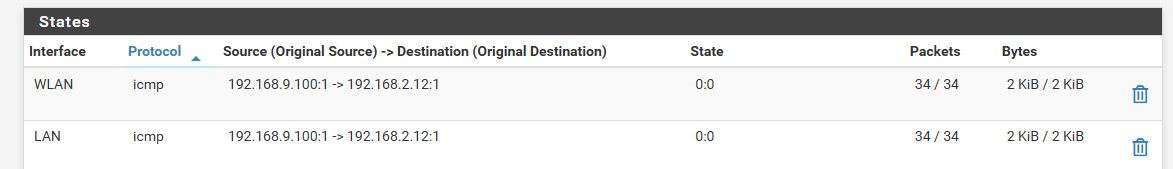
-
@johnpoz I made a mistake when I took the state snapshot in time in my above post. In my WLAN rules, I had the 3, .1.x components blocked when I took that state. My apologies.
I have since disabled those rules, used my browser on the 2.100 computer attached to the WLAN to connect to the 3 LAN components with no issues as seen below:
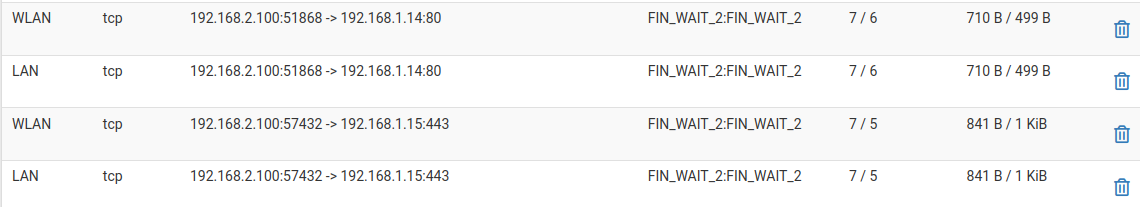

Sorry for the confusion.
-
-
@johnpoz there several block rules for 1.14, 1.15 and 1.16 higher up that should prevent access to those 3 web servers. Not sure why there are no hits on those rules.
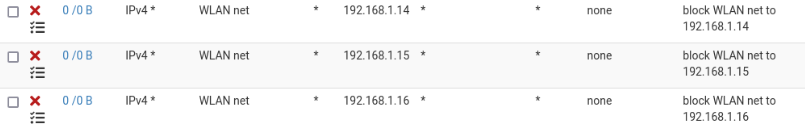
@newUser2pfSense Scrap all the rules and start over based off the rules screenshot that @johnpoz or @NOCling posted. Add any additional allow rules & aliases you need.
-
@ahking19 said in No WLAN Administering pfSense Box:
Not sure why there are no hits on those rules.
Because a state had prob already been created.. States are evaluated before rules.
if I have a state from 192.168.2.100 --> 192.168.1.14 on port 80..
Any block rule you create trying to stop said traffic is pretty useless until that state is gone.. Be it times out, be it closed by the client, be it killed by the pfsense admin, etc.
-
@johnpoz said in No WLAN Administering pfSense Box:
@newuser2pfsense well no duh you would be able to access those..
This rule allows that.
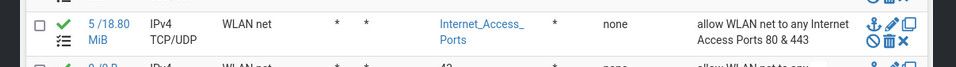
Doh, I didn't see that. Geez! I'm a moron! Ok then, so let me ask the question, how should a WLAN rule be created that allows internet access and blocks access to my 3 LAN components using any protocols and any ports given my above listed WLAN rules? As well, create a WLAN rule that blocks administration to my pfSense box on interface 192.168.2.1 which I also use as a DNS IP manually input into each of my computers connected to my WLAN? I'm just not seeing it right now.
-
@newuser2pfsense I already gave you an example of a locked down vlan..
Customize to your hearts content - rules are evaluated top down, first rule to trigger wins - no other rules are evaluated. It not difficult to come up with a set of rules to be very precise in what they allow or don't allow..
For example your block rules before your allow rule accomplished your goal of not getting those IPs, etc. Could prob just be done cleaner, etc..
This rule pretty useless
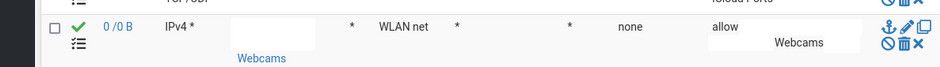
Something on the wlan net would never send any traffic to pfsense to talk to something else on the wlan net - so what exactly could this rule be wanting to allow where pfsense would be involved?